 WeChat Applet
WeChat Applet
 Mini Program Development
Mini Program Development
 WeChat Mini Program Authorization Login Process Timing - Detailed Graphical Explanation
WeChat Mini Program Authorization Login Process Timing - Detailed Graphical Explanation
WeChat Mini Program Authorization Login Process Timing - Detailed Graphical Explanation
I am currently working on a WeChat applet development project. Scenario layout: APPs and WeChat mini programs with the same subject under the same WeChat open platform complete the same business. When users enter the app or WeChat mini program, they must obtain the user's unionid to confirm the current user identity and complete the login. The calling method of the mini program's "get user information" api (getUserInfo) has been greatly updated compared to before. It is very important to elegantly implement user authorization and login. The following is my implementation of the WeChat mini program authorization login process during development. The ideas and summary are shared below.
1. WeChat applet login process timing sequence
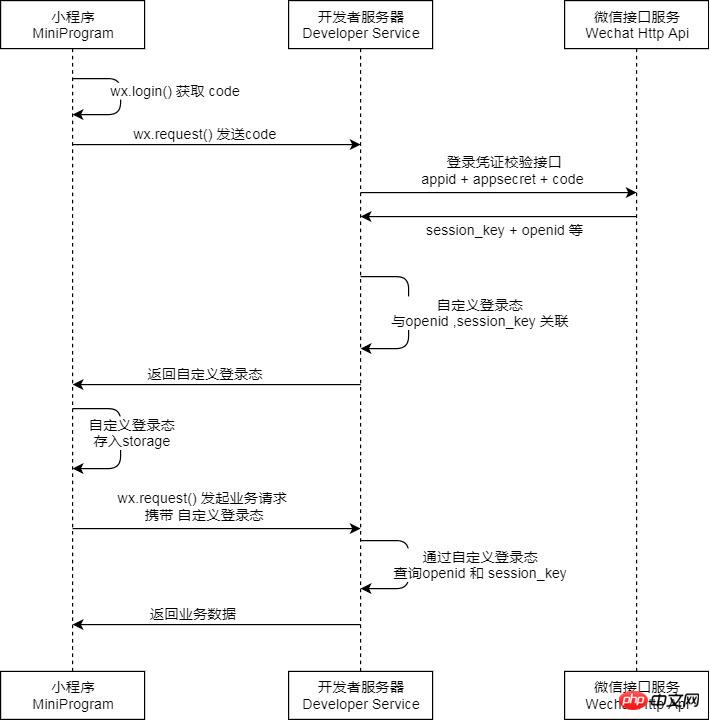
Instructions:
The applet calls wx.login( ) Get the temporary login credential code and send it back to the developer server
The developer server exchanges the code for the user's unique identifier openid and session key session_key.
The temporary login credential code can only be used once
What is openid?
Generate messages between followers and public accounts After interaction, the official account can obtain the follower's OpenID (encrypted WeChat ID, each user's OpenID for each official account is unique. For different official accounts, the same user's openid is different). ——WeChat public platform developer documentation
The identification of ordinary users, unique to the current public account
Different public accounts, the same user , openid is different
You can simply understand it as
openid = hash(uid + app_id)
What is unionid?
If the developer has multiple mobile applications, website applications, and public accounts (including mini programs), the user can be uniquely distinguished by unionid, because as long as they are mobile applications under the same WeChat open platform account , website applications and public accounts (including mini programs), the user's unionid is unique. In other words, for the same user, the unionid is the same for different applications under the same WeChat open platform. UnionID mechanism description
If a developer needs to unify user accounts among multiple mobile applications, website applications and public accounts, he needs to go to the WeChat open platform (open.weixin.qq.com) to bind the public account Then, the UnionID mechanism can be used to meet the above needs.
One WeChat open platform account can have multiple mobile applications, website applications, public accounts and mini programs
As long as it is the same WeChat For mobile applications, website applications and public accounts (including mini programs) under open platform accounts, the user's unionid is unique.
The user’s unique identifier on the open platform
You can simply understand it as:
unionid = hash(uid + 开放平台id)
Summary
WeChat has a unique openId for different users in different applications, but if you want to determine whether the users are the same user, you need to rely on unionid to distinguish. Generally, your own backend will have its own user table, and each user has a different userid. That is to say, the same user's applications of the same subject under the same WeChat open platform correspond to the same userid, unionid and different openid. So when a user logs in, we can only rely on the unionid returned to us by WeChat to determine whether it is the same user, and then associate it with our user table to get the corresponding userid.
