 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Analysis of PHP security encapsulation and library design technology
Analysis of PHP security encapsulation and library design technology
Analysis of PHP security encapsulation and library design technology
With the rapid development of the Internet, the security of Web applications has become an increasingly important issue. As a commonly used server-side programming language, PHP's security needs to be paid more attention to. This article will explore secure code encapsulation and library design techniques in PHP to help developers develop more secure and reliable Web applications.
- Understand security risks
Before designing secure code packages and libraries, we first need to understand common security risks. Common security risks include cross-site scripting attacks (XSS), SQL injection, cross-site request forgery (CSRF), etc. Understanding these risks can help us prevent potential security issues in code design.
- Input validation and filtering
When writing PHP code, we should always perform strict input validation and filtering. Using PHP's built-in functions (such as filter_var, htmlspecialchars, etc.) can help us verify the legitimacy of input data and filter potentially malicious code. Additionally, regular expressions can be used for more flexible validation.
- Secure processing of database operations
Avoid using concatenated strings to directly pass user input data to SQL query statements, which can easily lead to SQL injection attacks. Instead, parameterized queries or prepared statements should be used to increase the security of database operations. Parameterized queries prevent user input data from being parsed as part of the SQL statement, thereby avoiding SQL injection.
- Password encryption and storage
Password encryption and storage is a very important security issue. We should avoid storing user passwords in clear text and instead use a hash function to encrypt the password. PHP provides a series of hash functions (such as password_hash, password_verify, etc.) that can help us achieve secure password storage and verification.
- Permission Management
In a web application, different permissions should be assigned to different user roles. This can be achieved by using access control lists (ACLs) or role-based access control (RBAC). When designing code, we should reasonably divide user roles and design corresponding access restrictions for different permission levels.
- Defense against CSRF attacks
In order to defend against CSRF attacks, we can add hidden fields to the form or generate random tokens. When handling form submissions, we can verify the validity of the token, ensuring that the request comes from a legitimate source.
- Exception handling and error message hiding
In code design, we should handle exceptions reasonably and avoid returning sensitive error information to the client. Instead, only appropriate error messages should be displayed during error handling to avoid providing useful information to attackers.
- Design and use of security libraries
In order to facilitate developers to quickly implement secure code, when designing secure code encapsulation and libraries in PHP, we can use commonly used Security methods are encapsulated into functions or classes for developers to use. For example, input verification, password encryption, database operations, etc. can be encapsulated into functions or class libraries for developers to call directly.
Summary:
Secure code encapsulation and library design technology in PHP are crucial to building safe and reliable Web applications. During the development process, we need to understand common security risks and take appropriate measures to prevent potential attacks. Reasonable input validation and filtering, secure database operations, password encryption and storage, permission management, CSRF attack defense, exception handling and error message hiding, and the design and use of security libraries are all key elements to achieve secure code. Through reasonable technology selection and code design, we can build more secure and reliable web applications and protect user data security.
The above is the detailed content of Analysis of PHP security encapsulation and library design technology. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
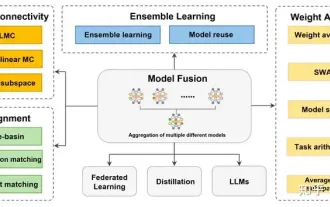 Review! Deep model fusion (LLM/basic model/federated learning/fine-tuning, etc.)
Apr 18, 2024 pm 09:43 PM
Review! Deep model fusion (LLM/basic model/federated learning/fine-tuning, etc.)
