How to configure the environment for bee-box LDAP injection
1. Overview
According to my learning process, I must know what the model and vulnerability principles of my web attack are. Now I have encountered an unpopular situation. I saw it for the first time. When I came to LDAP, I discovered an unpopular one (authorized) during a penetration test of a state-owned enterprise, which aroused my interest in it.
The concept of LDAP:
Full name: Lightweight Directory AccessProtocolt, Features: I won’t talk about the protocol, it’s too esoteric, it can be understood as a The database that stores data is special in that it is a tree-like database. First of all, the name of this database is equivalent to the root of the tree (i.e. DB = dc), and then all the nodes passing through from the root of the tree to a certain leaf node are called Branches (ou) and finally reaches the leaf node (uid) you are looking for. As shown in the figure below:
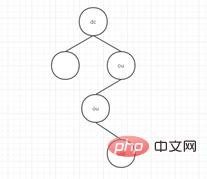
To be more specific, name each node and go through the diagram again, dc= root, fork 1 ou = database, fork 2 ou= mysql, leaf node uid = user.
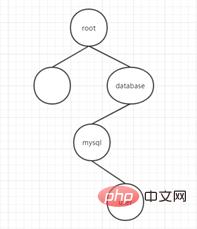
Then describe it in language: dn:cn =user,ou = database,ou = mysql,dc = root
dn identifies a record and describes it A detailed path of data is obtained, which is called "base DN". Through this record, a leaf node can be found conveniently and quickly. From the figure, LDAP can clearly divide the node area, that is, what is the parent node of the node, what are the child nodes, and extended to practical applications, what is the superior department of the department, and who are the employees of the department? , if used internally by the enterprise, it can clearly describe where each employee belongs.
Let’s first look at a case of server segment configuration:
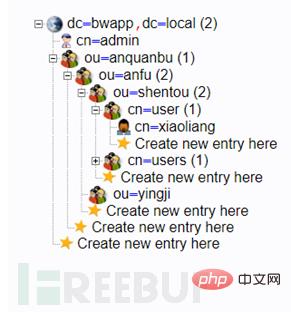
Assume that the name of a company is bwapp, and the CEO who manages this company is called admin.
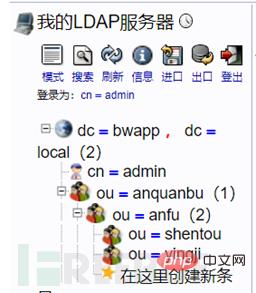
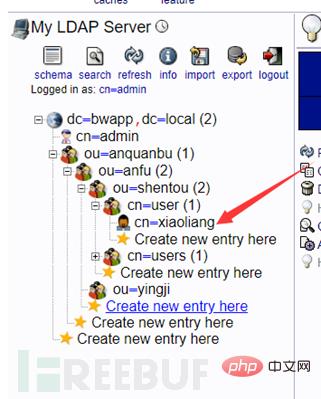
Now the CEO wants to add a new department to the company, called the security department (anquanbu). Under the security department is the security department (anfu). The security department is divided into penetration testing (sentou) and emergency response. (yingji) two teams, then Xiaoliang (xiaoliang) is in the infiltration team, and Xiaoming (xiaoming) is in the emergency team.
The configured directory structure is as shown below
2. LDAP configuration based on Bee-Box (Linux)
First find A relatively easy to configure LDAP architecture, OpenLDAP phpLDAPadmin is recommended here.
The steps are as follows:
First enter the following two installation commands:
sudo apt-getupdate
sudo apt-getinstall slapd ldap-utils
During the installation process, you will be asked to select and confirm the LDAP administrator password
sudodpkg-reconfigure slapd
This command needs to configure some ldap things. The following is a comparison between Chinese and English And screenshot
