 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 A deep dive into the features and benefits of EncryptPad in Linux operating systems
A deep dive into the features and benefits of EncryptPad in Linux operating systems
A deep dive into the features and benefits of EncryptPad in Linux operating systems

Detailed explanation of the role and advantages of EncryptPad in Linux systems
In today's era of information explosion, information security has become particularly important. Especially in Linux systems, protecting the security of sensitive data is particularly important. EncryptPad is an open source, cross-platform encryption software designed for protecting text files and notes. EncryptPad not only plays an important role in Linux systems, but also has many advantages, allowing users to easily encrypt and decrypt files, ensuring the confidentiality of data.
1. The role of EncryptPad
- Text file encryption: EncryptPad can encrypt text files to protect sensitive information from being seen by unauthorized persons. .
- Note Encryption: Users can use EncryptPad to encrypt and save private notes to ensure the security of personal information.
- Cross-platform support: EncryptPad can run on multiple operating systems such as Linux, Windows and macOS, allowing users to easily encrypt and decrypt files between different devices.
2. Advantages of EncryptPad
- Free and open source: EncryptPad is open source software, users can use it for free, and can view and modify its source code .
- Powerful encryption algorithm: EncryptPad supports powerful encryption algorithms such as AES, Twofish, and Blowfish to ensure file security.
- Easy to use: EncryptPad has an intuitive user interface, users can easily encrypt and decrypt files without complex operations.
- Password Generator: EncryptPad provides a password generator so that users can generate strong passwords to protect files.
3. Specific code examples
The following is a code example for using EncryptPad to encrypt files in a Linux system:
-
Install EncryptPad
sudo apt-get install encryptpad
Copy after login Encrypt files
encryptpad --encrypt example.txt
Copy after loginDecrypt files
encryptpad --decrypt example.txt.pad
Copy after login
With the above examples, users can easily use EncryptPad to encrypt and decrypt files in Linux systems.
When using EncryptPad, users need to remember the encryption password they set to ensure file security.
To sum up, EncryptPad plays an important role in Linux systems and has many advantages. It can effectively protect users' sensitive information and is a recommended encryption tool. I hope the above content can help readers gain a deeper understanding of the application and advantages of EncryptPad in Linux systems.
The above is the detailed content of A deep dive into the features and benefits of EncryptPad in Linux operating systems. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1657
1657
 14
14
 1415
1415
 52
52
 1309
1309
 25
25
 1257
1257
 29
29
 1230
1230
 24
24
 Using Task Manager in Linux
Aug 15, 2024 am 07:30 AM
Using Task Manager in Linux
Aug 15, 2024 am 07:30 AM
There are many questions that Linux beginners often ask, "Does Linux have a Task Manager?", "How to open the Task Manager on Linux?" Users from Windows know that the Task Manager is very useful. You can open the Task Manager by pressing Ctrl+Alt+Del in Windows. This task manager shows you all the running processes and the memory they consume, and you can select and kill a process from the task manager program. When you first use Linux, you will also look for something that is equivalent to a task manager in Linux. A Linux expert prefers to use the command line to find processes, memory consumption, etc., but you don't have to
 7 ways to help you check the registration date of Linux users
Aug 24, 2024 am 07:31 AM
7 ways to help you check the registration date of Linux users
Aug 24, 2024 am 07:31 AM
Did you know, how to check the creation date of an account on a Linux system? If you know, what can you do? Did you succeed? If yes, how to do it? Basically Linux systems don't track this information, so what are the alternative ways to get this information? You may ask why am I checking this? Yes, there are situations where you may need to review this information and it will be helpful to you at that time. You can use the following 7 methods to verify. Use /var/log/secure Use aureport tool Use .bash_logout Use chage command Use useradd command Use passwd command Use last command Method 1: Use /var/l
