Mysql主从复制技术(亲测)_MySQL
bitsCN.com
Mysql主从复制技术(亲测)
开始配置:
第一步:创建复制帐号
每个slave使用标准的MySQL用户名和密码连接master。进行复制操作的用户会授予
REPLICATIONSLAVE权限。
用户名的密码都会存储在文本文件master.info中。假如,你想创建repl用户,如下
mysql> GRANT REPLICATION SLAVE, REPLICATION CLIENT ON *.* TO repl@'192.
168.1.%' IDENTIFIED BY '123456';
第二步:配置My.cnf
配置Master的My.cnf,该文件默认位置为/etc/my.cnf
接下来对master进行配置,包括打开二进制日志,指定唯一的servr ID。例如,在配置文件
加入如下值:
[mysqld]
server-id=1
log-bin=mysql-bin
重启mysql,service mysql restart ,
登录mysql -uroot -p
运行SHOW MASTER STATUS,输出如下:
+------------------+----------+--------------+------------------+
| File | Position | Binlog_Do_DB | Binlog_Ignore_DB |
+------------------+----------+--------------+------------------+
| mysql-bin.000002 | 106 | | |
+------------------+----------+--------------+------------------+
1 row in set (0.00 sec)
配置Slave的My.cnf,该文件默认位置为/etc/my.cnf
Slave的配置与master类似,你同样需要重启slave的MySQL。如下:
server-id = 2
log-bin = mysql-bin
relay_log = mysql-relay-bin
log_slave_updates = 1
read_only = 1
server-id是必须的,而且唯一。slave没有必要开启二进制日志,但是在一些情况下,必须
设置,例如,如果slave为其它slave的master,必须设置bin_log。在这里,我们开启了二进制
日志,而且显示的命名(默认名称为hostname,但是,如果hostname改变则会出现问题)。
relay_log配置中继日志,log_slave_updates表示slave将复制事件写进自己的二进制日志(后面会
看到它的用处)。
有些人开启了slave的二进制日志,却没有设置log_slave_updates,然后查看slave的数据是否改
变,这是一种错误的配置。所以,尽量使用read_only,它防止改变数据(除了特殊的线程)。但是,
read_only并是很实用,特别是那些需要在slave上创建表的应用。
重启mysql,service mysql restart ,
登录mysql -uroot -p
第三步:启动slave
接下来就是让slave连接master,并开始重做master二进制日志中的事件。你不应该用配置
文件进行该操作,而应该使用CHANGE MASTER TO语句,该语句可以完全取代对配置文件的修改,
而且它可以为slave指定不同的master,而不需要停止服务器。如下:
mysql>CHANGE MASTER TO MASTER_HOST='192.168.60.73',MASTER_USER='repl',MASTER_PASSWORD='123456',MASTER
_LOG_FILE='mysql-bin.000002',MASTER_LOG_POS=0;
MASTER_LOG_POS的值为0,因为它是日志的开始位置。然后,你可以用SHOW SLAVE STATUS
语句查看slave的设置是否正确:
mysql> SHOW SLAVE STATUS/G
*************************** 1. row ***************************
Slave_IO_State:
Master_Host: server1
Master_User: repl
Master_Port: 3306
Connect_Retry: 60
Master_Log_File: mysql-bin.000001
Read_Master_Log_Pos: 4
Relay_Log_File: mysql-relay-bin.000001
Relay_Log_Pos: 4
Relay_Master_Log_File: mysql-bin.000001
Slave_IO_Running: No
Slave_SQL_Running: No
...omitted...
Seconds_Behind_Master: NULL
Slave_IO_State, Slave_IO_Running, 和Slave_SQL_Running表明slave还没有开始复制过程。
日志的位置为4而不是0,这是因为0只是日志文件的开始位置,并不是日志位置。实际上,MySQL知
道的第一个事件的位置是4。
为了开始复制,你可以运行:
mysql> START SLAVE;
mysql> SHOW SLAVE STATUS/G
运行SHOW SLAVE STATUS查看输出结果:
*************************** 1. row ***************************
Slave_IO_State: Waiting for master to send event
Master_Host: server1
Master_User: repl
Master_Port: 3306
Connect_Retry: 60
Master_Log_File: mysql-bin.000001
Read_Master_Log_Pos: 164
Relay_Log_File: mysql-relay-bin.000001
Relay_Log_Pos: 164
Relay_Master_Log_File: mysql-bin.000001
Slave_IO_Running: Yes
Slave_SQL_Running: Yes
...omitted...
