交换机中tag、untag的理解
交换机 中tag、untag的 理解 情况列举 Switch收发 Switch对标记的处理 remark Access (接收) Tagged = PVID 不接收 注:部分高端产品可能接收。 Access (接收) Tagged =/ PVID 不接收 注:部分高端产品可能接收。 Access (接收) Untagged 接收 增加tag=PVID
|
交换机中tag、untag的理解 |
|
情况列举 Switch收发 Switch对标记的处理 remark ================================ 先呈请一下上面的几个帖子的术语: |

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1425
1425
 52
52
 1327
1327
 25
25
 1273
1273
 29
29
 1252
1252
 24
24
 How to add swap space on Ubuntu 22.04 LTS
Feb 20, 2024 am 11:12 AM
How to add swap space on Ubuntu 22.04 LTS
Feb 20, 2024 am 11:12 AM
Swap space plays an important role in Linux systems, especially when the system is low on memory. It acts as a backup memory storage space that helps the system run smoothly and maintain stability even under high load. This article provides you with a detailed guide to adding swap space on Ubuntu 22.04LTS to ensure that your system performance is optimized and can handle various workloads. Understanding Swap Space Swap space provides virtual memory that is used to supplement the system's physical RAM. When the system is low on RAM, the kernel swaps data to disk to prevent out-of-memory and system crashes. Linux systems commonly use swap space to handle this situation. Run multiple memory-intensive applications simultaneously to process very large files or data
 Python program: Swap the positions of the first and last elements in a matrix between columns
Sep 08, 2023 pm 04:29 PM
Python program: Swap the positions of the first and last elements in a matrix between columns
Sep 08, 2023 pm 04:29 PM
A matrix is a two-dimensional array of numbers arranged in rows and columns. Python does not have any data type to represent matrices, but we can use nested lists or NumPy arrays as matrices. See the following input and output scenarios to see how to swap the first and last column elements of a matrix. Input-Output Scenario Suppose we have a 3X3 matrix represented using a list of lists. The output matrix will be the resulting matrix of swapping the first and last column elements. Inputmatrix:[1,3,4][4,5,6][7,8,3]Outputmatrix:[4,3,1][4,5,6][3,8,7]Let us consider another A matrix whose rows and columns are unequal. Inputmatrix:
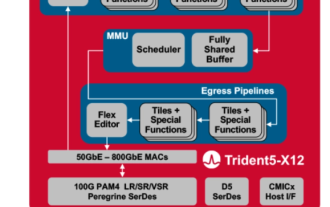 Broadcom Unveils Innovation, Launches Industry's First On-Chip Neural Network Switch
Dec 03, 2023 pm 08:51 PM
Broadcom Unveils Innovation, Launches Industry's First On-Chip Neural Network Switch
Dec 03, 2023 pm 08:51 PM
Broadcom recently announced the launch of the Trident5-X12 chip, which is equipped with a new NetGNT (Network General Neural Network Traffic Analyzer) on-chip neural network inference engine. NetGNT is different from traditional packet processing. It can work in parallel to enhance standard packet processing. pipeline. Traditional pipelines can only process one packet/path at a time, while NetGNT, as a machine learning inference engine, can be trained to identify various traffic patterns across the entire chip. It is understood that the Trident5-X12 chip has powerful software programming functions and on-site upgrade functions, providing a bandwidth of up to 16.0 Terabits/second, which is twice that of Trident4-X9. In addition, the new chip also supports
 Is Huawei tag useful?
Nov 07, 2023 pm 03:24 PM
Is Huawei tag useful?
Nov 07, 2023 pm 03:24 PM
Huawei Tag is useful in helping users track and locate items. Huawei Tag is an intelligent positioning device launched by Huawei. It can help users track and locate the location of items. It can help users retrieve lost items, prevent items from being stolen, provide remote alarm functions, and add items through the community help function. Chances of recovery. However, it should be noted that Tag’s positioning range is limited and relies on mobile phone connection. Users also need to pay attention to the protection of personal privacy.
 Learn more about the dis command in switch inspection
Feb 18, 2024 am 10:05 AM
Learn more about the dis command in switch inspection
Feb 18, 2024 am 10:05 AM
What is the dis command used in switch inspection? In the maintenance and management process of network equipment, switches are an indispensable part. Inspection of switches is one of the important links to ensure the normal operation of the network. During the inspection process, the dis command is a commonly used command on switches. The purpose and function of the dis command will be introduced in detail below. dis is the abbreviation of display. It is a commonly used command on Huawei switch equipment and is used to display various information of the equipment. The dis command can display the configuration information and operating status of the switch.
 How does a switch work?
Dec 26, 2023 pm 02:07 PM
How does a switch work?
Dec 26, 2023 pm 02:07 PM
The working principle of the switch is based on the second layer of the OSI reference model, the data link layer. A switch is a network device based on a learning process that enables communication between different devices in the network by parsing and forwarding data frames. The switch can continuously improve the contents of its internal forwarding table, improve the efficiency and reliability of data exchange, and ensure the stability and security of the connection. Switches are widely used in enterprise networks, data centers, campus networks and other scenarios to provide stable and efficient connection services for various applications.
 How does a switch work?
Dec 26, 2023 am 11:56 AM
How does a switch work?
Dec 26, 2023 am 11:56 AM
The working principle of the switch includes: 1. Data frame reception and analysis; 2. Forwarding table update; 3. Data frame forwarding; 4. Flood processing; 5. Connection maintenance. Detailed introduction: 1. Data frame reception and parsing. When the switch receives a data frame, it will first parse the data frame and extract the source MAC address and destination MAC address and other information; 2. Update of the forwarding table, The switch maintains a forwarding table internally, which records the correspondence between MAC addresses and interfaces; 3. Forwarding of data frames, etc.
 Interpret HTTP status code 404 and develop corresponding solutions
Feb 18, 2024 pm 04:44 PM
Interpret HTTP status code 404 and develop corresponding solutions
Feb 18, 2024 pm 04:44 PM
Understand the meaning of HTTP status code 404 and countermeasures HTTP is a protocol used to transmit hypertext. It uses status codes to indicate the server's response status to requests. Among them, status code 404 is the most common one, which means "Not Found". When we access a web page or request a resource in the browser, if the server cannot find the requested resource, it will return a 404 status code. The meaning of the 404 status code is to tell the client that the requested resource cannot be found. this




