 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Classic techniques for Linux inter-process communication
Classic techniques for Linux inter-process communication
Classic techniques for Linux inter-process communication
This article brings you relevant knowledge about Linux inter-process communication, including pipes, anonymous pipes, shared memory and other related issues. I hope it will be helpful to everyone.

·Inter-process communication: The method provided by the operating system for the system to implement inter-process communication
It is impossible to communicate directly between processes because each process has an independent virtual address space and accesses its own virtual address. Therefore, the process is independent and cannot communicate directly.
According to the communication scenario are different, so a variety of communication methods are provided
Types of inter-process communication methods: pipes, shared memory, message queues, semaphores
·Pipeline
Features: Half-duplex communication--one-way communication with the direction you can choose
Essence: Open up a buffer in the kernel (a piece of memory in the kernel space)
Principle: Multiple processes communicate by accessing the buffer in the same kernel (copying the operation handle of the buffer)
Classification: Anonymous pipe: The buffer has no identifier and can only be used with Inter-process communication of affinity
Named pipe: The buffer has an identifier and can be used for any inter-process communication on the same host
Everything under Linux is a file--everything is treated as a file Perform the same operations (including pipes), and complete access to the pipe through IO operations
·Anonymous pipe
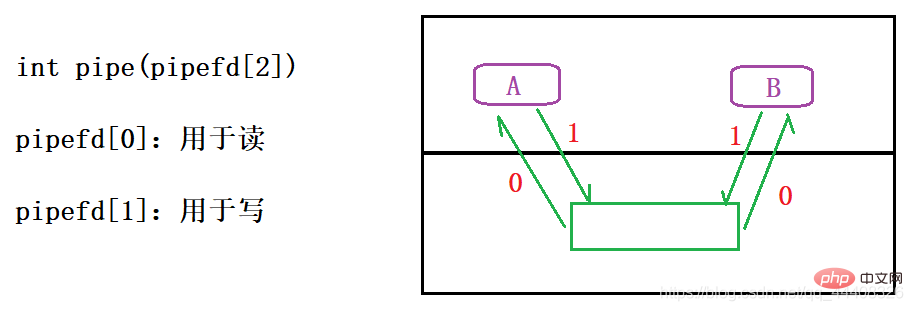
Return value: 0 on success; -1 on failure
Features: Can only be used for inter-process communication with affinity
Anonymous pipes have no identifiers , cannot be found by other processes, and can only obtain the operation handle to achieve communication by copying the parent process from the child process
Read and write characteristics: If there is no data in the pipe, read will block
If the data in the pipe is full, write will block
The reading end of all pipelines is closed, and continuing Write will trigger abnormalities, causing the process crash to withdraw from
all Pipelines to be closed Return 0 after completing the data and no longer block
Note: The pipe is a half-duplex communication. During communication, once the direction is selected, the unused end should be closed.
· Named pipe: is essentially a buffer in the kernel, with an identifier, Can be found by other processes, so it can be used for any inter-process communication on the same host
The identifier of a named pipe is a pipe type file visible in the file system
Multiple processes can open the same A pipe file, accessing the buffer in the same kernel to achieve communication
Command operation: mkfifo filename Create a named pipe file
Function operation: int mkfifo(const char *pathname, mode_t mode) ;
pathname: file name; mode: creation permission
Return value: 0 is returned on success; -1 is returned on failure
·Summary: The essence of the pipe: a buffer in the kernel space
Principle: Multiple processes achieve data transmission by accessing the same buffer
Category: anonymous pipe, named pipe
use using use with ’ ’ s ’ ’ s ’ through ’ s through ‐ through ‐ ‐‐ ‐‐‐ and --One-way communication with selectable direction
Provides byte stream transmission service: ordered, reliable, connection-based streaming transmission
Connection-based: all readers are closed If the write end is closed, the read will return 0
# Mutually exclusive: Make the process’s access to critical resources more reasonable and orderly through some conditional judgments# Then write blocks
③The life cycle depends on the process: without human intervention, after all processes that open the pipe exit, the pipe buffer is released
·Shared memory: Used to realize data sharing between processes Essence: a piece of physical memory
Principle: Open up a physical memory space, and multiple processes map the same block to their own virtual memory Address space is directly accessed through virtual addresses to achieve data sharing
Features: The fastest inter-process communication method, the life cycle follows the kernel
Shared memory directly accesses physical memory through virtual addresses to achieve data sharing. Compared with other methods, data needs to be transferred Copy to the kernel and copy to user mode when used, eliminating two data copy operations
Note: You need to pay attention to security issues when operating shared memory Operation process:
①Create or open shared memory
being mapped to the virtual address space of the process and the shared memory is mapped to the virtual address space of the process.
