What happens when w3wp.exe modifies the memory of php-cgi?
出现“w3wp.exe修改php-cgi的内存”是因为D盾为了支持同一个服务器支持多PHP版本,所以D盾是在加载php的php-cgi.exe进程时加入D盾保护的。

本文操作环境:Windows7系统、PHP7.1版、DELL G3电脑
w3wp.exe怎么修改php-cgi的内存?
关于使用D盾,安全狗提示w3wp.exe修改php-cgi.exe内存的说明
关于使用D盾,服务器安全狗提示 w3wp.exe 修改 php-cgi.exe 内存的一些说明
最近看到安全狗新版,会有这样的提示。
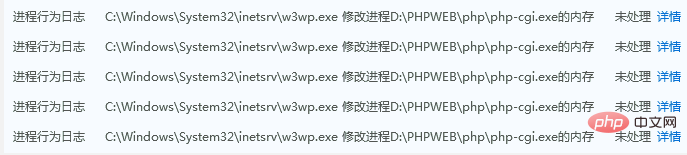
为了减少误解,还是说说这事!
D盾为了支持同一个服务器支持多PHP版本,所以D盾是在加载php的php-cgi.exe进程时加入D盾保护的。
需要在启动php-cgi.exe时修改内存并让php-cgi.exe加载D盾的保护模块的DLL。
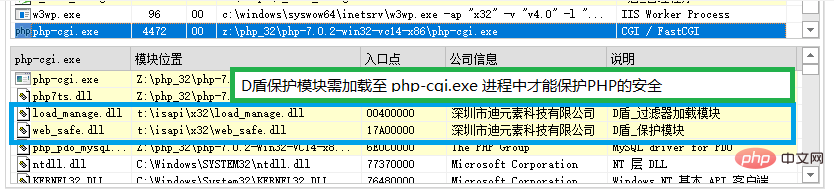
(最开始想通过php.ini配置来设置启动,但有些服务器上可能存在多个PHP版本,很容易疏漏,
也有可能用户动态修改或新增,无法及时得状态时就容易导致PHP没有做到保护,所以放弃这方案)
帖出一部份D盾的启动php-cgi并开启D盾保护的delphi代码
(为防止黑客了解太多细节,忽略一些细节):
// ######################################################## // HOOK执行函数会到这里过滤处理 // ######################################################## function My_CreateProcessInternalW(dw1_: Pointer; lpApplicationName: LPCWSTR; lpCommandLine: LPWSTR; lpProcessAttributes, lpThreadAttributes : PSecurityAttributes; bInheritHandles: BOOL; dwCreationFlags: dword; lpEnvironment: Pointer; lpCurrentDirectory: LPCWSTR; const lpStartupInfo: TStartupInfoW; var lpProcessInformation: TProcessInformation; Dw2: Pointer): BOOL; stdcall; var re_add: HMODULE; is_64_pe: boolean; Err_index: integer; ImageBaseAddress, AddressOfEntryPoint_: PVOID64; P_NT_HEAD_32: PImageNtHeaders32; // NT头 P_NT_HEAD_64: PImageNtHeaders64; // NT头 NtHead_: TImageNtHeaders64; // NT头 dwSize: SIZE_T; D_Safe_X32_load_manage_A: WideString; str: string; lpEnvironment_str: AnsiString; inf_: PWeb_Http_Context; Re_Fun_Add: HMODULE; App_, com_, com_exe_path, dir_: string; re_app_, re_cs_: string; App_len, Com_len: dword; comlin_inf_: TFilePath_pak; App_inf_: TFilePath_pak; Ex_Style_: dword; state_: integer; Nt_Head_add_: PVOID64; //简化了的进程创建函数 function CreateProcessInternalW_do(): BOOL; begin Result := CreateProcessInternalW_(dw1_, lpApplicationName, lpCommandLine, lpProcessAttributes, lpThreadAttributes, bInheritHandles, dwCreationFlags, lpEnvironment, lpCurrentDirectory, lpStartupInfo, lpProcessInformation, Dw2); end; //执行php-cgi.exe并加载D盾的保护 function RUN_PHP_FCGI(): boolean; var err_: integer; Function Kill_pro(pid_: dword): boolean; begin Result := false; // 显示不支持保护信息 // 32位池的D盾保护模块无法对64位的PHP做保护,请把池改为64位或使用32位的PHP版本 d_msg_(c_no_Support_64_php, NIIF_ERROR_); // 结束进程 TerminateProcess(OpenProcess(PROCESS_TERMINATE, false, pid_), $FFFFFFFF); SetLastError(5); end; begin // 创建php-cgi进程 Result := CreateProcessInternalW_do(); if Result then begin // 读到指定进程的NT头信息 ImageBaseAddress := D_Get_Process_NtHeaders(lpProcessInformation.hProcess, NtHead_, is_64_pe, Nt_Head_add_); if ImageBaseAddress > 0 then begin // 如果是64位进程时 if is_64_pe then begin P_NT_HEAD_64 := @NtHead_; AddressOfEntryPoint_ := ImageBaseAddress + P_NT_HEAD_64.OptionalHeader.AddressOfEntryPoint; //如果当前的iis进程不是64位的,并 php-cgi 的入口位置大于0x100000000时 if (D_IS_Win64_Project() = false) and (AddressOfEntryPoint_ >= $100000000) then begin case WIN_Ver_ of _WIN_VER_2003, _WIN_VER_2008: begin // 写入D盾的 64位的 load_manage.dll if Run_x64_LdrLoadDll(lpProcessInformation.hProcess, WIN_INF_.D_Safe_X64_load_manage) = false then begin // 失败时,结束进程 Result := Kill_pro(lpProcessInformation.hProcess); exit; end else begin Result := true; SetLastError(0); exit; end; end; _WIN_VER_2012: begin // 不支持保护时,结束进程 Result := Kill_pro(lpProcessInformation.hProcess); exit; end; end; end else begin // 写入D盾的 load_manage.dll if D_Write_DLL_To_Process(lpProcessInformation.hProcess, AddressOfEntryPoint_, WIN_INF_.D_Safe_X64_load_manage, true) then begin Result := true; SetLastError(0); exit; end else begin // 写入失败时结束php-cgi进程 Result := Kill_pro(lpProcessInformation.hProcess); exit; end; end; end else begin // 32位程序时 P_NT_HEAD_32 := @NtHead_; AddressOfEntryPoint_ := ImageBaseAddress + P_NT_HEAD_32.OptionalHeader.AddressOfEntryPoint; dwSize := sizeof(TSet_Fun_ADD_Head_32); // 写入D盾的 load_manage.dll if D_Write_DLL_To_Process(lpProcessInformation.hProcess, AddressOfEntryPoint_, WIN_INF_.D_Safe_X32_load_manage, false) then begin Result := true; SetLastError(0); exit; end else begin // 写入失败时结束php-cgi进程 Result := Kill_pro(lpProcessInformation.hProcess); exit; end; end; end else begin // 结束php-cgi进程 Result := Kill_pro(lpProcessInformation.hProcess); exit; end; end; end; begin .... //前面的代码,忽略 // ###################################################### // 如果是 PHP-cgi.exe // ###################################################### if ( .... //忽略掉一些代码 ) and (Pos(CONST_PHP_CGI, App_) > 0) and ((Com_len - App_len) = 2) then begin // 执行PHP-cgi.exe,并加入D盾的保护模块 Result := RUN_PHP_FCGI(); exit; end; ... //后面的代码,忽略
如需查看汇编代码,可以运行D盾WEB保护的情况下,用OllyICE调试 w3wp.exe 进程。
并选定并调试 web_safe.dll,查找字符 php-cgi.exe 即可快速定位相关代码位置
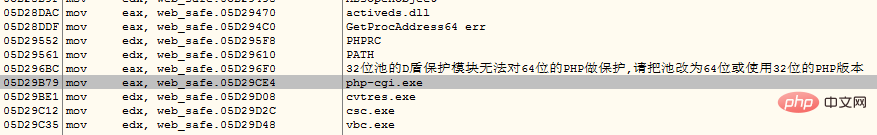
如下代码为 d_safe_2.1.4.4版本的 x32\web_safe.dll 汇编代码
05ED9B20 /E9 73010000 jmp web_safe.05ED9C98 05ED9B25 |8B45 28 mov eax, dword ptr [ebp+28] 05ED9B28 |50 push eax 05ED9B29 |8B85 B0FEFFFF mov eax, dword ptr [ebp-150] 05ED9B2F |E8 5C0BDEFF call web_safe.05CBA690 05ED9B34 |8D95 5EFCFFFF lea edx, dword ptr [ebp-3A2] 05ED9B3A |33C9 xor ecx, ecx 05ED9B3C |E8 BF82FAFF call web_safe.05E81E00 05ED9B41 |8D85 B8FEFFFF lea eax, dword ptr [ebp-148] 05ED9B47 |8B95 5EFCFFFF mov edx, dword ptr [ebp-3A2] 05ED9B4D |E8 A60BDEFF call web_safe.05CBA6F8 05ED9B52 |8D85 5EFCFFFF lea eax, dword ptr [ebp-3A2] 05ED9B58 |E8 1F67FAFF call web_safe.05E8027C 05ED9B5D |837D 20 00 cmp dword ptr [ebp+20], 0 05ED9B61 |74 3B je short web_safe.05ED9B9E 05ED9B63 |0FB785 62FCFFFF movzx eax, word ptr [ebp-39E] 05ED9B6A |3BF0 cmp esi, eax 05ED9B6C |75 30 jnz short web_safe.05ED9B9E 05ED9B6E |B9 01000000 mov ecx, 1 05ED9B73 |8B95 C0FEFFFF mov edx, dword ptr [ebp-140] 05ED9B79 |B8 E49CED05 mov eax, web_safe.05ED9CE4 ; php-cgi.exe 05ED9B7E |E8 F910DEFF call web_safe.05CBAC7C 05ED9B83 |85C0 test eax, eax 05ED9B85 |7E 17 jle short web_safe.05ED9B9E 05ED9B87 |2BFE sub edi, esi 05ED9B89 |83FF 02 cmp edi, 2 05ED9B8C |75 10 jnz short web_safe.05ED9B9E 05ED9B8E |55 push ebp 05ED9B8F |E8 A8FBFFFF call web_safe.05ED973C ; 进入 RUN_PHP_FCGI 函数 05ED9B94 |59 pop ecx 05ED9B95 |F6D8 neg al 05ED9B97 |1BDB sbb ebx, ebx 05ED9B99 |E9 FA000000 jmp web_safe.05ED9C98
D盾程序无壳,易调试,欢迎技术朋友监督。一直认为第三方的监督才是最好的监督。
--------------------------------------------------------------------------------
最后想说的是,如果禁止D盾在启动php-cgi.exe时修改内存,将会结束php-cgi.exe或无法保护,请不要禁止。
如果用户觉得需要一个开关来设置保护或不保护PHP的话,请和 啊D QQ:9269563 说说,视用户反馈情况看
是否要增加一个关掉PHP保护的开关。
D盾为了实现保护,需要大量HOOK相关API来实现保护,大部份都是需要修改汇编代码的内存来实现的,
