Review: MOBOX Hacked Analysis
Background
On March 14, 2024, according to the early warning of the Slow Mist MistEye security monitoring system, the decentralized lending protocol MOBOX on the Optimism chain was attacked, causing losses of approximately $750,000. The SlowMist security team analyzed the attack incident and shared the results as follows:
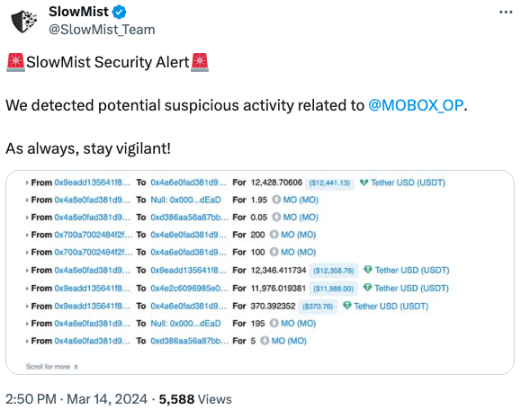
(https://twitter.com/SlowMist_Team /status/1768167772230713410)
##Related information
Attacker address:
0x4e2c6096985e0b2825d06c16f1c8cdc559c1d6f8
0x96f004c81d2c7b907f92c45922d38ab870a53945
Attacked contract address:
0xae7b6514af26bcb2332fea53b8dd57bc13a7838e
Attack transaction:
##0x4ec3061724ca9f0b8d400866dd83b92647ad8c943a1c0ae9ae6c9bd1ef789417There are two main core points of this attack. One is that the attacker exploits the borrow() function vulnerability in the contract, and each time it is called The function will trigger the distribution of rewards to the recommender's address. Since the reward calculation is based on the number of transferred tokens, the attacker can increase the amount of the next borrowing by transferring the reward to the referrer back to the attacked contract again. The second is that each time the borrow() function is called, a part of the MO tokens in the pool will be burned, so the price of MO tokens is continuously raised. In the end, the attacker can make profits by continuously borrowing and superimposing rewards. We can find that the entire attack process mainly involves calling the vulnerable borrow() function in a loop, and then immediately calling redeem() performs a redemption and then transfers the tokens allocated to the referrer back to the attack contract. Following up the analysis