Analysis of Laravel5 quick authentication logic flow
This article mainly introduces the analysis of Laravel5's fast authentication logic process. It has certain reference value. Now I share it with you. Friends in need can refer to it.
Laravel5 itself comes with a set of user authentication function, just use the command line php artisan make:auth and php artisan migrate under the new project to use the built-in fast authentication function.
The following is a logical analysis of the login function, which is based on Laravel 5.5 version.
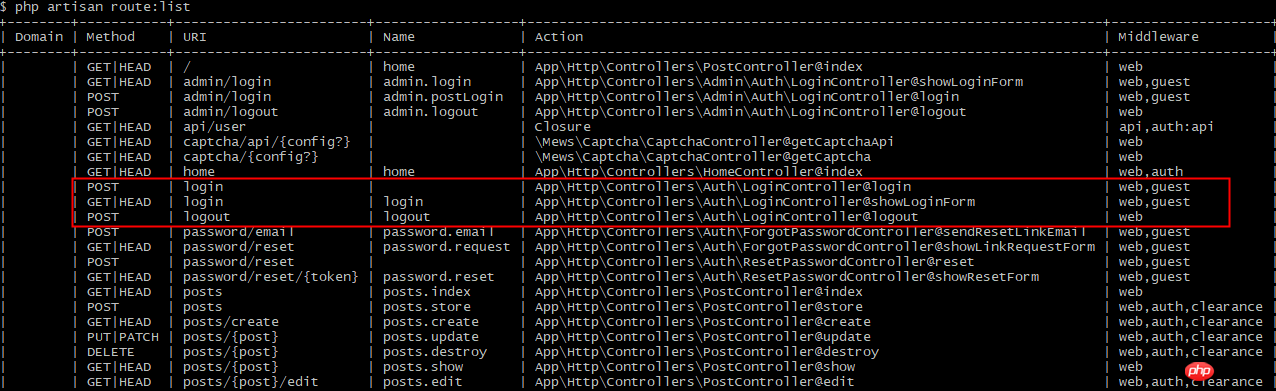
Get the login route (red box) through the command php artisan route:list:
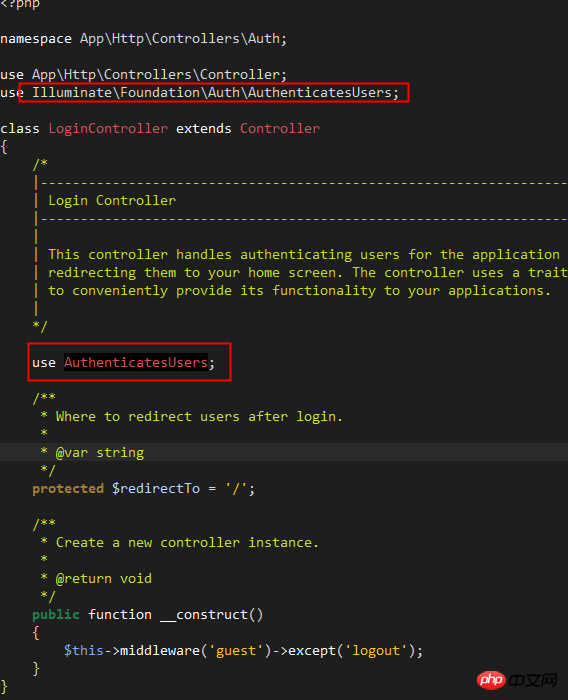
Open and view /app/Http/Controller/Auth/LoginController.php , the file code is very concise. In fact, the login logic and methods are integrated in the trait of Illuminate/Foundation/Auth/AuthenticatesUsers:
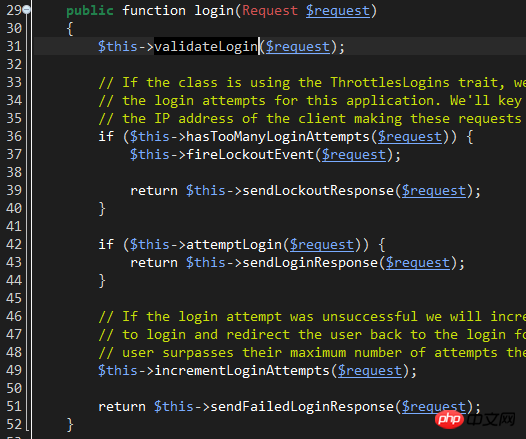
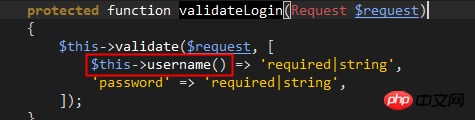
line31: The validateLogin method is responsible for calling The validate method of the controller itself verifies whether the username and password comply with simple rules. There is no need to go into this in depth.
