What are the basic principles of network security review?
Basic principles: 1. "Real-name principle". When operators sign an agreement with users or confirm the provision of services, they require users to provide real identity information. 2. "Interconnection Principle", realizing interconnection is not only the need for the development of my country's Internet industry, but also the need to safeguard the interests of consumers. 3. "Principles of Critical Data Assessment and Management"; 4. "Principles of Protecting Personal Privacy"; 5. "Firewall Principles". Operators should strengthen the management of information released by users. If any illegal information is found, they should immediately stop transmitting the information and take measures to Eliminate and other disposal measures to prevent the spread of information.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
Network security is of great concern to everyone. Network security involves many people. For this reason, the country has also introduced a network security law to ensure the safety of everyone’s network information. Cybersecurity must also adhere to the basic principles of review in the Cybersecurity Law to ensure that the information and interests of individuals and businesses in the cyberspace are not infringed upon.
Basic principles of network security review
1. Principle of real-name system
Network operators are When users handle network access, domain name registration services, handle fixed-line, mobile phone and other network access procedures, or provide users with information release services, they should require users to provide their true identity information when signing an agreement with the user or confirming the provision of services. If users do not provide their true identity information, network operators are not allowed to provide relevant services.
2. Principle of interconnection
“The state supports the research and development of safe and convenient electronic identity authentication technology, and promotes mutual recognition and universal use of different electronic identity authentication technologies. ".
In the field of Internet information technology in my country, beggar-thy-neighbor and unfair competition phenomena occur from time to time. On the one hand, this shows that my country's Internet field is a relatively competitive field. On the other hand, it also shows that some Internet operators use their own technical advantages to engage in unfair practices by blocking or deleting other Internet operators' information or software. compete.
Achieving interconnection is not only a need for the development of my country's Internet industry, but also a need for safeguarding the interests of consumers. Because of this, it is necessary to clearly stipulate in the form of law that Internet operators must consider interconnection issues in the process of developing software and providing Internet information services and take all measures to achieve seamless network connections.
3. Principles of critical data assessment and management
Operators of critical information infrastructure should store citizens’ personal information collected and generated during operations within the territory of the People’s Republic of China and other important data; if it is indeed necessary to store overseas or provide it to overseas organizations or individuals due to business needs, a security assessment shall be conducted in accordance with the methods formulated by the national network information department in conjunction with relevant departments of the State Council.
Operators of critical information infrastructure should conduct inspections and assessments of the security and possible risks of their networks on their own or by entrusting professional institutions to do so at least once a year, and propose network security monitoring and assessment status and improvement measures. Report and submit it to the relevant departments responsible for the security protection of critical information infrastructure.
4. Principles of protecting personal privacy
The draft law further strengthens the basic principles of Internet information protection on the basis of summarizing the implementation of the decision on the protection of personal information online. The principle clearly requires that "departments that are legally responsible for the supervision and management of Internet network security must strictly keep citizens' personal information, privacy and business secrets that they learn in the performance of their duties strictly confidential, and must not leak, sell or illegally provide them to others."
5. Firewall Principle
"Network operators should strengthen the management of information released by users. If they find that laws or administrative regulations prohibit the release or transmission of information, they should immediately Stop transmitting the information, take disposal measures such as elimination, prevent the spread of the information, save relevant records, and report to the relevant competent authorities."
"Electronic information sent by electronic information publishers and application software provided by application software providers must not be equipped with malicious programs, and must not contain information that is prohibited from being published or transmitted by laws and administrative regulations."
What impact will the coming of the Cybersecurity Law have on individuals and businesses
1. The protection of personal information will be more clear
According to the "38th Statistical Report on China's Internet Development" by the China Internet Network Information Center, as of the end of June 2016, the number of Internet users in China reached 710 million, and the Internet penetration rate reached 51.7%, of which mobile Internet users Reaching 656 million, network security issues cannot be taken lightly.
The Cybersecurity Law has clear provisions on the protection of personal information, such as “network operators shall not leak, tamper with, or damage the personal information they collect” and “any individual or organization shall not steal or obtain personal information in other illegal ways” , shall not illegally sell or illegally provide personal information to others”, etc.
Zuo Xiaodong, deputy director of the China Information Security Research Institute, pointed out that protecting personal information is an important aspect of current network work. Although relevant departments have previously had some policies and regulations, they are generally scattered and unsystematic. Such a system is needed. Superior method.
Li Yi, deputy director of the "Internet" Research and Consultation Center of the Internet Society of China, said that in the future, online chat records and email exchanges can be retained as evidence for evidence collection, making it easier to trace network disputes and security issues. This has greatly improved the confidence of netizens in online consumption life. He gave an analogy. If an individual user downloads and uses an APP on a mobile phone, resulting in the leakage of personal information, in the past, he could not complain to the application provider that provided the service, but the cybersecurity law provides a clear legal basis, "This means that in the future Lawsuits involving the Internet field may become increasingly difficult to fight.”
