Analysis of switch port security examples
[Experiment name]
Port security configuration of the switch
[Experiment purpose]
Master the port security function of the switch and control the user's secure access
[Background description]
You are A network administrator for a company that requires strict control over the network. In order to prevent
IP address conflicts of users within the company and prevent network attacks and sabotage within the company. Each employee is assigned a fixed IP address,
and only company employee hosts are allowed to use the network, and they are not allowed to connect to other hosts at will. For example: the
IP address assigned to an employee is 172.16.1.55/24, the host MAC address is 00-06-1B-DE-13-B4, and the host is connected to a 2126G
.
[Requirement Analysis]
For all ports of the switch, configure the maximum number of connections to 1, and perform IP+MAC address
binding for the interface of the PC1 host.
[Experimental Principle]
The switch port security function refers to configuring the security attributes of the switch port to control the user's safe access. There are two main types of switch port security: one is to limit the maximum number of connections on the switch port, and the other is to bind the MAC address and IP address of the switch port.
Limiting the maximum number of connections on a switch port can control the number of hosts connected to the switch port and prevent users from malicious
ARP spoofing.
The address binding of the switch port can be flexibly bound for IP address, MAC address, and IP+MAC.
Can achieve strict control over users. Ensure users' safe access and prevent common intranet network attacks. Such as
ARP spoofing, IP, MAC address spoofing, IP address spoofing, etc.
After configuring the port security function of the switch, when the actual application exceeds the configuration requirements, a security violation will be generated.
There are three ways to handle security violations:
? protect When the number of safe addresses is full Afterwards, the secure port will drop packets with unknown addresses (not any of the secure
addresses for that port).
? restrict When a violation occurs, a Trap notification will be sent.
? shutdown When a violation occurs, the port will be closed and a Trap notification will be sent.
? When the port is closed due to a violation, use the command errdisable recovery in global configuration mode to recover the
interface from the error state.
[Experimental steps]
The first step: Configure the maximum connection limit of the switch port
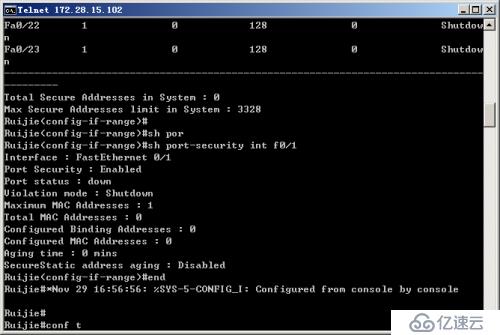
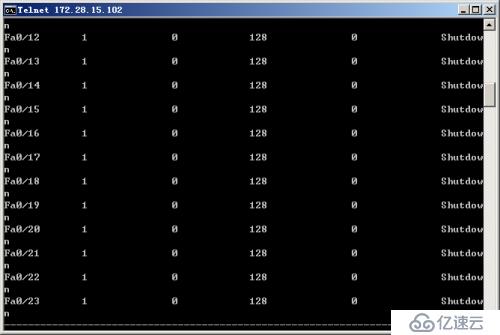
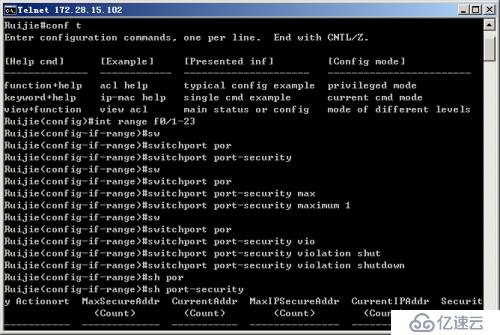 The second step: Verify the maximum connection limit of the switch port
The second step: Verify the maximum connection limit of the switch port
 Step 3: Configure the MAC and IP address binding of the switch port
Step 3: Configure the MAC and IP address binding of the switch port
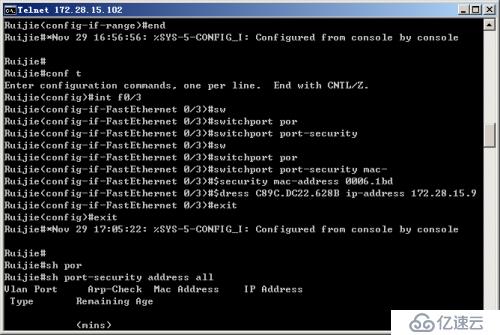 Step 4: View the address security binding configuration
Step 4: View the address security binding configuration
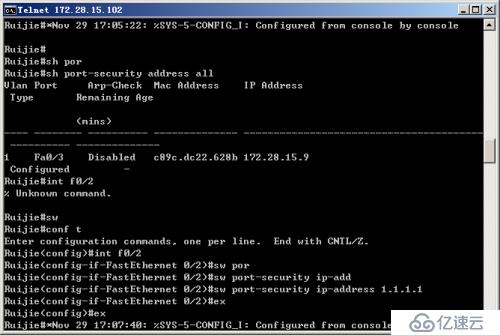 Step 5: Configure the IP of the switch port
Step 5: Configure the IP of the switch port
The above is the detailed content of Analysis of switch port security examples. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Broadcom Unveils Innovation, Launches Industry's First On-Chip Neural Network Switch
Dec 03, 2023 pm 08:51 PM
Broadcom Unveils Innovation, Launches Industry's First On-Chip Neural Network Switch
Dec 03, 2023 pm 08:51 PM
Broadcom recently announced the launch of the Trident5-X12 chip, which is equipped with a new NetGNT (Network General Neural Network Traffic Analyzer) on-chip neural network inference engine. NetGNT is different from traditional packet processing. It can work in parallel to enhance standard packet processing. pipeline. Traditional pipelines can only process one packet/path at a time, while NetGNT, as a machine learning inference engine, can be trained to identify various traffic patterns across the entire chip. It is understood that the Trident5-X12 chip has powerful software programming functions and on-site upgrade functions, providing a bandwidth of up to 16.0 Terabits/second, which is twice that of Trident4-X9. In addition, the new chip also supports
 Learn more about the dis command in switch inspection
Feb 18, 2024 am 10:05 AM
Learn more about the dis command in switch inspection
Feb 18, 2024 am 10:05 AM