of the borrow() function, we can find that every time this function is called, part of the MO tokens in the pool will be burned. However, the amount of USDT loaned out is calculated based on the price of MO tokens in the pool. Since the price of MO tokens is burned due to The continuous increase eventually led to the attacker using a small amount of MO tokens to lend out a large amount of USDT tokens. In addition, each time a loan is borrowed, a referrer address will be given a dividend reward, and this function is based on the number of MO tokens passed in. computational. However, since the recommender address is also controlled by the attacker (0x96f004c81d2c7b907f92c45922d38ab870a53945), the attacker can reward this part after completing the loan operation. Transfer it back to superimpose the next borrowing amount and dividend rewards. After the above cycle operation, the attacker increased the price of MO tokens, and finally could use a very small number of MO tokens to lend out large amounts of money in the contract. amount of USDT, and directly exchange all USDT in the unbalanced pool to make a profit. The core of this attack is that the attacker uses the borrow() function to burn the pool The mechanism of partial tokens in the middle continuously borrows assets to increase the price of tokens in the pool and obtains referrer rewards, and then transfers the tokens back and borrows them again, thereby continuously adding rewards and manipulating prices. The SlowMist security team recommends that project parties add lock-up time limits to similar functions and consider multiple factors when designing the price model of lending to avoid similar incidents from happening again. Attack Core
Transaction Analysis