On the other hand, the Cybersecurity Law proposes that “network operators handle network access and domain name registration services for users, handle fixed-line telephone calls, mobile phone calls, etc. For Internet access procedures such as telephone calls, or to provide users with information release, instant messaging and other services, users should be required to provide their true identity information." The "Internet real-name system" has also been clarified in legal form. This provides a legal basis for curbing today's chaos such as the wanton spread of online rumors and the proliferation of online violence.
Zuo Xiaodong believes that from the perspective of combating crime and safeguarding national security, the online real-name system proposed this time has a wider scope than the previous telephone real-name system, and its principle of "anonymity in the front office and real name in the backend" is also sufficient Protect personal privacy. For example, individuals can be anonymous when posting online, but when law enforcement is involved, the background can track and investigate individuals.
2. Increased entry threshold and security capability requirements for enterprises
In the opinion of industry experts, the development of the Internet at this stage requires setting thresholds and no longer " "Growing wildly"; this threshold is security, and the Cybersecurity Law is the "gate to security".
Zhu Wei, deputy director of the Communication Law Research Center of China University of Political Science and Law, pointed out that the cybersecurity law has specific provisions on the security qualifications, internal technology, systems, etc. of enterprises, which will serve as a measure of the development of Internet companies.
At the same time, the Cybersecurity Law also puts forward higher requirements for Internet companies. In particular, large Internet companies are now regarded as basic information platforms, such as Alibaba, Baidu, Tencent, etc., with hundreds of millions of users, and these companies should assume corresponding obligations. Li Yi believes that Internet companies must have technical capabilities that match their basic information platforms, such as responding to hacker attacks and avoiding user losses. At the same time, there must also be relevant legal provisions to regulate the "overlord clauses" of large companies.
In general, the Cybersecurity Law will raise the market access threshold for Internet companies and put forward higher requirements for development and operation. Small and medium-sized enterprises that do not have security technology capabilities may be more likely to be eliminated in the future.
It is urgent to strengthen network security. To maintain network security, we need to implement the basic principles of the Network Security Law, increase network management and control, screen out some bad information, and ensure the purity of the network environment. However, in general, to ensure network security, it is not enough to adhere to the law. It is more important to consider every network participant. Actively maintaining network security is also a more important guarantee for everyone's interests.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What are the basic principles of network security review?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
![WLAN expansion module has stopped [fix]](https://img.php.cn/upload/article/000/465/014/170832352052603.gif?x-oss-process=image/resize,m_fill,h_207,w_330) WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
If there is a problem with the WLAN expansion module on your Windows computer, it may cause you to be disconnected from the Internet. This situation is often frustrating, but fortunately, this article provides some simple suggestions that can help you solve this problem and get your wireless connection working properly again. Fix WLAN Extensibility Module Has Stopped If the WLAN Extensibility Module has stopped working on your Windows computer, follow these suggestions to fix it: Run the Network and Internet Troubleshooter to disable and re-enable wireless network connections Restart the WLAN Autoconfiguration Service Modify Power Options Modify Advanced Power Settings Reinstall Network Adapter Driver Run Some Network Commands Now, let’s look at it in detail
 How to solve win11 DNS server error
Jan 10, 2024 pm 09:02 PM
How to solve win11 DNS server error
Jan 10, 2024 pm 09:02 PM
We need to use the correct DNS when connecting to the Internet to access the Internet. In the same way, if we use the wrong dns settings, it will prompt a dns server error. At this time, we can try to solve the problem by selecting to automatically obtain dns in the network settings. Let’s take a look at the specific solutions. How to solve win11 network dns server error. Method 1: Reset DNS 1. First, click Start in the taskbar to enter, find and click the "Settings" icon button. 2. Then click the "Network & Internet" option command in the left column. 3. Then find the "Ethernet" option on the right and click to enter. 4. After that, click "Edit" in the DNS server assignment, and finally set DNS to "Automatic (D
 Fix 'Failed Network Error' downloads on Chrome, Google Drive and Photos!
Oct 27, 2023 pm 11:13 PM
Fix 'Failed Network Error' downloads on Chrome, Google Drive and Photos!
