10 recommended articles about the md5() function() function
The application scenarios for generating unique IDs are very common, such as temporary cache file names, temporary variables, temporary security codes, etc. The uniqid() function generates a unique ID based on the current time in microseconds. Since generating a unique ID is tied to microsecond time, the uniqueness of the ID is very reliable. The generated unique ID returns a string that is 13 strings long by default. If the prefix of the unique ID is not defined, it can return up to 23 strings long. If combined with the md5() function, the reliability of the generated unique ID will be higher. , the biggest advantage of this generated ID over random ID is that it can be sorted, especially some values that need to be stored in the database. 1. The function prototype string uniqid ([string prefix [, bool more_entropy]]) can define the prefix and length of the unique ID. 2. The version is compatible with PHP 3, PHP 4, PHP 5. 3. Basic usage and example of the function 1, generate a unique ID< ;?php echo&am
1. uniqid() function 10 recommended content

Introduction: Application scenarios for generating unique IDs are very common, such as temporary cache file names, temporary variables, temporary security codes, etc. The uniqid() function generates a unique ID based on the current time in microseconds. Since generating a unique ID is tied to microsecond time, the uniqueness of the ID is very reliable. The generated unique ID returns a string that is 13 strings long by default. If the prefix of the unique ID is not defined, it can return up to 23 strings long. If combined with the md5() function, the reliability of the generated unique ID will be higher. , the biggest advantage of this generated ID over random ID is...
2. Summary of the definition and usage of the md5() function in php

Introduction: PHP encryption function—md5() function encryption What is the MD5() function? The MD5() function is the MD5 hash value of the calculator string, using the MD5 algorithm. The full name of MD5 is Message-Digest Algorithm 5. Its function is to calculate data information of different lengths into a 128-bit value through a series of algorithms. The value is to turn a byte string of any length into a large integer of a certain length. Note that what is said here is "byte string", not "string", because this transformation is only related to the value of the byte, and has nothing to do with the character set or encoding...
3. PHP encryption function—md5() function encryption example usage

