 Backend Development
Backend Development
 C#.Net Tutorial
C#.Net Tutorial
 Use VS2010 C# to develop ActiveX controls (Part 2), complete code package download
Use VS2010 C# to develop ActiveX controls (Part 2), complete code package download
Use VS2010 C# to develop ActiveX controls (Part 2), complete code package download
In fact, if we do not set it up, but just modify the code, after running the program, the error interface will be as shown in Figure 1 below:
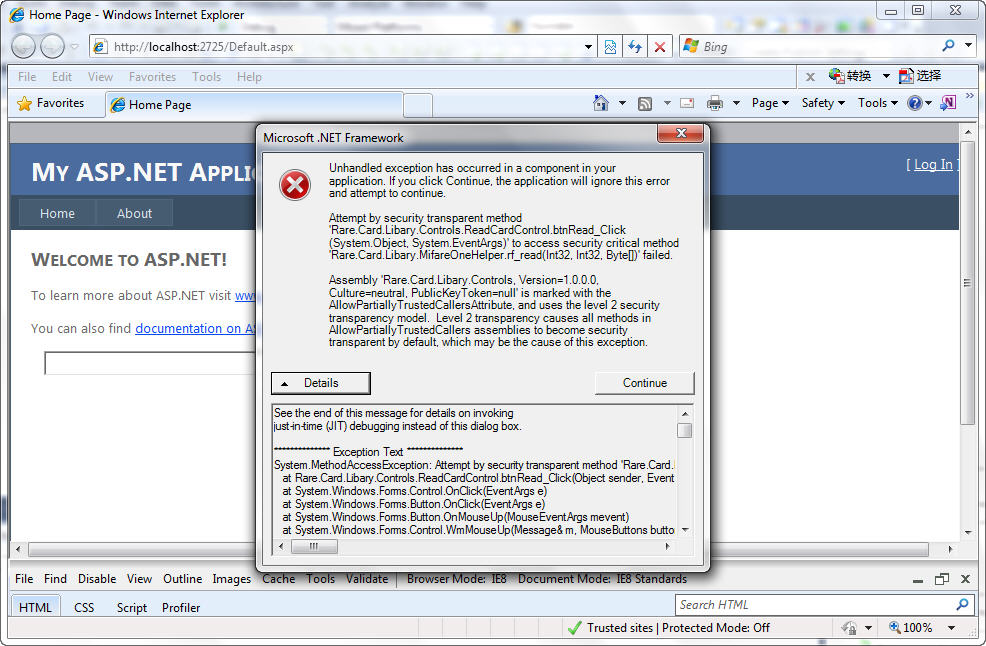
The exception thrown is as follows:
************** Exception Text **************
System.MethodAccessException: Attempt by security transparent method ' Rare.Card.Libary.Controls.
ReadCardControl.btnRead_Click(System.Object, System.EventArgs)' to call native code through method 'Rare.Card.Libary.MifareOneHelper.rf_read(Int32, Int32, Byte[ ])' failed. Methods must be security critical or
security safe-critical to call native code.
By consulting MSDN, the explanation of the exception is as follows:
In Microsoft .NET Framework 4, the common language runtime (CLR) security model has undergone many changes. One of the changes, the adoption of Level2 transparency (very similar to Silverlight's security model) is likely to affect the authors of the AllowPartiallyTrustedCallers (APTCA) library. There are three transparency attributes: SecurityTransparent, SecuritySafeCritical and SecurityCritical.
SecurityTransparent: Code marked as SecurityTransparent is reliable from a security perspective. It cannot accomplish any dangerous operations, such as asserting permissions,
executing unverifiable code, or calling native code. It also cannot call SecurityCritical code directly.
As mentioned above, for security reasons, all partially trusted code is forced to be SecurityTransparent. This is also the default transparency of the APTCA library.
SecurityCritical: Unlike SecurityTransparent, SecurityCritical code is able to perform any desired operation. It can perform declarations,
calls to native code, and other operations. It can call other methods without being restricted by the transparency flag.
Only fully trusted code can be SecurityCritical. In fact, (non-APTCA) fully trusted code is SecurityCritical by default,
thereby protecting it from calls by transparent partially trusted callers.
SecuritySafeCritical: SecuritySafeCritical code plays the role of a bridge, which allows transparent code to call key methods. SecuritySafeCritical
code has the same permissions as SecurityCritical code, but it can be called by SecurityTransparent code. Therefore, it is extremely important that SecuritySafeCritical code exposes the underlying SecurityCritical methods in a secure manner (to avoid some partially trusted malicious code trying to attack these methods through the SecuritySafeCritical layer).
Like SecurityCritical code, SecuritySafeCritical code must be fully trusted.
According to MSDN's explanation, the problem lies in the C# class library CardReader.Library that encapsulates the original Dll. We can set the transparency attribute at the code level to solve the problem.
