 Web Front-end
Web Front-end
 JS Tutorial
JS Tutorial
 What is a DDos attack? How does the node SSR service prevent and handle attacks?
What is a DDos attack? How does the node SSR service prevent and handle attacks?
What is a DDos attack? How does the node SSR service prevent and handle attacks?
What is a DDos attack? node How does the SSR service prevent and deal with DDos attacks? The following article will take you to understand DDos attacks, and introduce how the node SSR service prevents and handles DDos attacks. I hope it will be helpful to everyone!

Preventing and dealing with DDos attacks is an important part of stability construction. If it is not prevented in advance, once it is attacked, the service will fall into an unavailable state. , may bring great losses to the business
This article will be biased towards the node ssr service perspective, front-end development students should pay more attention to this aspect. [Related tutorial recommendations: nodejs video tutorial]
What is a DDos attack?
To give a common example, our website can be compared to a bank. Under normal circumstances, the bank can handle the business of up to 100 people at the same time. Normally, you can just walk into the bank and get a number. Can be served
Suddenly a rogue organization wanted to collect protection fees, but the bank refused to give it, so the rogue sent 3,000 or even 30,000 people to get the number at the same time. After passing the number, continue to take the number. The result is that the server cannot handle it, and a large number of normal customers have been waiting. This is a DDOS attack. It initiates a large number of requests in a short period of time, exhausts the server's resources, and is unable to respond to normal access, causing the website to actually degrade. Wire.
DDOS is not an attack, but a general term for a large class of attacks. There are dozens of types, and new attack methods are constantly being invented. Every aspect of website operation can be a target of attack. As long as one link is broken and the entire process cannot run, the purpose of paralyzing the service will be achieved.
Among them, one of the more common attacks is the cc attack. CC attacks are targeted at web pages. CC attacks themselves are normal requests. Normal requests for dynamic pages on the website will also interact with the database. When this "normal request" reaches a certain level, the server will not be able to respond. , thereby collapsing.
baike.baidu.com/item/cc�%…The following content of this article is aimed at cc attacks.
How to prevent?First understand the path between a request coming to our services

After intercepting malicious traffic in the outer layer, the business cluster does not need frequent operation and maintenance (capacity expansion and contraction, limit flow, etc.), reducing operation and maintenance costs
- The business cluster does not need to prepare too many additional resources to attack traffic, saving costs
- It has good versatility and is easy to be transplanted to other services, bringing To stabilize the income
- Access to the CDN layer
- nginx current limit
- Connect to WAF firewall
- Other protection layers
- Improve the processing capabilities of the origin site.
- For the SSR service, there are 2 suggestions
- Let the SSR service only handle the return of the root HTML, and all other resources must be placed on the CDN
- When an attack occurs, temporarily downgrade SSR to CSR
The CDN layer will be the outermost layer, which is convenient for emergency situations. You can enable CDN caching or enable CDN paid projects to protect the security of other internal services. For example:
- For example, if instantaneous traffic of millions, tens of millions or more comes in, it is possible that the load balancing layer will be down, which will affect the entire company's business. , it’s not just the service that was attacked
- CDN’s protection capabilities include: CDN cache, Robot detection, IP reputation database, and building a custom protection rule set (combined with historical attacks Features and business forms), etc. (enabled by paid level)
- Another aside (personal opinion), CDN vendors have countless servers around the world, and large CDN vendors can almost against all attacks, and will also charge according to the protection level (protection fee). I personally think that some attacks are probably caused by CDN vendors colluding with illegal companies. It is equivalent to rogues charging protection fees. If they don’t pay the protection fees, they will smash the store (attack) to let you know the pain, and then buy CDN protection services. And it can activate more than tens of millions of QPS. Except for CDN manufacturers (which have many servers), it should be difficult for ordinary people
#
2. nginx current limit
3. Connect to WAF firewall
Let’s talk about these two together, which is also biased The operation and maintenance level is company-level infrastructure, and the specific access methods and specific configurations vary from company to company. I won’t go into detail here
What is nginx current limit?
