Can't allow access to camera and microphone in iPhone
Are you getting "Unable to allow access to camera and microphone" when trying to use the app? Typically, you grant camera and microphone permissions to specific people on a need-to-provide basis. However, if you deny permission, the camera and microphone will not work and will display this error message instead. Solving this problem is very basic and you can do it in a minute or two.
Fix 1 – Provide camera, microphone permissions
You can provide the necessary camera and microphone permissions directly in the settings.
Step 1 – Go to the Settings tab.
Step 2 – Open the Privacy & Security panel.
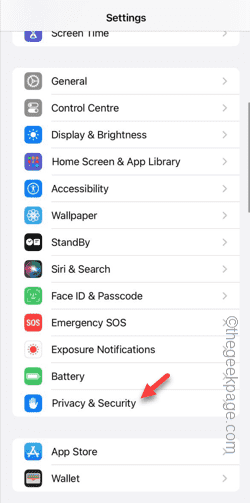
Step 3 – Turn on the “Camera” permission there.
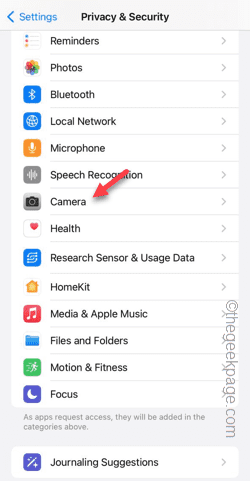
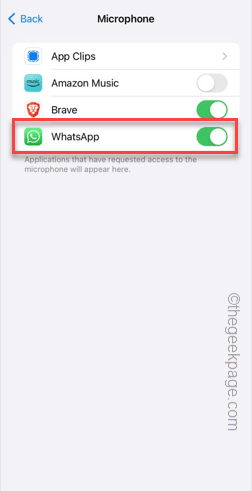
Step 4 – Inside, you will find a list of apps that have requested your phone’s camera permission.
Step 5 – Turn on the “Camera” permission for the specified app.
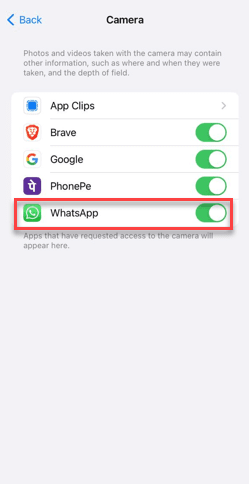
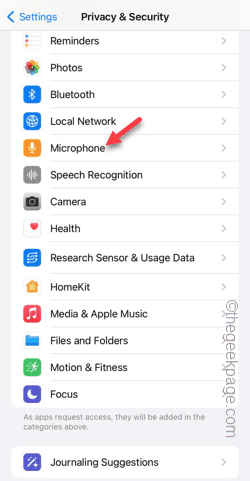
Step 6 – Go back to the main Privacy & Security tab.
Step 7 – After a while, turn on “Microphone”.
# Step 8 – Following the same process, you can allow camera, microphone permissions for other apps.
# Now open the app again and try to use the camera or record a reel in the app. You will no longer be faced with this message.
Fix 2 – Change App Settings
Change app settings directly from the Settings page.
Step 1 – Just go to Settings.
Step 2 – Instead, swipe down and find the app in the list to open its settings.

# Step 3 – Once in the app settings, make sure the Microphone and Camera settings are enabled.
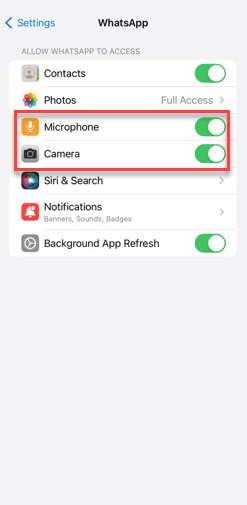
Now, if you see this message in multiple apps, you must also enable camera and microphone permissions for those apps
Fix 3 – Uninstall and reinstall the app
Another easy fix is to uninstall and reinstall the app. When it asks for camera and microphone permission, allow it.
Note – If you encounter this issue in WhatsApp, you should create a local backup of your account before uninstalling it.
Step 1 – Find the App on your phone screen or App Library.
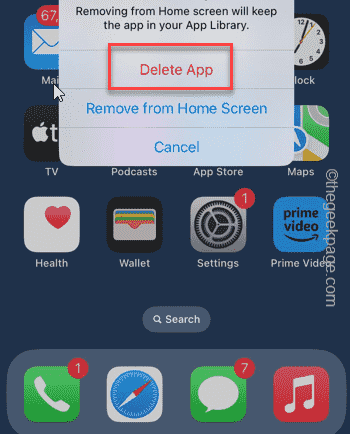
Step 2 – Then, press and hold the app and tap on “Delete App”.