2. How do WeChat mini programs obtain unionid?
Mini programs bound to a developer account can obtain UnionID through the following three methods.
Call the interface wx.getUserInfo to obtain the UnionID from the decrypted data. Note that this interface requires user authorization. Developers should properly handle the situation after the user refuses authorization.
If there is a public account with the same subject under the developer account, and the user has already followed the public account. Developers can obtain the user's UnionID directly through wx.login without the user's authorization again.
If there is a public account or mobile application of the same subject under the developer account, and the user has been authorized to log in to the public account or mobile application. Developers can also obtain the user's UnionID directly through wx.login without requiring the user to authorize again.
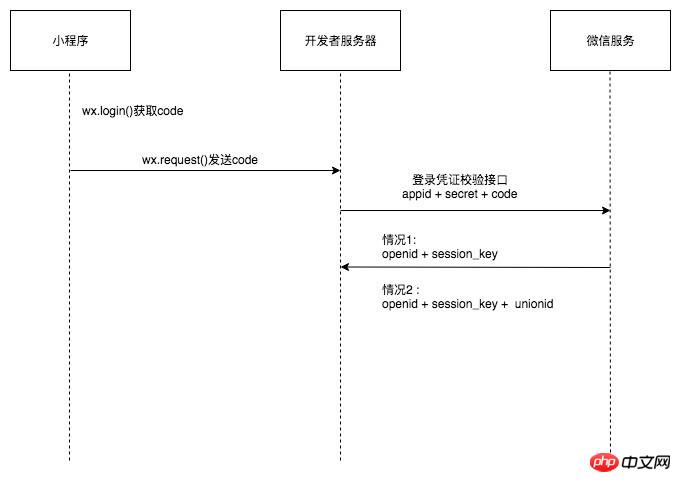
When the user meets conditions 2 and 3, the developer can directly obtain the user's unionid through wx.login, otherwise the interface must be calledwx.getUserInfo, extra attention needs to be paid to properly handling the situation where the user refuses authorization.
3. Login best practices
Call wx.login to get the code.
Use wx.getSetting to obtain the user's authorization status
If the user has been authorized, directly call API wx.getUserInfo to obtain the user's latest Information;
The user is not authorized. A button is displayed in the interface to prompt the user to log in. When the user clicks and authorizes, the user's latest information is obtained.
Pass the obtained user data to the backend together with the code returned by wx.login

Encapsulate ajax()
In real business scenarios, we hope that when users enter the mini program, they can browse the products normally without logging in, have a basic understanding of the mini program, and do not directly pop up the box Require user authorization, otherwise it will interfere with users and lead to the loss of new users. When users need to use some advanced functions and scenarios, ask users for authorization at this time, so that the probability of user authorization will be greatly increased.
Encapsulate the login logic with ajax
Process: 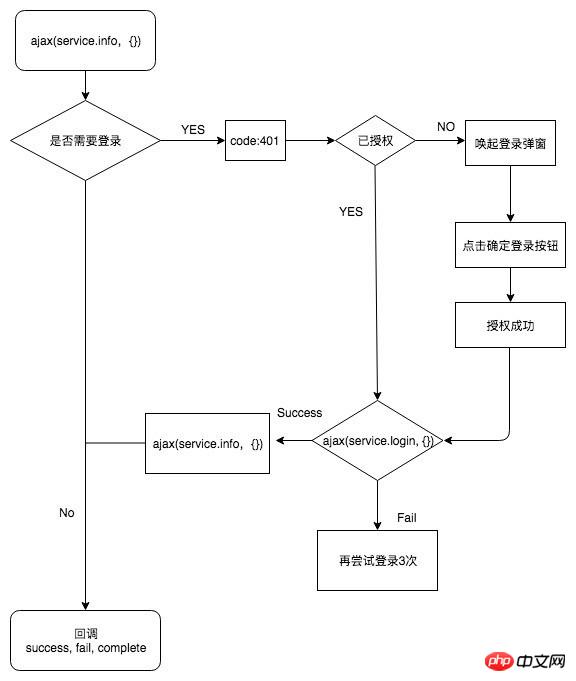
The meaning of encapsulation
No longer pay attention to whether the current interface requires login, whether the user has Authorization, all requests directly call ajax(), and complete all login and authorization processes when necessary. The entrance page of the mini program has been increased. When expanding your business, you only need to focus on business implementation.