Apr 18, 2024 pm 09:43 PM
In September 23, the paper "DeepModelFusion:ASurvey" was published by the National University of Defense Technology, JD.com and Beijing Institute of Technology. Deep model fusion/merging is an emerging technology that combines the parameters or predictions of multiple deep learning models into a single model. It combines the capabilities of different models to compensate for the biases and errors of individual models for better performance. Deep model fusion on large-scale deep learning models (such as LLM and basic models) faces some challenges, including high computational cost, high-dimensional parameter space, interference between different heterogeneous models, etc. This article divides existing deep model fusion methods into four categories: (1) "Pattern connection", which connects solutions in the weight space through a loss-reducing path to obtain a better initial model fusion
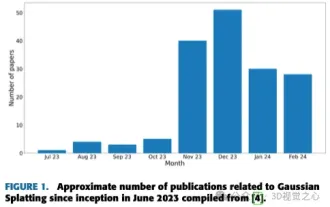 More than just 3D Gaussian! Latest overview of state-of-the-art 3D reconstruction techniques
Jun 02, 2024 pm 06:57 PM
More than just 3D Gaussian! Latest overview of state-of-the-art 3D reconstruction techniques
Jun 02, 2024 pm 06:57 PM
Written above & The author’s personal understanding is that image-based 3D reconstruction is a challenging task that involves inferring the 3D shape of an object or scene from a set of input images. Learning-based methods have attracted attention for their ability to directly estimate 3D shapes. This review paper focuses on state-of-the-art 3D reconstruction techniques, including generating novel, unseen views. An overview of recent developments in Gaussian splash methods is provided, including input types, model structures, output representations, and training strategies. Unresolved challenges and future directions are also discussed. Given the rapid progress in this field and the numerous opportunities to enhance 3D reconstruction methods, a thorough examination of the algorithm seems crucial. Therefore, this study provides a comprehensive overview of recent advances in Gaussian scattering. (Swipe your thumb up
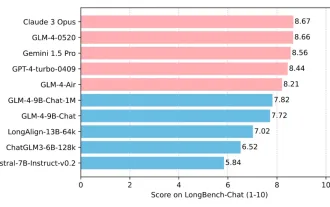 Tsinghua University and Zhipu AI open source GLM-4: launching a new revolution in natural language processing
Jun 12, 2024 pm 08:38 PM
Tsinghua University and Zhipu AI open source GLM-4: launching a new revolution in natural language processing
Jun 12, 2024 pm 08:38 PM
Since the launch of ChatGLM-6B on March 14, 2023, the GLM series models have received widespread attention and recognition. Especially after ChatGLM3-6B was open sourced, developers are full of expectations for the fourth-generation model launched by Zhipu AI. This expectation has finally been fully satisfied with the release of GLM-4-9B. The birth of GLM-4-9B In order to give small models (10B and below) more powerful capabilities, the GLM technical team launched this new fourth-generation GLM series open source model: GLM-4-9B after nearly half a year of exploration. This model greatly compresses the model size while ensuring accuracy, and has faster inference speed and higher efficiency. The GLM technical team’s exploration has not
 The Mistral open source code model takes the throne! Codestral is crazy about training in over 80 languages, and domestic Tongyi developers are asking to participate!
Jun 08, 2024 pm 09:55 PM
The Mistral open source code model takes the throne! Codestral is crazy about training in over 80 languages, and domestic Tongyi developers are asking to participate!
Jun 08, 2024 pm 09:55 PM
Produced by 51CTO technology stack (WeChat ID: blog51cto) Mistral released its first code model Codestral-22B! What’s crazy about this model is not only that it’s trained on over 80 programming languages, including Swift, etc. that many code models ignore. Their speeds are not exactly the same. It is required to write a "publish/subscribe" system using Go language. The GPT-4o here is being output, and Codestral is handing in the paper so fast that it’s hard to see! Since the model has just been launched, it has not yet been publicly tested. But according to the person in charge of Mistral, Codestral is currently the best-performing open source code model. Friends who are interested in the picture can move to: - Hug the face: https
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.
 PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
In the security comparison between Slim and Phalcon in PHP micro-frameworks, Phalcon has built-in security features such as CSRF and XSS protection, form validation, etc., while Slim lacks out-of-the-box security features and requires manual implementation of security measures. For security-critical applications, Phalcon offers more comprehensive protection and is the better choice.
 Revolutionary GPT-4o: Reshaping the human-computer interaction experience
Jun 07, 2024 pm 09:02 PM
Revolutionary GPT-4o: Reshaping the human-computer interaction experience
Jun 07, 2024 pm 09:02 PM
The GPT-4o model released by OpenAI is undoubtedly a huge breakthrough, especially in its ability to process multiple input media (text, audio, images) and generate corresponding output. This ability makes human-computer interaction more natural and intuitive, greatly improving the practicality and usability of AI. Several key highlights of GPT-4o include: high scalability, multimedia input and output, further improvements in natural language understanding capabilities, etc. 1. Cross-media input/output: GPT-4o+ can accept any combination of text, audio, and images as input and directly generate output from these media. This breaks the limitation of traditional AI models that only process a single input type, making human-computer interaction more flexible and diverse. This innovation helps power smart assistants
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access