Seconds_Behind_Master: 0
注意,slave的I/O和SQL线程都已经开始运行,而且Seconds_Behind_Master不再是NULL。日志
的位置增加了,意味着一些事件被获取并执行了。如果你在master上进行修改,你可以在slave上看
到各种日志文件的位置的变化,同样,你也可以看到数据库中数据的变化。
你可查看master和slave上线程的状态。在master上,你可以看到slave的I/O线程创建的连接:
mysql> show processlist /G
*************************** 1. row ***************************
Id: 1
User: root
Host: localhost:2096
db: test
Command: Query
Time: 0
State: NULL
Info: show processlist
*************************** 2. row ***************************
Id: 2
User: repl
Host: localhost:2144
db: NULL
Command: Binlog Dump
Time: 1838
State: Has sent all binlog to slave; waiting for binlog to be updated
Info: NULL
2 rows in set (0.00 sec)
基本到这里就完成,至于后期的加强操作,我会在另行添加。
Mysql复制的时候可以做到限制复制(主)
binlog-do-db=work #只复制
binlog_ignore_db=mysql #不允许复制
Replicate_Do_DB=mysql
replicate-ignore-db=mysql
另外还有几条常用的命令
flush mater; #清除垃圾
flush slave; #清除垃圾
start slave; #开始服务
reset slave; #重设服务
stop slave; #停止服务
上面复制方式是假设在新设Master和slave的情况下,实际环境并不十分实用,例如,你在一
组运行了很久的Master中加入一个新的slave呢?
这样我们就需要优先进行数据处理。
1.现将Master的数据库锁定,以免数据复制的时候出现差异。
FLUSH TABLES WITH READ LOCK;
2. 在另一个连接用mysqldump创建一个你想进行复制的数据库的转储:
shell> mysqldump --all-databases --lock-all-tables >dbdump.db
3. 对表释放锁。
mysql> UNLOCK TABLES;
上面方法中,第2部需要将数据库复制到新slave中还原,这样,Master和新Slave的数据源就一致。
其实第2部的方法有很多,也可以使用Mysql软件进行同步,例如:Navicat for Mysql
方法不是唯一,只要结果一致即可。
4.完成旧数据同步后,Master中输入
mysql> show master status;
##得到:
+------------------+----------+--------------+---------------------------+
| File | Position | Binlog_Do_DB | Binlog_Ignore_DB |
+------------------+----------+--------------+---------------------------+
| mysql-bin.000024 | 38113 | | mysql,test |
1 row in set (0.00 sec)
5.然后在根据上表中内容输入上文启动Slave步骤的内容。
CHANGE MASTER TO MASTER_HOST='192.168.60.73',MASTER_USER='repl',MASTER_PASSWORD='123456',
MASTER_LOG_FILE='mysql-bin.000002',MASTER_LOG_POS=0;
6.启动slave
START SLAVE;
7.启动完成后进行检查。
mysql> SHOW SLAVE STATUS/G ***************************
1. row ***************************
Slave_IO_State: Waiting for master to send event
Master_Host: 192.168.1.171
Master_User: repl
Master_Port: 3306
Connect_Retry: 60
Master_Log_File: mysql-bin.000024
Read_Master_Log_Pos: 38255
Relay_Log_File: mysql-relay-bin.000002
Relay_Log_Pos: 393
Relay_Master_Log_File: mysql-bin.000024
Slave_IO_Running: Yes
Slave_SQL_Running: Yes
Replicate_Do_DB:
Replicate_Ignore_DB: mysql,wdcpdb,mysql,wdcpdb
Replicate_Do_Table:
Replicate_Ignore_Table:
Replicate_Wild_Do_Table:
Replicate_Wild_Ignore_Table:
Last_Errno: 0
Last_Error:
Skip_Counter: 0
Exec_Master_Log_Pos: 38255
Relay_Log_Space: 548
Until_Condition: None
Until_Log_File:
Until_Log_Pos: 0
Master_SSL_Allowed: No
Master_SSL_CA_File:
Master_SSL_CA_Path:
Master_SSL_Cert:
Master_SSL_Cipher:
Master_SSL_Key:
Seconds_Behind_Master: 0
Master_SSL_Verify_Server_Cert: No
Last_IO_Errno: 0
Last_IO_Error:
Last_SQL_Errno: 0
Last_SQL_Error:
1 row in set (0.00 sec)
完成
测试过程要主要的问题:
1.请先配置好Mysql
2.开通复制前请将Mysql的库和表的框架复制过去。
(在测试一下能不能连表都复制过去!)
