Detailed explanation of using Proxy in JS

Detailed explanation of the use of Proxy in JS, specific code examples are required
Introduction:
In JavaScript, Proxy is a very powerful and useful feature. It allows us to create a proxy object that intercepts and customizes the operations of the target object. In this article, we will introduce the use of Proxy in detail, including creating Proxy objects, interception operations and practical application examples.
1. Create a Proxy object
To create a Proxy object, we can use the Proxy constructor. The Proxy constructor accepts two parameters, the target object and the handler. The target object is the object being proxied, and the handler is an object that contains a set of interception methods.
The following is a simple example of creating a Proxy object:
const target = {
name: 'Alice',
age: 25
};
const handler = {
get: function(target, property) {
console.log(`正在获取${property}`);
return target[property];
},
set: function(target, property, value) {
console.log(`正在设置${property}为${value}`);
target[property] = value;
}
};
const proxy = new Proxy(target, handler);In the above code, we create a target object and then define a handler object as the Proxy handler. In the handler object, we can define interception methods to capture and modify operations on the target object.
2. Interception operations
Through Proxy, we can intercept and process various operations of the target object, including obtaining properties (get), setting properties (set), deleting properties (deleteProperty), calling functions ( apply) and so on. The following are some examples of commonly used interception methods:
- get interception
The get method is used to intercept the acquisition operation of the target object's attributes:
const handler = {
get: function(target, property) {
console.log(`正在获取${property}`);
return target[property];
}
};- set Interception
The set method is used to intercept the setting operation of the target object's properties:
const handler = {
set: function(target, property, value) {
console.log(`正在设置${property}为${value}`);
target[property] = value;
}
};- deleteProperty interception
The deleteProperty method is used to intercept the deletion operation of the target object's properties:
const handler = {
deleteProperty: function(target, property) {
console.log(`正在删除${property}`);
delete target[property];
}
};- apply interception
The apply method is used to intercept the function call operation on the target object:
const handler = {
apply: function(target, thisArg, args) {
console.log(`正在调用函数${target.name}`);
return target.apply(thisArg, args);
}
};3. Practical application examples
Application of Proxy It is very broad and can be used to enhance the functionality of objects or implement data hijacking, etc. The following are some practical application examples:
- Data validation
By intercepting the set method, we can perform data validation when setting attributes. For example, we can intercept the operation of setting the age attribute and ensure that the age is a legal value:
const data = {
name: 'Alice',
age: 25
};
const handler = {
set: function(target, property, value) {
if (property === 'age' && typeof value !== 'number') {
throw new Error('年龄必须是一个数值');
}
target[property] = value;
}
};
const proxy = new Proxy(data, handler);
proxy.age = '25'; // 抛出错误:年龄必须是一个数值- Cache
By intercepting the get method, we can implement a cache object to Reduce the cost of repeated calculations. For example, we can create an object that calculates the area of a circle and caches the calculated results:
const cache = {};
const handler = {
get: function(target, property) {
if (property === 'area') {
if (cache.area) {
console.log('从缓存中获取面积');
return cache.area;
} else {
const area = Math.PI * target.radius * target.radius;
cache.area = area;
return area;
}
}
return target[property];
}
};
const circle = new Proxy({ radius: 5 }, handler);
console.log(circle.area); // 计算并缓存面积
console.log(circle.area); // 从缓存中获取面积Conclusion:
Proxy is a very powerful and practical feature in JavaScript that can Intercept and customize the operation of the target object. By properly using Proxy, we can implement various functions such as data validation and caching, which greatly enhances the flexibility and scalability of JavaScript.