- You can search by yourself
What is a WAF firewall?
- You can read this articlewww.huaweicloud.com/zhishi/waf0…
To summarize the WAF layer, it will pass the pre- Set up a rich reputation database to detect and intercept threats such as malicious scanners, IPs, and cyberhorses
Comprehensive attack protection: supports SQL injection, XSS cross-site scripting, Detect and intercept threats such as file inclusion, directory traversal, sensitive file access, command\code injection, web Trojan upload, third-party vulnerability attacks, etc.
Human-computer recognition
Interface speed limit, WAF can set a flexible speed limit policy based on IP or cookie
-
Based on a rich combination of fields and logical conditions, precise control
- Supports rich field conditions: based on common HTTP parameters and fields such as IP, URL, Referer, User-Agent, Params, etc. Condition combination.
- Supports a variety of conditional logic: supports logical conditions such as inclusion, not inclusion, equal, not equal, prefix equal, prefix not equal, etc., and sets blocking or releasing policies.
#4. Other protective layers
Different companies may have other protection layers corresponding to different businesses and their own characteristics. Protection layer, such as overload protection for single instances (determine whether the current service status is overloaded, and then dynamically discard some low-priority requests based on the priority of the traffic to ensure the normal operation of the service as much as possible)
There are many kinds of protective layers here. If you are interested, you can learn more about it
5. Improve the processing capabilities of the origin station
Forging iron requires one's own hard work 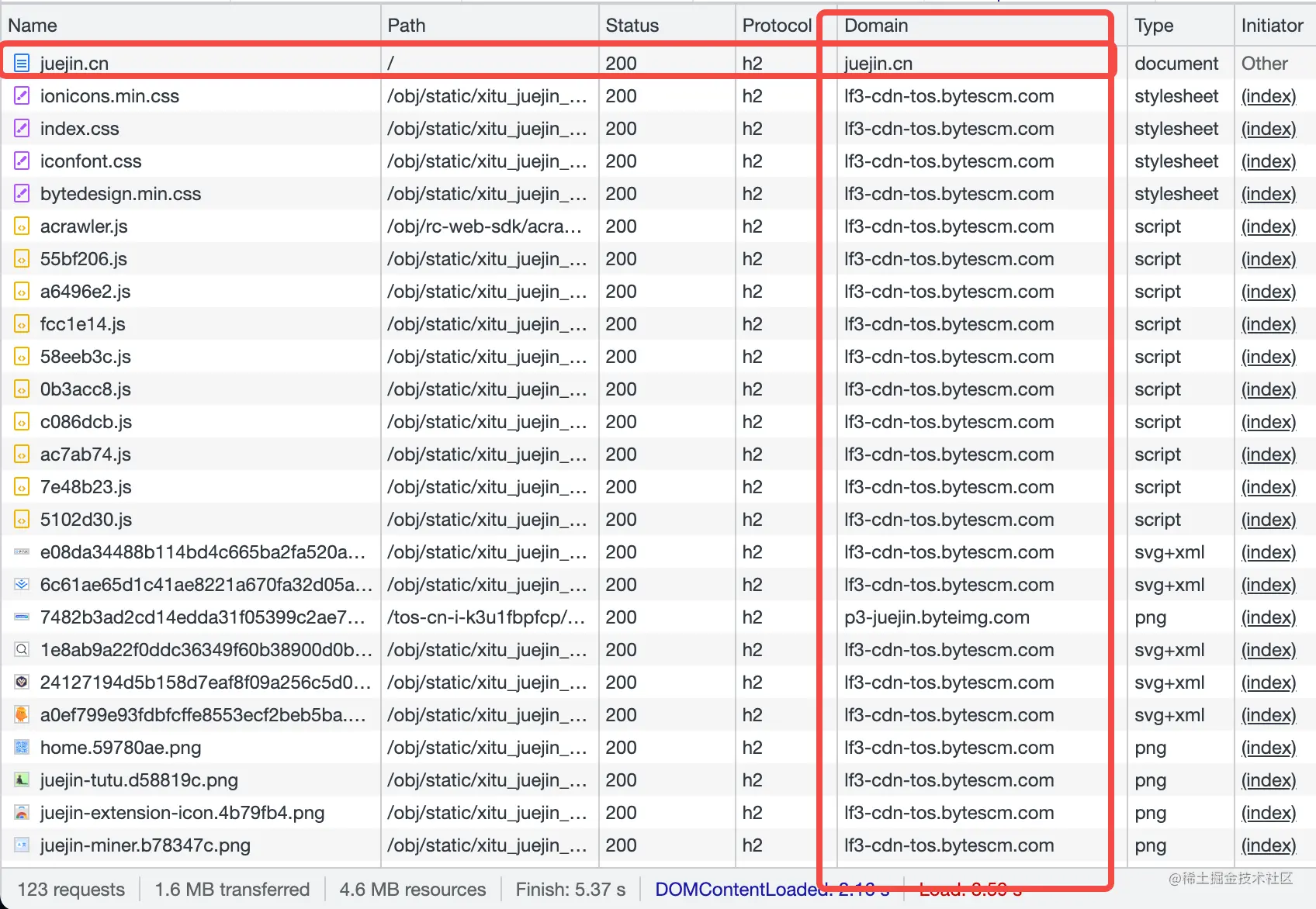