line36: hasTooManyLoginAttempts method, used to check whether the number of account login attempts reaches the set maximum value.
This method refers to the trait of Illuminate\Foundation\Auth\ThrottlesLogins. Looking at the trait name, you can guess that it is responsible for avoiding violent logins.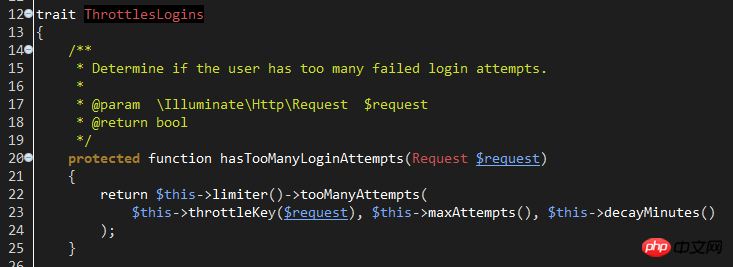
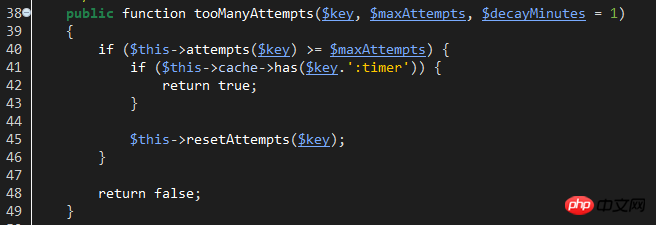
$key: The corresponding key used by cacche to save the login number of the current account. The key composition is like this:
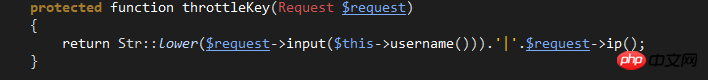
$maxAttempts: Setting value for the maximum number of login attempts.
This value can be customized. You can write the custom maxAttempts attribute in LoginController. The default is 5 times: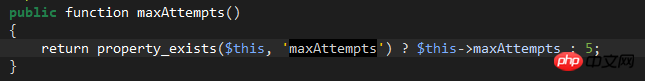
$decayMinutes:The waiting time (minutes) for resuming login after reaching the maximum number of attempts.
This value is also customizable. Customize this property in LoginController. The default is 1 minute: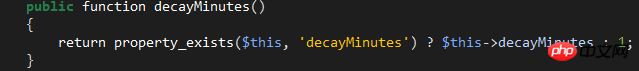
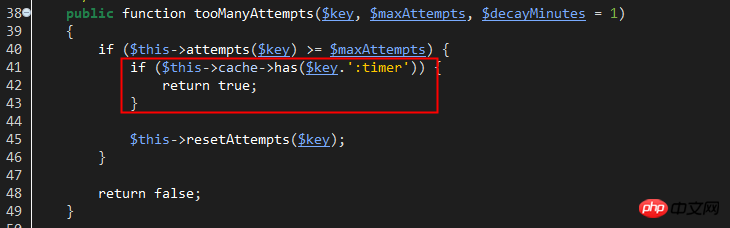
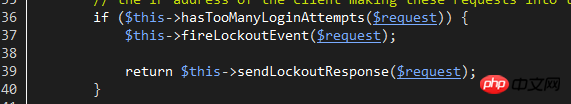
When hasTooManyLoginAttempts returns true, the Lockout event is initiated and the LockoutResponse response is returned. Users can generate a Lockout event monitor to process the logic related to the event, such as recording login logs, etc.
