Oracle自带安全特性与DBCoffer比较
安全产品 优点 缺点 Oracle Database Vault 1、可以防住DBA等特权用户 2、 Oracle内部实现,应用无需改动,安装灵活 3、
安全产品
优点
缺点
Oracle Database Vault
1、可以防住DBA等特权用户
2、 Oracle内部实现,应用无需改动,安装灵活
3、很好的控制何人、何时、何地可以访问应用程序,
1、有Oracle版本要求
2、新增权限系统复杂
3、DBA将失数据库相关对像的维护管理能力
4、还没有发行官方稳定版本
5、性能方面需要考虑
透明数据加密(TDE)
1、 能实现数据在存储加密
2、 且上层应用完全透明访问
1、功能单一,需要与其他安全策略配合使用
Oracle Label Security
1、 实现数据的行级访问控制
2、 且提供图型化的配置工具
1、不能防住DBA对数据的访问
2、且安装时需停启数据数据库实例
3、设置的数据逻辑要求高,实现不灵活
虚拟专用数据库(VPD)
1、 实现数据的行级访问控制,实现逻辑对数据有依赖(即必须有数据过滤条件)
2、 实现不灵活,一般和其他安全策略结合使用
3、 不便于大规模部署
1、不能防住DBA对敏感数据的访问
安全的应用程序角色
将数据库访问控制策略绑定到角色,,需要VPD支持
1、不能防住DBA对敏感数据的访问
细粒度审计
1、 实现关于特定条件的审计,如特定时间、IP、列、值
2、 此审计在Oracle内部实现,无需改动应用
1、不能防住DBA对敏感数据的访问
DBCoffer安全加固
1、 能实现数据的存储加密
2、 提供敏感数据的访问审计
3、 能有效防止DBA等特权用户对敏感数据的访问
4、 能提供特定IP、时间对数据的访问控制
5、 提供敏感数据的读写控制
6、 提供界面的逻辑控制,使用方便
7、 对于Oracle常规应用开发接口透明
1、 暂不支持行级的访问控制
2、 需要大量测试来验证Oracle的应用透明
3、 外部扩展多,总体逻辑复杂
4、 暂只提供字段级的数据保护,当大规应用时,对性能影响大
5、 由于需求的改变,软件改动大,软件的稳定性有待提高
以上纯属于个人实践后的总结,如有相关的指导或想法,希望不佞赐教,欢迎随时来信。
fnxjiabo@foxmail.com


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 When might a full table scan be faster than using an index in MySQL?
Apr 09, 2025 am 12:05 AM
When might a full table scan be faster than using an index in MySQL?
Apr 09, 2025 am 12:05 AM
Full table scanning may be faster in MySQL than using indexes. Specific cases include: 1) the data volume is small; 2) when the query returns a large amount of data; 3) when the index column is not highly selective; 4) when the complex query. By analyzing query plans, optimizing indexes, avoiding over-index and regularly maintaining tables, you can make the best choices in practical applications.
 Can I install mysql on Windows 7
Apr 08, 2025 pm 03:21 PM
Can I install mysql on Windows 7
Apr 08, 2025 pm 03:21 PM
Yes, MySQL can be installed on Windows 7, and although Microsoft has stopped supporting Windows 7, MySQL is still compatible with it. However, the following points should be noted during the installation process: Download the MySQL installer for Windows. Select the appropriate version of MySQL (community or enterprise). Select the appropriate installation directory and character set during the installation process. Set the root user password and keep it properly. Connect to the database for testing. Note the compatibility and security issues on Windows 7, and it is recommended to upgrade to a supported operating system.
 Explain InnoDB Full-Text Search capabilities.
Apr 02, 2025 pm 06:09 PM
Explain InnoDB Full-Text Search capabilities.
Apr 02, 2025 pm 06:09 PM
InnoDB's full-text search capabilities are very powerful, which can significantly improve database query efficiency and ability to process large amounts of text data. 1) InnoDB implements full-text search through inverted indexing, supporting basic and advanced search queries. 2) Use MATCH and AGAINST keywords to search, support Boolean mode and phrase search. 3) Optimization methods include using word segmentation technology, periodic rebuilding of indexes and adjusting cache size to improve performance and accuracy.
 Difference between clustered index and non-clustered index (secondary index) in InnoDB.
Apr 02, 2025 pm 06:25 PM
Difference between clustered index and non-clustered index (secondary index) in InnoDB.
Apr 02, 2025 pm 06:25 PM
The difference between clustered index and non-clustered index is: 1. Clustered index stores data rows in the index structure, which is suitable for querying by primary key and range. 2. The non-clustered index stores index key values and pointers to data rows, and is suitable for non-primary key column queries.
 MySQL: Simple Concepts for Easy Learning
Apr 10, 2025 am 09:29 AM
MySQL: Simple Concepts for Easy Learning
Apr 10, 2025 am 09:29 AM
MySQL is an open source relational database management system. 1) Create database and tables: Use the CREATEDATABASE and CREATETABLE commands. 2) Basic operations: INSERT, UPDATE, DELETE and SELECT. 3) Advanced operations: JOIN, subquery and transaction processing. 4) Debugging skills: Check syntax, data type and permissions. 5) Optimization suggestions: Use indexes, avoid SELECT* and use transactions.
 Can mysql and mariadb coexist
Apr 08, 2025 pm 02:27 PM
Can mysql and mariadb coexist
Apr 08, 2025 pm 02:27 PM
MySQL and MariaDB can coexist, but need to be configured with caution. The key is to allocate different port numbers and data directories to each database, and adjust parameters such as memory allocation and cache size. Connection pooling, application configuration, and version differences also need to be considered and need to be carefully tested and planned to avoid pitfalls. Running two databases simultaneously can cause performance problems in situations where resources are limited.
 The relationship between mysql user and database
Apr 08, 2025 pm 07:15 PM
The relationship between mysql user and database
Apr 08, 2025 pm 07:15 PM
In MySQL database, the relationship between the user and the database is defined by permissions and tables. The user has a username and password to access the database. Permissions are granted through the GRANT command, while the table is created by the CREATE TABLE command. To establish a relationship between a user and a database, you need to create a database, create a user, and then grant permissions.
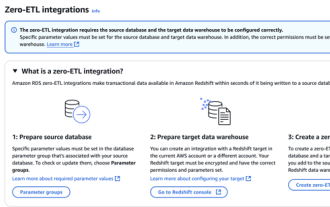 RDS MySQL integration with Redshift zero ETL
Apr 08, 2025 pm 07:06 PM
RDS MySQL integration with Redshift zero ETL
Apr 08, 2025 pm 07:06 PM
Data Integration Simplification: AmazonRDSMySQL and Redshift's zero ETL integration Efficient data integration is at the heart of a data-driven organization. Traditional ETL (extract, convert, load) processes are complex and time-consuming, especially when integrating databases (such as AmazonRDSMySQL) with data warehouses (such as Redshift). However, AWS provides zero ETL integration solutions that have completely changed this situation, providing a simplified, near-real-time solution for data migration from RDSMySQL to Redshift. This article will dive into RDSMySQL zero ETL integration with Redshift, explaining how it works and the advantages it brings to data engineers and developers.