This is easy to understand. Improving the processing capacity of the service will naturally allow it to handle more traffic.
For SSR services, there are several suggestions as follows
Suggestion 1: Let the ssr service only handle the return of the root HTML, and all other resources must be placed on the CDN
For the ssr service, it is very important to give a Suggestions
Let the ssr service only handle the return of the root HTML, and all other resources must be placed on the CDN
Here It is easy to understand if we take juejin as an example. We can see from the figure below that juejin itself is also an SSR service. The origin site only processes the root HTML, and all other resources (js, css, pictures, fonts, etc.) are placed in on CDN. The purpose of this is also to improve the processing capabilities of the origin site, which puts a lot of pressure on the CDN

Suggestions 2: When an attack comes, temporarily downgrade SSR to CSR

SSR rendering is more CPU-intensive (requires compilation and parsing to generate HTML) , so the QPS capability of the ssr service is not high. It is easy to be defeated when facing attacks
Solution: Temporarily downgrade SSR to CSR
How to downgrade SSR?
-
Downgrade to CSR (client-side rendering), so that there is no need to generate complex HTML on the server side, and only need to return simple HTML.
CSR is a single-page application. The simplest example is the UI component library. As you can see in the picture below, this HTML is very simple and static. Returning this static HTML does not consume much server resources.
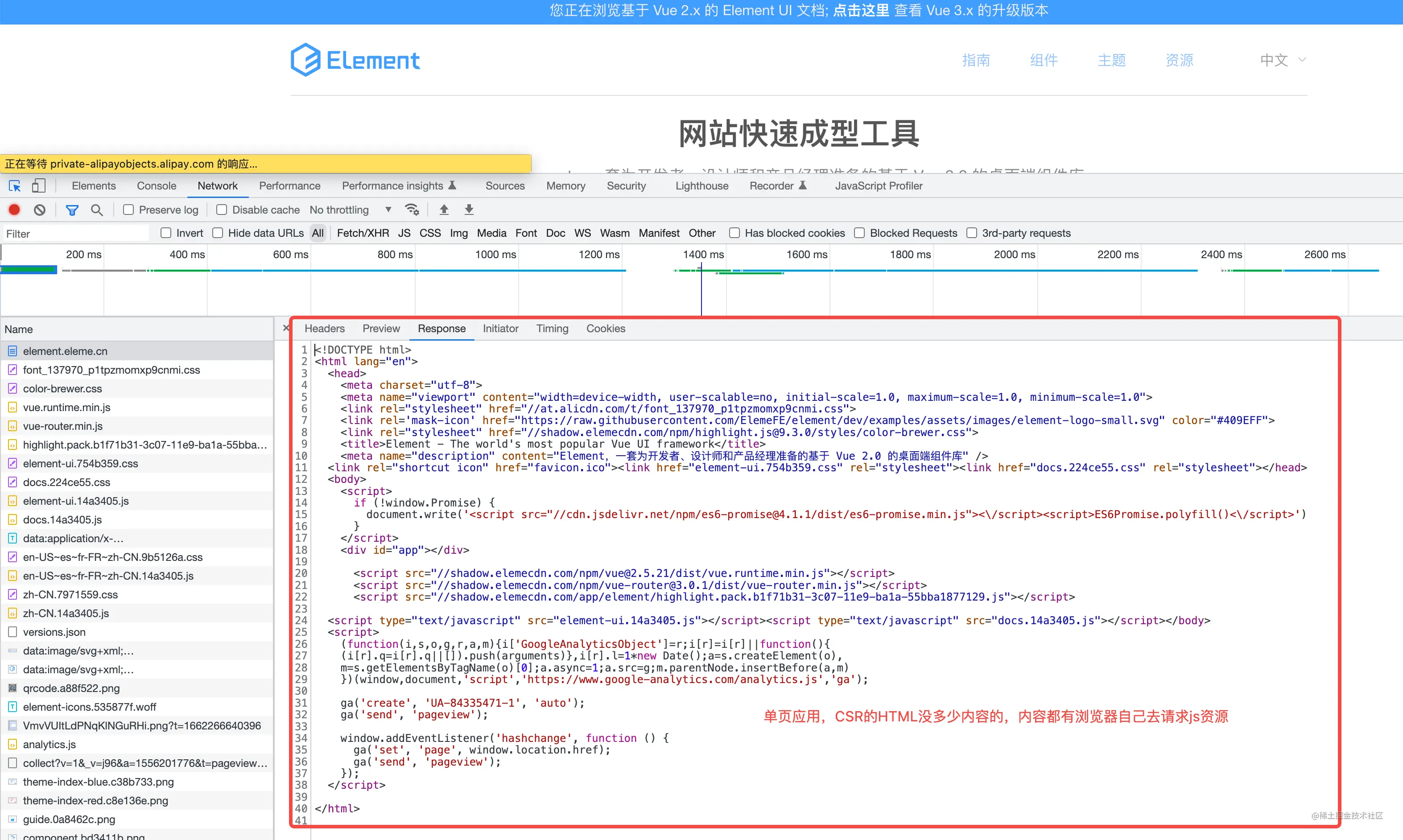
And you can also cache the root HTML file in memory, which can increase the processing power of the server. Improved dozens or even hundreds of times
