What protocol does the 'ping' command use?

What protocol does the "ping" command use?
The "ping" command uses the ICMP protocol, which is a sub-protocol of the TCP/IP protocol suite and is used to transmit control messages between IP hosts and routers. The control message indicates whether the network is connected or not. , whether the host is reachable, whether the route is available, and other information about the network itself.
ICMP protocol
ICMP protocol is a connectionless-oriented protocol used to transmit error reporting control information. It is a very important protocol and it is extremely important for network security. It is a network layer protocol and is mainly used to transfer control information between hosts and routers, including reporting errors, exchanging restricted control and status information, etc. When IP data cannot access the target or the IP router cannot forward data packets at the current transmission rate, ICMP messages will be automatically sent.
ICMP is an important member of the network layer in the TCP/IP model. Together with the IP protocol, ARP protocol, RARP protocol and IGMP protocol, it constitutes the network layer in the TCP/IP model. Ping and tracert are two commonly used network management commands. Ping is used to test network reachability, and tracert is used to display the path to the destination host. Both ping and tracert use the ICMP protocol to implement network functions. They are typical examples of applying network protocols to daily network management.
From a technical perspective, ICMP is an "error detection and reporting mechanism". Its purpose is to allow us to detect the network connection status and ensure the accuracy of the connection. When an accident occurs while the router is processing a data packet, it can report the relevant event to the source of the data packet through ICMP.
Its main functions include: detecting the existence of remote hosts, establishing and maintaining routing data, redirecting data transmission paths (ICMP redirection), and data flow control. During communication, ICMP mainly uses different categories (Type) and codes (Code) to allow machines to identify different connection conditions.
ICMP is a very useful protocol, especially when we need to judge the network connection status.
Recommended tutorial "PHP"
The above is the detailed content of What protocol does the 'ping' command use?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to fix Xbox Series S/X download speeds, reduced ping and lag
Apr 16, 2023 pm 04:49 PM
How to fix Xbox Series S/X download speeds, reduced ping and lag
Apr 16, 2023 pm 04:49 PM
Xbox consoles have improved dramatically over the years. Over the years, games have evolved with life-like features that gamers can't seem to get enough of. Playing your favorite games on Xbox can be a completely engrossing experience. However, sometimes using these advanced features, we end up with lag or ping issues if the internet speed is not that good. Sometimes we want games to download faster. Today, games like Forza Horizon 5 and Mortal Kombat require over 100GB of RAM. Downloading such games can take a long time if we don't have the right internet settings to help us. Method 1: Pass
 What is the reason for the ping request timeout?
Aug 28, 2023 pm 04:17 PM
What is the reason for the ping request timeout?
Aug 28, 2023 pm 04:17 PM
The reasons for the ping request timeout include unreachable target host, network congestion, firewall or security settings, and DNS resolution issues. Detailed introduction: 1. The target host is unreachable. The Ping request timeout may mean that the target host cannot be accessed through the network. This may be due to the target host closing the network connection, the network where the target host is located failing, the target host IP address being set incorrectly, etc. ; 2. Network congestion. Ping request timeout may also be caused by network congestion. Network congestion may be due to large amounts of data transmission, network equipment failures, etc.
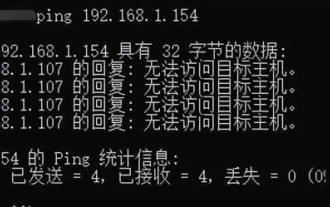 Why can't I ping the gateway? Why can't ping?
Mar 13, 2024 pm 03:40 PM
Why can't I ping the gateway? Why can't ping?
Mar 13, 2024 pm 03:40 PM
The network cannot ping, what's going on? In fact, this is a very common problem. It is mainly divided into two situations: pinging fails on the same network segment and pinging fails on different network segments. Let’s take a look at the details below. There are usually two reasons why the ping command cannot connect to the same network segment: one is an IP address that cannot be pinged in the same network segment, and the other is an IP address that cannot be pinged in a different network segment. These two situations have different solutions. First, let’s discuss the situation where ping fails within the same network segment. 1. Ping fails on the same network segment, and the result is "Unable to access the target host." The destination IP and source IP are on the same network segment, and the ping result is &l
 How to solve the error message 'ping is not recognized as an internal or external command or an operable program'
Feb 22, 2023 pm 04:28 PM
How to solve the error message 'ping is not recognized as an internal or external command or an operable program'
Feb 22, 2023 pm 04:28 PM
Solution: 1. Click the "Start" button, click "Control Panel" - "System" in the start menu; 2. In the settings interface, click "Advanced System Settings" - "Advanced" - "Environment Variables"; 3. . Check whether there is a Path variable in Administrator's user variables. If you do not see this variable, click "New" and add the variable Path and variable value.
 What are the reasons why the IP address cannot be pinged?
Dec 15, 2020 pm 04:37 PM
What are the reasons why the IP address cannot be pinged?
Dec 15, 2020 pm 04:37 PM
The reasons why the IP address cannot be pinged are: 1. The other party is shut down or the IP address does not exist; 2. The network segment is different and cannot be found through routing; 3. The firewall filters the ICMP packets sent by ping; 4. The IP address is set incorrectly; 5. Network cable failure; 6. The gateway is not set.
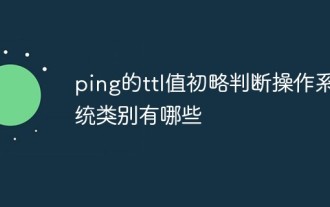 The ttl value of ping briefly determines the operating system categories.
May 22, 2023 am 09:04 AM
The ttl value of ping briefly determines the operating system categories.
May 22, 2023 am 09:04 AM
The type of some operating systems can often be roughly judged by the ttl value of ping. Here is a summary: The TTL field value of the ICMP echo response of UNIX and UNIX-like operating systems is 255. CompaqTru645.0 The TTL field value of the ICMP echo response is 64. The TTL field value of the ICMP echo response of the Microsoft Windows NT/2K operating system is 128. The TTL field value of the ICMP echo response of the Microsoft Windows 95 operating system is 32. Of course, these ttl values can also be changed. Windows series systems can modify the following key values in the registry. Implementation: [HKEY_LOCAL_MACHINE\system\Curren
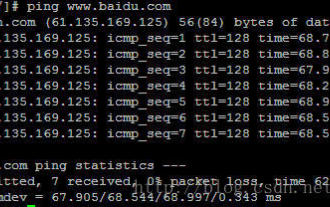 Several simple examples of using the linux ping command
Jan 09, 2024 am 08:26 AM
Several simple examples of using the linux ping command
Jan 09, 2024 am 08:26 AM
I found that there are quite a lot of ping commands under Linux. Here are a few examples: 1. pingwww.baidu.com, the roughest usage. At this time, the host will continue to send ICMPechorequest packets to the destination address until you press Ctrl +c2, ping-Ieth0www.baidu.com or ping-I192.168.8.151www.baidu.com, that is, the -I option can specify the network card that sends the ping packet. -I can be followed by the network card name or the IP address of the network card. 3. Ping-c3www.baidu.com, the -c option can specify how many ICMP packets to send, and you can see the host connection
 what is ping
Aug 04, 2023 pm 01:31 PM
what is ping
Aug 04, 2023 pm 01:31 PM
Ping is a computer network tool used to test connectivity between hosts. By sending ICMP echo request messages to determine whether the target host is reachable, and measuring indicators such as round-trip delay time and packet loss rate, ping can help programmers diagnose network problems, optimize network performance, and ensure the stability of network connections.