##int shmget(key_t key, size_t size, int shmflg);
key: identifier (multiple processes open the same shared memory through the same identifier) size: The size of the space opened during creation (in memory pages) shmflg: Opening method Creation permission--IPC_CREAT|IPC_EXCL|0664--Operation handle; failure returns -1
void *shmat(int shmid, const void *shmaddr, int shmflg);
shmid: the operation handle returned by shmget shmaddr: mapping address, usually set to NULLint shmdt(const void *shmaddr);
int shmdt(const void *shmaddr); #
int shmctl(int shmid, int cmd, struct shmid_ds *buf);shmid: the operation handle returned by shmget
cmd: operation type--IPC_RMID Mark shared memory Is destroyed buf: For IPC_RMID, 0 is returned on success, -1 is returned on failure
·Message Queue
Essence: A priority queue in the kernel. Multiple processes access the same queue and add or obtain nodes to the queue to realize data block transmission between processes
Features: Built-in synchronization and mutual exclusion, life The cycle changes with the kernel
·Semaphore
Essence: a counter pcb waiting queue in the kernel Function: used for Realize synchronization and mutual exclusion between processes, and coordinate access to critical resources by processes
P operation: Counter -1, judge if the count is less than 0, block the process
V operation: Counter 1, wake up A blocked process
counts resources through its own counter, and uses the counting to determine whether the process's acquisition of resources is reasonable. If it is not reasonable, it will be blocked. After waiting for a resource to be generated, wake up the blocked process Synchronous implementation: Count the resource through a counter, and perform P operation before acquiring the resource Mutually exclusive implementation: The counter is 1, which means There is only one resource. The process performs P operation before accessing the resource and performs V operation after accessing the resource
Related recommendations: "Linux Video Tutorial"
The above is the detailed content of Classic techniques for Linux inter-process communication. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
VS Code system requirements: Operating system: Windows 10 and above, macOS 10.12 and above, Linux distribution processor: minimum 1.6 GHz, recommended 2.0 GHz and above memory: minimum 512 MB, recommended 4 GB and above storage space: minimum 250 MB, recommended 1 GB and above other requirements: stable network connection, Xorg/Wayland (Linux)
 Linux Architecture: Unveiling the 5 Basic Components
Apr 20, 2025 am 12:04 AM
Linux Architecture: Unveiling the 5 Basic Components
Apr 20, 2025 am 12:04 AM
The five basic components of the Linux system are: 1. Kernel, 2. System library, 3. System utilities, 4. Graphical user interface, 5. Applications. The kernel manages hardware resources, the system library provides precompiled functions, system utilities are used for system management, the GUI provides visual interaction, and applications use these components to implement functions.
 How to run java code in notepad
Apr 16, 2025 pm 07:39 PM
How to run java code in notepad
Apr 16, 2025 pm 07:39 PM
Although Notepad cannot run Java code directly, it can be achieved by using other tools: using the command line compiler (javac) to generate a bytecode file (filename.class). Use the Java interpreter (java) to interpret bytecode, execute the code, and output the result.
 vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
The reasons for the installation of VS Code extensions may be: network instability, insufficient permissions, system compatibility issues, VS Code version is too old, antivirus software or firewall interference. By checking network connections, permissions, log files, updating VS Code, disabling security software, and restarting VS Code or computers, you can gradually troubleshoot and resolve issues.
 vscode terminal usage tutorial
Apr 15, 2025 pm 10:09 PM
vscode terminal usage tutorial
Apr 15, 2025 pm 10:09 PM
vscode built-in terminal is a development tool that allows running commands and scripts within the editor to simplify the development process. How to use vscode terminal: Open the terminal with the shortcut key (Ctrl/Cmd). Enter a command or run the script. Use hotkeys (such as Ctrl L to clear the terminal). Change the working directory (such as the cd command). Advanced features include debug mode, automatic code snippet completion, and interactive command history.
 How to check the warehouse address of git
Apr 17, 2025 pm 01:54 PM
How to check the warehouse address of git
Apr 17, 2025 pm 01:54 PM
To view the Git repository address, perform the following steps: 1. Open the command line and navigate to the repository directory; 2. Run the "git remote -v" command; 3. View the repository name in the output and its corresponding address.
 Where to write code in vscode
Apr 15, 2025 pm 09:54 PM
Where to write code in vscode
Apr 15, 2025 pm 09:54 PM
Writing code in Visual Studio Code (VSCode) is simple and easy to use. Just install VSCode, create a project, select a language, create a file, write code, save and run it. The advantages of VSCode include cross-platform, free and open source, powerful features, rich extensions, and lightweight and fast.
 Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
VS Code is available on Mac. It has powerful extensions, Git integration, terminal and debugger, and also offers a wealth of setup options. However, for particularly large projects or highly professional development, VS Code may have performance or functional limitations.





