SQL2005解密已经被加密的存储过程
SQL2005解密已经被加密的存储过程 第一步:打开DAC连接功能 第二步:在MASTER数据库创建一个解密存储过程 1 USE master . ( , ) 王成辉翻译整理,转贴请注明出自微软BI开拓者 10 调用形式为: 11 exec dbo.sp__windbi$decrypt @procedure,0 12 如果第二个参
SQL2005解密已经被加密的存储过程
第一步:打开DAC连接功能


第二步:在MASTER数据库创建一个解密存储过程
1 USE master .( , ) 王成辉翻译整理,转贴请注明出自微软BI开拓者 10 调用形式为: 11 exec dbo.sp__windbi$decrypt @procedure,0 12 如果第二个参数使用1的话,,会给出该存储过程的一些提示。 13 --版本4.0 修正存储过程过长解密出来是空白的问题 NOCOUNT , , , (subobjid) 29 FROM sys.sysobjvalues (@procedure) ((MAX) (MAX) (MAX) (MAX) , (MAX) (2) , (MAX) type, (parent_object_id) 43 FROM sys.objects (@procedure) ( imageval 48 FROM sys.sysobjvalues ( subobjid 51 ) #output 54 ( (1, 1) , (MAX) 58 ) WITH ENCRYPTION AS select 1 ((MAX)), ) () RETURNS INT WITH ENCRYPTION AS BEGIN RETURN 1 ((MAX)), ) WITH ENCRYPTION AS select 1 as col ((MAX)), ) ,16,10) ((MAX)), ) (@fake_01) ( imageval 88 FROM sys.sysobjvalues ( subobjid 91 ) WITH ENCRYPTION AS select 1 ((MAX)), ) () RETURNS INT WITH ENCRYPTION AS BEGIN RETURN 1 ((MAX)), ) WITH ENCRYPTION AS select 1 as col ((MAX)), ) ,16,10) ((MAX)), ) ((MAX)), 115 ( DATALENGTH(@real_01) / 2 )) ( DATALENGTH(@real_01) / 2 ) (@real_decrypt_01, @intProcSpace, 1, 124 NCHAR(UNICODE(SUBSTRING(@real_01, 125 @intProcSpace, 1)) ^ ( UNICODE(SUBSTRING(@fake_01, (SUBSTRING(@fake_encrypt_01, 127 @intProcSpace, 1)) ))) #output ( real_decrypt ) SYSNAME , , , , , , , , , (MAX) , (255) #CommentText 152 ( 153 LineId INT , (255) COLLATE database_default 155 ) ms_crs_syscom CURSOR LOCAL real_decrypt 160 FROM #output ident ms_crs_syscom ms_crs_syscom (@SyscomText) (CHAR(13) + CHAR(10), 177 @SyscomText, @BasePos) ( ) ( ISNULL(LEN(@Line), ) 186 INSERT #CommentText 187 VALUES ( @LineId, (SUBSTRING(@SyscomText, 189 @BasePos, 190 @AddOnLen), N'') ) , , , (@Line, N'') + ISNULL(SUBSTRING(@SyscomText, 196 @BasePos, ), 198 N'') #CommentText 201 VALUES ( @LineId, @Line ) ( ) ( ISNULL(LEN(@Line), ) 215 INSERT #CommentText 216 VALUES ( @LineId, (SUBSTRING(@SyscomText, 218 @BasePos, 219 @AddOnLen), N'') ) , , , (@Line, N'') + ISNULL(SUBSTRING(@SyscomText, 226 @BasePos, ), 228 N'') ((' ', 230 @SyscomText, ) , ms_crs_syscom #CommentText 245 VALUES ( @LineId, @Line ) #CommentText LineId 249 CLOSE ms_crs_syscom 250 DEALLOCATE ms_crs_syscom #CommentText #output 258 GO

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1419
1419
 52
52
 1311
1311
 25
25
 1261
1261
 29
29
 1234
1234
 24
24
 Huawei will launch innovative MED storage products next year: rack capacity exceeds 10 PB and power consumption is less than 2 kW
Mar 07, 2024 pm 10:43 PM
Huawei will launch innovative MED storage products next year: rack capacity exceeds 10 PB and power consumption is less than 2 kW
Mar 07, 2024 pm 10:43 PM
This website reported on March 7 that Dr. Zhou Yuefeng, President of Huawei's Data Storage Product Line, recently attended the MWC2024 conference and specifically demonstrated the new generation OceanStorArctic magnetoelectric storage solution designed for warm data (WarmData) and cold data (ColdData). Zhou Yuefeng, President of Huawei's data storage product line, released a series of innovative solutions. Image source: Huawei's official press release attached to this site is as follows: The cost of this solution is 20% lower than that of magnetic tape, and its power consumption is 90% lower than that of hard disks. According to foreign technology media blocksandfiles, a Huawei spokesperson also revealed information about the magnetoelectric storage solution: Huawei's magnetoelectronic disk (MED) is a major innovation in magnetic storage media. First generation ME
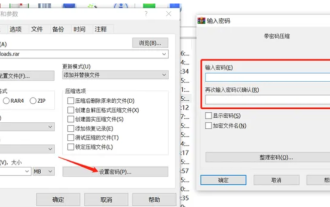 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 Git installation process on Ubuntu
Mar 20, 2024 pm 04:51 PM
Git installation process on Ubuntu
Mar 20, 2024 pm 04:51 PM
