AI meets 6G—opportunities and challenges
Background introduction
6G technology introduction
With the 5G network expectations With the development of digital transformation, the 6G communication era envisions how humans will interact with the digital virtual world after 2030 to cope with the communication and network challenges after 2030. While traditional applications (such as multimedia streaming) will still exist, the article envisions new application areas for 6G systems, such as multi-sensor extended reality (XR) applications, connected robots and autonomous systems (CRAS), and wireless brain-computer interaction (BCI) [1]. Holographic telepresence, eHealth (including in vivo networks) are other 6G use cases that require extremely high data rates, ultra-low latency and ultra-reliability [2].
6G revolutionizes wireless networks from connected things to “connected intelligence” [1], [2]. Therefore, artificial intelligence becomes an integral part of the network. Distributed heterogeneous networks require ubiquitous AI services to ensure 6G goals are achieved. Intelligent wireless communications, network closed-loop optimization, and 6G big data analysis emphasize the use of artificial intelligence in all aspects of 6G networks.
After 2030, wireless applications will require higher data rates (up to 1 Tb/s), extremely low end-to-end latency (
Threats to 6G security
This section also discusses the Security issues arising from architectural changes and new technologies. Figure 1 illustrates possible attacks on different layers of the 6G architecture, outlining how this paper presents the security threat picture for 6G.
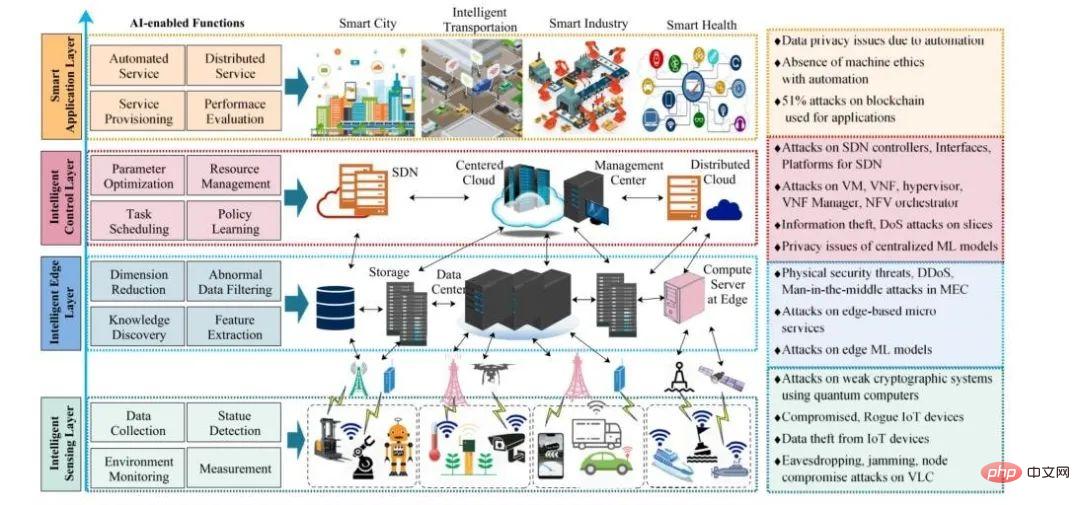
Figure 1 Intelligent 6G architecture [6] and 6G security and privacy issues
in 5G Network softwareization technologies such as software-defined networking (SDN), network functions virtualization (NFV), multi-access edge computing (MEC), and network slicing are still applicable to 6G systems; therefore, their security issues still exist in 6G. Prominent security issues related to SDN are attacks on SDN controllers, attacks on northbound and southbound interfaces, inherent vulnerabilities in the platforms used to deploy SDN controllers/applications [7]. NFV-related security issues are attacks on virtual machines (VMs), virtual network functions (VNFs), hypervisors, VNF managers, and NFV coordinators [8]. Due to the massively distributed nature of 6G systems, MEC in 6G is subject to physical security threats, distributed denial of service (DDoS), and man-in-the-middle attacks. A potential attack on network slicing is a DoS attack, where information is stolen through a compromised slice. Attacks on network softwareization technologies prevent 6G networks from achieving the promised dynamism and full automation.