Step 3 – Click on “Remove App” to delete the app.
Step 4 – After a while, open the App Store.
Step 5 – Reinstall the app on your phone.
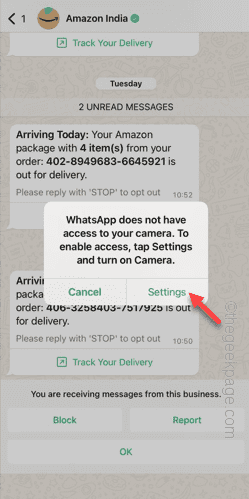
Step 6 – Try to access the camera from the app. It will display this message –
WhatsApp does not have access to your camera. To enable access, tap Settings and turn on Camera.
Step 7 – Tap on “Settings”.
Step 8 – Turn on “Camera” and “Microphone” permissions.
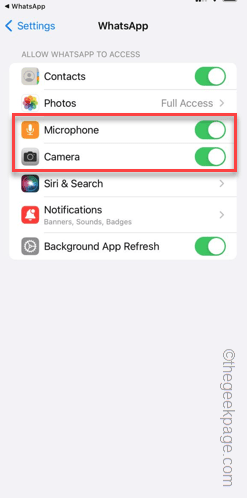
Return to the app after this and you can use the camera and microphone normally.
Check if this helps.
Fix 4 – Change content and privacy restrictions
If you still can’t use the camera and microphone in the app, you can change the content and privacy restrictions settings.
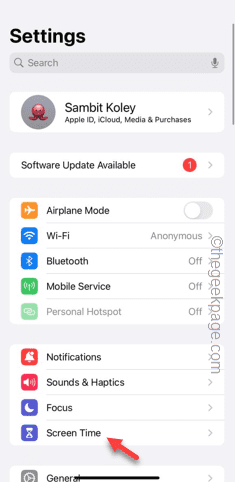
Step 1 – Open Settings and then Screen Time settings.
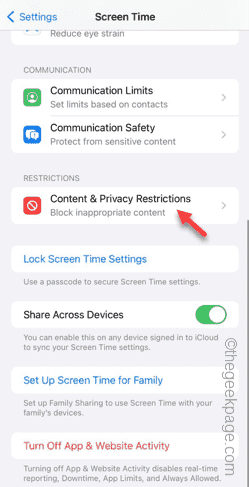
Step 2 – Find the “Content and Privacy Restrictions” module and open it.
Step 3 – Open Photos settings.
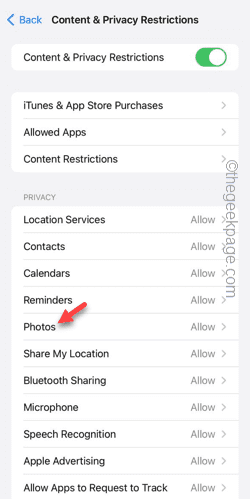
Step 4 – Set it to “Allow Changes”.
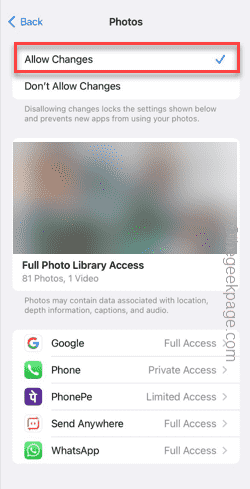
#Step 5 – Click the “Back” icon to enter the main content and privacy restrictions page.
Step 6 – This time, open the Microphone settings.
Step 7 – Select the “Allow changes” option.
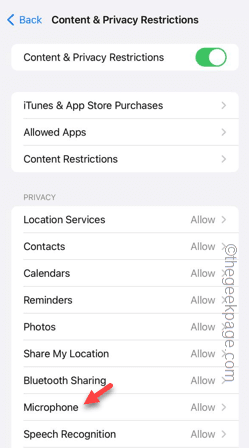
# After that, open the app and try to access the camera and microphone in the app.
This way, you can access these contents in the application without any problem.
The above is the detailed content of Can't allow access to camera and microphone in iPhone. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use sql if statement
Apr 09, 2025 pm 06:12 PM
How to use sql if statement
Apr 09, 2025 pm 06:12 PM
SQL IF statements are used to conditionally execute SQL statements, with the syntax as: IF (condition) THEN {statement} ELSE {statement} END IF;. The condition can be any valid SQL expression, and if the condition is true, execute the THEN clause; if the condition is false, execute the ELSE clause. IF statements can be nested, allowing for more complex conditional checks.
