Introduction to encryption of hashlib module
Used for encryption-related operations, 3.x replaced the md5 module and sha module, mainly providing SHA1, SHA224, SHA256, SHA384, SHA512, MD5 algorithms
import hashlib m = hashlib.md5() m.update(b"hello") print(m.hexdigest()) m.update(b"It's me") print(m.hexdigest()) m.update(b"It's been a long time since we spoken.") print(m.hexdigest()) m2 = hashlib.md5() m2.update(b"helloIt's me") print(m2.hexdigest()) # 输出 5d41402abc4b2a76b9719d911017c592 64f69d95135bc13d4827f871b37f780f 0c9a83e10aa2f9e9629be61146db9cc2 64f69d95135bc13d4827f871b37f780f #第二个和第四个 md5值是相同的,所以第二个加密的是 helloIt'sme
print(m.digest()) #Binary format hash
print(len(m.hexdigest())) #Hexadecimal format hash# ######## sha1 ######## hash = hashlib.sha1() hash.update('admin') print(hash.hexdigest()) # ######## sha256 ######## hash = hashlib.sha256() hash.update('admin') print(hash.hexdigest()) # ######## sha384 ######## hash = hashlib.sha384() hash.update('admin') print(hash.hexdigest()) # ######## sha512 ######## hash = hashlib.sha512() hash.update('admin') print(hash.hexdigest())
Python also has a hmac module, which internally processes the key and content we create and then encrypts them.
Hash message authentication code, referred to as HMAC, is a message authentication code based on MAC (Message Authentication Code) authentication mechanism. When using HMAC, both parties in the message communication authenticate the message by verifying the authentication key K added to the message;
is generally used for message encryption in network communications, provided that both parties must first agree on the key. Just like the joint code, the message sender then uses the key to encrypt the message, and the receiver uses key + message plaintext to encrypt it again. The encrypted value is compared with the sender's value to see if it is equal, so that the authenticity of the message can be verified, and The sender's legitimacy.
import hmac
h = hmac.new("天王盖地虎".encode(encoding="utf-8"), "你是小松鼠".encode(encoding="utf-8"))
print(h.digest())
print(h.hexdigest())
#输出
b'fx\xad\xdd\x9e\xd6\xddcQN\x82c\xcd\xd9\x80-'
6678addd9ed6dd63514e8263cdd9802dThe above is the detailed content of Introduction to encryption of hashlib module. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1426
1426
 52
52
 1328
1328
 25
25
 1273
1273
 29
29
 1254
1254
 24
24
![WLAN expansion module has stopped [fix]](https://img.php.cn/upload/article/000/465/014/170832352052603.gif?x-oss-process=image/resize,m_fill,h_207,w_330) WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
If there is a problem with the WLAN expansion module on your Windows computer, it may cause you to be disconnected from the Internet. This situation is often frustrating, but fortunately, this article provides some simple suggestions that can help you solve this problem and get your wireless connection working properly again. Fix WLAN Extensibility Module Has Stopped If the WLAN Extensibility Module has stopped working on your Windows computer, follow these suggestions to fix it: Run the Network and Internet Troubleshooter to disable and re-enable wireless network connections Restart the WLAN Autoconfiguration Service Modify Power Options Modify Advanced Power Settings Reinstall Network Adapter Driver Run Some Network Commands Now, let’s look at it in detail
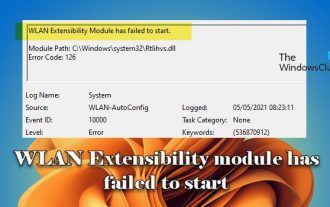 WLAN extensibility module cannot start
Feb 19, 2024 pm 05:09 PM
WLAN extensibility module cannot start
Feb 19, 2024 pm 05:09 PM
This article details methods to resolve event ID10000, which indicates that the Wireless LAN expansion module cannot start. This error may appear in the event log of Windows 11/10 PC. The WLAN extensibility module is a component of Windows that allows independent hardware vendors (IHVs) and independent software vendors (ISVs) to provide users with customized wireless network features and functionality. It extends the capabilities of native Windows network components by adding Windows default functionality. The WLAN extensibility module is started as part of initialization when the operating system loads network components. If the Wireless LAN Expansion Module encounters a problem and cannot start, you may see an error message in the event viewer log.
 Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Bitlocker is the default encryption technology for Windows operating systems. It is widely used on Windows, but some users prefer third-party solutions such as VeraCrypt. What many users of Bitlocker don't know is that it defaults to 128-bit encryption, even though 256-bit is available. Without going into too much detail about the differences; the core difference between AES 128-bit and 256-bit encryption is the length of the security key. Longer keys make brute force attacks more difficult. While the default is 128-bit, even Microsoft recommends 256-bit for better security. The problem is, most users probably don't know about the weaker defaults or how to change them. First, you might want to know W
 Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Microsoft previously provided dns encryption services for win11, but many users do not know how to use win11 encrypted dns. In fact, we only need to open the dns settings under network settings. Detailed tutorial on win11 encrypted dns: 1. First enter the disk and find the folder you want to encrypt. 2. Then open "Ethernet" on the right 3. Then find the DNS server allocation below and click "Edit" 4. After changing "Auto (DHCP)" to "Manual", open "IPv4" below 5. After turning it on, enter "8.8.8.8" in the preferred DNS 6. Then change the preferred DNS encryption to "Encryption only (DNS over HTTPS)" 7. After the changes are completed, click "Save" and you will find
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
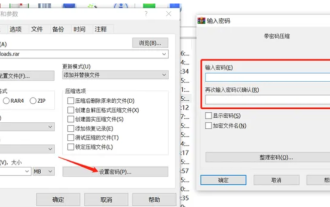 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
 Detailed explanation of how Ansible works
Feb 18, 2024 pm 05:40 PM
Detailed explanation of how Ansible works
Feb 18, 2024 pm 05:40 PM
The working principle of Ansible can be understood from the above figure: the management end supports three methods of local, ssh, and zeromq to connect to the managed end. The default is to use the ssh-based connection. This part corresponds to the connection module in the above architecture diagram; you can press the application type HostInventory (host list) classification is carried out in other ways. The management node implements corresponding operations through various modules. A single module and batch execution of a single command can be called ad-hoc; the management node can implement a collection of multiple tasks through playbooks. Implement a type of functions, such as installation and deployment of web services, batch backup of database servers, etc. We can simply understand playbooks as, the system passes