6G envisions the Internet of Everything (IOE), a collection of billions of heterogeneous devices. A basic device security model that relies on SIM cards is not a realistic deployment of IOE in 6G, especially for small form factor devices such as in-body sensors. In such a large network, key distribution and management functions are inefficient. Resource-constrained IoT devices are unable to provide complex passwords to maintain strong security, making them prime targets for attackers. These devices can be compromised and potentially used to launch attacks. Hyperconnected IOEs pose privacy concerns for providing data collection for 6G applications. Exploiting resource-constrained IoT devices for data theft will impact data privacy, location privacy, and identity privacy.
Existing 5G network deployments typically serve vertical industries such as industry, healthcare, and education. 6G further extends this concept by allowing smaller networks such as in-body networks, swarms of drones, environmental sensor networks with longer battery life [4]. These local networks operate as independent networks and interoperate with wide area connections when needed. Unlike well-defined native 5G networks, many stakeholders implement native 6G networks with varying levels of embedded security. On-premises 6G networks with minimal security provide an opportunity for intruders to launch attacks. Then infiltrate into the network of trust-compromised networks.
Security of 6G architecture
Dense cellular deployments, mesh networks, multiple connections and device-to-device (D2D) communications will become the norm in 6G. Malicious parties are more likely to exploit distributed networks with more vulnerable devices, each with mesh connectivity, increasing the threat surface. The definition of subnetworks requires changes to the security policy. It is far from practical for a WAN to provide security for a large number of devices within each subnet. In 6G, a hierarchical security mechanism that distinguishes subnet-level communication security and subnet-to-WAN security will be a better approach. 6G networks will coexist with frameworks such as zero-touch networking and service management (ZSM) architectures to shorten service time to market, lower operational costs and reduce human error. Full automation with self-learning capabilities allows attacks to propagate in a closed loop and data privacy protection is extremely challenging because in a zero-touch network, automation and less human intervention are required.
The security of 6G technology
6G relies on artificial intelligence to achieve a fully autonomous network . Therefore, attacks on AI systems, especially machine learning (ML) systems, will impact 6G. Poisoning attacks, data injection, data manipulation, logic destruction, model evasion, model inversion, model extraction, and membership inference attacks are potential security threats against ML systems. A larger set of features makes AI systems perform better. Attacks on collected data, as well as inadvertent use of private data, can lead to privacy concerns because data processing is often invisible to users. Blockchain is also a key technology to unlock the potential of 6G systems. Blockchain is suitable for decentralized resource management, spectrum sharing and service management in large-scale distributed 6G networks. A 51% attack is feasible on quantum computers to destabilize a blockchain. Since blockchain networks store data publicly, privacy protection is challenging. The current 5G standard does not address the security issues posed by quantum computing; instead, it relies on traditional cryptography such as elliptic curve cryptography (ECC). Since the 6G era marks the emergence of quantum computers, current security mechanisms based on asymmetric key encryption are vulnerable to quantum computer-based attacks. Therefore, without the design of quantum-safe cryptographic algorithms, secure 5G communications utilizing asymmetric key cryptography may no longer be suitable for post-quantum security.
The important role of AI in 6G security
##Use AI to mitigate security issues in 6G architecture Compared to current centralized cloud-based AI systems, 6G will primarily rely on edge intelligence. The distributed nature enables edge-based federated learning to be performed across large-scale devices and data systems to achieve network security and ensure communication efficiency. 6G architecture envisions connected intelligence and uses AI at different levels of the network hierarchy. Tiny cell-level AI has the potential to thwart DoS attacks on cloud servers at the lowest level. The multi-connectivity of devices in a mesh network allows multiple base stations to evaluate a device's behavior using an AI classification algorithm and jointly determine authenticity using a weighted average scheme. Behavior-based approaches reduce the overhead of frequent key exchanges due to frequent handovers caused by microcells and multiple-access technologies. Based on federated learning, there can be different levels of authorization at the subnet level and WAN level. Trust scores obtained within a subnetwork level can be shared externally only when external communication is required. Learning-based intrusion detection methods may be good candidates for preventing CPMS and UPMS attacks because the edge already has data provided by intelligent services. Frameworks like ZSM are equipped with domain analysis and domain intelligence services for zero-touch management of networks, primarily based on artificial intelligence. AI model evaluation, API security AI engine is a key security functional component that enhances the security of the ZSM reference architecture. Using AI to mitigate security issues in 6G technology Predictive analysis using AI can Predict attacks before they occur, such as 51% blockchain attacks. Quantum computers could threaten asymmetric key encryption. However, they can also provide exponential speeds to AI/ML algorithms to perform tasks faster and achieve previously impossible tasks. Therefore, quantum machine learning for cybersecurity is a potential defense technology against quantum computer-based attacks. Reinforcement learning (RL)-based smart beamforming technology provides optimal beamforming strategies against eavesdropper attacks in VLC systems. Jamming is similar to a DoS attack. Therefore, anomaly-based detection systems equipped with AI are possible solutions to detect jamming attacks. AI-based authentication and authorization systems are also suitable for preventing node disclosure attacks. Using AI for 6G privacy protectionMulti-connectivity mesh networks with microcells in 6G allow devices to communicate simultaneously through multiple base stations. Edge-based ML models can be used for dynamic detection of privacy-preserving routing, ranking devices, and allowing devices to transmit data through privacy-preserving routing based on ranking. Compared to cloud-based centralized learning, federated learning keeps data close to users to enhance data privacy and location privacy. 6G subnetwork-level AI allows privacy to be preserved within the subnetwork and only shared externally learned information to minimize privacy risks. Restricting data within a network is suitable for applications such as in vivo networks. With the vast number of applications in 6G and the massive collection of data to feed intelligent models, users will choose different levels of privacy on different applications. AI-based service-oriented privacy protection policy updates are potential solutions to support fully automated 6G networks.
