 Computer Tutorials
Computer Tutorials
 Computer Knowledge
Computer Knowledge
 Secure boot can be enabled when the system is in user mode
Secure boot can be enabled when the system is in user mode
Secure boot can be enabled when the system is in user mode
Secure Boot is a security standard developed by members of the PC industry to ensure that devices can only boot and run software trusted by the original equipment manufacturer (OEM). In Windows 11, secure boot is a basic requirement. When you enable Secure Boot, if you encounter the error SYSTEM in setup mode, this may indicate that the system is currently in user mode. In this case, the solutions provided in this article will help you.
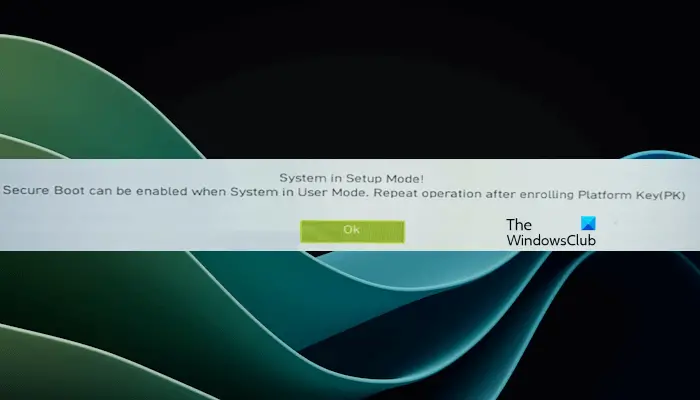
Secure Boot can be enabled when the system is in user mode
After enabling Secure Boot on your device, you may receive the error "Secure Boot can be enabled when the system is in user mode." To install Windows 11, Secure Boot must be enabled on the system. Nonetheless, other methods exist to install Windows 11 without Secure Boot.
Some games may require the Secure Boot option to be enabled to run properly. If you successfully installed Windows 11 by bypassing the Secure Boot option, these games may not play properly. Therefore, it is important to fix this problem. Here are a few suggestions to help you resolve this error.
Let's look at all the fixes in detail.
1]Check your hard drive partition style
The first step is to check the partition type of the hard disk. To do this, follow these steps:
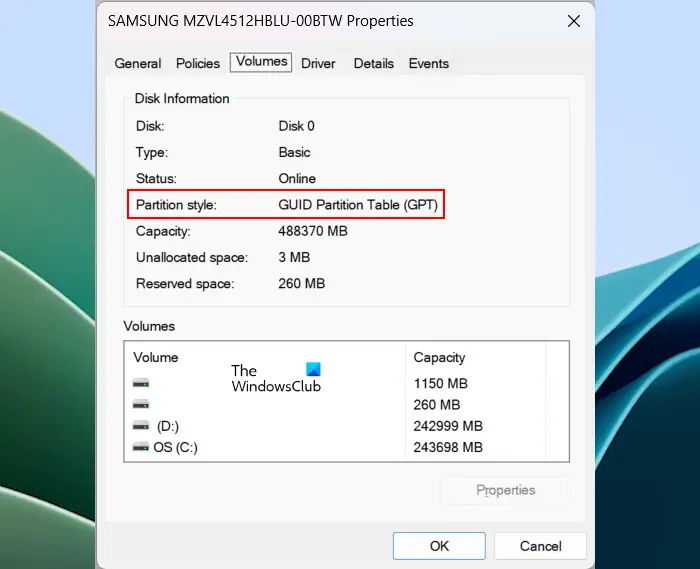
If your hard drive adopts MBR partition type, please consider converting it to GPT. Normally, converting MBR to GPT will result in data loss, but there are some special tools and methods that can help you complete this conversion without losing data. Therefore, before performing this operation, be sure to back up important data in case something unexpected happens. Doing so ensures that your data is fully protected and no important information is lost during the conversion of partition type.
Now, try to enable secure boot. If Secure Boot cannot be enabled, try other fixes.
2]Close CSM
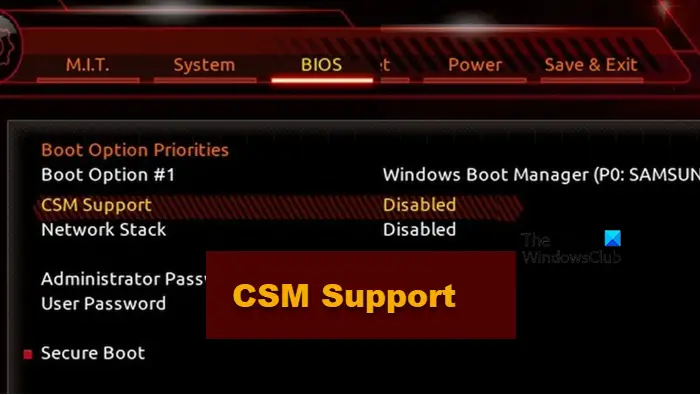
Modern computer systems come with UEFI support. In such computer systems, CSM support is not required. So, if CSM is enabled on your system, you can disable it. Different brands of motherboards may have different methods of disabling CSM in the BIOS. You need to visit your computer motherboard manufacturer's official website to learn the exact method of disabling CSM in the BIOS.