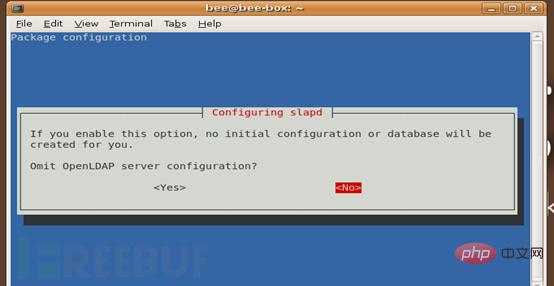
1. OpenLDAP server configuration is omitted? No
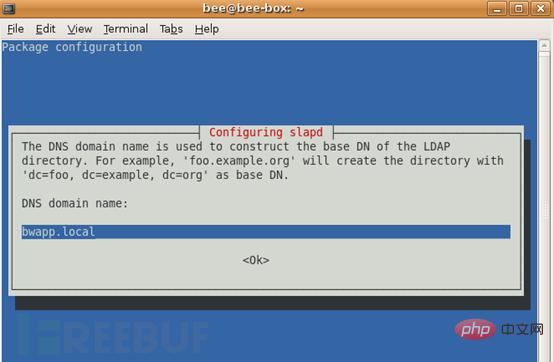
2. DNS domain name?
This option will determine the basic structure of the directory path. Read the message to find out how this will be achieved. Even if you don't own the actual domain, you can choose any value you want. However, this tutorial assumes you have the appropriate server domain name, so you should use that. Here for the bwapp shooting range, set it to bwapp.local
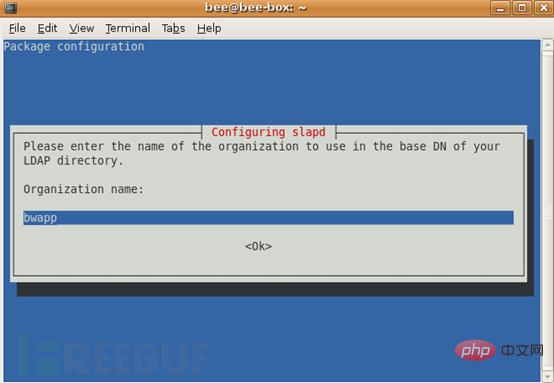
3. Organization name?
We use bwapp
4. Administrator password? Enter the security password twice
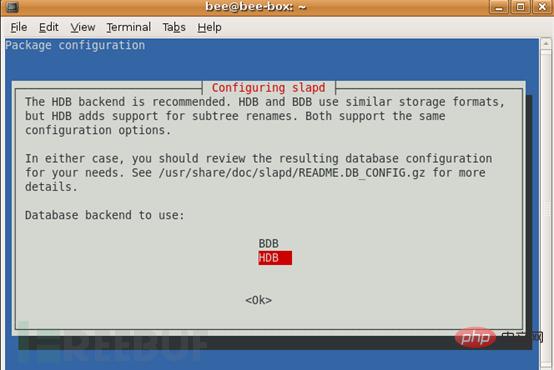
5. Database backend? HDB
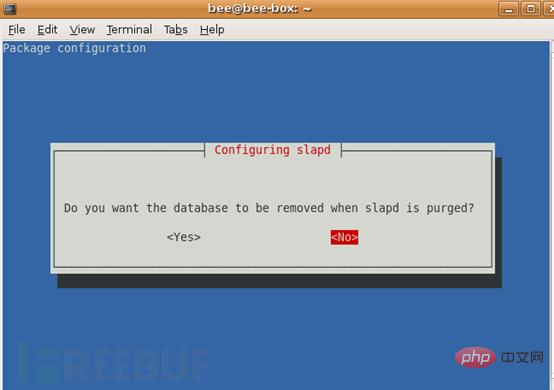
#5. Delete the database when clearing slapd? No
#6. Move the old database? Yes
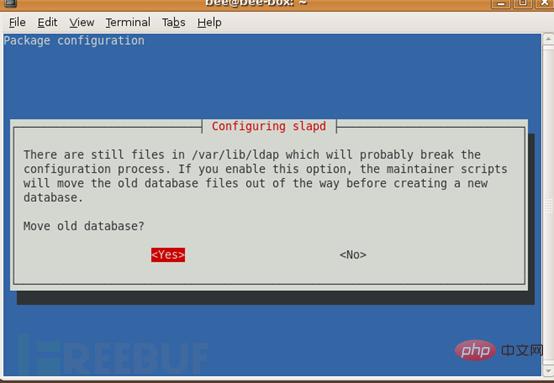
#7. Allow LDAPv2 protocol? No
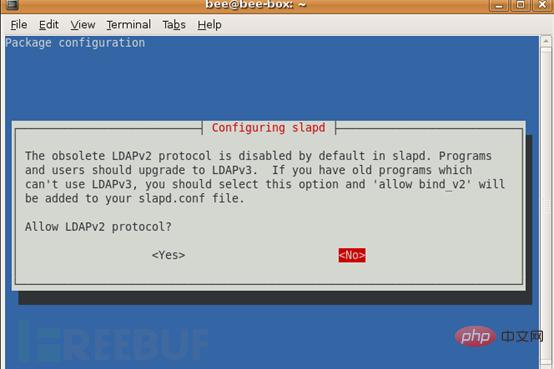
At this point the initial configuration is complete, open the LDAP port on the firewall so that external clients can connect:
sudo ufw allow ldap

Test whether the LDAP connection to ldapwhoami is successful, the connection should return the username we connected to:
ldapwhoami -H ldap:// -x
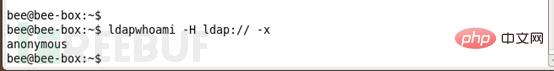
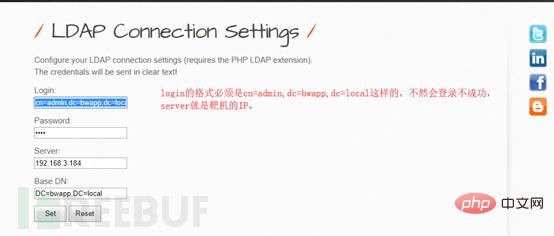
Access the phpLDAPadmin of the virtual machine from the host
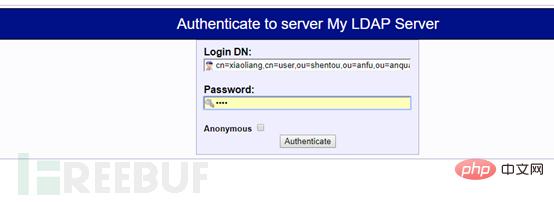
https://virtual machine IP /phpldapadmin/
Enter the password to log in.
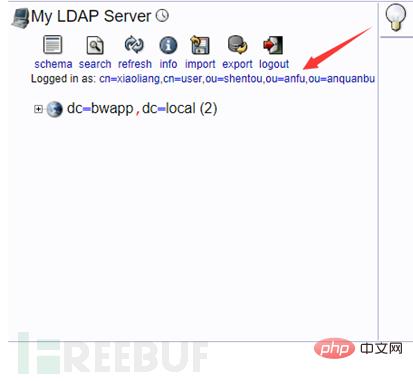
Login successful

Then the configuration on the server is as follows
The following configuration They are all translated into Chinese using the Google Translate plug-in.
First create the security department:

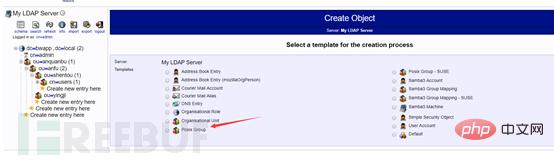
Select the organizational unit
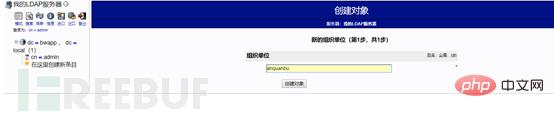
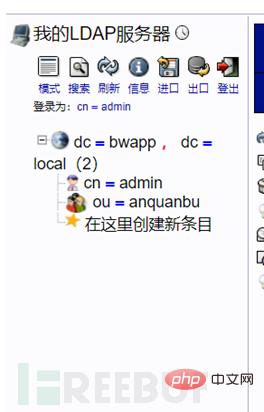
Create the object
Then create the sub-department of the security department, security (anfu)
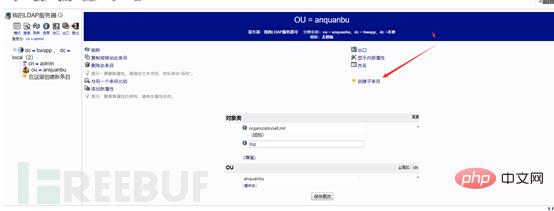
Create the sub-department Entry
The steps are the same as above
Created successfully
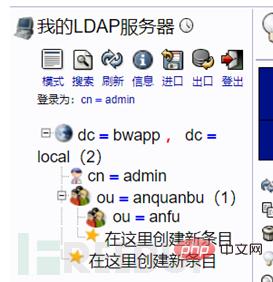
Then create penetration (shentou) and emergency (yingji) under the security server
The steps are the same as above
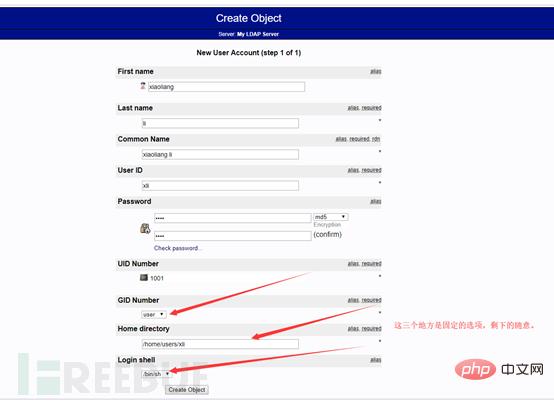
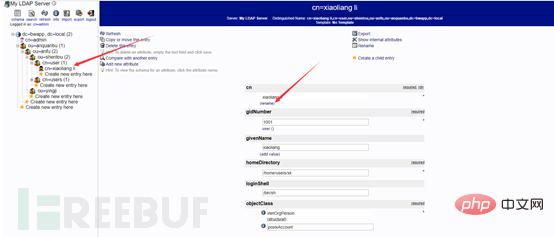
