How does RFID technology enhance security measures?

Radio frequency identification (RFID) technology dates back to the early 1980s, but it has only been widely adopted in recent years.
This efficient, cost-effective and innovative technology plays a subtle but powerful role in organizations around the world, with benefits more immediate than the security enhancements it provides. This article will take a closer look at how RFID technology can be used to enhance enterprise security.
Strong Access Security
Ensuring that all organizations should properly protect their facilities are safe and secure. Failure to do so may result in loss of assets and put employees and customers at risk. With RFID readers, businesses can ensure that only authorized individuals have access to their websites. Think of RFID access cards as a modern solution to keys. With just one card, individuals can easily access all authorized parts of the facility without having to carry heavy keys. Additionally, if an employee's access needs to be changed, that access can be granted with just a few clicks of a button.
Reduce reliance on security personnel
There are many ways to control access to a facility. Often, the burden of maintaining site security falls almost entirely on security personnel. However, security personnel cannot monitor all parts of the building at the same time. Additionally, even the most well-trained and vigilant security personnel make mistakes from time to time. Leveraging RFID technology can help reduce the burden on security teams. Once the technology is integrated, there is another safety check. Think of RFID technology as a division of responsibility for site security. There is no need to pay too much attention to who is accessing the equipment, because this check will be taken care of by RFID.
Access Data
RFID technology not only ensures that only authorized personnel have access to a facility, it also tells who visited the facility and when. This information can be used to help combat insider crime, investigate on-site incidents, and make data-backed strategic decisions.
For example, senior management can inspect access data to identify employees who may be responsible for hazardous work practices. Likewise, if an internal theft or other unwelcome event occurs, the data generated by the RFID reader can be used to determine who was on site at the time of the incident.
RFID data can be used to determine employee-related decisions. For example, it can analyze how many people are on site and when, which could lead to shifts in members' working patterns.
Visual Deterrence
To prevent unwanted intrusions, using RFID access control as a line of defense provides a valuable line of defense. In addition to this, it also provides a visual deterrent to potential criminals. In addition to security personnel and off-street television cameras, RFID access control machines convey the facility's seriousness about access control. This applies to employees, too - if every door is equipped with RFID security, you know you're unlikely to get away with a crime within, and shouldn't even try.
Update Software
Once cut, the key remains the same forever. If that key is copied by an outsider, it could gain access to the facility until the locks are updated, by which time it may be too late.
RFID devices are like modern dynamic keys, always one step ahead of potential criminals. Manufacturers are always at the forefront of these activities, constantly developing new models to help enhance system robustness.
Overall Business Security
RFID readers alone cannot protect a business from all known threats. However, it can help play a vital role in the overall security of an organization. From keeping unauthorized personnel at bay, providing insightful data about who enters a site when, and automating processes that could be compromised by employee error, RFID technology has been proven to make facilities more robust and secure within the space. People are safer.
It’s easy to install and configure, and as RFID technology continues to improve, it’s time for businesses of all sizes to consider incorporating this technology into their operations.
The above is the detailed content of How does RFID technology enhance security measures?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Best AI Art Generators (Free & Paid) for Creative Projects
Apr 02, 2025 pm 06:10 PM
Best AI Art Generators (Free & Paid) for Creative Projects
Apr 02, 2025 pm 06:10 PM
The article reviews top AI art generators, discussing their features, suitability for creative projects, and value. It highlights Midjourney as the best value for professionals and recommends DALL-E 2 for high-quality, customizable art.
 Getting Started With Meta Llama 3.2 - Analytics Vidhya
Apr 11, 2025 pm 12:04 PM
Getting Started With Meta Llama 3.2 - Analytics Vidhya
Apr 11, 2025 pm 12:04 PM
Meta's Llama 3.2: A Leap Forward in Multimodal and Mobile AI Meta recently unveiled Llama 3.2, a significant advancement in AI featuring powerful vision capabilities and lightweight text models optimized for mobile devices. Building on the success o
 Best AI Chatbots Compared (ChatGPT, Gemini, Claude & More)
Apr 02, 2025 pm 06:09 PM
Best AI Chatbots Compared (ChatGPT, Gemini, Claude & More)
Apr 02, 2025 pm 06:09 PM
The article compares top AI chatbots like ChatGPT, Gemini, and Claude, focusing on their unique features, customization options, and performance in natural language processing and reliability.
 Is ChatGPT 4 O available?
Mar 28, 2025 pm 05:29 PM
Is ChatGPT 4 O available?
Mar 28, 2025 pm 05:29 PM
ChatGPT 4 is currently available and widely used, demonstrating significant improvements in understanding context and generating coherent responses compared to its predecessors like ChatGPT 3.5. Future developments may include more personalized interactions and real-time data processing capabilities, further enhancing its potential for various applications.
 Top AI Writing Assistants to Boost Your Content Creation
Apr 02, 2025 pm 06:11 PM
Top AI Writing Assistants to Boost Your Content Creation
Apr 02, 2025 pm 06:11 PM
The article discusses top AI writing assistants like Grammarly, Jasper, Copy.ai, Writesonic, and Rytr, focusing on their unique features for content creation. It argues that Jasper excels in SEO optimization, while AI tools help maintain tone consist
 Choosing the Best AI Voice Generator: Top Options Reviewed
Apr 02, 2025 pm 06:12 PM
Choosing the Best AI Voice Generator: Top Options Reviewed
Apr 02, 2025 pm 06:12 PM
The article reviews top AI voice generators like Google Cloud, Amazon Polly, Microsoft Azure, IBM Watson, and Descript, focusing on their features, voice quality, and suitability for different needs.
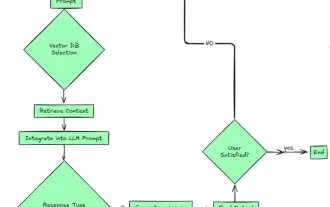 Top 7 Agentic RAG System to Build AI Agents
Mar 31, 2025 pm 04:25 PM
Top 7 Agentic RAG System to Build AI Agents
Mar 31, 2025 pm 04:25 PM
2024 witnessed a shift from simply using LLMs for content generation to understanding their inner workings. This exploration led to the discovery of AI Agents – autonomous systems handling tasks and decisions with minimal human intervention. Buildin
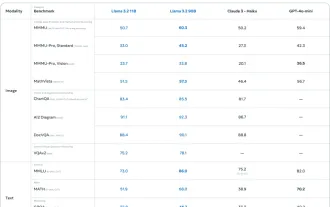 AV Bytes: Meta's Llama 3.2, Google's Gemini 1.5, and More
Apr 11, 2025 pm 12:01 PM
AV Bytes: Meta's Llama 3.2, Google's Gemini 1.5, and More
Apr 11, 2025 pm 12:01 PM
This week's AI landscape: A whirlwind of advancements, ethical considerations, and regulatory debates. Major players like OpenAI, Google, Meta, and Microsoft have unleashed a torrent of updates, from groundbreaking new models to crucial shifts in le