LockoutResponse response essentially throws a verification exception, which will be automatically interpreted by Laravel as a response with a 423 status code and accompanied by auth.throttle configuration information. The original language of this configuration is located at: /resources/lang/en/auth.php. Users can customize their own language information.
Then, return to line 42 of Illuminate\Foundation\Auth\AuthenticatesUsers and start to perform login verification:
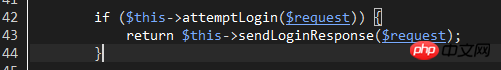
attemptLogin method passes config/auth.php Configure the guard name, generate the corresponding guard object, and then call the object's attempt for login verification.
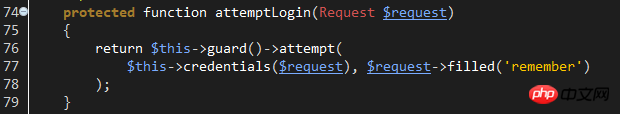
Laravel5 guard currently supports two types: SessionGuard and tokenGuard, both are saved in the Illuminate\Auth folder, and they are both implemented in the Illuminate\Contracts\Auth\Guard interface. So if you need to customize the watcher, please implement this interface.
If you want to implement a web guard, you can further implement the Illuminate\Contracts\Auth\StatefulGuard interface.
As for which guard to use under which circumstances, they are all configured in config/auth.php:
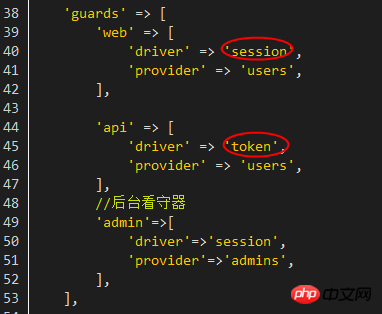
Since what I analyzed this time is Web login process, so check the attempt method of Illuminate\Auth\sessionGuard:
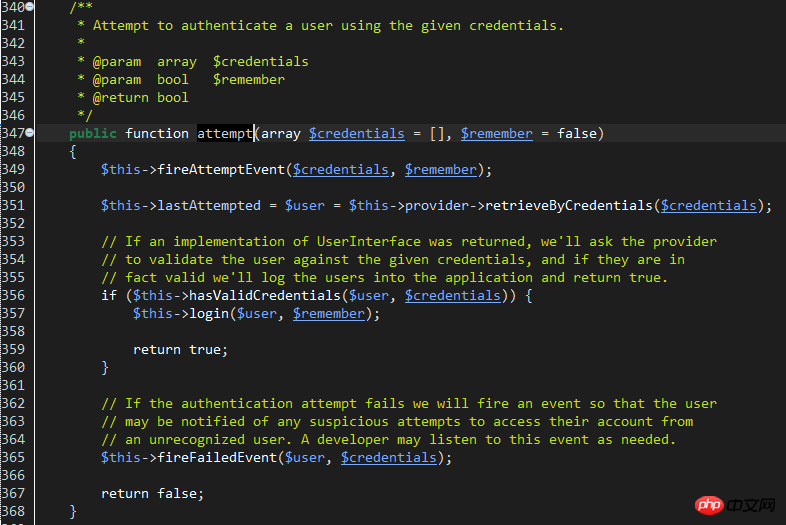
#line 351: The function of this line is to retrieve the account information through the configured provider provider. There are also two types of providers: DatabaseUserProvider and EloquentUserProvider. The file is located at: /Illuminate/Auth.
The specific provider to use is configured through the providers parameter of config/auth.php. After configuration, you also need to specify which provider to use in the 'guards' parameter. The provider essentially provides a way to query the database account table. Database directly uses the database Db facade to query, while eloquent uses a model to query.