bitsCN.com

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1418
1418
 52
52
 1311
1311
 25
25
 1261
1261
 29
29
 1234
1234
 24
24
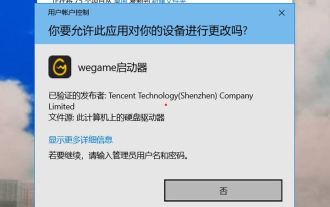 How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
When using Win11 system, sometimes you will encounter a prompt that requires you to enter the administrator username and password. This article will discuss how to deal with this situation. Method 1: 1. Click [Windows Logo], then press [Shift+Restart] to enter safe mode; or enter safe mode this way: click the Start menu and select Settings. Select "Update and Security"; select "Restart Now" in "Recovery"; after restarting and entering the options, select - Troubleshoot - Advanced Options - Startup Settings -&mdash
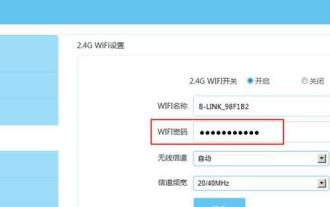 How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
Wireless networks have become an indispensable part of people's lives in today's digital world. Protecting the security of personal wireless networks is particularly important, however. Setting a strong password is key to ensuring that your WiFi network cannot be hacked by others. To ensure your network security, this article will introduce in detail how to use your mobile phone to change the router WiFi password. 1. Open the router management page - Open the router management page in the mobile browser and enter the router's default IP address. 2. Enter the administrator username and password - To gain access, enter the correct administrator username and password in the login page. 3. Navigate to the wireless settings page - find and click to enter the wireless settings page, in the router management page. 4. Find the current Wi
 The Stable Diffusion 3 paper is finally released, and the architectural details are revealed. Will it help to reproduce Sora?
Mar 06, 2024 pm 05:34 PM
The Stable Diffusion 3 paper is finally released, and the architectural details are revealed. Will it help to reproduce Sora?
Mar 06, 2024 pm 05:34 PM
StableDiffusion3’s paper is finally here! This model was released two weeks ago and uses the same DiT (DiffusionTransformer) architecture as Sora. It caused quite a stir once it was released. Compared with the previous version, the quality of the images generated by StableDiffusion3 has been significantly improved. It now supports multi-theme prompts, and the text writing effect has also been improved, and garbled characters no longer appear. StabilityAI pointed out that StableDiffusion3 is a series of models with parameter sizes ranging from 800M to 8B. This parameter range means that the model can be run directly on many portable devices, significantly reducing the use of AI
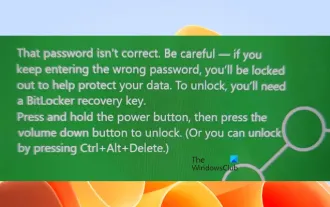 Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
This article will explore how to solve the problem of wrong password, especially the need to be careful when dealing with BitLocker warnings. This warning is triggered when an incorrect password is entered multiple times in BitLocker to unlock the drive. Usually, this warning occurs because the system has a policy that limits incorrect login attempts (usually three login attempts are allowed). In this case, the user will receive an appropriate warning message. The complete warning message is as follows: The password entered is incorrect. Please note that continuously entering incorrect passwords will cause the account to be locked. This is to protect the security of your data. If you need to unlock your account, you will need to use a BitLocker recovery key. The password is incorrect, beware the BitLocker warning you receive when you log in to your computer
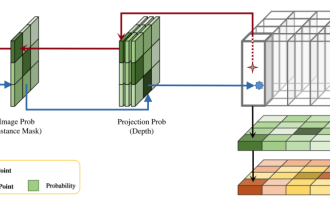 DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
This paper explores the problem of accurately detecting objects from different viewing angles (such as perspective and bird's-eye view) in autonomous driving, especially how to effectively transform features from perspective (PV) to bird's-eye view (BEV) space. Transformation is implemented via the Visual Transformation (VT) module. Existing methods are broadly divided into two strategies: 2D to 3D and 3D to 2D conversion. 2D-to-3D methods improve dense 2D features by predicting depth probabilities, but the inherent uncertainty of depth predictions, especially in distant regions, may introduce inaccuracies. While 3D to 2D methods usually use 3D queries to sample 2D features and learn the attention weights of the correspondence between 3D and 2D features through a Transformer, which increases the computational and deployment time.