The specific solution is as follows:
1. Set the transparent attribute of the ActiveX control card reading code to: SecuritySafeCritical. The code list after setting is as follows:[SecuritySafeCritical]
/// <summary>
/// 读卡
/// </summary>
/// <param name="sender"></param>
/// <param name="e"></param>
private void btnRead_Click(object sender, EventArgs e)
{
int i = 0;
byte[] data = new byte[16];
byte[] buff = new byte[32];
for (i = 0; i < 16; i++)
data[i] = 0;
for (i = 0; i < 32; i++)
buff[i] = 0;
st = MifareOneHelper.rf_read(icdev, sec * 4 + 1, data);
if (st == 0)
{
SerialInterfaceHelper.hex_a(data, buff, 16);
txtCardID.Text = System.Text.Encoding.ASCII.GetString(buff);
lblMsg.Text = "读取卡号成功!";
}
else
lblMsg.Text = "读取卡号失败!";
//test method
//if (string.IsNullOrEmpty(txtCardID.Text))
//{
// lblMsg.Text = "读取数据失败!";
//}
//else
//{
// lblMsg.Text = string.Format("读取数据:{0}!", txtCardID.Text);
//}
}Be careful to add a reference: using System .Security; The test code is commented out here, and the serial communication and card reading code are used.
2. Set the transparent attribute that encapsulates the original card reader Dll.
Set the transparent attribute of the M1 card reader helper class MifareOneHelper to: [SecurityCritical], and set the
transparent attribute of the called method MifareOneHelper.rf_read to [SecurityCritical].
Set the transparent attribute of the serial communication helper class SerialInterfaceHelper to: [SecurityCritical], and set the
transparent attribute of the called method SerialInterfaceHelper.hex_a to [SecurityCritical].
The complete code has been provided. There are two other things to note. If the client fails to install ActiveX, the address running ActiveX will be added to the trusted site.
The security level of the trusted site will be reduced to Minimize or set the Trust Sites option regarding ActiveX.
More on using VS2010 C# to develop ActiveX controls (Part 2), complete code package downloads, please pay attention to the PHP Chinese website for related articles!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use various symbols in C language
Apr 03, 2025 pm 04:48 PM
How to use various symbols in C language
Apr 03, 2025 pm 04:48 PM
The usage methods of symbols in C language cover arithmetic, assignment, conditions, logic, bit operators, etc. Arithmetic operators are used for basic mathematical operations, assignment operators are used for assignment and addition, subtraction, multiplication and division assignment, condition operators are used for different operations according to conditions, logical operators are used for logical operations, bit operators are used for bit-level operations, and special constants are used to represent null pointers, end-of-file markers, and non-numeric values.
 What is the role of char in C strings
Apr 03, 2025 pm 03:15 PM
What is the role of char in C strings
Apr 03, 2025 pm 03:15 PM
In C, the char type is used in strings: 1. Store a single character; 2. Use an array to represent a string and end with a null terminator; 3. Operate through a string operation function; 4. Read or output a string from the keyboard.
 How to handle special characters in C language
Apr 03, 2025 pm 03:18 PM
How to handle special characters in C language
Apr 03, 2025 pm 03:18 PM
In C language, special characters are processed through escape sequences, such as: \n represents line breaks. \t means tab character. Use escape sequences or character constants to represent special characters, such as char c = '\n'. Note that the backslash needs to be escaped twice. Different platforms and compilers may have different escape sequences, please consult the documentation.
 The difference between multithreading and asynchronous c#
Apr 03, 2025 pm 02:57 PM
The difference between multithreading and asynchronous c#
Apr 03, 2025 pm 02:57 PM
The difference between multithreading and asynchronous is that multithreading executes multiple threads at the same time, while asynchronously performs operations without blocking the current thread. Multithreading is used for compute-intensive tasks, while asynchronously is used for user interaction. The advantage of multi-threading is to improve computing performance, while the advantage of asynchronous is to not block UI threads. Choosing multithreading or asynchronous depends on the nature of the task: Computation-intensive tasks use multithreading, tasks that interact with external resources and need to keep UI responsiveness use asynchronous.
 The difference between char and wchar_t in C language
Apr 03, 2025 pm 03:09 PM
The difference between char and wchar_t in C language
Apr 03, 2025 pm 03:09 PM
In C language, the main difference between char and wchar_t is character encoding: char uses ASCII or extends ASCII, wchar_t uses Unicode; char takes up 1-2 bytes, wchar_t takes up 2-4 bytes; char is suitable for English text, wchar_t is suitable for multilingual text; char is widely supported, wchar_t depends on whether the compiler and operating system support Unicode; char is limited in character range, wchar_t has a larger character range, and special functions are used for arithmetic operations.
 How to convert char in C language
Apr 03, 2025 pm 03:21 PM
How to convert char in C language
Apr 03, 2025 pm 03:21 PM
In C language, char type conversion can be directly converted to another type by: casting: using casting characters. Automatic type conversion: When one type of data can accommodate another type of value, the compiler automatically converts it.
 How to use char array in C language
Apr 03, 2025 pm 03:24 PM
How to use char array in C language
Apr 03, 2025 pm 03:24 PM
The char array stores character sequences in C language and is declared as char array_name[size]. The access element is passed through the subscript operator, and the element ends with the null terminator '\0', which represents the end point of the string. The C language provides a variety of string manipulation functions, such as strlen(), strcpy(), strcat() and strcmp().
 What is the difference between char and unsigned char
Apr 03, 2025 pm 03:36 PM
What is the difference between char and unsigned char
Apr 03, 2025 pm 03:36 PM
char and unsigned char are two data types that store character data. The main difference is the way to deal with negative and positive numbers: value range: char signed (-128 to 127), and unsigned char unsigned (0 to 255). Negative number processing: char can store negative numbers, unsigned char cannot. Bit mode: char The highest bit represents the symbol, unsigned char Unsigned bit. Arithmetic operations: char and unsigned char are signed and unsigned types, and their arithmetic operations are different. Compatibility: char and unsigned char