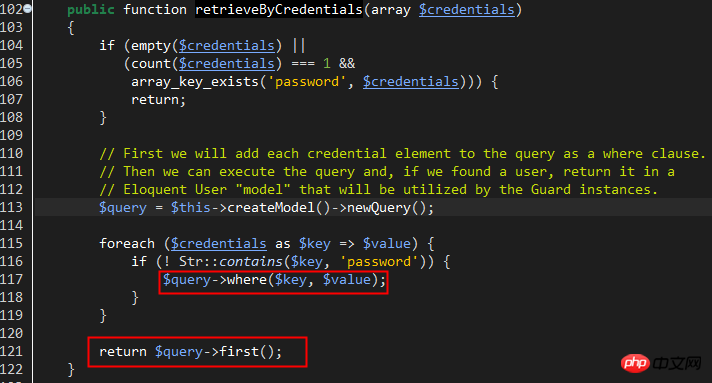
Laravel uses EloquentUserProvider by default. Looking at the retrieveByCredentials method, it is obvious that the user information is retrieved directly by the account name:
Back The attempt method of Illuminate\Auth\sessionGuard and the hasValidCredentials method of line 356 verify the password, if the user information in the previous step can be retrieved normally.
As can be seen from the hasValidCredentials method body, it calls the provider's validateCredentials method for password verification. Check out the EloquentUserProvider::validateCredentials method:
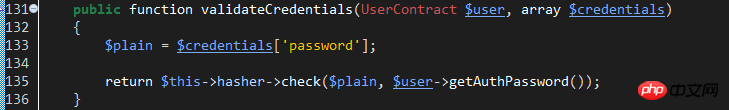
This verification method uses the check method of the hash class implemented by the HasherContract contract. The specific implementation classes are: Illuminate\Hashing\BcryptHasher. Let's look at the check method of this class:
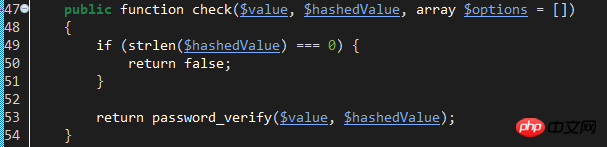
Obviously, it uses the password_verify function to compare the entered plaintext password with the hashed password value. This requires that the database passwords have been hashed using password_hash.
If the password verification is successful, return true. Return to sessionGuard and execute the login method of line357 to record the session and cookie login status.
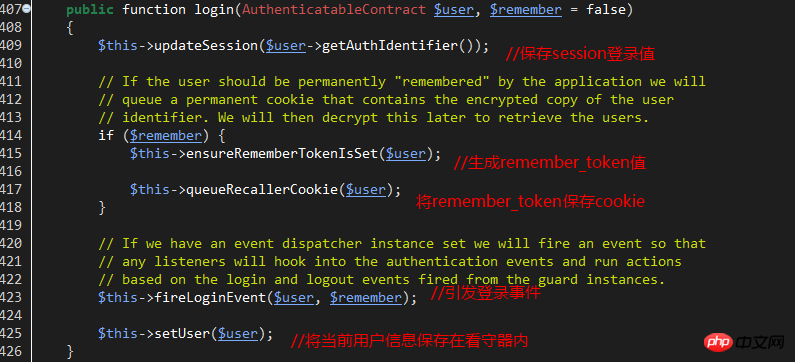
The key and value of the saved session are:
'key'=>'login_session_'.sha1(static::class) // static::class refers to the sessionGuard class itself
'value'=>The primary key value of the current user
If the remember_me option is used, the following cookie is saved, and the key and value are as follows:
'key'=>''remember_session_'.sha1(static::class) //static::class refers to the sessionGuard class itself
'value'=>User primary key value .'|'.The latest remembered_token value saved.'|'.User password hash value
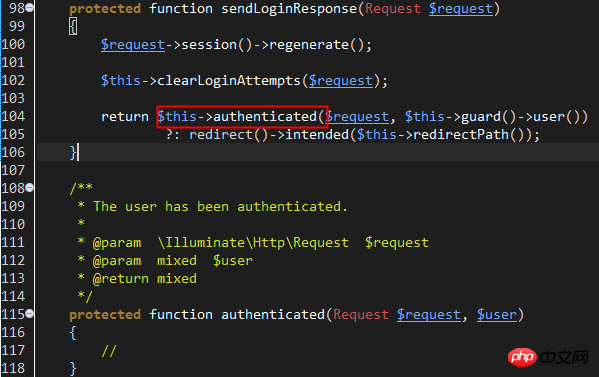
At this point, the user has successfully logged in, and the execution point finally returns to line 42 of Illuminate\Foundation\Auth\AuthenticatesUsers , attemptLogin has been executed and returned true, and then the sendLoginResponse method is called to jump to the main page after login or the last login page.