所以以后不再讨论修改内存之类的问题,在此声明一下!
推荐学习:《PHP视频教程》
The above is the detailed content of What happens when w3wp.exe modifies the memory of php-cgi?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 OWASP Top 10 PHP: Describe and mitigate common vulnerabilities.
Mar 26, 2025 pm 04:13 PM
OWASP Top 10 PHP: Describe and mitigate common vulnerabilities.
Mar 26, 2025 pm 04:13 PM
The article discusses OWASP Top 10 vulnerabilities in PHP and mitigation strategies. Key issues include injection, broken authentication, and XSS, with recommended tools for monitoring and securing PHP applications.
 PHP Secure File Uploads: Preventing file-related vulnerabilities.
Mar 26, 2025 pm 04:18 PM
PHP Secure File Uploads: Preventing file-related vulnerabilities.
Mar 26, 2025 pm 04:18 PM
The article discusses securing PHP file uploads to prevent vulnerabilities like code injection. It focuses on file type validation, secure storage, and error handling to enhance application security.
 PHP API Rate Limiting: Implementation strategies.
Mar 26, 2025 pm 04:16 PM
PHP API Rate Limiting: Implementation strategies.
Mar 26, 2025 pm 04:16 PM
The article discusses strategies for implementing API rate limiting in PHP, including algorithms like Token Bucket and Leaky Bucket, and using libraries like symfony/rate-limiter. It also covers monitoring, dynamically adjusting rate limits, and hand
 PHP Input Validation: Best practices.
Mar 26, 2025 pm 04:17 PM
PHP Input Validation: Best practices.
Mar 26, 2025 pm 04:17 PM
Article discusses best practices for PHP input validation to enhance security, focusing on techniques like using built-in functions, whitelist approach, and server-side validation.
 PHP XSS Prevention: How to protect against XSS.
Mar 26, 2025 pm 04:12 PM
PHP XSS Prevention: How to protect against XSS.
Mar 26, 2025 pm 04:12 PM
The article discusses strategies to prevent XSS attacks in PHP, focusing on input sanitization, output encoding, and using security-enhancing libraries and frameworks.
 ACID vs BASE Database: Differences and when to use each.
Mar 26, 2025 pm 04:19 PM
ACID vs BASE Database: Differences and when to use each.
Mar 26, 2025 pm 04:19 PM
The article compares ACID and BASE database models, detailing their characteristics and appropriate use cases. ACID prioritizes data integrity and consistency, suitable for financial and e-commerce applications, while BASE focuses on availability and
 PHP Password Hashing: password_hash and password_verify.
Mar 26, 2025 pm 04:15 PM
PHP Password Hashing: password_hash and password_verify.
Mar 26, 2025 pm 04:15 PM
The article discusses the benefits of using password_hash and password_verify in PHP for securing passwords. The main argument is that these functions enhance password protection through automatic salt generation, strong hashing algorithms, and secur
 PHP Interface vs Abstract Class: When to use each.
Mar 26, 2025 pm 04:11 PM
PHP Interface vs Abstract Class: When to use each.
Mar 26, 2025 pm 04:11 PM
The article discusses the use of interfaces and abstract classes in PHP, focusing on when to use each. Interfaces define a contract without implementation, suitable for unrelated classes and multiple inheritance. Abstract classes provide common funct