Oct 27, 2023 pm 11:13 PM
What is the "Network error download failed" issue? Before we delve into the solutions, let’s first understand what the “Network Error Download Failed” issue means. This error usually occurs when the network connection is interrupted during downloading. It can happen due to various reasons such as weak internet connection, network congestion or server issues. When this error occurs, the download will stop and an error message will be displayed. How to fix failed download with network error? Facing “Network Error Download Failed” can become a hindrance while accessing or downloading necessary files. Whether you are using browsers like Chrome or platforms like Google Drive and Google Photos, this error will pop up causing inconvenience. Below are points to help you navigate and resolve this issue
 Fix: WD My Cloud doesn't show up on the network in Windows 11
Oct 02, 2023 pm 11:21 PM
Fix: WD My Cloud doesn't show up on the network in Windows 11
Oct 02, 2023 pm 11:21 PM
If WDMyCloud is not showing up on the network in Windows 11, this can be a big problem, especially if you store backups or other important files in it. This can be a big problem for users who frequently need to access network storage, so in today's guide, we'll show you how to fix this problem permanently. Why doesn't WDMyCloud show up on Windows 11 network? Your MyCloud device, network adapter, or internet connection is not configured correctly. The SMB function is not installed on the computer. A temporary glitch in Winsock can sometimes cause this problem. What should I do if my cloud doesn't show up on the network? Before we start fixing the problem, you can perform some preliminary checks:
 What should I do if the earth is displayed in the lower right corner of Windows 10 when I cannot access the Internet? Various solutions to the problem that the Earth cannot access the Internet in Win10
Feb 29, 2024 am 09:52 AM
What should I do if the earth is displayed in the lower right corner of Windows 10 when I cannot access the Internet? Various solutions to the problem that the Earth cannot access the Internet in Win10
Feb 29, 2024 am 09:52 AM
This article will introduce the solution to the problem that the globe symbol is displayed on the Win10 system network but cannot access the Internet. The article will provide detailed steps to help readers solve the problem of Win10 network showing that the earth cannot access the Internet. Method 1: Restart directly. First check whether the network cable is not plugged in properly and whether the broadband is in arrears. The router or optical modem may be stuck. In this case, you need to restart the router or optical modem. If there are no important things being done on the computer, you can restart the computer directly. Most minor problems can be quickly solved by restarting the computer. If it is determined that the broadband is not in arrears and the network is normal, that is another matter. Method 2: 1. Press the [Win] key, or click [Start Menu] in the lower left corner. In the menu item that opens, click the gear icon above the power button. This is [Settings].
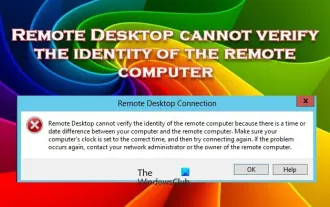 Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Remote Desktop cannot authenticate the remote computer's identity
Feb 29, 2024 pm 12:30 PM
Windows Remote Desktop Service allows users to access computers remotely, which is very convenient for people who need to work remotely. However, problems can be encountered when users cannot connect to the remote computer or when Remote Desktop cannot authenticate the computer's identity. This may be caused by network connection issues or certificate verification failure. In this case, the user may need to check the network connection, ensure that the remote computer is online, and try to reconnect. Also, ensuring that the remote computer's authentication options are configured correctly is key to resolving the issue. Such problems with Windows Remote Desktop Services can usually be resolved by carefully checking and adjusting settings. Remote Desktop cannot verify the identity of the remote computer due to a time or date difference. Please make sure your calculations
 How to enable/disable Wake on LAN in Windows 11
Sep 06, 2023 pm 02:49 PM
How to enable/disable Wake on LAN in Windows 11
Sep 06, 2023 pm 02:49 PM
Wake on LAN is a network feature on Windows 11 that allows you to remotely wake your computer from hibernation or sleep mode. While casual users don't use it often, this feature is useful for network administrators and power users using wired networks, and today we'll show you how to set it up. How do I know if my computer supports Wake on LAN? To use this feature, your computer needs the following: The PC needs to be connected to an ATX power supply so that you can wake it from sleep mode remotely. Access control lists need to be created and added to all routers in the network. The network card needs to support the wake-up-on-LAN function. For this feature to work, both computers need to be on the same network. Although most Ethernet adapters use
 2024 CSRankings National Computer Science Rankings Released! CMU dominates the list, MIT falls out of the top 5
Mar 25, 2024 pm 06:01 PM
2024 CSRankings National Computer Science Rankings Released! CMU dominates the list, MIT falls out of the top 5
Mar 25, 2024 pm 06:01 PM
The 2024CSRankings National Computer Science Major Rankings have just been released! This year, in the ranking of the best CS universities in the United States, Carnegie Mellon University (CMU) ranks among the best in the country and in the field of CS, while the University of Illinois at Urbana-Champaign (UIUC) has been ranked second for six consecutive years. Georgia Tech ranked third. Then, Stanford University, University of California at San Diego, University of Michigan, and University of Washington tied for fourth place in the world. It is worth noting that MIT's ranking fell and fell out of the top five. CSRankings is a global university ranking project in the field of computer science initiated by Professor Emery Berger of the School of Computer and Information Sciences at the University of Massachusetts Amherst. The ranking is based on objective





