 Database
Database
 Mysql Tutorial
Mysql Tutorial
 Detailed graphic explanation of RBAC user rights management database design in thinkphp
Detailed graphic explanation of RBAC user rights management database design in thinkphp
Detailed graphic explanation of RBAC user rights management database design in thinkphp
RBAC (Role-Based Access Control, role-based Access Control) means that users are associated with permissions through roles. Simply put, a user has several roles, and each role has several permissions. In this way, the authorization model of "user-role-permission" is constructed. In this model, there is generally a many-to-many relationship between users and roles, and between roles and permissions. (As shown below)
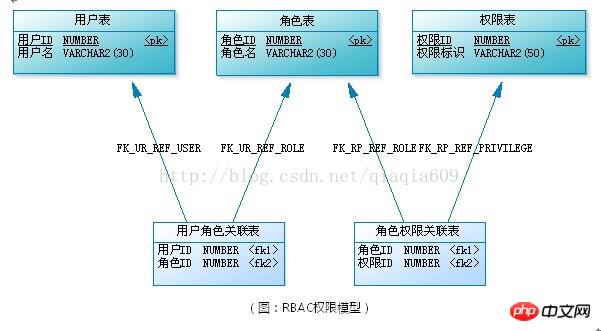
What is the role? It can be understood as a collection of a certain number of permissions and a carrier of permissions. For example: in a forum system, "super administrator" and "moderator" are roles. Moderators can manage posts in the forum, manage users in the forum, etc. These are permissions. To grant these permissions to a user, you do not need to grant permissions directly to the user. You can give the user the "moderator" role.
When the number of users is very large, it is very cumbersome to authorize (grant roles) to each user of the system one by one. At this time, you need to group users, and each user group has multiple users. In addition to authorizing users, you can also authorize user groups. In this way, all the permissions a user has are the sum of the permissions owned by the user personally and the permissions owned by the user group to which the user belongs. (The figure below shows the relationship between user groups, users and roles)

In the application system, permissions are expressed What? Operations on functional modules, deletion and modification of uploaded files, access to menus, and even visibility control of a button and a picture on the page are all Can fall within the scope of authority. Some permission designs will treat functional operations as one category, and files, menus, page elements, etc. as another category, thus forming a "user-role-permission-resource" authorization model. When doing data table modeling, functional operations and resources can be managed in a unified manner, that is, they are directly associated with the permission table, which may be more convenient and scalable. (See the picture below)

Please note that there is a column "Permission Type" in the permission table, we will take the value according to its value To distinguish which type of permission it is, for example, "MENU" means the access permission of the menu, "OPERATION" means the operation permission of the function module, "FILE" means the modification permission of the file, and "ELEMENT" means the permission of the page element. Visibility control etc.
There are two advantages to this design. First, there is no need to distinguish which are permission operations and which are resources (in fact, sometimes it is not easy to distinguish, such as the menu, should it be understood as a resource or a function module permission?). Second, it is convenient for expansion. When the system wants to control permissions on new things, I only need to create a new association table "Permission XX Association Table" and determine the permission type of such permissionsString .
It should be noted here that the permission table and the permission menu association table, the permission menu association table and the menu table are all in a one-to-one relationship. (The same applies to files, page permissions, functional operations, etc.). That is to say, every time a menu is added, a record must be inserted into each of these three tables at the same time. In this way, the permission menu association table is not needed and the permission table is directly associated with the menu table. At this time, a new column must be added to the permission table to save the ID of the menu. The permission table passes the "permission type" Use this ID to distinguish which record it is under.
Here, the complete design diagram of the extended model of the RBAC permission model is as follows:

