 System Tutorial
System Tutorial
 Windows Series
Windows Series
 How to configure password-protected access to a shared folder on a local area network
How to configure password-protected access to a shared folder on a local area network
How to configure password-protected access to a shared folder on a local area network
In a modern collaborative environment, using LAN shared folders is crucial for team efficiency and resource sharing. However, in order to protect sensitive data, it is necessary to set an access password for the shared folder. This article provides a detailed tutorial on how to set a password for a shared folder. PHP editor Xiaoxin will take you step by step to understand the entire process to ensure that your shared folders are safe and reliable.
Setting method
1. First select the folder to be shared, right-click and select "Properties" in the option list.

#2. In the window interface that opens, switch to the "Share" option in the top.
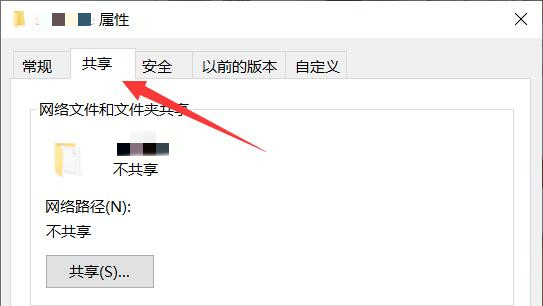
#3. Then click "Network and Sharing Center" below.
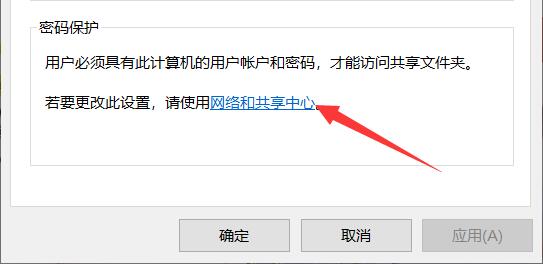
4. Then expand the "All Networks" option.
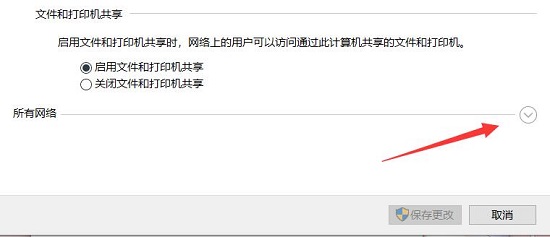
#5. Check "Password protected sharing" and click "Save changes".
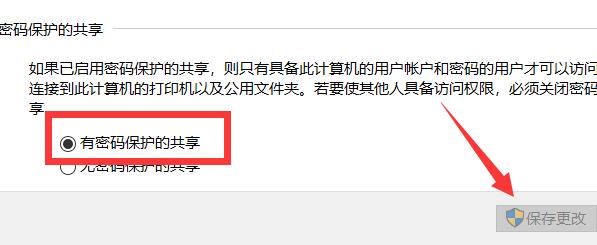
#6. Then right-click "This PC" on the desktop and select "Manage" in the option list.
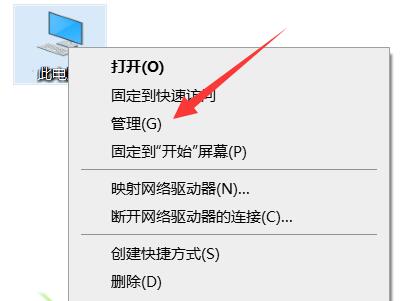
#7. After entering the new window interface, click "System Tools - Local Users and Groups - Users" in the left column, and then right-click "Guest" account on the side, select "Set Password" in the options list.
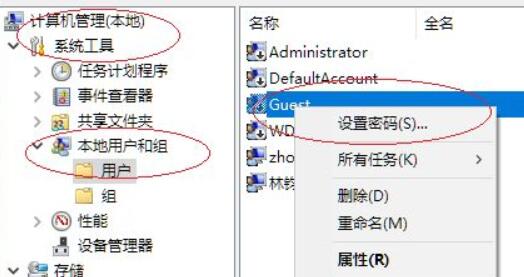
#8. Then in the pop-up window, set a suitable password and save it.
Extended reading
| File Management | |||
| The file has no associated application | Batch modify the file suffix name | Unable to access font folder | Change user folder name |
| Fix file system error | The shared folder requires a password | Crash when opening the shared folder | Folder shrink The thumbnail cannot be displayed |
| Cannot delete the folder | Close the shared folder | The file manager loads slowly | Solution to the file manager crash |
| gxxmiscutil.dll is missing and error message | Open the folder and keep loading in circles | xlive.dll is an invalid image | Change the image format |
The above is the detailed content of How to configure password-protected access to a shared folder on a local area network. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to connect Redmi Note13RPro to the computer?
May 09, 2024 pm 06:52 PM
How to connect Redmi Note13RPro to the computer?
