AES/RSA encryption mechanism
During HTTP communication between the server and the terminal device, packets are often captured by the network. , decompilation (Android APK decompilation tool) and other technologies to obtain the HTTP communication interface address and parameters. In order to ensure the security of the information, we use the AES+RSA combination. Method to encrypt and decrypt interface parameters.
1. Regarding the RSA encryption mechanism: the public key is used to encrypt the data, and the private key is used to decrypt the data. The public key and the private key are generated at the same time. , one-to-one correspondence. For example: A has a public key, and B has a public key and a private key. After A encrypts the data with the public key, B can decrypt it with the private key and public key.
#2. AES encryption is also called symmetric encryption: After A uses the password to AES encrypt the data, B uses the same password to AES decrypt the ciphertextSpecific operation method. : 1. Use openssl mode to enter the relevant 2. At this time, it is assumed that the Android client has the public key Public
Key, and the server has the public key. PublicKey and private key PrivateKey.
3. Android sends a request to the server: Android randomly generates a Byte[] random password, assuming RandomKey="123456", and uses the AES algorithm toJson data Use encryption.
4. But at this moment, the server does not know what the client's RandomKey is, so it needs to pass the Randomkey to the server at the same time, otherwise the server cannot decrypt the Json data through AES. But if the request is sent directly, The RandomKey will be exposed, so the RandomKey must be irreversibly encrypted with RSA. 5. Android will use Randomkey for AES encryption and RandomKey for RSA encryption to send the data to the server through HTTP. The request is completed. 6. The server receives the AES-encrypted Json data and the Rsa-encrypted RandomKey data. 7. The server decrypts the encrypted RandomKey using the private key. Get the original RandomKey generated by Android. 8. Use the original RandomKey to perform AES symmetric decryption of the encrypted Json data. At this point, the original Json data sent from the Android side has been obtained. Perform regular server business operations, and then encrypt the returned data with AES through RandomKey on the Android side, and then the Response is returned. 9. After the Android terminal receives the Response data, it can directly perform AES decryption using the RandomKey generated locally. You can view the detailed flow chart below.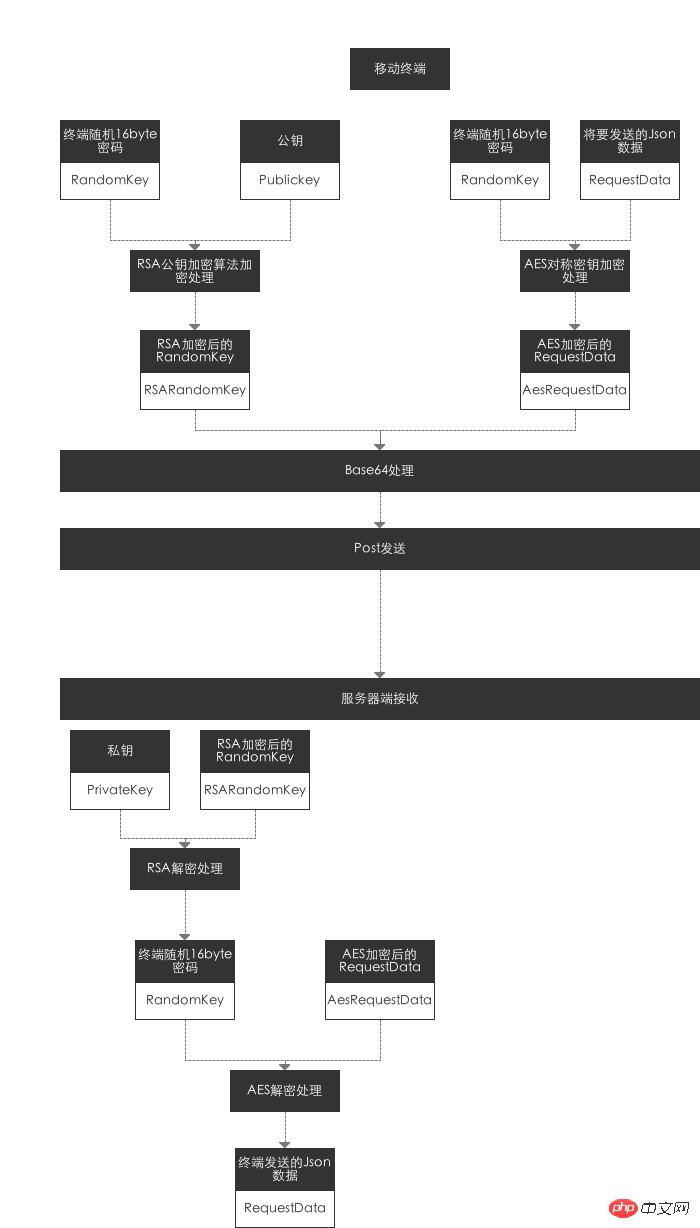
Notes:
1. During the actual development process, it was found that RSA and AES have different ciphertext generation standards and are incompatible with IOS. IOS requires a different public key in the RSA algorithm than JAVA. For detailed solutions, please see: 2. AES encryption cannot use KEYs exceeding 128Byte, because versions above jdk1.7 do not support KEYs exceeding 128Byte. Summary: From a performance perspective, the entire client from sending encrypted data to decrypting and getting the original data returned does not exceed300ms (Iphone4 and Centos Java server transmission test). This plan does not use TOKEN, but it may be used in the future. How to update the public key also needs to continue to be improved.