Note that the authenticated method is an empty method. You can redefine this method in LoginController to customize how to jump and process other logic after login.
If the login is unsuccessful, execute the incrementLoginAttempts($request) method of Illuminate\Foundation\Auth\AuthenticatesUsers to increase the number of failed logins. The method to increase the number of times is also to indirectly call the hit() method of the RateLimiter class.
Finally call sendFailedLoginResponse to return a login exception.
Finally, the timing diagram is attached. The drawing is average. Some UML concepts are not well grasped. Sorry:
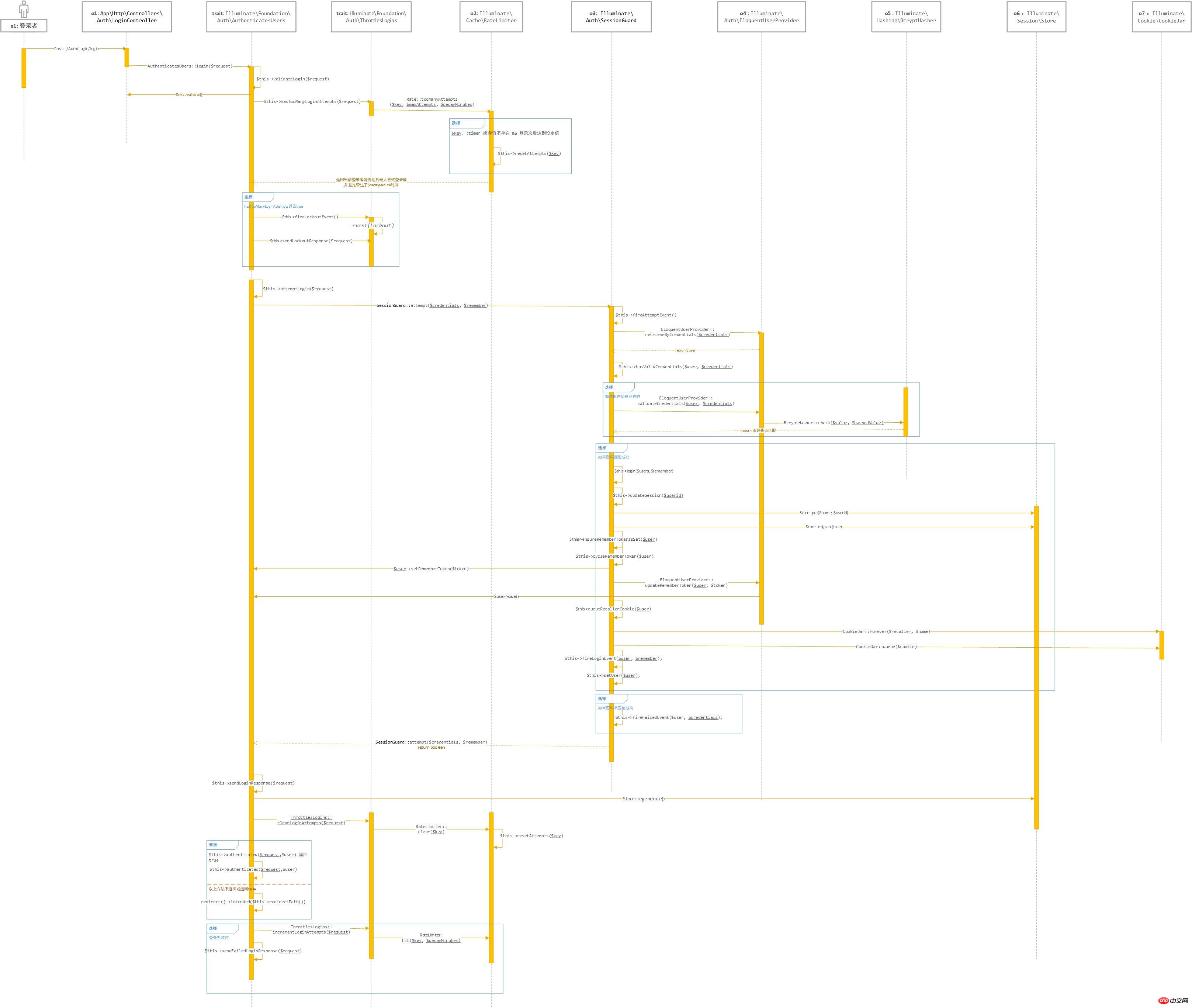
That’s all. The entire content of this article is hoped to be helpful to everyone's study. For more related content, please pay attention to the PHP Chinese website!