##Introduction: MD5 The () function is the MD5 hash value of the calculator string, using the MD5 algorithm. The full name of MD5 is Message-Digest Algorithm 5. Its function is to calculate data information of different lengths into a 128-bit value through a series of algorithms. Numeric value is to convert a byte string of any length into a large integer of a certain length. Note that this is "byte string", not "string", because this transformation is only related to the byte value and has nothing to do with the character set or encoding method.
4. php object-oriented problem
Introduction: {code...} My question is: Why does the md5() function report an error when used as shown above? ? Can't the attributes in PHP object-oriented use PHP's own methods? ? ?
5. vbscript.encode PHP encryption functions md5, crypt, base64_encode and other usage introduction
Introduction: vbscript .encode:vbscript.encode PHP encryption functions md5, crypt, base64_encode and other usage introduction: The irreversible encryption functions are: md5(), crypt() md5() is used to calculate MD5 hash. The syntax is: string md5(string str); crypt() encrypts the string using UNIX's standard encryption DES module. This is a one-way encryption function and cannot be decrypted. To compare strings, place the first two characters of the encrypted string in the salt parameter, and then compare the encrypted strings. The syntax is: string cry
Introduction:: PHP encryption technology: I learned some knowledge about PHP encryption a few days ago. Now I will summarize several encryption forms in PHP: Md5() encryption algorithm Crypt() encryption algorithm Sha1() encryption algorithm URL encoding Encryption technology Base64 encoding encryption technology Md5() encryption algorithm Syntax: string md5(string $str [, bool $raw_output = false ] ) $str: original string Optional (not commonly used
7. Introduction to the use of php's encryption functions md5, crypt, base64_encode, etc._PHP tutorial
Introduction: Introduction to the use of php's encryption functions md5, crypt, base64_encode, etc. . The irreversible encryption functions are: md5(), crypt() md5() is used to calculate MD5 hash. The syntax is: string md5(string str); crypt() encrypts the string using the UNIX standard encryption DES module. Yes
##8. PHP5.3 language features_PHP tutorial
Introduction: PHP5.3 language features performance. Improved the overall performance of PHP 5.3 by 5 - 15% md5() is 10-15% faster Better stack implementation in the engine Constants moved to read-only memory Exception handling process improvement (simplified,
9. php function notes_PHP tutorial
Introduction: PHP function notes. String function: htmlspecialchars() md5() number_format() preg_match () trim() printf() str_replace() strip_tags() explode() implode() sprintf strpos strrchr strrpos strstr substr
10. php md5 encryption function reference detailed explanation_ PHP tutorial
Introduction: Detailed reference for php md5 encryption function. Many PHP developers will use this md() encryption function, but some friends may not know the reference. Today Let’s take a look at the parameters of the md5() function. Syntax md5(string,raw) md5() function
[Related Q&A recommendations]:
How to find the implementation of Python’s hashlib (see screenshot)?
Encryption and decryption-Java encryption, What do bc and cc in decryption mean?
The above is the detailed content of 10 recommended articles about the md5() function() function. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Bitlocker is the default encryption technology for Windows operating systems. It is widely used on Windows, but some users prefer third-party solutions such as VeraCrypt. What many users of Bitlocker don't know is that it defaults to 128-bit encryption, even though 256-bit is available. Without going into too much detail about the differences; the core difference between AES 128-bit and 256-bit encryption is the length of the security key. Longer keys make brute force attacks more difficult. While the default is 128-bit, even Microsoft recommends 256-bit for better security. The problem is, most users probably don't know about the weaker defaults or how to change them. First, you might want to know W
 Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Microsoft previously provided dns encryption services for win11, but many users do not know how to use win11 encrypted dns. In fact, we only need to open the dns settings under network settings. Detailed tutorial on win11 encrypted dns: 1. First enter the disk and find the folder you want to encrypt. 2. Then open "Ethernet" on the right 3. Then find the DNS server allocation below and click "Edit" 4. After changing "Auto (DHCP)" to "Manual", open "IPv4" below 5. After turning it on, enter "8.8.8.8" in the preferred DNS 6. Then change the preferred DNS encryption to "Encryption only (DNS over HTTPS)" 7. After the changes are completed, click "Save" and you will find
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
 PHP calculates MD5 hash of file
Mar 21, 2024 pm 01:42 PM
PHP calculates MD5 hash of file
Mar 21, 2024 pm 01:42 PM
This article will explain in detail about PHP calculating the MD5 hash of files. The editor thinks it is quite practical, so I share it with you as a reference. I hope you can gain something after reading this article. PHP calculates the MD5 hash of a file MD5 (MessageDigest5) is a one-way encryption algorithm that converts messages of arbitrary length into a fixed-length 128-bit hash value. It is widely used to ensure file integrity, verify data authenticity and create digital signatures. Calculating the MD5 hash of a file in PHP PHP provides multiple methods to calculate the MD5 hash of a file: Use the md5_file() function. The md5_file() function directly calculates the MD5 hash value of the file and returns a 32-character
 Common network communication and security problems and solutions in C#
Oct 09, 2023 pm 09:21 PM
Common network communication and security problems and solutions in C#
Oct 09, 2023 pm 09:21 PM
Common network communication and security problems and solutions in C# In today's Internet era, network communication has become an indispensable part of software development. In C#, we usually encounter some network communication problems, such as data transmission security, network connection stability, etc. This article will discuss in detail common network communication and security issues in C# and provide corresponding solutions and code examples. 1. Network communication problems Network connection interruption: During the network communication process, the network connection may be interrupted, which may cause
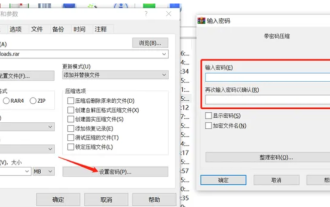 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below






