 Database
Database
 Mysql Tutorial
Mysql Tutorial
 How do I secure MySQL against common vulnerabilities (SQL injection, brute-force attacks)?
How do I secure MySQL against common vulnerabilities (SQL injection, brute-force attacks)?
How do I secure MySQL against common vulnerabilities (SQL injection, brute-force attacks)?
How do I secure MySQL against common vulnerabilities (SQL injection, brute-force attacks)?
Securing MySQL against common vulnerabilities like SQL injection and brute-force attacks requires a multi-faceted approach. Here are detailed steps to enhance your MySQL security:
-
SQL Injection Prevention:
- Use Prepared Statements: Prepared statements with parameterized queries are the most effective way to prevent SQL injection. This separates the SQL logic from the data, ensuring that user input is treated as data, not executable code.
- Input Validation: Always validate and sanitize user inputs on the application layer before passing them to SQL queries. Use whitelist validation to ensure only expected data formats are accepted.
- Least Privilege Principle: Ensure that database users have the minimum required permissions. For instance, a web application should not have full administrative privileges on the database.
- Stored Procedures: Use stored procedures as an additional layer of abstraction between the application and the database. They can help encapsulate SQL logic and reduce the risk of injection.
-
Brute-Force Attack Prevention:
- Strong Password Policies: Implement robust password policies that require strong, complex passwords. This includes using a mix of letters, numbers, and special characters, and enforcing minimum password length.
-
Account Lockout Mechanisms: Configure MySQL to lock accounts after a certain number of failed login attempts. This can be done using the
max_connect_errorsvariable in MySQL. - Rate Limiting: Implement rate limiting at the application or firewall level to slow down repeated login attempts from the same IP address.
- Use of SSL/TLS: Enable SSL/TLS for MySQL connections to encrypt data in transit, making it more difficult for attackers to intercept and use credentials.
By combining these strategies, you can significantly reduce the risk of SQL injection and brute-force attacks on your MySQL server.
What are the best practices for preventing SQL injection in MySQL databases?
Preventing SQL injection in MySQL databases requires adherence to several best practices:
-
Use Prepared Statements:
Prepared statements with parameterized queries are the gold standard for preventing SQL injection. They separate the SQL logic from the data, ensuring that user input cannot alter the structure of the SQL command. For example, in MySQL with PHP, you can use PDO or MySQLi with prepared statements:$stmt = $pdo->prepare('SELECT * FROM users WHERE username = :username'); $stmt->execute(['username' => $username]);Copy after login Input Validation and Sanitization:
Always validate user inputs to ensure they meet expected formats before they reach the database. Use whitelist validation to check for allowed patterns. Additionally, sanitize inputs to remove any potentially harmful characters:$username = filter_var($username, FILTER_SANTIZE_STRING);
Copy after login- Stored Procedures:
Using stored procedures can add an extra layer of security by encapsulating SQL logic on the server. This reduces the surface area for injection as the application interacts with the stored procedure rather than raw SQL. - ORM and Query Builders:
If you're using an Object-Relational Mapping (ORM) system or query builders, ensure they use parameterized queries internally. Many modern frameworks, such as Laravel with Eloquent or Django with ORM, provide built-in protection against SQL injection. - Regular Security Audits:
Perform regular security audits and penetration testing to identify and fix any vulnerabilities in your SQL queries and application logic.
By following these best practices, you can significantly mitigate the risk of SQL injection in your MySQL databases.
How can I implement robust password policies to protect MySQL from brute-force attacks?