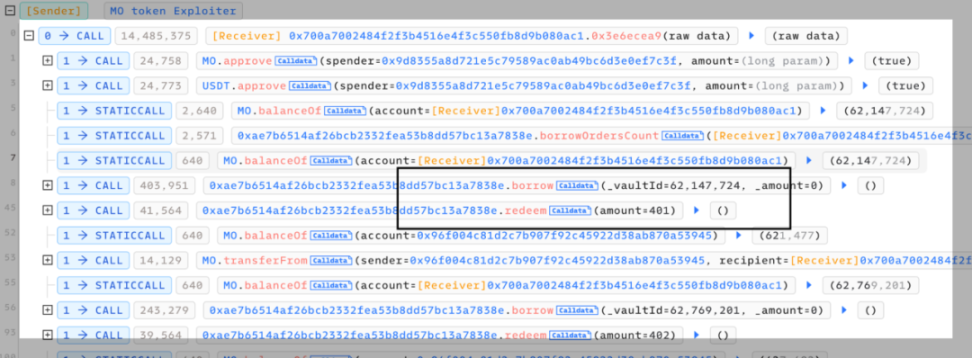
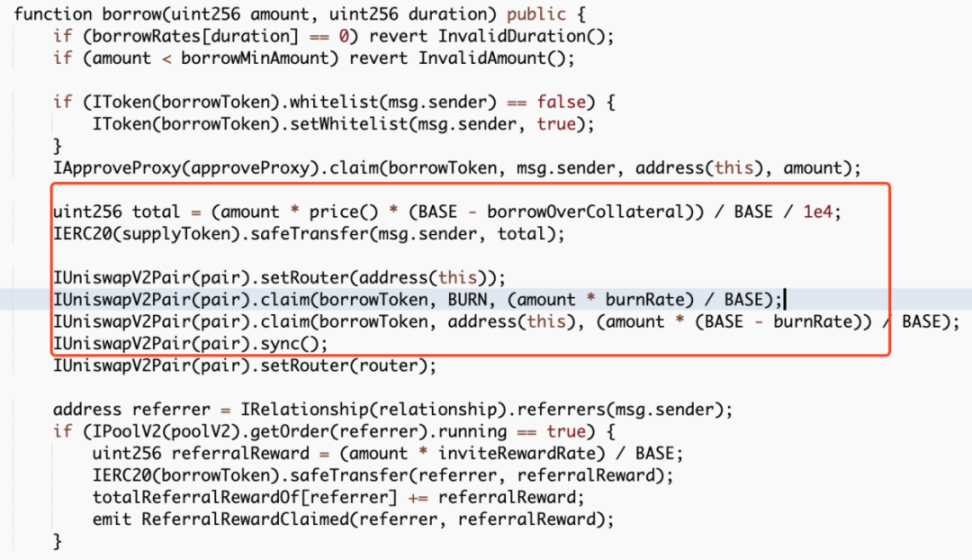
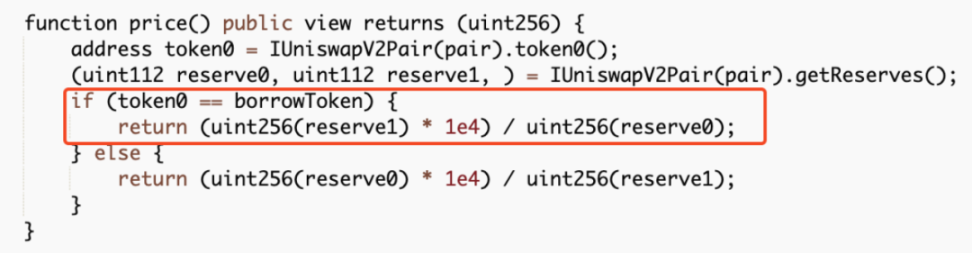
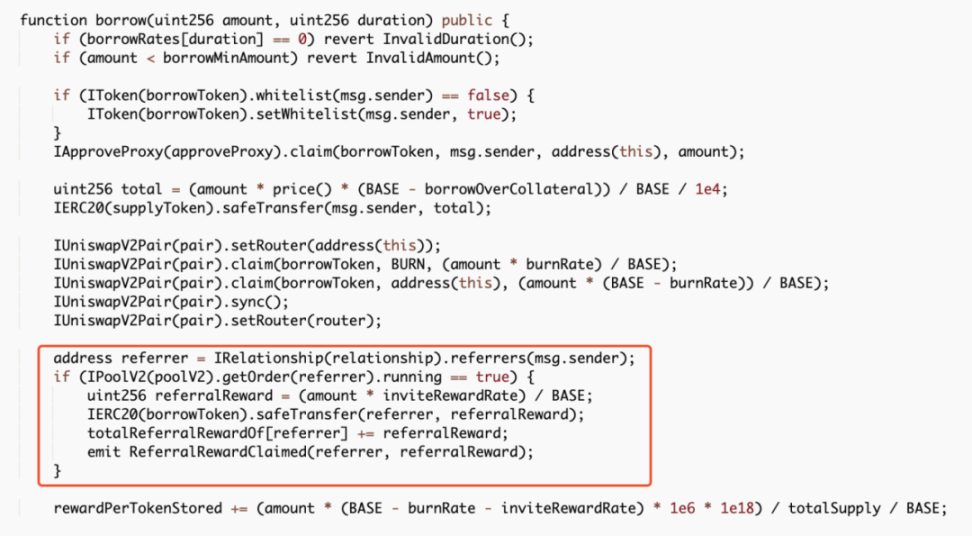
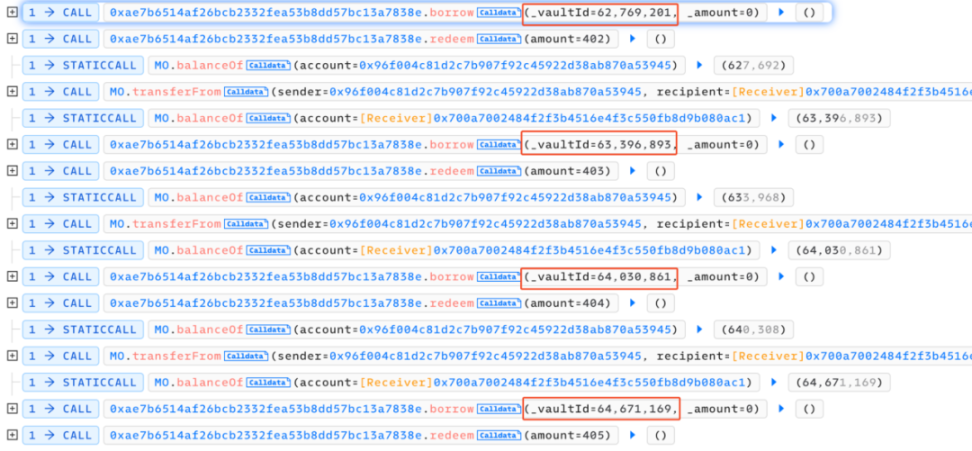
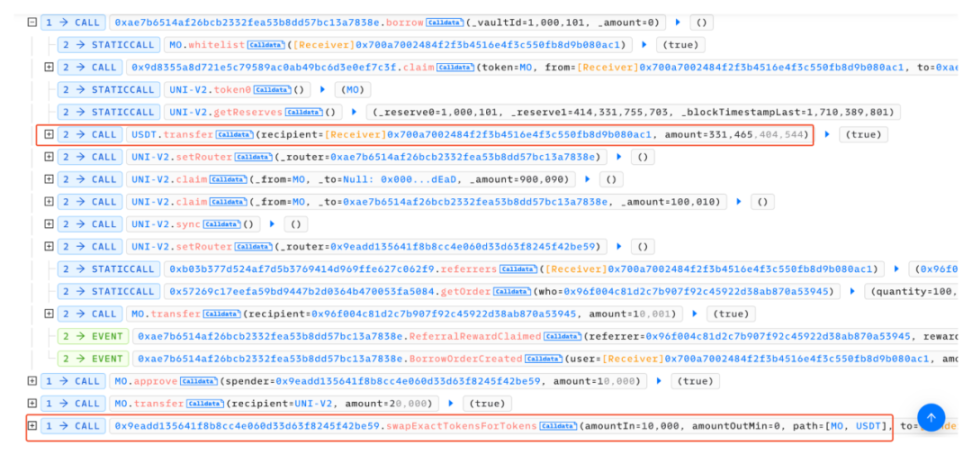
Summary
The above is the detailed content of Review: MOBOX Hacked Analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Ouyi Ouyi Ouyi Ouix Ouyi Global Station Login Home Page
Apr 21, 2025 pm 11:57 PM
Ouyi Ouyi Ouyi Ouix Ouyi Global Station Login Home Page
Apr 21, 2025 pm 11:57 PM
Ouyi OKX is the world's leading digital asset trading platform. 1) Its development history includes: it will be launched in 2017, the Chinese name "Ouyi" will be launched in 2021, and it will be renamed Ouyi OKX in 2022. 2) Core services include: trading services (coin, leverage, contracts, DEX, fiat currency trading) and financial services (Yubibao, DeFi mining, lending). 3) The platform's special functions include: market data services and risk control system. 4) Core advantages include: technical strength, security system, service support and market coverage.
 How to trade quantum chains
Apr 21, 2025 pm 11:42 PM
How to trade quantum chains
Apr 21, 2025 pm 11:42 PM
The quantum chain (Qtum) transaction process includes three stages: preliminary preparation, purchase and sale. 1. Preparation: Select a compliant exchange, register an account, perform identity verification, and set up a wallet. 2. Purchase quantum chains: recharge funds, find trading pairs, place orders (market orders or limit orders), and confirm transactions. 3. Sell quantum chains: Enter the trading page, select the trading pair and order type (market order or limit order), confirm the transaction and withdraw cash.