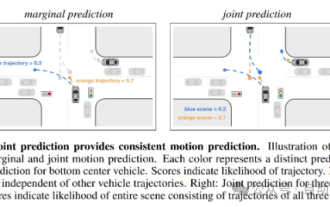 This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
Trajectory prediction plays an important role in autonomous driving. Autonomous driving trajectory prediction refers to predicting the future driving trajectory of the vehicle by analyzing various data during the vehicle's driving process. As the core module of autonomous driving, the quality of trajectory prediction is crucial to downstream planning control. The trajectory prediction task has a rich technology stack and requires familiarity with autonomous driving dynamic/static perception, high-precision maps, lane lines, neural network architecture (CNN&GNN&Transformer) skills, etc. It is very difficult to get started! Many fans hope to get started with trajectory prediction as soon as possible and avoid pitfalls. Today I will take stock of some common problems and introductory learning methods for trajectory prediction! Introductory related knowledge 1. Are the preview papers in order? A: Look at the survey first, p
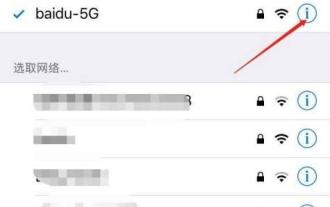 Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Wireless networks have become an indispensable part of our lives with the rapid development of the Internet. In order to protect personal information and network security, it is very important to change your wifi password regularly, however. To help you better protect your home network security, this article will introduce you to a detailed tutorial on how to use your mobile phone to change your WiFi password. 1. Understand the importance of WiFi passwords. WiFi passwords are the first line of defense to protect personal information and network security. In the Internet age, understanding its importance can better understand why passwords need to be changed regularly. 2. Confirm that the phone is connected to wifi. First, make sure that the phone is connected to the wifi network whose password you want to change before changing the wifi password. 3. Open the phone’s settings menu and enter the phone’s settings menu.
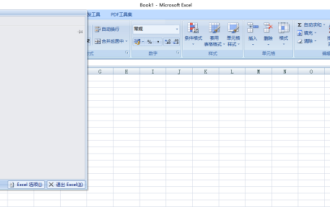 How to set a password for excel
Mar 21, 2024 am 09:00 AM
How to set a password for excel
Mar 21, 2024 am 09:00 AM
A few days ago, my cousin came to me to complain that he had worked hard to create a lot of data using Excel, but it was later modified by his colleagues. He didn't know the situation at the time. After sending it to his boss, he was scolded. This is really frustrating. Some people just don’t like you and want to deliberately punish you. After you leave school and enter society, you will find that more and more people are stabbing you in the back. In addition to a few words of comfort to my cousin, I also gave my cousin an advice. If you are afraid of encountering such a thing again in the future, then set a password for the excel form so that no one can open it except you. Netizens, if you are afraid that your Excel spreadsheet will be secretly modified by others, you should also set a password. How to set password for excel password form? Come with me to find out! 1.