Implementing robust password policies is crucial for protecting MySQL from brute-force attacks. Here’s how you can do it:
Complexity Requirements:
Enforce password complexity by requiring a mix of uppercase and lowercase letters, numbers, and special characters. A strong password policy might look like this:- At least 12 characters long
- At least one uppercase letter
- At least one lowercase letter
- At least one number
- At least one special character
- Password Length:
Longer passwords are inherently more secure. Enforce a minimum password length of at least 12 characters, but consider 16 or more for enhanced security. - Password Expiration:
Implement a password expiration policy to force users to change their passwords periodically. For example, you might require password changes every 90 days. - Password History:
Prevent users from reusing recent passwords. MySQL can be configured to remember the last few passwords, ensuring that users do not reuse them within a specified period. Account Lockout:
Implement an account lockout mechanism to temporarily or permanently lock accounts after a certain number of failed login attempts. In MySQL, you can use themax_connect_errorsvariable to achieve this:SET GLOBAL max_connect_errors = 3;
Copy after login-
Multi-Factor Authentication (MFA):
Where possible, implement MFA to add an extra layer of security. MySQL supports plugins likemysql_native_passwordandcaching_sha2_password, which can be extended to support MFA. -
Password Strength Testing:
Use password strength testing tools to ensure that users' chosen passwords meet the defined criteria. Tools like zxcvbn can be integrated into the application to provide real-time feedback on password strength.
By implementing these robust password policies, you can significantly reduce the effectiveness of brute-force attacks on your MySQL server.
What tools or services can I use to monitor and mitigate ongoing SQL injection attempts on my MySQL server?
Several tools and services can help you monitor and mitigate ongoing SQL injection attempts on your MySQL server:
-
Web Application Firewalls (WAFs):
WAFs like Cloudflare, AWS WAF, and ModSecurity can detect and block SQL injection attempts at the network level. They use predefined rules to identify and filter out malicious traffic. -
Intrusion Detection Systems (IDS):
Tools like Snort and Suricata can monitor network traffic for SQL injection patterns and alert you to potential threats. They can be configured to work specifically with MySQL traffic. -
Database Activity Monitoring (DAM) Tools:
DAM tools such as Imperva SecureSphere and IBM Guardium can monitor database queries in real-time and identify suspicious activity. They can be integrated with MySQL to provide detailed logs and alerts. -
Security Information and Event Management (SIEM) Systems:
SIEM systems like Splunk and LogRhythm can aggregate and analyze log data from your MySQL server to detect SQL injection attempts. They provide a centralized view of security events across your infrastructure. -
MySQL Audit Plugin:
The MySQL Audit Plugin can log all database activities, including queries, which can be useful for forensic analysis and real-time monitoring of SQL injection attempts. -
Open Source Tools:
- SQLMap: An open-source penetration testing tool that can help you identify SQL injection vulnerabilities and simulate attacks to test your defenses.
- OWASP ZAP: An open-source web application security scanner that can detect SQL injection vulnerabilities in your applications.
-
Third-Party Services:
Services like Acunetix and Netsparker offer automated scanning for SQL injection vulnerabilities and can provide ongoing monitoring and mitigation suggestions.
By using these tools and services, you can effectively monitor and mitigate SQL injection attempts on your MySQL server, ensuring the security and integrity of your data.
The above is the detailed content of How do I secure MySQL against common vulnerabilities (SQL injection, brute-force attacks)?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 When might a full table scan be faster than using an index in MySQL?
Apr 09, 2025 am 12:05 AM
When might a full table scan be faster than using an index in MySQL?
Apr 09, 2025 am 12:05 AM
Full table scanning may be faster in MySQL than using indexes. Specific cases include: 1) the data volume is small; 2) when the query returns a large amount of data; 3) when the index column is not highly selective; 4) when the complex query. By analyzing query plans, optimizing indexes, avoiding over-index and regularly maintaining tables, you can make the best choices in practical applications.
 Can I install mysql on Windows 7
Apr 08, 2025 pm 03:21 PM
Can I install mysql on Windows 7
Apr 08, 2025 pm 03:21 PM
Yes, MySQL can be installed on Windows 7, and although Microsoft has stopped supporting Windows 7, MySQL is still compatible with it. However, the following points should be noted during the installation process: Download the MySQL installer for Windows. Select the appropriate version of MySQL (community or enterprise). Select the appropriate installation directory and character set during the installation process. Set the root user password and keep it properly. Connect to the database for testing. Note the compatibility and security issues on Windows 7, and it is recommended to upgrade to a supported operating system.