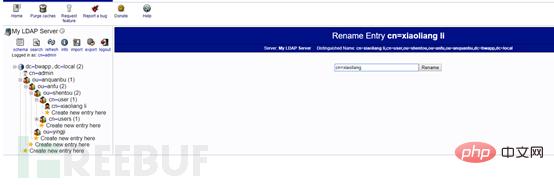
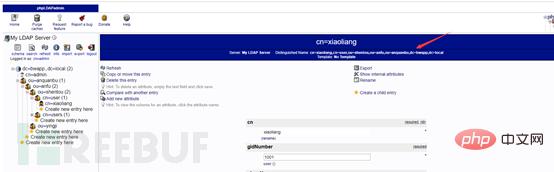
Create employees Li Xiaoliang (xiaoliang) and Wang Xiaoming (xiaoming) for penetration (shentou) and emergency (yingji) respectively
The steps to create personnel are as follows. The above are the steps to create organizational departments.
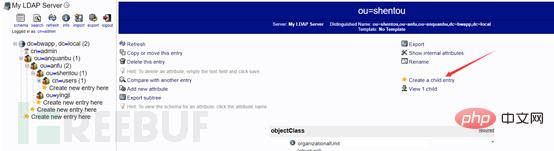
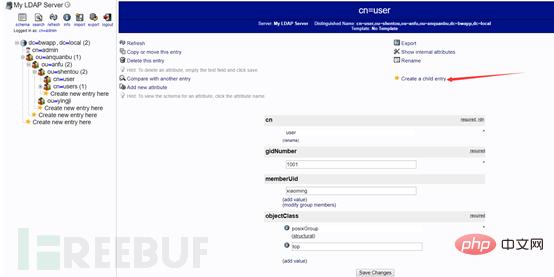
First create the user account xiaoliang under the penetration group
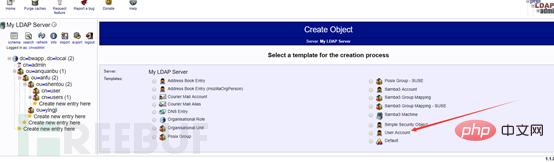
phpMyAdmin. To create a user, you need to create a user group first. If there is no There is no way to create users in this user group. The process of creating a user group is as follows:
Create sub-entry
Create user group
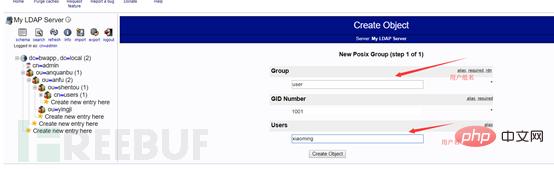
Then create a user under the user group
The above is the detailed content of How to configure the environment for bee-box LDAP injection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to understand LDAP injection
May 22, 2023 pm 09:47 PM
How to understand LDAP injection
May 22, 2023 pm 09:47 PM
1. LDAP injection LDAP (Light Directory Access Portocol) is a lightweight directory access protocol based on the X.500 standard. It provides services and protocols for accessing directory databases. It is often used to form directory services with directory databases. The directory is a professional distributed database optimized for query, browsing and search. It organizes data in a tree structure, similar to the file directory in Linux/Unix systems. Data that is not modified frequently, such as public certificates, security keys, and company physical device information, is suitable for storage in the directory. LDAP can be understood as a search protocol, which is similar to SQL and has query syntax, but also has the risk of injection attacks. LDAP injection refers to the client
 How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
If the essence of sql injection is to splice strings, then the essence of everything that can be injected is to splice strings. LDAP injection is no exception as a kind of injection. What is more interesting is that it is splicing parentheses (sql injection is also concatenates parentheses, but it is more conventional to say that it concatenates strings). In the environment configuration chapter, the configuration of the ldap