I will write about how to achieve SSR downgrade in a later article
6. Others
For example, there may be elastic expansion and contraction capabilities, which can only resist small traffic attacks
How to deal with emergency situations after being attacked?
has been attacked, and the service has started to be very slow, or even directly blocked. At this time, it is too late to optimize the code layer, and can only do some configurations at the operation and maintenance layer
I mainly list the following three points here, welcome to add
Expansion
Upgrade protection strategy
Enable CDN caching
1. Capacity expansion
can only deal with small traffic attacks
2. Upgrade protection strategy
This is a bit involving business secrets... I don’t dare to write about it. Friends who are interested can search for it by themselves, or ask about the company’s operation and maintenance
Anyway, there is one thing I guessed. Generally, after paying money to the CDN, there may not be attacks later. Even if there are, they may only be attacks with small traffic and easy to protect.
3. Turn on CDN caching
ssr service, if the CDN cache is not turned on during normal access, you can temporarily turn on the CDN cache when it is attacked.
Summary
The sooner you take preventive measures, the better. Don’t start taking them only after you are attacked, because a lot of losses may have already been caused.
Only when you have done what you need to do and answered what needs to be done, you will have room to operate the configuration when you are actually attacked. Otherwise, you can only pray to God to attack quickly. Stop... Or you can only passively accept blackmail
Safety is no trivial matter, may the world be peaceful
For more node-related knowledge, please visit:nodejs tutorial !