The above is the detailed content of AES/RSA encryption mechanism. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to perform AES encryption and decryption operations in Java
May 08, 2023 pm 10:34 PM
How to perform AES encryption and decryption operations in Java
May 08, 2023 pm 10:34 PM
1. Background knowledge In cryptography, encryption algorithms are divided into one-way encryption and two-way encryption. Symmetric encryption means that the same key is used for encryption and decryption, including AES encryption, DES encryption, etc. Asymmetric encryption refers to the use of different keys for encryption and decryption, including RSA encryption, etc. One-way encryption includes digest algorithms such as MD5 and SHA, which are irreversible. Two-way encryption includes symmetric encryption and asymmetric encryption. Two-way encryption is reversible, and the key to the ciphertext exists. 2. Introduction to AES AES: Advanced Encryption Standard (Advanced Encryption Standard) is a block encryption standard adopted by the U.S. federal government and is currently the most popular symmetric encryption algorithm. It is a new generation block encryption algorithm used to replace DES.
 Use Python to implement RSA encryption and decryption
Apr 14, 2023 pm 02:13 PM
Use Python to implement RSA encryption and decryption
Apr 14, 2023 pm 02:13 PM
Yesterday I saw an English article [1] that showed how to use Python to implement the RSA algorithm. The logic of the code is the same as the previous article Understanding the RSA Algorithm. Friends who are not familiar with RSA can read the article Understanding the RSA Algorithm, which faces What is RSA, the mathematical principles of RSA are explained, and a simple example is given. It can be said that this is the easiest article to understand RSA on Quanzhihu (this comes from readers' comments). I ran the code provided in English and found that it could not encrypt Chinese, so I modified the encryption and decryption functions to support Chinese encryption and decryption. Today’s article will share how to use Python to implement the RSA encryption and decryption process to help you establish
 How to use PHP and GMP to perform RSA encryption and decryption algorithms for large integers
Jul 28, 2023 pm 05:25 PM
How to use PHP and GMP to perform RSA encryption and decryption algorithms for large integers
Jul 28, 2023 pm 05:25 PM
How to use PHP and GMP to perform RSA encryption and decryption algorithm for large integers. The RSA encryption algorithm is an asymmetric encryption algorithm that is widely used in the field of data security. It implements the process of public key encryption and private key decryption based on two particularly large prime numbers and some simple mathematical operations. In the PHP language, the calculation of large integers can be realized through the GMP (GNUMultiplePrecision) library, and the encryption and decryption functions can be realized by combining the RSA algorithm. This article will introduce how to use PHP and GMP libraries to
 How SpringBoot implements RAS+AES automatic interface decryption
May 20, 2023 pm 04:04 PM
How SpringBoot implements RAS+AES automatic interface decryption
May 20, 2023 pm 04:04 PM
1. Let’s talk about a cliché about accident interface safety. Before the Chinese New Year, I made a small H5 game about airplane battles. In the infinite mode, the user’s points need to be saved, because the Body used to pass parameters is visible. For the sake of interface safety, I The front-end and I agreed that the parameters to be passed are: the user's unlimited mode points + "a number we agreed upon" + the sum of the user id. After encrypting with Base64, the request is sent to the server and I decrypt it to get the user's unlimited mode points; as follows: { "integral":"MTExMTM0NzY5NQ==",} But during the Chinese New Year, the operation suddenly came to me and told me that the infinite mode points ranking list score was wrong: This is very strange, the second place is only one
 How to implement RSA encryption and decryption algorithms using PHP and GMP
Jul 28, 2023 pm 11:54 PM
How to implement RSA encryption and decryption algorithms using PHP and GMP
Jul 28, 2023 pm 11:54 PM
How to use PHP and GMP to implement RSA encryption and decryption algorithm RSA encryption algorithm is an asymmetric encryption algorithm that is widely used in the field of information security. In practical applications, it is often necessary to use programming languages to implement RSA encryption and decryption algorithms. PHP is a commonly used server-side scripting language, and GMP (GNUMultiplePrecision) is a high-precision mathematical calculation library that can help us perform large number operations required in the RSA algorithm. This article will introduce how to use PHP and GMP
 Detailed explanation of AES256 encryption technology in PHP and its application in the framework
Jun 09, 2023 pm 12:25 PM
Detailed explanation of AES256 encryption technology in PHP and its application in the framework
Jun 09, 2023 pm 12:25 PM
With the development and popularization of the Internet, data security has received more and more attention. Encryption technology is a very effective means during data transmission and storage. Encryption can ensure the confidentiality and integrity of data. In PHP, AES256 encryption technology is a very popular encryption method. This article will introduce in detail its application method in the framework. Introduction to AES256 encryption technology AES (Advanced Encryption Standard) is the advanced encryption standard and is a modern popular encryption method.
 PHP implements RSA asymmetric encryption technology
Jun 18, 2023 am 09:34 AM
PHP implements RSA asymmetric encryption technology
Jun 18, 2023 am 09:34 AM
RSA asymmetric encryption technology is one of the most popular and secure encryption methods currently. As a widely used programming language, PHP also has unique advantages in implementing RSA encryption. This article will introduce readers to how to use PHP to implement RSA asymmetric encryption technology. 1. What is the RSA algorithm? The RSA algorithm is an asymmetric encryption technology. It is usually used for data encryption and digital signatures. Its security is mainly based on a number theory problem, namely the difficulty of factoring very large integers in a very short time. RSA algorithm encrypted stream
 How to write RSA encryption algorithm using Python?
Sep 20, 2023 pm 01:21 PM
How to write RSA encryption algorithm using Python?
Sep 20, 2023 pm 01:21 PM
How to write RSA encryption algorithm using Python? Introduction: RSA is an asymmetric encryption algorithm that is widely used in the field of information security. In modern communications, the RSA encryption algorithm is commonly used to encrypt and decrypt sensitive data. This article will introduce how to use Python to write the RSA encryption algorithm and provide specific code examples. Install the Python library Before you start writing the RSA encryption algorithm, you need to install the Python encryption library. It can be installed using the following command: pipinstallrsa generate






