There are several aspects of network security
Network security mainly includes system security, network security, information dissemination security, and information content security. The details are as follows:

1. System security
Operating system security means ensuring the security of the information processing and transmission system. Focus on ensuring the normal operation of the system. Avoid damage and loss to messages stored, processed and transmitted by the system due to system collapse and damage. Avoid information leakage due to electromagnetic leakage, interfering with others or being interfered by others. (Recommended learning: web front-end video tutorial)
2. Network security
The security of system information on the network, including user password authentication, User access rights control, data access rights, method control, security audit. Safety issues follow. Computer virus prevention, data encryption, etc.
3. Information dissemination security
The security of information dissemination on the Internet refers to the safety of the consequences of information dissemination, including information filtering, etc. It focuses on preventing and controlling the consequences of the dissemination of illegal and harmful information, and avoiding the loss of control of information freely transmitted on public networks.
4. Information content security
The security of information content on the Internet focuses on protecting the confidentiality, authenticity and integrity of information. Prevent attackers from exploiting system security vulnerabilities to conduct eavesdropping, impersonation, fraud, and other behaviors that are detrimental to legitimate users. Its essence is to protect the interests and privacy of users.
Tools for maintaining network security include VIEID, digital certificates, digital signatures, and local or cloud-based anti-virus software.
1. Internet Firewall
It can enhance the security of the organization’s internal network. Internet firewalls manage access between the Internet and the organization's internal network. Without a firewall, each node on the internal network is exposed to other hosts on the Internet and is extremely vulnerable to attacks. This means that the security of the internal network is determined by the strength of each host, and is as secure as the weakest system among them.
2, VIEID
In this network ecosystem, each network user can trust each other’s identity, and network users can also choose whether to have electronic identification. . In addition to increasing network security, electronic identification can also allow network users to create and apply more trusted virtual identities, allowing network users to remember less or even no need to remember those annoying passwords.
3. Digital certificate
The CA center adopts digital certificate authentication technology with digital encryption technology as the core. Through digital certificates, the CA center can Various types of transmitted information undergo various processing such as encryption, decryption, digital signature and signature authentication. It also ensures that the digital transmission process will not be invaded by criminals, or even if it is invaded, the contents will not be viewable.
The above is the detailed content of There are several aspects of network security. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
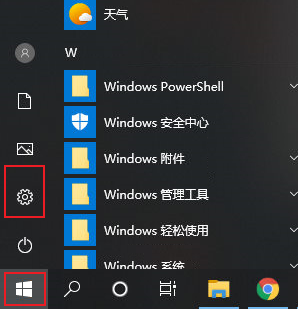 How to set up Win10 firewall whitelist? Win10 plus firewall whitelist
Jul 14, 2023 pm 03:18 PM
How to set up Win10 firewall whitelist? Win10 plus firewall whitelist
Jul 14, 2023 pm 03:18 PM
The built-in firewall function of win10 can block the attacks of some malicious programs for us, but occasionally it may be blocked by the firewall and prevent the program from being installed normally. If we can understand the security of this software and the importance of installation, then we can allow the installation by adding a whitelist to the firewall. 1. Use the win key to open the win10 system menu window, and click on the left side of the menu window to open the "Settings" dialog box. 2. In the Windows Settings dialog box that opens, you can look for the "Update & Security" item and click to open it. 3. After entering the upgrade and security policy page, click the "Windows Security Manager" sub-menu in the left toolbar. 4. Then in the specific content on the right
 Master network security and penetration testing in Go
Nov 30, 2023 am 10:16 AM
Master network security and penetration testing in Go
Nov 30, 2023 am 10:16 AM
With the development of the Internet, network security has become an urgent issue. For technical personnel engaged in network security work, it is undoubtedly necessary to master an efficient, stable, and secure programming language. Among them, Go language has become the first choice of many network security practitioners. Go language, referred to as Golang, is an open source programming language created by Google. The language has outstanding features such as high efficiency, high concurrency, high reliability and high security, so it is widely used in network security and penetration testing.