As the system becomes larger and larger, in order to facilitate management, role groups can be introduced to classify and manage roles. Unlike user groups, role groups do not participate in authorization. For example: In the Permission Management module of a certain power grid system, roles are hung under the district bureau, and the district bureau can be used as a role group here, and it does not participate in permission distribution. In addition, in order to facilitate the management and search of each main table above, a tree structure can be used, such as menu tree, function tree, etc. Of course, these do not need to participate in permission allocation.
The above is expanded from the basic RBAC model, and the specific design must be adjusted according to the needs of the project business.
The above is the detailed content of Detailed graphic explanation of RBAC user rights management database design in thinkphp. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Comparative analysis of Oracle and DB2 database technology
Mar 11, 2024 am 09:54 AM
Comparative analysis of Oracle and DB2 database technology
Mar 11, 2024 am 09:54 AM
Oracle and DB2 are two well-known relational database management systems (RDBMS) that are widely used in enterprise applications. In this article, we will compare the two database technologies of Oracle and DB2 and analyze them in detail, including analysis of their characteristics, performance, functions and usage examples. 1. Overview of Oracle database technology Oracle is a relational database management system developed by Oracle Corporation of the United States. It is widely used in enterprise-level applications and has strong performance and stability.
 What is Discuz? Introduction to functions and features
Mar 03, 2024 am 10:18 AM
What is Discuz? Introduction to functions and features
Mar 03, 2024 am 10:18 AM
First, let’s explain what Discuz is. Discuz (formerly known as Discuz!) is an open source forum software developed by Chinese developers and is suitable for establishing online communities or forums. It provides rich features and flexible customization options, allowing website administrators to easily create a powerful community platform. Discuz's popularity is mainly due to its ease of use, stability and powerful social functions, which is suitable for websites of different sizes and needs. Next, let’s take a closer look at the functions and features of Discuz
 Login verification and user rights management issues encountered when using Vue development
Oct 09, 2023 am 10:12 AM
Login verification and user rights management issues encountered when using Vue development
Oct 09, 2023 am 10:12 AM
Login verification and user rights management issues encountered in Vue development require specific code examples. In the development process of Vue, login verification and user rights management are a very important issue. When a user logs into the system, he or she needs to be authenticated, and the pages and functions that the user can access are determined based on different permission levels. The following will be combined with specific code examples to introduce how to implement login verification and user rights management in Vue. Login verification Login verification is an important part of ensuring system security. In front-end development, we usually
 How to use Laravel to implement user rights management functions
Nov 02, 2023 pm 02:09 PM
How to use Laravel to implement user rights management functions
Nov 02, 2023 pm 02:09 PM
How to use Laravel to implement user rights management functions With the development of web applications, user rights management has become more and more important in many projects. Laravel, as a popular PHP framework, provides many powerful tools and functions for handling user rights management. This article will introduce how to use Laravel to implement user rights management functions and provide specific code examples. Database design First, we need to design a database model to store the relationship between users, roles and permissions. To make things easier we will make
 Research on solutions to database design problems encountered in development using MongoDB technology
Oct 08, 2023 pm 05:53 PM
Research on solutions to database design problems encountered in development using MongoDB technology
Oct 08, 2023 pm 05:53 PM
Exploring solutions to database design problems encountered in the development of MongoDB technology Abstract: With the rapid development of big data and cloud computing, database design is particularly important in software development. This article will discuss common database design issues encountered during development and introduce MongoDB solutions through specific code examples. Introduction: In the software development process, database design is a key link. Traditional relational databases have some performance and scalability issues when processing large-scale data. And MongoD
 Redundant Field Issues in Database Design: Best Practices in PHP Programming
Jun 22, 2023 am 11:02 AM
Redundant Field Issues in Database Design: Best Practices in PHP Programming
Jun 22, 2023 am 11:02 AM
With the popularity of the Internet and the increasing number of application scenarios, database design has become an extremely important issue. In database design, redundant fields are a very important issue. Redundant fields refer to duplicate or unnecessary fields that appear when designing the database. Although redundant fields can improve query efficiency and speed to a certain extent, they also waste storage space, increase maintenance difficulty, and even affect data consistency and security. Therefore, in PHP programming, certain best practices should be followed to solve the problems caused by redundant fields.
 How to use PHP to develop a simple user rights management function
Sep 25, 2023 pm 12:30 PM
How to use PHP to develop a simple user rights management function
Sep 25, 2023 pm 12:30 PM
How to use PHP to develop a simple user rights management function Introduction: With the development of the Internet, user rights management functions are becoming more and more important. PHP, as a popular server-side scripting language, is widely used to develop dynamic websites. Using PHP to develop a simple user rights management function can help website administrators flexibly control user access rights and protect the security of the website. This article will introduce how to use PHP to implement such functionality and provide specific code examples. 1. Database design First, we need
 Implementing Role-Based Access Control (RBAC): Using PHP and RBAC
Jun 20, 2023 pm 10:39 PM
Implementing Role-Based Access Control (RBAC): Using PHP and RBAC
Jun 20, 2023 pm 10:39 PM
With the popularity of Internet applications, we hope to protect data within the application to ensure that sensitive data is not misused or stolen. One of the solutions is to use role-based access control (RBAC). Role-based access control (RBAC) is an access control model based on the relationship between users and roles. The core idea of this model is to link the user's role to the access control operation, rather than linking the access control operation directly to the user. This approach improves the flexibility of access control,