Related recommendations:
Introduction to Laravel’s Eloquent model
How to use Wamp to build a Php local development environment and HBuilder debugging
The above is the detailed content of Analysis of Laravel5 quick authentication logic flow. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP...
 Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
JWT is an open standard based on JSON, used to securely transmit information between parties, mainly for identity authentication and information exchange. 1. JWT consists of three parts: Header, Payload and Signature. 2. The working principle of JWT includes three steps: generating JWT, verifying JWT and parsing Payload. 3. When using JWT for authentication in PHP, JWT can be generated and verified, and user role and permission information can be included in advanced usage. 4. Common errors include signature verification failure, token expiration, and payload oversized. Debugging skills include using debugging tools and logging. 5. Performance optimization and best practices include using appropriate signature algorithms, setting validity periods reasonably,
 How does session hijacking work and how can you mitigate it in PHP?
Apr 06, 2025 am 12:02 AM
How does session hijacking work and how can you mitigate it in PHP?
Apr 06, 2025 am 12:02 AM
Session hijacking can be achieved through the following steps: 1. Obtain the session ID, 2. Use the session ID, 3. Keep the session active. The methods to prevent session hijacking in PHP include: 1. Use the session_regenerate_id() function to regenerate the session ID, 2. Store session data through the database, 3. Ensure that all session data is transmitted through HTTPS.
 Describe the SOLID principles and how they apply to PHP development.
Apr 03, 2025 am 12:04 AM
Describe the SOLID principles and how they apply to PHP development.
Apr 03, 2025 am 12:04 AM
The application of SOLID principle in PHP development includes: 1. Single responsibility principle (SRP): Each class is responsible for only one function. 2. Open and close principle (OCP): Changes are achieved through extension rather than modification. 3. Lisch's Substitution Principle (LSP): Subclasses can replace base classes without affecting program accuracy. 4. Interface isolation principle (ISP): Use fine-grained interfaces to avoid dependencies and unused methods. 5. Dependency inversion principle (DIP): High and low-level modules rely on abstraction and are implemented through dependency injection.
 How to debug CLI mode in PHPStorm?
Apr 01, 2025 pm 02:57 PM
How to debug CLI mode in PHPStorm?
Apr 01, 2025 pm 02:57 PM
How to debug CLI mode in PHPStorm? When developing with PHPStorm, sometimes we need to debug PHP in command line interface (CLI) mode...
 How to automatically set permissions of unixsocket after system restart?
Mar 31, 2025 pm 11:54 PM
How to automatically set permissions of unixsocket after system restart?
Mar 31, 2025 pm 11:54 PM
How to automatically set the permissions of unixsocket after the system restarts. Every time the system restarts, we need to execute the following command to modify the permissions of unixsocket: sudo...
 Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Static binding (static::) implements late static binding (LSB) in PHP, allowing calling classes to be referenced in static contexts rather than defining classes. 1) The parsing process is performed at runtime, 2) Look up the call class in the inheritance relationship, 3) It may bring performance overhead.
 How to send a POST request containing JSON data using PHP's cURL library?
Apr 01, 2025 pm 03:12 PM
How to send a POST request containing JSON data using PHP's cURL library?
Apr 01, 2025 pm 03:12 PM
Sending JSON data using PHP's cURL library In PHP development, it is often necessary to interact with external APIs. One of the common ways is to use cURL library to send POST�...