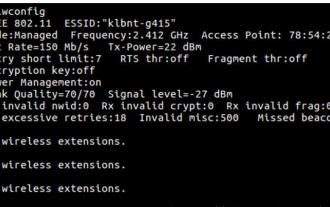 How to connect two Ubuntu hosts to the Internet using one network cable
Aug 07, 2024 pm 01:39 PM
How to connect two Ubuntu hosts to the Internet using one network cable
Aug 07, 2024 pm 01:39 PM
How to use one network cable to connect two ubuntu hosts to the Internet 1. Prepare host A: ubuntu16.04 and host B: ubuntu16.042. Host A has two network cards, one is connected to the external network and the other is connected to host B. Use the iwconfig command to view all network cards on the host. As shown above, the network cards on the author's A host (laptop) are: wlp2s0: This is a wireless network card. enp1s0: Wired network card, the network card connected to host B. The rest has nothing to do with us, no need to care. 3. Configure the static IP of A. Edit the file #vim/etc/network/interfaces to configure a static IP address for interface enp1s0, as shown below (where #==========
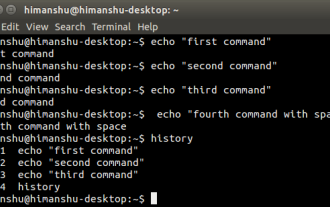 How to hide your Linux command line history
Aug 17, 2024 am 07:34 AM
How to hide your Linux command line history
Aug 17, 2024 am 07:34 AM
If you are a Linux command line user, sometimes you may not want certain commands to be recorded in your command line history. There could be many reasons, for example, you hold a certain position in a company and you have certain privileges that you don't want others to abuse. Or maybe there are some particularly important commands that you don't want to execute by mistake while browsing the history list. However, is there a way to control which commands go into the history list and which don't? Or in other words, can we enable incognito mode like a browser in a Linux terminal? The answer is yes, and depending on the specific goals you want, there are many ways to achieve it. In this article, we’ll discuss some proven methods. Note: All commands appearing in this article have been tested under Ubuntu. different
 How to convert XML files to PDF on your phone?
Apr 02, 2025 pm 10:12 PM
How to convert XML files to PDF on your phone?
Apr 02, 2025 pm 10:12 PM
It is impossible to complete XML to PDF conversion directly on your phone with a single application. It is necessary to use cloud services, which can be achieved through two steps: 1. Convert XML to PDF in the cloud, 2. Access or download the converted PDF file on the mobile phone.
 Detailed explanation: Shell script variable judgment parameter command
Sep 02, 2024 pm 03:25 PM
Detailed explanation: Shell script variable judgment parameter command
Sep 02, 2024 pm 03:25 PM
The system variable $n is the parameter passed to the script or function. n is a number indicating the number of parameters. For example, the first parameter is $1, and the second parameter is $2$? The exit status of the previous command, or the return value of the function. Returns 0 on success, 1 on failure $#Number of parameters passed to the script or function $* All these parameters are enclosed in double quotes. If a script receives two parameters, $* is equal to $1$2$0The name of the command being executed. For shell scripts, this is the path to the activated command. When $@ is enclosed in double quotes (""), it is slightly different from $*. If a script receives two parameters, $@ is equivalent to $1$2$$the process number of the current shell. For a shell script, this is the process I when it is executing
 Zabbix 3.4 Source code compilation installation
Sep 04, 2024 am 07:32 AM
Zabbix 3.4 Source code compilation installation
Sep 04, 2024 am 07:32 AM
1. Installation environment (Hyper-V virtual machine): $hostnamectlStatichostname:localhost.localdomainIconname:computer-vmChassis:vmMachineID:renwoles1d8743989a40cb81db696400BootID:renwoles272f4aa59935dcdd0d456501Virtualization:microsoftOperatingSystem:CentOS Linux7(Core)CPEOSName:cpe:
 Is Coinone a formal trading platform?
Aug 21, 2024 pm 03:24 PM
Is Coinone a formal trading platform?
Aug 21, 2024 pm 03:24 PM
Coinone is a formal cryptocurrency trading platform founded in 2014 and is one of the leading trading platforms in South Korea. It is known for its transparency, security, reliability, and wide selection of digital assets. Coinone complies with Korean government regulations and provides transparent fees and clear transaction information. It uses industry-leading security measures, including 2FA, cold storage, and DDoS protection. Coinone has strong liquidity, ensures fast transactions, and provides over-the-counter trading and a user-friendly interface. But it is mainly targeted at the Korean market and transaction fees may be slightly higher.