Reference materials
Mini program •Small story (4)——Get user information
Get user basic information ( UnionID mechanism)
UnionID mechanism description
Related recommendations:
WeChat Mini Program Development Document
Practical video tutorial on developing WeChat mini program
Video tutorial on developing WeChat mini program
The above is the detailed content of WeChat Mini Program Authorization Login Process Timing - Detailed Graphical Explanation. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 The difference between H5 and mini-programs and APPs
Apr 06, 2025 am 10:42 AM
The difference between H5 and mini-programs and APPs
Apr 06, 2025 am 10:42 AM
H5. The main difference between mini programs and APP is: technical architecture: H5 is based on web technology, and mini programs and APP are independent applications. Experience and functions: H5 is light and easy to use, with limited functions; mini programs are lightweight and have good interactiveness; APPs are powerful and have smooth experience. Compatibility: H5 is cross-platform compatible, applets and APPs are restricted by the platform. Development cost: H5 has low development cost, medium mini programs, and highest APP. Applicable scenarios: H5 is suitable for information display, applets are suitable for lightweight applications, and APPs are suitable for complex functions.
 Ouyi Exchange app domestic download tutorial
Mar 21, 2025 pm 05:42 PM
Ouyi Exchange app domestic download tutorial
Mar 21, 2025 pm 05:42 PM
This article provides a detailed guide to safe download of Ouyi OKX App in China. Due to restrictions on domestic app stores, users are advised to download the App through the official website of Ouyi OKX, or use the QR code provided by the official website to scan and download. During the download process, be sure to verify the official website address, check the application permissions, perform a security scan after installation, and enable two-factor verification. During use, please abide by local laws and regulations, use a safe network environment, protect account security, be vigilant against fraud, and invest rationally. This article is for reference only and does not constitute investment advice. Digital asset transactions are at your own risk.
 What should I do if the company's security software conflicts with applications? How to troubleshoot HUES security software causes common software to fail to open?
Apr 01, 2025 pm 10:48 PM
What should I do if the company's security software conflicts with applications? How to troubleshoot HUES security software causes common software to fail to open?
Apr 01, 2025 pm 10:48 PM
Compatibility issues and troubleshooting methods for company security software and application. Many companies will install security software in order to ensure intranet security. However, security software sometimes...
 What is the difference between H5 page production and WeChat applets
Apr 05, 2025 pm 11:51 PM
What is the difference between H5 page production and WeChat applets
Apr 05, 2025 pm 11:51 PM
H5 is more flexible and customizable, but requires skilled technology; mini programs are quick to get started and easy to maintain, but are limited by the WeChat framework.
 How to solve the problem of JS resource caching in enterprise WeChat?
Apr 04, 2025 pm 05:06 PM
How to solve the problem of JS resource caching in enterprise WeChat?
Apr 04, 2025 pm 05:06 PM
Discussion on the JS resource caching issue of Enterprise WeChat. When upgrading project functions, some users often encounter situations where they fail to successfully upgrade, especially in the enterprise...
 How to choose H5 and applets
Apr 06, 2025 am 10:51 AM
How to choose H5 and applets
Apr 06, 2025 am 10:51 AM
The choice of H5 and applet depends on the requirements. For applications with cross-platform, rapid development and high scalability, choose H5; for applications with native experience, rich functions and platform dependencies, choose applets.
 Is the company's security software causing the application to fail to run? How to troubleshoot and solve it?
Apr 19, 2025 pm 04:51 PM
Is the company's security software causing the application to fail to run? How to troubleshoot and solve it?
Apr 19, 2025 pm 04:51 PM
Troubleshooting and solutions to the company's security software that causes some applications to not function properly. Many companies will deploy security software in order to ensure internal network security. ...
 Detailed tutorial on how to buy and sell Binance virtual currency
Mar 18, 2025 pm 01:36 PM
Detailed tutorial on how to buy and sell Binance virtual currency
Mar 18, 2025 pm 01:36 PM
This article provides a brief guide to buying and selling of Binance virtual currency updated in 2025, and explains in detail the operation steps of virtual currency transactions on the Binance platform. The guide covers fiat currency purchase USDT, currency transaction purchase of other currencies (such as BTC), and selling operations, including market trading and limit trading. In addition, the guide also specifically reminds key risks such as payment security and network selection for fiat currency transactions, helping users to conduct Binance transactions safely and efficiently. Through this article, you can quickly master the skills of buying and selling virtual currencies on the Binance platform and reduce transaction risks.