environment in bee-box has been discussed in great detail. The shooting range practice chapter is more about the connection process between php and ldap, the introduction of the special functions used in the middle, and some techniques for splicing parentheses. Let’s first talk about the login process of the ldap shooting range in bwapp: First, this is an LDAP login interface, the URL is http://192.168.3.184/bW
 How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
1. Overview According to my learning process, I must know what the model and vulnerability of my web attack are. Now I have encountered an unexpected situation. The first time I saw LDAP was during a penetration test in a state-owned enterprise. I found an unpopular one (authorized) and piqued my interest in it. The concept of LDAP: Full name: Lightweight Directory Access Protocol (Lightweight Directory Access Protocol), features: I won’t talk about the protocol, it’s too esoteric, it can be understood as a database for storing data, its special feature is that it is a tree A database in the form of a database. First, the name of the database is equivalent to the root of the tree (i.e. DB=dc), and then the process from the root to a leaf node is
 Solution to PHP Fatal error: Call to undefined function ldap_bind()
Jun 22, 2023 pm 11:37 PM
Solution to PHP Fatal error: Call to undefined function ldap_bind()
Jun 22, 2023 pm 11:37 PM
When developing web applications using PHP, we often need to use LDAP authentication to protect application access. However, in some cases, when we try to use PHP's LDAP functionality to implement authentication, we may encounter the following error message: "PHPFatalerror:Calltoundefinedfunctionldap_bind()". This error message usually occurs when an application calls the ldap_bind() function
 Using LDAP for user authentication in PHP
Jun 20, 2023 pm 10:25 PM
Using LDAP for user authentication in PHP
Jun 20, 2023 pm 10:25 PM
LDAP (LightweightDirectoryAccessProtocol) is a protocol for accessing distributed directory services. It can be used for tasks such as user authentication, authorization, account maintenance, and data storage. In PHP applications, LDAP can be used as a powerful authentication mechanism to provide powerful authentication and authorization functions for applications. This article will introduce how to use LDAP for user authentication in PHP. The specific content includes: Installation and configuration L
