How to run SUDO commands in Windows 11/10
With the sudo command, users can run commands in elevated privilege mode without switching to superuser mode. This article will introduce how to simulate functions similar to sudo commands in Windows systems.
What is Shudao Command?
Sudo (short for "superuser do") is a command-line tool that allows users of Unix-based operating systems such as Linux and MacOS to execute commands with elevated privileges that are typically held by administrators .
Running SUDO Commands in Windows 11/10
However, with the launch of the latest Windows 11 Insider preview, Windows users can now experience this feature. This new feature enables users to run elevated commands directly in an unelevated console session without opening a separate elevated terminal. If you haven't seen this feature in stable releases yet, please be patient and wait for it to roll out on your PC.
How to enable SUDO in Windows?
Enabling SUDO in Windows provides basic administrative control and security to the system. It improves the overall security of the system by elevating privileges as needed and restricting access to sensitive activities and resources. This helps prevent unauthorized installation or changes that may pose a threat to system integrity. Before executing the SUDO command, ensure that the SUDO function is enabled in the Windows system. By enabling SUDO, you can manage your system more efficiently and ensure that only authorized users can access and modify sensitive data and settings. This permission management method can help you improve the security of your system and effectively prevent potential security risks. Therefore, before using the SUDO command to perform any critical operations, please ensure that the SUDO function is properly configured and enabled to ensure the security and stability of the system.
Follow the prescribed steps:
- Press the Windows I key combination to open the Settings application.
- Go to the left side of the window, click System, then click Developers.
- Find the Enable SUDO feature and turn on the toggle switch.
- Finally, click Yes to confirm.
How to configure SUDO for Windows?
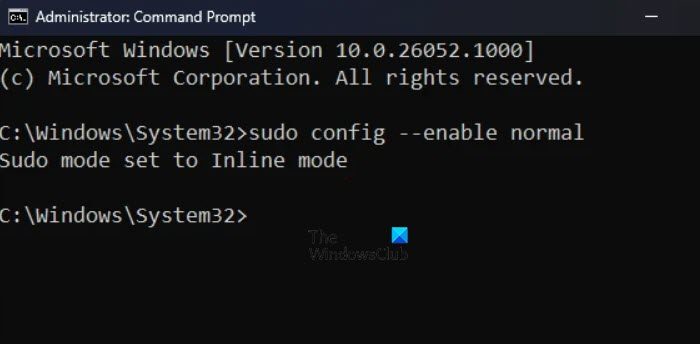
SUDO for Windows usually has three configuration options:
- In new window(ForceNewWindow)
- Input close (DisableInput)
- Inline(normal)
To change the default configuration options for SUDO for Windows, do the following:
- Press the Windows I key combination to open the Settings application.
- Go to the left side of the screen and click System.
- Scroll down and click for developers.
- Find the Enable SUDO option and then find the way to configure SUDO to run your application.
- From the drop-down menu, select In New Window (ForceNewWindow), Input Off (DisableInput), or Inline (Normal).
Additionally, you can open an elevated command line.
- After replacing
with forceNewWindow, input disabled or normal, type the following command and press the Enter button:
SUDO配置--启用<;配置选项>;
This will do the job for you.
How to use SUDO on Windows?
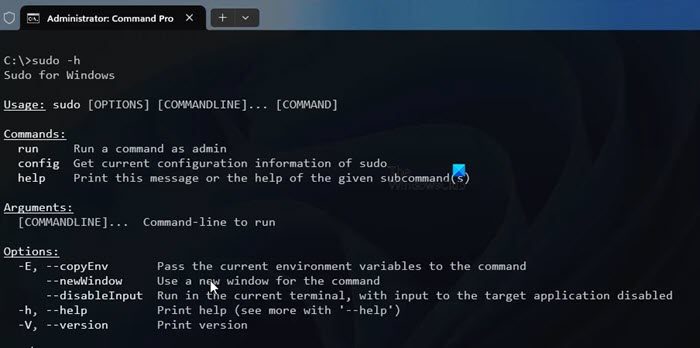
Make sure that before using SUDO in Windows, SUDO must be enabled and configured on your computer.
- Press the Windows key, type command prompt, and select Run as administrator.
- Now use sudo Before any command you want to use, enter the following command to learn about the options that come with sudo.
数都-h
that's all!