3]Change system mode to user
The error message states that Secure Boot can be enabled when the system is in user mode. Therefore, if your system is in setup mode, Secure Boot cannot be enabled. Change setup mode to user mode and you will be able to enable secure boot.
Different brands of motherboards may switch between system mode and user mode differently. Please refer to the motherboard's user manual or refer to its official website for specific operation methods.
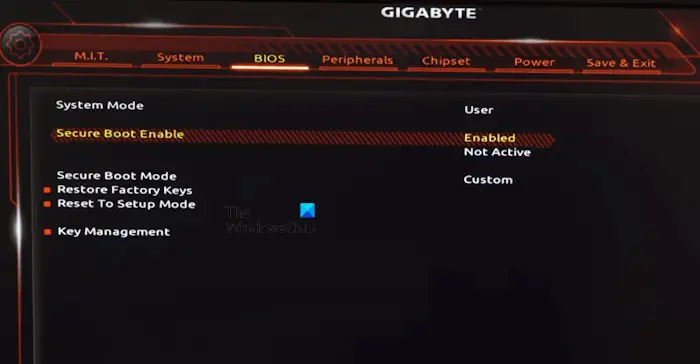
For example, in MSI and GB motherboards, you must install the default factory key. Here are the steps to do this:
You may receive a pop-up message about resetting your system. Click No. You should now be able to enable secure boot. After enabling Secure Boot, change the Secure Boot mode back to Standard. Save BIOS settings and exit.
4]Generate platform key (for ASUS Phantom gaming motherboard users)
This solution is for ASUS Phantom gaming motherboard users. If your system has this motherboard and you are unable to install the default Secure Boot key, you can generate a platform key.
To do this, enter your computer's BIOS and go to the Security tab. There, you will see an option called Key Management. Select it and then choose Build Options or something similar to Build Options.
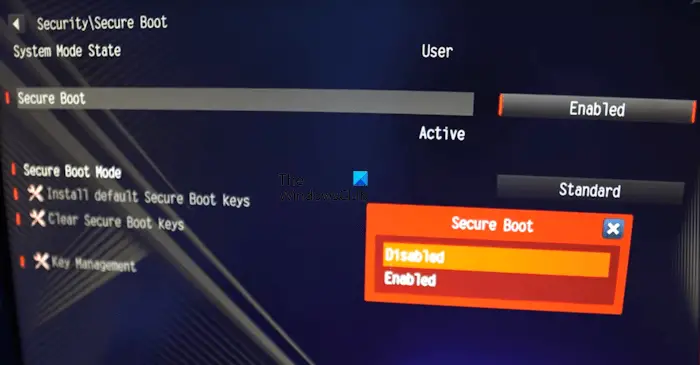
Now, go back to the Secure Boot page in BIOS and switch the Secure Boot mode from Standard to Custom. This will enable the option to install the default Secure Boot key. Click on the Install Default Secure Boot Keys option. Once this is done, enable secure boot.
After enabling Secure Boot, change the Secure Boot mode back to Standard. Save changes and exit.
5]Restore BIOS settings to default settings
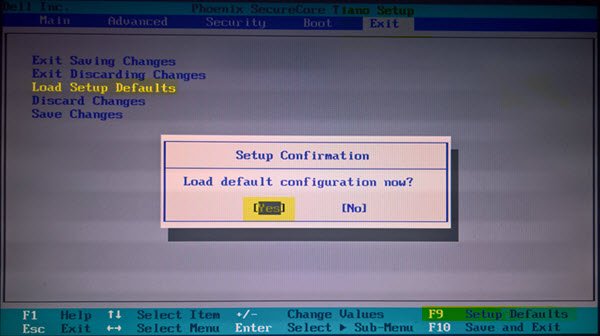
If none of the above fixes solve your problem, you can restore all BIOS settings to their default settings. After doing this, you should be able to enable secure boot. Before resetting your BIOS settings to default, we recommend that you write down all the changes you have made in the BIOS so that you can make all these changes again after enabling Secure Boot.
I hope this helps.
How to enable secure boot in system configuration?
There is no option to enable secure boot in the system configuration or message configuration. Therefore, it is necessary to enter your BIOS settings to enable Secure Boot on your device. Visit your computer manufacturer's official website to learn the private key to enter the BIOS.
Why can't I enable Secure Boot?
There may be many reasons why Secure Boot cannot be enabled or the Secure Boot option is grayed out on your system. You may have changed the settings to disable the secure boot option. The easiest way to fix this problem is to reset the BIOS to factory default settings.
Read next: Windows computer won’t boot after enabling Secure Boot.