May 09, 2024 pm 06:52 PM
The phone Redmi Note13RPro has been very popular recently. Many consumers have purchased this phone. However, many users are using this phone for the first time, so they don’t know how to connect the Redmi Note13RPro to the computer. In this regard, the editor is here to explain to you Detailed tutorial introduction is provided. How to connect Redmi Note13RPro to the computer? 1. Use a USB data cable to connect the Redmi phone to the USB interface of the computer. 2. Open the phone settings, click Options, and turn on USB debugging. 3. Open the device manager on your computer and find the mobile device option. 4. Right-click the mobile device, select Update Driver, and then select Automatically search for updated drivers. 5. If the computer does not automatically search for the driver,
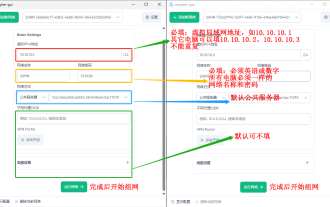 How to use EasyTier remote networking
Jun 19, 2024 am 10:14 AM
How to use EasyTier remote networking
Jun 19, 2024 am 10:14 AM
EasyTier is an open source, free, decentralized intranet penetration remote networking tool. It is an easy-to-use and feature-rich remote networking solution, suitable for remote office collaboration, game connection and other scenarios. The following is a brief introduction to how to use EasyTier remote networking. Download the easytier-gui program and install it. Download address: https://github.com/EasyTier/EasyTier Just set it up as shown above on the computer that needs to be networked. Virtual IPv4 address: required. For example, computer A is 10.10.10.1, B is 10.10.10.2, and C is 10.10.10.3. It cannot be repeated. (Such IP segments are available: 10.
 How to extract text from pictures on Redmi Note13RPro?
May 08, 2024 pm 10:00 PM
How to extract text from pictures on Redmi Note13RPro?
May 08, 2024 pm 10:00 PM
The Redmi Note13RPro mobile phone integrates a number of smart tools in terms of software functions. Among them, quickly and accurately extracting text content from pictures is one of them. The following editor will introduce to you how Redmi Note13RPro extracts text from pictures. How to extract text from pictures on Redmi Note13RPro? Use the Xiaomi QR code scanning function, open the QR code scanning application on your phone, click the picture icon, select a picture, and then click the "Recognize text" option on the right to successfully extract the text in the picture. Operate through mobile phone album. Find the picture for which text needs to be extracted in the mobile phone album, click "More" below the picture, and select "Extract Text". After successful recognition, you can copy or save the text as needed. Use WeChat mini programs. Open micro
 What is the value and use of icp coins?
May 09, 2024 am 10:47 AM
What is the value and use of icp coins?
May 09, 2024 am 10:47 AM
As the native token of the Internet Computer (IC) protocol, ICP Coin provides a unique set of values and uses, including storing value, network governance, data storage and computing, and incentivizing node operations. ICP Coin is considered a promising cryptocurrency, with its credibility and value growing with the adoption of the IC protocol. In addition, ICP coins play an important role in the governance of the IC protocol. Coin holders can participate in voting and proposal submission, affecting the development of the protocol.
 The difference between oracle database and mysql
May 10, 2024 am 01:54 AM
The difference between oracle database and mysql
May 10, 2024 am 01:54 AM
Oracle database and MySQL are both databases based on the relational model, but Oracle is superior in terms of compatibility, scalability, data types and security; while MySQL focuses on speed and flexibility and is more suitable for small to medium-sized data sets. . ① Oracle provides a wide range of data types, ② provides advanced security features, ③ is suitable for enterprise-level applications; ① MySQL supports NoSQL data types, ② has fewer security measures, and ③ is suitable for small to medium-sized applications.
 How to connect Redmi Note13RPro to TV?
May 09, 2024 pm 06:40 PM
How to connect Redmi Note13RPro to TV?
May 09, 2024 pm 06:40 PM
Redmi Note13RPro is a mobile phone with many functions. For example, connecting the mobile phone to the TV allows the TV's large screen to display the content on the mobile phone, bringing a more comfortable experience. If you want to know how to connect Redmi Note13RPro to the TV, then follow the editor to learn together. How to connect Redmi Note13RPro to TV? 1. Confirm that the TV and mobile phone are connected to the same wifi name, find the [Settings] function option on the mobile phone desktop, and click to open it. 2. After entering the settings, click to open the [More Connection Methods] option. 3. Find the [Wireless Display] option and click to open it. 4. Click on the [Turn on wireless display] option. If the TV and the mobile phone are connected under the same wifi name, the mobile phone will automatically scan for the wireless display.
 The difference between get and post in vue
May 09, 2024 pm 03:39 PM
The difference between get and post in vue
May 09, 2024 pm 03:39 PM
In Vue.js, the main difference between GET and POST is: GET is used to retrieve data, while POST is used to create or update data. The data for a GET request is contained in the query string, while the data for a POST request is contained in the request body. GET requests are less secure because the data is visible in the URL, while POST requests are more secure.
 Security Vulnerabilities and Solutions in PHP Development
May 09, 2024 pm 03:33 PM
Security Vulnerabilities and Solutions in PHP Development
May 09, 2024 pm 03:33 PM
Security Vulnerabilities and Solutions in PHP Development Introduction PHP is a popular server-side scripting language that is widely used in web development. However, like any software, PHP has some security vulnerabilities. This article will explore common PHP security vulnerabilities and their solutions. Common PHP security vulnerability SQL injection: allows an attacker to access or modify data in the database by entering malicious SQL code into a web form or URL. Cross-site scripting (XSS): allows an attacker to execute malicious script code in the user's browser. File Contains: Allows an attacker to load and execute remote files or sensitive files on the server. Remote Code Execution (RCE): allows attackers to execute arbitrary