Git is a fast, reliable, and adaptable distributed version control system. It is designed to support distributed, non-linear workflows, making it ideal for software development teams of all sizes. Each Git working directory is an independent repository with a complete history of all changes and the ability to track versions even without network access or a central server. GitHub is a Git repository hosted on the cloud that provides all the features of distributed revision control. GitHub is a Git repository hosted on the cloud. Unlike Git which is a CLI tool, GitHub has a web-based graphical user interface. It is used for version control, which involves collaborating with other developers and tracking changes to scripts and
 How to set up word decryption
Mar 20, 2024 pm 04:36 PM
How to set up word decryption
Mar 20, 2024 pm 04:36 PM
In today's work environment, everyone's awareness of confidentiality is getting stronger and stronger, and encryption operations are often performed to protect files when using software. Especially for key documents, the awareness of confidentiality should be increased, and the security of documents should be given top priority at all times. So I don’t know how well everyone understands word decryption. How to operate it specifically? Today we will actually show you the process of word decryption through the explanation below. Friends who need to learn word decryption knowledge should not miss today's course. A decryption operation is first required to protect the file, which means that the file is processed as a protective document. After doing this to a file, a prompt pops up when you open the file again. The way to decrypt the file is to enter the password, so you can directly
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Original author: Meteor, ChainCatcher Original editor: Marco, ChainCatcher Recently, the full-chain interoperability protocol Analog has entered the public eye with the disclosure of US$16 million in financing. Investment institutions include TribeCapital, NGCVentures, Wintermute, GSR, NEAR, OrangeDAO, and Mike Novogratz’s Alternative asset management companies Samara Asset Group, Balaji Srinivasan, etc. At the end of 2023, Analog caused some excitement in the industry. They released information on the open testnet registration event on the X platform.
 Full analysis of Java collection framework: dissecting data structure and revealing the secret of efficient storage
Feb 23, 2024 am 10:49 AM
Full analysis of Java collection framework: dissecting data structure and revealing the secret of efficient storage
Feb 23, 2024 am 10:49 AM
Overview of Java Collection Framework The Java collection framework is an important part of the Java programming language. It provides a series of container class libraries that can store and manage data. These container class libraries have different data structures to meet the data storage and processing needs in different scenarios. The advantage of the collection framework is that it provides a unified interface, allowing developers to operate different container class libraries in the same way, thereby reducing the difficulty of development. Data structures of the Java collection framework The Java collection framework contains a variety of data structures, each of which has its own unique characteristics and applicable scenarios. The following are several common Java collection framework data structures: 1. List: List is an ordered collection that allows elements to be repeated. Li
 How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to de-encrypt videos on EZVIZ Cloud: There are many ways to de-encrypt videos on EZVIZ Cloud, one of which is by using the EZVIZ Cloud Mobile App. Users only need to enter the device list, select the camera to be decrypted and enter the device details page. On the device details page, find the "Settings" option, and then select "Video Encryption" to make relevant settings. In the video encryption settings interface, you can choose the option to turn off video encryption, and save the settings to complete the decryption operation. This simple step allows users to easily decrypt videos and improves the convenience of using the camera. If you use the computer client of EZVIZ Cloud, you can also cancel video encryption through similar steps. Just log in and select the corresponding camera, enter the device details interface, and then look for video addition in the settings.