 Unable to log in to mysql as root
Apr 08, 2025 pm 04:54 PM
Unable to log in to mysql as root
Apr 08, 2025 pm 04:54 PM
The main reasons why you cannot log in to MySQL as root are permission problems, configuration file errors, password inconsistent, socket file problems, or firewall interception. The solution includes: check whether the bind-address parameter in the configuration file is configured correctly. Check whether the root user permissions have been modified or deleted and reset. Verify that the password is accurate, including case and special characters. Check socket file permission settings and paths. Check that the firewall blocks connections to the MySQL server.
 Multi-party certification: iPhone 17 standard version will support high refresh rate! For the first time in history!
Apr 13, 2025 pm 11:15 PM
Multi-party certification: iPhone 17 standard version will support high refresh rate! For the first time in history!
Apr 13, 2025 pm 11:15 PM
Apple's iPhone 17 may usher in a major upgrade to cope with the impact of strong competitors such as Huawei and Xiaomi in China. According to the digital blogger @Digital Chat Station, the standard version of iPhone 17 is expected to be equipped with a high refresh rate screen for the first time, significantly improving the user experience. This move marks the fact that Apple has finally delegated high refresh rate technology to the standard version after five years. At present, the iPhone 16 is the only flagship phone with a 60Hz screen in the 6,000 yuan price range, and it seems a bit behind. Although the standard version of the iPhone 17 will have a high refresh rate screen, there are still differences compared to the Pro version, such as the bezel design still does not achieve the ultra-narrow bezel effect of the Pro version. What is more worth noting is that the iPhone 17 Pro series will adopt a brand new and more
 Can mysql workbench connect to the sql server
Apr 08, 2025 pm 05:30 PM
Can mysql workbench connect to the sql server
Apr 08, 2025 pm 05:30 PM
No, MySQL Workbench cannot connect directly to SQL Server because it is only MySQL compatible. You need to use other tools or methods, such as using SQL Server Management Studio (SSMS), a common database client (such as DBeaver, DataGrip), or a command line tool (such as SQLCMD).
 Can mysql return json
Apr 08, 2025 pm 03:09 PM
Can mysql return json
Apr 08, 2025 pm 03:09 PM
MySQL can return JSON data. The JSON_EXTRACT function extracts field values. For complex queries, you can consider using the WHERE clause to filter JSON data, but pay attention to its performance impact. MySQL's support for JSON is constantly increasing, and it is recommended to pay attention to the latest version and features.
 How to configure zend for apache
Apr 13, 2025 pm 12:57 PM
How to configure zend for apache
Apr 13, 2025 pm 12:57 PM
How to configure Zend in Apache? The steps to configure Zend Framework in an Apache Web Server are as follows: Install Zend Framework and extract it into the Web Server directory. Create a .htaccess file. Create the Zend application directory and add the index.php file. Configure the Zend application (application.ini). Restart the Apache Web server.
 How to use Debian Apache logs to improve website performance
Apr 12, 2025 pm 11:36 PM
How to use Debian Apache logs to improve website performance
Apr 12, 2025 pm 11:36 PM
This article will explain how to improve website performance by analyzing Apache logs under the Debian system. 1. Log Analysis Basics Apache log records the detailed information of all HTTP requests, including IP address, timestamp, request URL, HTTP method and response code. In Debian systems, these logs are usually located in the /var/log/apache2/access.log and /var/log/apache2/error.log directories. Understanding the log structure is the first step in effective analysis. 2. Log analysis tool You can use a variety of tools to analyze Apache logs: Command line tools: grep, awk, sed and other command line tools.
 Summary of phpmyadmin vulnerabilities
Apr 10, 2025 pm 10:24 PM
Summary of phpmyadmin vulnerabilities
Apr 10, 2025 pm 10:24 PM
The key to PHPMyAdmin security defense strategy is: 1. Use the latest version of PHPMyAdmin and regularly update PHP and MySQL; 2. Strictly control access rights, use .htaccess or web server access control; 3. Enable strong password and two-factor authentication; 4. Back up the database regularly; 5. Carefully check the configuration files to avoid exposing sensitive information; 6. Use Web Application Firewall (WAF); 7. Carry out security audits. These measures can effectively reduce the security risks caused by PHPMyAdmin due to improper configuration, over-old version or environmental security risks, and ensure the security of the database.