References
[1] W.Saad, M.Bennis, and M.Chen, “A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems, ” IEEE Network, vol. 34, no. 3, pp. 134–142, 2019
[2] C. de Alwis, A. Kalla, Q. V. Pham , P. Kumar, K. Dev, W. J. Hwang, and M. Liyanage, “Survey on 6G Frontiers: Trends, Applications, Requirements, Technologies and Future Research,” IEEE Open Journal of the Communications Society, pp. 1–1, 2021.
[3]J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang, W. Zhao, A survey on internet of things: architecture, enabling technologies, security and privacy, and applications, IEEE Internet Things J. 4 (5) (2017) 1 125–1 142 .
[4]T. Shinzaki , I. Morikawa , Y. Yamaoka , Y. Sakemi , IoT security for utilization of big data: Mutual authentication technology and anonymization technology for positional data, Fujitsu Sci. Tech. J. 52 (4) (2016) 52–60 .
[5]M. Ylianttila, R. Kantola, A. Gurtov, L. Mucchi, I. Oppermann, Z. Yan, T. H. Nguyen, F. Liu, T. Hewa, M. Liyanage et al., “6G White Paper: Research Challenges for Trust, Security and Privacy,” arXiv preprint arXiv :2004.11665, 2020.
[6]K. B. Letaief, W. Chen, Y. Shi, J. Zhang, and Y.-J. A. Zhang, “The Roadmap to 6G: AI Empowered Wireless Networks,” IEEE Communi cations Magazine, vol. 57, no. 8, pp. 84–90, 2019.
[7]I. Ahmad, T. Kumar, M. Liyanage, J. Okwuibe, M. Ylianttila, and A . Gurtov, “Overview of 5G Security Challenges and Solutions,” IEEE Communications Standards Magazine, vol. 2, no. 1, pp. 36–43, 2018.
[8]R. Khan, P. Kumar , D. N. K. Jayakody, and M. Liyanage, “A survey on security and privacy of 5g technologies: Potential solutions, recent advancements, and future directions,” IEEE Communications Surveys & Tutorials, vol. 22, no. 1, pp.196–248 , 2019.
The above is the detailed content of AI meets 6G—opportunities and challenges. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 WorldCoin (WLD) price forecast 2025-2031: Will WLD reach USD 4 by 2031?
Apr 21, 2025 pm 02:42 PM
WorldCoin (WLD) price forecast 2025-2031: Will WLD reach USD 4 by 2031?
Apr 21, 2025 pm 02:42 PM
WorldCoin (WLD) stands out in the cryptocurrency market with its unique biometric verification and privacy protection mechanisms, attracting the attention of many investors. WLD has performed outstandingly among altcoins with its innovative technologies, especially in combination with OpenAI artificial intelligence technology. But how will the digital assets behave in the next few years? Let's predict the future price of WLD together. The 2025 WLD price forecast is expected to achieve significant growth in WLD in 2025. Market analysis shows that the average WLD price may reach $1.31, with a maximum of $1.36. However, in a bear market, the price may fall to around $0.55. This growth expectation is mainly due to WorldCoin2.
 What is the analysis chart of Bitcoin finished product structure? How to draw?
Apr 21, 2025 pm 07:42 PM
What is the analysis chart of Bitcoin finished product structure? How to draw?