The above is the detailed content of How to run SUDO commands in Windows 11/10. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Can I install mysql on Windows 7
Apr 08, 2025 pm 03:21 PM
Can I install mysql on Windows 7
Apr 08, 2025 pm 03:21 PM
Yes, MySQL can be installed on Windows 7, and although Microsoft has stopped supporting Windows 7, MySQL is still compatible with it. However, the following points should be noted during the installation process: Download the MySQL installer for Windows. Select the appropriate version of MySQL (community or enterprise). Select the appropriate installation directory and character set during the installation process. Set the root user password and keep it properly. Connect to the database for testing. Note the compatibility and security issues on Windows 7, and it is recommended to upgrade to a supported operating system.
 How to solve mysql cannot connect to local host
Apr 08, 2025 pm 02:24 PM
How to solve mysql cannot connect to local host
Apr 08, 2025 pm 02:24 PM
The MySQL connection may be due to the following reasons: MySQL service is not started, the firewall intercepts the connection, the port number is incorrect, the user name or password is incorrect, the listening address in my.cnf is improperly configured, etc. The troubleshooting steps include: 1. Check whether the MySQL service is running; 2. Adjust the firewall settings to allow MySQL to listen to port 3306; 3. Confirm that the port number is consistent with the actual port number; 4. Check whether the user name and password are correct; 5. Make sure the bind-address settings in my.cnf are correct.
 Unable to access mysql from terminal
Apr 08, 2025 pm 04:57 PM
Unable to access mysql from terminal
Apr 08, 2025 pm 04:57 PM
Unable to access MySQL from the terminal may be due to: MySQL service not running; connection command error; insufficient permissions; firewall blocks connection; MySQL configuration file error.
 How to copy and paste mysql
Apr 08, 2025 pm 07:18 PM
How to copy and paste mysql
Apr 08, 2025 pm 07:18 PM
Copy and paste in MySQL includes the following steps: select the data, copy with Ctrl C (Windows) or Cmd C (Mac); right-click at the target location, select Paste or use Ctrl V (Windows) or Cmd V (Mac); the copied data is inserted into the target location, or replace existing data (depending on whether the data already exists at the target location).
 How to avoid sql injection
Apr 09, 2025 pm 05:00 PM
How to avoid sql injection
Apr 09, 2025 pm 05:00 PM
To avoid SQL injection attacks, you can take the following steps: Use parameterized queries to prevent malicious code injection. Escape special characters to avoid them breaking SQL query syntax. Verify user input against the whitelist for security. Implement input verification to check the format of user input. Use the security framework to simplify the implementation of protection measures. Keep software and databases updated to patch security vulnerabilities. Restrict database access to protect sensitive data. Encrypt sensitive data to prevent unauthorized access. Regularly scan and monitor to detect security vulnerabilities and abnormal activity.
 How to encrypt oracle view
Apr 11, 2025 pm 08:30 PM
How to encrypt oracle view
Apr 11, 2025 pm 08:30 PM
Oracle View Encryption allows you to encrypt data in the view, thereby enhancing the security of sensitive information. The steps include: 1) creating the master encryption key (MEk); 2) creating an encrypted view, specifying the view and MEk to be encrypted; 3) authorizing users to access the encrypted view. How encrypted views work: When a user querys for an encrypted view, Oracle uses MEk to decrypt data, ensuring that only authorized users can access readable data.
 Can vs code run in Windows 8
Apr 15, 2025 pm 07:24 PM
Can vs code run in Windows 8
Apr 15, 2025 pm 07:24 PM
VS Code can run on Windows 8, but the experience may not be great. First make sure the system has been updated to the latest patch, then download the VS Code installation package that matches the system architecture and install it as prompted. After installation, be aware that some extensions may be incompatible with Windows 8 and need to look for alternative extensions or use newer Windows systems in a virtual machine. Install the necessary extensions to check whether they work properly. Although VS Code is feasible on Windows 8, it is recommended to upgrade to a newer Windows system for a better development experience and security.
 How to prevent sql injection vulnerabilities
Apr 09, 2025 pm 04:54 PM
How to prevent sql injection vulnerabilities
Apr 09, 2025 pm 04:54 PM
To prevent SQL injection vulnerabilities, organizations should take the following steps: Replace sensitive data with parameterized queries. Verify the format and characters of the data input. Limits the list of characters entered by the user. Escape special characters to avoid being interpreted as SQL commands. Use precompiled stored procedures for increased security. Integrate security frameworks to protect applications. Update software and databases regularly to fix vulnerabilities.