 How to use Nginx to protect against LDAP injection attacks
Jun 10, 2023 pm 08:19 PM
How to use Nginx to protect against LDAP injection attacks
Jun 10, 2023 pm 08:19 PM
With the increase in network security vulnerabilities, LDAP injection attacks have become a security risk faced by many websites. In order to protect website security and prevent LDAP injection attacks, some security measures need to be used. Among them, Nginx, as a high-performance web server and reverse proxy server, can provide us with a lot of convenience and protection. This article will introduce how to use Nginx to prevent LDAP injection attacks. LDAP injection attack LDAP injection attack is an attack method targeting the LDAP database. The attacker
 How to protect against LDAP injection vulnerabilities using PHP
Jun 24, 2023 am 10:40 AM
How to protect against LDAP injection vulnerabilities using PHP
Jun 24, 2023 am 10:40 AM
As network security issues receive more and more attention, more and more programmers are beginning to pay attention and learn how to prevent code from being attacked. Among them, common attack methods include SQL injection, XSS, CSRF, etc. However, there is another common attack method that is underestimated: LDAP injection vulnerabilities. This article will introduce the principle of this attack method and how to use PHP to prevent LDAP injection vulnerabilities. LDAP introduction LDAP (LightweightDirectoryAccessProtocol)
 How to use PHP and LDAP to implement user group management and authorization
Jun 25, 2023 am 08:22 AM
How to use PHP and LDAP to implement user group management and authorization
Jun 25, 2023 am 08:22 AM
As the scale of enterprises and business needs continue to expand, user group management and authorization have become an essential part. LDAP (Lightweight Directory Access Protocol), as a directory service protocol widely used in enterprise networks, provides an efficient way to achieve user group management and authorization. This article will introduce how to use PHP and LDAP to implement user group management and authorization. 1. What is LDAP LDAP is a lightweight directory access protocol that is widely used as a directory service protocol in enterprise networks. LDAP is client/server based