 The latest updates to the oldest virtual currency rankings
Apr 22, 2025 am 07:18 AM
The latest updates to the oldest virtual currency rankings
Apr 22, 2025 am 07:18 AM
The ranking of virtual currencies’ “oldest” is as follows: 1. Bitcoin (BTC), issued on January 3, 2009, is the first decentralized digital currency. 2. Litecoin (LTC), released on October 7, 2011, is known as the "lightweight version of Bitcoin". 3. Ripple (XRP), issued in 2011, is designed for cross-border payments. 4. Dogecoin (DOGE), issued on December 6, 2013, is a "meme coin" based on the Litecoin code. 5. Ethereum (ETH), released on July 30, 2015, is the first platform to support smart contracts. 6. Tether (USDT), issued in 2014, is the first stablecoin to be anchored to the US dollar 1:1. 7. ADA,
 What are the hybrid blockchain trading platforms?
Apr 21, 2025 pm 11:36 PM
What are the hybrid blockchain trading platforms?
Apr 21, 2025 pm 11:36 PM
Suggestions for choosing a cryptocurrency exchange: 1. For liquidity requirements, priority is Binance, Gate.io or OKX, because of its order depth and strong volatility resistance. 2. Compliance and security, Coinbase, Kraken and Gemini have strict regulatory endorsement. 3. Innovative functions, KuCoin's soft staking and Bybit's derivative design are suitable for advanced users.
 Ranking of leveraged exchanges in the currency circle The latest recommendations of the top ten leveraged exchanges in the currency circle
Apr 21, 2025 pm 11:24 PM
Ranking of leveraged exchanges in the currency circle The latest recommendations of the top ten leveraged exchanges in the currency circle
Apr 21, 2025 pm 11:24 PM
The platforms that have outstanding performance in leveraged trading, security and user experience in 2025 are: 1. OKX, suitable for high-frequency traders, providing up to 100 times leverage; 2. Binance, suitable for multi-currency traders around the world, providing 125 times high leverage; 3. Gate.io, suitable for professional derivatives players, providing 100 times leverage; 4. Bitget, suitable for novices and social traders, providing up to 100 times leverage; 5. Kraken, suitable for steady investors, providing 5 times leverage; 6. Bybit, suitable for altcoin explorers, providing 20 times leverage; 7. KuCoin, suitable for low-cost traders, providing 10 times leverage; 8. Bitfinex, suitable for senior play
 Ranking of the top ten digital currency exchanges The latest list of top ten virtual currency trading software platforms
Apr 22, 2025 pm 01:15 PM
Ranking of the top ten digital currency exchanges The latest list of top ten virtual currency trading software platforms
Apr 22, 2025 pm 01:15 PM
The top ten digital currency exchanges are: 1. Binance, 2. OKX, 3. gate.io, 4. Coinbase, 5. Kraken, 6. Bitfinex, 7. Huobi, 8. KuCoin, 9. Bitstamp, 10. Gemini, these platforms are highly regarded for their high liquidity, extensive trading pairs, relatively low transaction fees, multi-level security measures, and a friendly user interface.
 How long does it take to recharge digital currency to arrive? Recommended mainstream digital currency recharge platform
Apr 21, 2025 pm 08:00 PM
How long does it take to recharge digital currency to arrive? Recommended mainstream digital currency recharge platform
Apr 21, 2025 pm 08:00 PM
The time for recharge of digital currency varies depending on the method: 1. Bank transfer usually takes 1-3 working days; 2. Recharge of credit cards or third-party payment platforms within a few minutes to a few hours; 3. The time for recharge of digital currency transfer is usually 10 minutes to 1 hour based on the blockchain confirmation time, but it may be delayed due to factors such as network congestion.
 What to do if the USDT transfer address is incorrect? Guide for beginners
Apr 21, 2025 pm 12:12 PM
What to do if the USDT transfer address is incorrect? Guide for beginners
Apr 21, 2025 pm 12:12 PM
After the USDT transfer address is incorrect, first confirm that the transfer has occurred, and then take measures according to the error type. 1. Confirm the transfer: view the transaction history, obtain and query the transaction hash value on the blockchain browser. 2. Take measures: If the address does not exist, wait for the funds to be returned or contact customer service; if it is an invalid address, contact customer service and seek professional help; if it is transferred to someone else, try to contact the payee or seek legal help.