Apr 21, 2025 pm 07:42 PM
The steps to draw a Bitcoin structure analysis chart include: 1. Determine the purpose and audience of the drawing, 2. Select the right tool, 3. Design the framework and fill in the core components, 4. Refer to the existing template. Complete steps ensure that the chart is accurate and easy to understand.
 Why is the rise or fall of virtual currency prices? Why is the rise or fall of virtual currency prices?
Apr 21, 2025 am 08:57 AM
Why is the rise or fall of virtual currency prices? Why is the rise or fall of virtual currency prices?
Apr 21, 2025 am 08:57 AM
Factors of rising virtual currency prices include: 1. Increased market demand, 2. Decreased supply, 3. Stimulated positive news, 4. Optimistic market sentiment, 5. Macroeconomic environment; Decline factors include: 1. Decreased market demand, 2. Increased supply, 3. Strike of negative news, 4. Pessimistic market sentiment, 5. Macroeconomic environment.
 What does cross-chain transaction mean? What are the cross-chain transactions?
Apr 21, 2025 pm 11:39 PM
What does cross-chain transaction mean? What are the cross-chain transactions?
Apr 21, 2025 pm 11:39 PM
Exchanges that support cross-chain transactions: 1. Binance, 2. Uniswap, 3. SushiSwap, 4. Curve Finance, 5. Thorchain, 6. 1inch Exchange, 7. DLN Trade, these platforms support multi-chain asset transactions through various technologies.
 The top ten free platform recommendations for real-time data on currency circle markets are released
Apr 22, 2025 am 08:12 AM
The top ten free platform recommendations for real-time data on currency circle markets are released
Apr 22, 2025 am 08:12 AM
Cryptocurrency data platforms suitable for beginners include CoinMarketCap and non-small trumpet. 1. CoinMarketCap provides global real-time price, market value, and trading volume rankings for novice and basic analysis needs. 2. The non-small quotation provides a Chinese-friendly interface, suitable for Chinese users to quickly screen low-risk potential projects.
 How to win KERNEL airdrop rewards on Binance Full process strategy
Apr 21, 2025 pm 01:03 PM
How to win KERNEL airdrop rewards on Binance Full process strategy
Apr 21, 2025 pm 01:03 PM
In the bustling world of cryptocurrencies, new opportunities always emerge. At present, KernelDAO (KERNEL) airdrop activity is attracting much attention and attracting the attention of many investors. So, what is the origin of this project? What benefits can BNB Holder get from it? Don't worry, the following will reveal it one by one for you.
 Aavenomics is a recommendation to modify the AAVE protocol token and introduce token repurchase, which has reached the quorum number of people.
Apr 21, 2025 pm 06:24 PM
Aavenomics is a recommendation to modify the AAVE protocol token and introduce token repurchase, which has reached the quorum number of people.
Apr 21, 2025 pm 06:24 PM
Aavenomics is a proposal to modify the AAVE protocol token and introduce token repos, which has implemented a quorum for AAVEDAO. Marc Zeller, founder of the AAVE Project Chain (ACI), announced this on X, noting that it marks a new era for the agreement. Marc Zeller, founder of the AAVE Chain Initiative (ACI), announced on X that the Aavenomics proposal includes modifying the AAVE protocol token and introducing token repos, has achieved a quorum for AAVEDAO. According to Zeller, this marks a new era for the agreement. AaveDao members voted overwhelmingly to support the proposal, which was 100 per week on Wednesday
 Rexas Finance (RXS) can surpass Solana (Sol), Cardano (ADA), XRP and Dogecoin (Doge) in 2025
Apr 21, 2025 pm 02:30 PM
Rexas Finance (RXS) can surpass Solana (Sol), Cardano (ADA), XRP and Dogecoin (Doge) in 2025
Apr 21, 2025 pm 02:30 PM
In the volatile cryptocurrency market, investors are looking for alternatives that go beyond popular currencies. Although well-known cryptocurrencies such as Solana (SOL), Cardano (ADA), XRP and Dogecoin (DOGE) also face challenges such as market sentiment, regulatory uncertainty and scalability. However, a new emerging project, RexasFinance (RXS), is emerging. It does not rely on celebrity effects or hype, but focuses on combining real-world assets (RWA) with blockchain technology to provide investors with an innovative way to invest. This strategy makes it hoped to be one of the most successful projects of 2025. RexasFi