What is the dis command used in switch inspection? In the maintenance and management process of network equipment, switches are an indispensable part. Inspection of switches is one of the important links to ensure the normal operation of the network. During the inspection process, the dis command is a commonly used command on switches. The purpose and function of the dis command will be introduced in detail below. dis is the abbreviation of display. It is a commonly used command on Huawei switch equipment and is used to display various information of the equipment. The dis command can display the configuration information and operating status of the switch.
 How does a switch work?
Dec 26, 2023 am 11:56 AM
How does a switch work?
Dec 26, 2023 am 11:56 AM
The working principle of the switch includes: 1. Data frame reception and analysis; 2. Forwarding table update; 3. Data frame forwarding; 4. Flood processing; 5. Connection maintenance. Detailed introduction: 1. Data frame reception and parsing. When the switch receives a data frame, it will first parse the data frame and extract the source MAC address and destination MAC address and other information; 2. Update of the forwarding table, The switch maintains a forwarding table internally, which records the correspondence between MAC addresses and interfaces; 3. Forwarding of data frames, etc.
 How does a switch work?
Dec 26, 2023 pm 02:07 PM
How does a switch work?
Dec 26, 2023 pm 02:07 PM
The working principle of the switch is based on the second layer of the OSI reference model, the data link layer. A switch is a network device based on a learning process that enables communication between different devices in the network by parsing and forwarding data frames. The switch can continuously improve the contents of its internal forwarding table, improve the efficiency and reliability of data exchange, and ensure the stability and security of the connection. Switches are widely used in enterprise networks, data centers, campus networks and other scenarios to provide stable and efficient connection services for various applications.
 What are the main functions of a switch?
Aug 18, 2022 pm 02:56 PM
What are the main functions of a switch?
Aug 18, 2022 pm 02:56 PM
The main functions of the switch are physical addressing, network topology, error checking, frame sequence and flow control; the switch is a network device used for electro-optical signal forwarding, and also has some new functions such as support for virtual LAN, Support for link aggregation, and some even have firewall functions.
 What are the three authentication mode configurations of H3C switch telnet service?
May 21, 2023 pm 07:40 PM
What are the three authentication mode configurations of H3C switch telnet service?
May 21, 2023 pm 07:40 PM
The following takes an H3C switch as an example to introduce the three authentication methods of telnet service. Configuration steps for None authentication mode: [H3C] telnetserverenable//Enable Telnet service [H3C] user-interfacevty04//Allow remote users 0-4, a total of 5 accounts at the same time Log in [H3C-line-vty0-4] authentication-modenone//Authentication mode is none, no authentication is required [H3C-line-vty0-4] user-rolelevel-3//Set login user permissions Password authentication mode configuration steps: [ H3C]telne
 What is the difference between a switch and a router
Jan 16, 2024 pm 03:39 PM
What is the difference between a switch and a router
Jan 16, 2024 pm 03:39 PM
Differences: 1. Different working principles: The switch works at the relay layer and is mainly addressed based on MAC address. The router works at the network layer, addresses according to the IP address, and can handle the TCP/IP protocol; 2. Different functions: the switch can make multiple computers connected to it form a local area network, but it cannot automatically identify the address where the data packet is sent and arrived. The router is responsible for automatically identifying the addresses where data packets are sent and arrived, and can handle the routing of data packets; 3. Different usage scenarios: Routers are usually used for sending and receiving in one place. A switch is used to connect multiple computers.
 What is a switch
Jan 31, 2023 pm 03:30 PM
What is a switch
Jan 31, 2023 pm 03:30 PM
A switch is a network device used for forwarding electrical (optical) signals. It can provide an exclusive electrical signal path for any two network nodes connected to the switch. The switch is only used to distribute network data. It can connect many hosts, each of which has its own external IP. The switch works at the relay layer, addressing based on MAC address, and cannot provide this function.