 Artificial Intelligence in Cybersecurity: Current Issues and Future Directions
Mar 01, 2024 pm 08:19 PM
Artificial Intelligence in Cybersecurity: Current Issues and Future Directions
Mar 01, 2024 pm 08:19 PM
Artificial intelligence (AI) has revolutionized every field, and cybersecurity is no exception. As our reliance on technology continues to increase, so do the threats to our digital infrastructure. Artificial intelligence (AI) has revolutionized the field of cybersecurity, providing advanced capabilities for threat detection, incident response, and risk assessment. However, there are some difficulties with using artificial intelligence in cybersecurity. This article will delve into the current status of artificial intelligence in cybersecurity and explore future directions. The role of artificial intelligence in cybersecurity Governments, businesses and individuals are facing increasingly severe cybersecurity challenges. As cyber threats become more sophisticated, the need for advanced security protection measures continues to increase. Artificial intelligence (AI) relies on its unique method to identify, prevent
 How do C++ functions implement network security in network programming?
Apr 28, 2024 am 09:06 AM
How do C++ functions implement network security in network programming?
Apr 28, 2024 am 09:06 AM
C++ functions can achieve network security in network programming. Methods include: 1. Using encryption algorithms (openssl) to encrypt communication; 2. Using digital signatures (cryptopp) to verify data integrity and sender identity; 3. Defending against cross-site scripting attacks ( htmlcxx) to filter and sanitize user input.
 Ten methods in AI risk discovery
Apr 26, 2024 pm 05:25 PM
Ten methods in AI risk discovery
Apr 26, 2024 pm 05:25 PM
Beyond chatbots or personalized recommendations, AI’s powerful ability to predict and eliminate risks is gaining momentum in organizations. As massive amounts of data proliferate and regulations tighten, traditional risk assessment tools are struggling under the pressure. Artificial intelligence technology can quickly analyze and supervise the collection of large amounts of data, allowing risk assessment tools to be improved under compression. By using technologies such as machine learning and deep learning, AI can identify and predict potential risks and provide timely recommendations. Against this backdrop, leveraging AI’s risk management capabilities can ensure compliance with changing regulations and proactively respond to unforeseen threats. Leveraging AI to tackle the complexities of risk management may seem alarming, but for those passionate about staying on top in the digital race
 Roborock sweeping robot passed Rheinland dual certification, leading the industry in corner cleaning and sterilization
Mar 19, 2024 am 10:30 AM
Roborock sweeping robot passed Rheinland dual certification, leading the industry in corner cleaning and sterilization
Mar 19, 2024 am 10:30 AM
Recently, TUV Rheinland Greater China ("TUV Rheinland"), an internationally renowned third-party testing, inspection and certification agency, issued important network security and privacy protection certifications to three sweeping robots P10Pro, P10S and P10SPro owned by Roborock Technology. certificate, as well as the "Efficient Corner Cleaning" China-mark certification. At the same time, the agency also issued self-cleaning and sterilization performance test reports for sweeping robots and floor washing machines A20 and A20Pro, providing an authoritative purchasing reference for consumers in the market. As network security is increasingly valued, TUV Rheinland has implemented strict network security and privacy protection for Roborock sweeping robots in accordance with ETSIEN303645 standards.
 The cybersecurity industry can draw inspiration from 'Musk's algorithm'
Nov 03, 2023 pm 05:13 PM
The cybersecurity industry can draw inspiration from 'Musk's algorithm'
Nov 03, 2023 pm 05:13 PM
Today, we have entered an era of disruptive innovation driven by artificial intelligence and digital transformation. In this era, network security is no longer just the "cost and friction" of enterprise IT. On the contrary, it has become a key fulcrum for building the next generation of digital infrastructure and information order, as well as all technological innovations (from drug research and development to military intelligent manufacturing) necessary elements. This means that traditional network security technology research and development, program implementation, defense system design and operation all need to undergo a revolution in methods and concepts. Agility and intelligence have become the two main themes of network security evolution. In short, network security A Musk-style "out of the circle" revolution is needed. From electric cars to rockets to Starlink and even Twitter (X), Musk shows us how to use "first
 How to install Zeek Internet Security Monitor 12 on Debian
Feb 19, 2024 pm 01:54 PM
How to install Zeek Internet Security Monitor 12 on Debian
Feb 19, 2024 pm 01:54 PM
Bro has been renamed Zeek and is a powerful open source network security monitor. It is not only an IDS, but also a network analysis framework. Zeek provides you with real-time insights into network operations to help detect and prevent security incidents. Its benefits include detailed network traffic logging, event-driven analysis and the ability to detect a wide range of network anomalies and security events. Install Zeek Internet Security Monitor 12 Bookworm on Debian Step 1. Before installing Zeek, you need to update and refresh your Debian repository by executing the following command: sudoaptupdatesudoaptupgrade This command will update the package list for upgrades and new package installations. Step 2. Install ZeekN on Debian