 Explain InnoDB Full-Text Search capabilities.
Apr 02, 2025 pm 06:09 PM
Explain InnoDB Full-Text Search capabilities.
Apr 02, 2025 pm 06:09 PM
InnoDB's full-text search capabilities are very powerful, which can significantly improve database query efficiency and ability to process large amounts of text data. 1) InnoDB implements full-text search through inverted indexing, supporting basic and advanced search queries. 2) Use MATCH and AGAINST keywords to search, support Boolean mode and phrase search. 3) Optimization methods include using word segmentation technology, periodic rebuilding of indexes and adjusting cache size to improve performance and accuracy.
 MySQL: Simple Concepts for Easy Learning
Apr 10, 2025 am 09:29 AM
MySQL: Simple Concepts for Easy Learning
Apr 10, 2025 am 09:29 AM
MySQL is an open source relational database management system. 1) Create database and tables: Use the CREATEDATABASE and CREATETABLE commands. 2) Basic operations: INSERT, UPDATE, DELETE and SELECT. 3) Advanced operations: JOIN, subquery and transaction processing. 4) Debugging skills: Check syntax, data type and permissions. 5) Optimization suggestions: Use indexes, avoid SELECT* and use transactions.
 Difference between clustered index and non-clustered index (secondary index) in InnoDB.
Apr 02, 2025 pm 06:25 PM
Difference between clustered index and non-clustered index (secondary index) in InnoDB.
Apr 02, 2025 pm 06:25 PM
The difference between clustered index and non-clustered index is: 1. Clustered index stores data rows in the index structure, which is suitable for querying by primary key and range. 2. The non-clustered index stores index key values and pointers to data rows, and is suitable for non-primary key column queries.
 Can mysql and mariadb coexist
Apr 08, 2025 pm 02:27 PM
Can mysql and mariadb coexist
Apr 08, 2025 pm 02:27 PM
MySQL and MariaDB can coexist, but need to be configured with caution. The key is to allocate different port numbers and data directories to each database, and adjust parameters such as memory allocation and cache size. Connection pooling, application configuration, and version differences also need to be considered and need to be carefully tested and planned to avoid pitfalls. Running two databases simultaneously can cause performance problems in situations where resources are limited.
 The relationship between mysql user and database
Apr 08, 2025 pm 07:15 PM
The relationship between mysql user and database
Apr 08, 2025 pm 07:15 PM
In MySQL database, the relationship between the user and the database is defined by permissions and tables. The user has a username and password to access the database. Permissions are granted through the GRANT command, while the table is created by the CREATE TABLE command. To establish a relationship between a user and a database, you need to create a database, create a user, and then grant permissions.
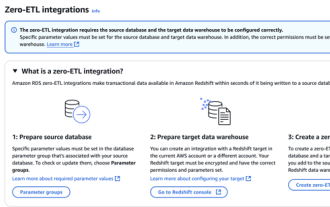 RDS MySQL integration with Redshift zero ETL
Apr 08, 2025 pm 07:06 PM
RDS MySQL integration with Redshift zero ETL
Apr 08, 2025 pm 07:06 PM
Data Integration Simplification: AmazonRDSMySQL and Redshift's zero ETL integration Efficient data integration is at the heart of a data-driven organization. Traditional ETL (extract, convert, load) processes are complex and time-consuming, especially when integrating databases (such as AmazonRDSMySQL) with data warehouses (such as Redshift). However, AWS provides zero ETL integration solutions that have completely changed this situation, providing a simplified, near-real-time solution for data migration from RDSMySQL to Redshift. This article will dive into RDSMySQL zero ETL integration with Redshift, explaining how it works and the advantages it brings to data engineers and developers.