The above is the detailed content of What is a DDos attack? How does the node SSR service prevent and handle attacks?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1667
1667
 14
14
 1426
1426
 52
52
 1328
1328
 25
25
 1273
1273
 29
29
 1255
1255
 24
24
 How to delete node in nvm
Dec 29, 2022 am 10:07 AM
How to delete node in nvm
Dec 29, 2022 am 10:07 AM
How to delete node with nvm: 1. Download "nvm-setup.zip" and install it on the C drive; 2. Configure environment variables and check the version number through the "nvm -v" command; 3. Use the "nvm install" command Install node; 4. Delete the installed node through the "nvm uninstall" command.
 How to use express to handle file upload in node project
Mar 28, 2023 pm 07:28 PM
How to use express to handle file upload in node project
Mar 28, 2023 pm 07:28 PM
How to handle file upload? The following article will introduce to you how to use express to handle file uploads in the node project. I hope it will be helpful to you!
 Pi Node Teaching: What is a Pi Node? How to install and set up Pi Node?
Mar 05, 2025 pm 05:57 PM
Pi Node Teaching: What is a Pi Node? How to install and set up Pi Node?
Mar 05, 2025 pm 05:57 PM
Detailed explanation and installation guide for PiNetwork nodes This article will introduce the PiNetwork ecosystem in detail - Pi nodes, a key role in the PiNetwork ecosystem, and provide complete steps for installation and configuration. After the launch of the PiNetwork blockchain test network, Pi nodes have become an important part of many pioneers actively participating in the testing, preparing for the upcoming main network release. If you don’t know PiNetwork yet, please refer to what is Picoin? What is the price for listing? Pi usage, mining and security analysis. What is PiNetwork? The PiNetwork project started in 2019 and owns its exclusive cryptocurrency Pi Coin. The project aims to create a one that everyone can participate
 An in-depth analysis of Node's process management tool 'pm2”
Apr 03, 2023 pm 06:02 PM
An in-depth analysis of Node's process management tool 'pm2”
Apr 03, 2023 pm 06:02 PM
This article will share with you Node's process management tool "pm2", and talk about why pm2 is needed, how to install and use pm2, I hope it will be helpful to everyone!
 What to do if npm node gyp fails
Dec 29, 2022 pm 02:42 PM
What to do if npm node gyp fails
Dec 29, 2022 pm 02:42 PM
npm node gyp fails because "node-gyp.js" does not match the version of "Node.js". The solution is: 1. Clear the node cache through "npm cache clean -f"; 2. Through "npm install -g n" Install the n module; 3. Install the "node v12.21.0" version through the "n v12.21.0" command.
 Let's talk about how to use pkg to package Node.js projects into executable files.
Dec 02, 2022 pm 09:06 PM
Let's talk about how to use pkg to package Node.js projects into executable files.
Dec 02, 2022 pm 09:06 PM
How to package nodejs executable file with pkg? The following article will introduce to you how to use pkg to package a Node project into an executable file. I hope it will be helpful to you!
 Token-based authentication with Angular and Node
Sep 01, 2023 pm 02:01 PM
Token-based authentication with Angular and Node
Sep 01, 2023 pm 02:01 PM
Authentication is one of the most important parts of any web application. This tutorial discusses token-based authentication systems and how they differ from traditional login systems. By the end of this tutorial, you will see a fully working demo written in Angular and Node.js. Traditional Authentication Systems Before moving on to token-based authentication systems, let’s take a look at traditional authentication systems. The user provides their username and password in the login form and clicks Login. After making the request, authenticate the user on the backend by querying the database. If the request is valid, a session is created using the user information obtained from the database, and the session information is returned in the response header so that the session ID is stored in the browser. Provides access to applications subject to
 A brief analysis of how node implements ocr
Oct 31, 2022 pm 07:09 PM
A brief analysis of how node implements ocr
Oct 31, 2022 pm 07:09 PM
How to implement OCR (optical character recognition)? The following article will introduce to you how to use node to implement OCR. I hope it will be helpful to you!