The above is the detailed content of Secure boot can be enabled when the system is in user mode. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1421
1421
 52
52
 1315
1315
 25
25
 1266
1266
 29
29
 1239
1239
 24
24
 Summary of phpmyadmin vulnerabilities
Apr 10, 2025 pm 10:24 PM
Summary of phpmyadmin vulnerabilities
Apr 10, 2025 pm 10:24 PM
The key to PHPMyAdmin security defense strategy is: 1. Use the latest version of PHPMyAdmin and regularly update PHP and MySQL; 2. Strictly control access rights, use .htaccess or web server access control; 3. Enable strong password and two-factor authentication; 4. Back up the database regularly; 5. Carefully check the configuration files to avoid exposing sensitive information; 6. Use Web Application Firewall (WAF); 7. Carry out security audits. These measures can effectively reduce the security risks caused by PHPMyAdmin due to improper configuration, over-old version or environmental security risks, and ensure the security of the database.
 How to update the image of docker
Apr 15, 2025 pm 12:03 PM
How to update the image of docker
Apr 15, 2025 pm 12:03 PM
The steps to update a Docker image are as follows: Pull the latest image tag New image Delete the old image for a specific tag (optional) Restart the container (if needed)
 What are the common misunderstandings in CentOS HDFS configuration?
Apr 14, 2025 pm 07:12 PM
What are the common misunderstandings in CentOS HDFS configuration?
Apr 14, 2025 pm 07:12 PM
Common problems and solutions for Hadoop Distributed File System (HDFS) configuration under CentOS When building a HadoopHDFS cluster on CentOS, some common misconfigurations may lead to performance degradation, data loss and even the cluster cannot start. This article summarizes these common problems and their solutions to help you avoid these pitfalls and ensure the stability and efficient operation of your HDFS cluster. Rack-aware configuration error: Problem: Rack-aware information is not configured correctly, resulting in uneven distribution of data block replicas and increasing network load. Solution: Double check the rack-aware configuration in the hdfs-site.xml file and use hdfsdfsadmin-printTopo
 What are the oracle11g database migration tools?
Apr 11, 2025 pm 03:36 PM
What are the oracle11g database migration tools?
Apr 11, 2025 pm 03:36 PM
How to choose Oracle 11g migration tool? Determine the migration target and determine the tool requirements. Mainstream tool classification: Oracle's own tools (expdp/impdp) third-party tools (GoldenGate, DataStage) cloud platform services (such as AWS, Azure) to select tools that are suitable for project size and complexity. FAQs and Debugging: Network Problems Permissions Data Consistency Issues Insufficient Space Optimization and Best Practices: Parallel Processing Data Compression Incremental Migration Test
 How to solve the oracle lock table
Apr 11, 2025 pm 07:45 PM
How to solve the oracle lock table
Apr 11, 2025 pm 07:45 PM
Oracle lock tables can be solved by viewing lock information and finding locked objects and sessions. Use the KILL command to terminate the idle locked session. Restart the database instance and release all locks. Use the ALTER SYSTEM KILL SESSION command to terminate a stubborn locked session. Use the DBMS_LOCK package for programmatic lock management. Optimize query to reduce lock frequency. Set lock compatibility level to reduce lock contention. Use concurrency control mechanisms to reduce locking requirements. Enable automatic deadlock detection, and the system will automatically roll back the deadlock session.
 What is the impact of Redis persistence on memory?
Apr 10, 2025 pm 02:15 PM
What is the impact of Redis persistence on memory?
Apr 10, 2025 pm 02:15 PM
Redis persistence will take up extra memory, RDB temporarily increases memory usage when generating snapshots, and AOF continues to take up memory when appending logs. Influencing factors include data volume, persistence policy and Redis configuration. To mitigate the impact, you can reasonably configure RDB snapshot policies, optimize AOF configuration, upgrade hardware and monitor memory usage. Furthermore, it is crucial to find a balance between performance and data security.
 How to create oracle database How to create oracle database
Apr 11, 2025 pm 02:36 PM
How to create oracle database How to create oracle database
Apr 11, 2025 pm 02:36 PM
To create an Oracle database, the common method is to use the dbca graphical tool. The steps are as follows: 1. Use the dbca tool to set the dbName to specify the database name; 2. Set sysPassword and systemPassword to strong passwords; 3. Set characterSet and nationalCharacterSet to AL32UTF8; 4. Set memorySize and tablespaceSize to adjust according to actual needs; 5. Specify the logFile path. Advanced methods are created manually using SQL commands, but are more complex and prone to errors. Pay attention to password strength, character set selection, tablespace size and memory
 What to do if the oracle log is full
Apr 12, 2025 am 06:09 AM
What to do if the oracle log is full
Apr 12, 2025 am 06:09 AM
When Oracle log files are full, the following solutions can be adopted: 1) Clean old log files; 2) Increase the log file size; 3) Increase the log file group; 4) Set up automatic log management; 5) Reinitialize the database. Before implementing any solution, it is recommended to back up the database to prevent data loss.



