 Software Tutorial
Software Tutorial
 Mobile Application
Mobile Application
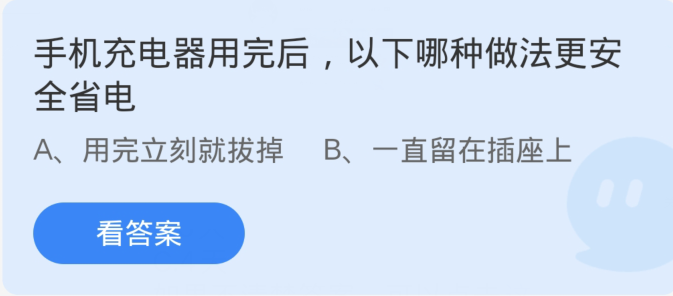
 Ant Manor March 30: Which of the following methods is safer and saves power after running out of mobile phone chargers?
Ant Manor March 30: Which of the following methods is safer and saves power after running out of mobile phone chargers?
Ant Manor March 30: Which of the following methods is safer and saves power after running out of mobile phone chargers?
Question from Ant Manor on March 30: After using up the mobile phone charger, which of the following methods is safer and saves power? Many friends don’t know which method is safer and saves power after using up the mobile phone charger, so the editor below will bring you the answer to Ant Manor’s daily question on March 30. If you are interested, come and find out.
php Editor Strawberry reminds: Ant Manor 3 officially announced on March 30, which of the following methods is safer and saves power after the mobile phone charger is used up? When using a charger, in order to ensure safety and extend battery life, it is recommended to avoid operating the charger at the same time, avoid long-term overtime charging, choose the original charger, avoid using inferior chargers, do not over-discharge, avoid over-charging and other operations , to ensure charging safety.
Ant Manor Today’s Answer 3.27
Ant Manor March 30: After running out of mobile phone chargers, which of the following methods is safer and saves power?
Question: After using up the mobile phone charger, which of the following methods is safer and saves power?
Answer:Unplug it immediately after use
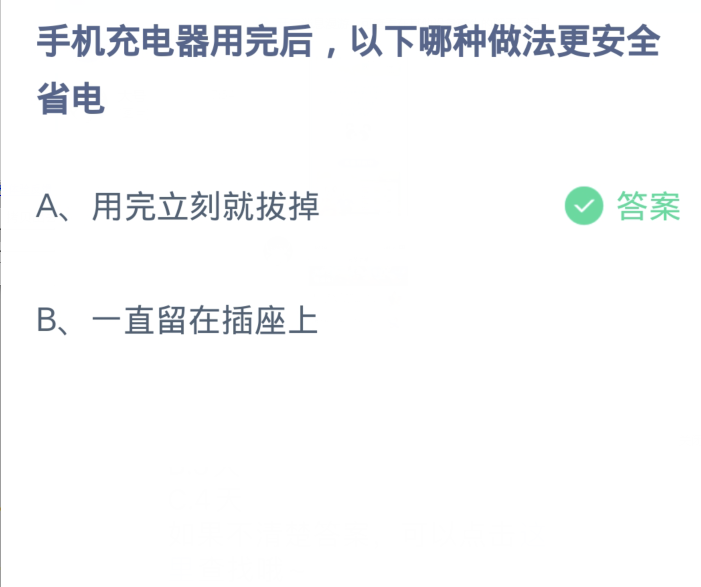
Answer analysis:
1. The brightness of the mobile phone screen is the biggest power consumption of the mobile phone. Appropriately lowering the screen brightness can effectively save the power of the mobile phone;
2. We can also turn on the "Automatically adjust brightness" setting to let the brightness change with changes in the external environment;
3. Some gadgets in mobile phones also consume power, such as Wi-Fi, Bluetooth, GPS positioning, traffic, etc.

The above is the detailed content of Ant Manor March 30: Which of the following methods is safer and saves power after running out of mobile phone chargers?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1425
1425
 52
52
 1325
1325
 25
25
 1272
1272
 29
29
 1252
1252
 24
24
 What are the new ways to accumulate sesame seeds with Alipay's Sesame Credit?_Introduction to Alipay's new ways to increase Sesame Credit
Apr 11, 2024 pm 02:20 PM
What are the new ways to accumulate sesame seeds with Alipay's Sesame Credit?_Introduction to Alipay's new ways to increase Sesame Credit
Apr 11, 2024 pm 02:20 PM
1. We open Alipay, search for Sesame Credit, and click to enter the official mini program. 2. Click Credit Management. 3. Click on Life Record. 4. Here we can see that credit can be accumulated through various methods such as watering trees with energy, saving money, donating eggs in Ant Manor, and walking for charity. If there is something you want to define, you can click below Can't find what you want to do? click here. 5. Here we take the Ant Forest to accumulate energy as an example. We click to record. 6. You can choose the duration and frequency according to your own situation. Click Next when finished. 7. You can set the number of sesame seeds that will be deducted when the task is not completed. Click Agree to start immediately.
 List of answers to Alipay Ant Manor April 15th
Apr 15, 2024 pm 01:22 PM
List of answers to Alipay Ant Manor April 15th
Apr 15, 2024 pm 01:22 PM
List of answers to Alipay’s Ant Manor on April 15th. Friends, Ant Manor will update two questions every day. Today’s questions are “Chicken and rabbit in the same cage”, which is a popular mathematical question in my country. Guess where it first appeared. Food tips in this book: Any of the following vegetables can be eaten raw or cooked. Let me tell you the correct answer below. List of answers to Alipay Ant Manor on April 15th 1. "Chicken and rabbit in the same cage" is a popular mathematical question in my country. Guess which book it first appeared in. The correct answer is: "Sun Zi Suan Jing" 2. Food tips: Which of the following vegetables can be eaten raw or cooked? The correct answer is: White radish Friends, the updated questions in Ant Manor not only allow friends to learn a variety of knowledge, but also participate in charity activities. White radish can be
 Where is Alipay Baba Farm closed_How to close Alipay Baba Farm
Apr 11, 2024 pm 07:34 PM
Where is Alipay Baba Farm closed_How to close Alipay Baba Farm
Apr 11, 2024 pm 07:34 PM
1. Open Alipay, then find the option of Ant Manor and click to enter. 2. After entering Ant Manor, click the three dots in the upper right corner, and click the settings option in the pop-up page. 3. After entering the settings, find the option to close Baba Farm and click Close on the right.
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access
 PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
In the security comparison between Slim and Phalcon in PHP micro-frameworks, Phalcon has built-in security features such as CSRF and XSS protection, form validation, etc., while Slim lacks out-of-the-box security features and requires manual implementation of security measures. For security-critical applications, Phalcon offers more comprehensive protection and is the better choice.
 How to enhance the security of Spring Boot framework
Jun 01, 2024 am 09:29 AM
How to enhance the security of Spring Boot framework
Jun 01, 2024 am 09:29 AM
How to Enhance the Security of SpringBoot Framework It is crucial to enhance the security of SpringBoot applications to protect user data and prevent attacks. The following are several key steps to enhance SpringBoot security: 1. Enable HTTPS Use HTTPS to establish a secure connection between the server and the client to prevent information from being eavesdropped or tampered with. In SpringBoot, HTTPS can be enabled by configuring the following in application.properties: server.ssl.key-store=path/to/keystore.jksserver.ssl.k
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.