Reference:
- MDN Web Docs - Proxy: https://developer.mozilla.org/zh-CN/docs/Web/JavaScript/Reference/Global_Objects/Proxy
The above is the detailed content of Detailed explanation of using Proxy in JS. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1655
1655
 14
14
 1414
1414
 52
52
 1307
1307
 25
25
 1254
1254
 29
29
 1228
1228
 24
24
 What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
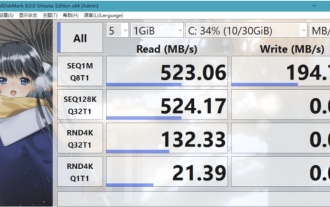
CrystalDiskMark is a small HDD benchmark tool for hard drives that quickly measures sequential and random read/write speeds. Next, let the editor introduce CrystalDiskMark to you and how to use crystaldiskmark~ 1. Introduction to CrystalDiskMark CrystalDiskMark is a widely used disk performance testing tool used to evaluate the read and write speed and performance of mechanical hard drives and solid-state drives (SSD). Random I/O performance. It is a free Windows application and provides a user-friendly interface and various test modes to evaluate different aspects of hard drive performance and is widely used in hardware reviews
 How to download foobar2000? -How to use foobar2000
Mar 18, 2024 am 10:58 AM
How to download foobar2000? -How to use foobar2000
Mar 18, 2024 am 10:58 AM
foobar2000 is a software that can listen to music resources at any time. It brings you all kinds of music with lossless sound quality. The enhanced version of the music player allows you to get a more comprehensive and comfortable music experience. Its design concept is to play the advanced audio on the computer The device is transplanted to mobile phones to provide a more convenient and efficient music playback experience. The interface design is simple, clear and easy to use. It adopts a minimalist design style without too many decorations and cumbersome operations to get started quickly. It also supports a variety of skins and Theme, personalize settings according to your own preferences, and create an exclusive music player that supports the playback of multiple audio formats. It also supports the audio gain function to adjust the volume according to your own hearing conditions to avoid hearing damage caused by excessive volume. Next, let me help you
 BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
MetaMask (also called Little Fox Wallet in Chinese) is a free and well-received encryption wallet software. Currently, BTCC supports binding to the MetaMask wallet. After binding, you can use the MetaMask wallet to quickly log in, store value, buy coins, etc., and you can also get 20 USDT trial bonus for the first time binding. In the BTCCMetaMask wallet tutorial, we will introduce in detail how to register and use MetaMask, and how to bind and use the Little Fox wallet in BTCC. What is MetaMask wallet? With over 30 million users, MetaMask Little Fox Wallet is one of the most popular cryptocurrency wallets today. It is free to use and can be installed on the network as an extension
 How to use NetEase Mailbox Master
Mar 27, 2024 pm 05:32 PM
How to use NetEase Mailbox Master
Mar 27, 2024 pm 05:32 PM
NetEase Mailbox, as an email address widely used by Chinese netizens, has always won the trust of users with its stable and efficient services. NetEase Mailbox Master is an email software specially created for mobile phone users. It greatly simplifies the process of sending and receiving emails and makes our email processing more convenient. So how to use NetEase Mailbox Master, and what specific functions it has. Below, the editor of this site will give you a detailed introduction, hoping to help you! First, you can search and download the NetEase Mailbox Master app in the mobile app store. Search for "NetEase Mailbox Master" in App Store or Baidu Mobile Assistant, and then follow the prompts to install it. After the download and installation is completed, we open the NetEase email account and log in. The login interface is as shown below
 How to use Baidu Netdisk app
Mar 27, 2024 pm 06:46 PM
How to use Baidu Netdisk app
Mar 27, 2024 pm 06:46 PM
Cloud storage has become an indispensable part of our daily life and work nowadays. As one of the leading cloud storage services in China, Baidu Netdisk has won the favor of a large number of users with its powerful storage functions, efficient transmission speed and convenient operation experience. And whether you want to back up important files, share information, watch videos online, or listen to music, Baidu Cloud Disk can meet your needs. However, many users may not understand the specific use method of Baidu Netdisk app, so this tutorial will introduce in detail how to use Baidu Netdisk app. Users who are still confused can follow this article to learn more. ! How to use Baidu Cloud Network Disk: 1. Installation First, when downloading and installing Baidu Cloud software, please select the custom installation option.
 Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Windows operating system is one of the most popular operating systems in the world, and its new version Win11 has attracted much attention. In the Win11 system, obtaining administrator rights is an important operation. Administrator rights allow users to perform more operations and settings on the system. This article will introduce in detail how to obtain administrator permissions in Win11 system and how to effectively manage permissions. In the Win11 system, administrator rights are divided into two types: local administrator and domain administrator. A local administrator has full administrative rights to the local computer
 How to use Thunder to download magnet links
Feb 25, 2024 pm 12:51 PM
How to use Thunder to download magnet links
Feb 25, 2024 pm 12:51 PM
With the rapid development of network technology, our lives have also been greatly facilitated, one of which is the ability to download and share various resources through the network. In the process of downloading resources, magnet links have become a very common and convenient download method. So, how to use Thunder magnet links? Below, I will give you a detailed introduction. Xunlei is a very popular download tool that supports a variety of download methods, including magnet links. A magnet link can be understood as a download address through which we can obtain relevant information about resources.
 Teach you how to use the new advanced features of iOS 17.4 'Stolen Device Protection'
Mar 10, 2024 pm 04:34 PM
Teach you how to use the new advanced features of iOS 17.4 'Stolen Device Protection'
Mar 10, 2024 pm 04:34 PM
Apple rolled out the iOS 17.4 update on Tuesday, bringing a slew of new features and fixes to iPhones. The update includes new emojis, and EU users will also be able to download them from other app stores. In addition, the update also strengthens the control of iPhone security and introduces more "Stolen Device Protection" setting options to provide users with more choices and protection. "iOS17.3 introduces the "Stolen Device Protection" function for the first time, adding extra security to users' sensitive information. When the user is away from home and other familiar places, this function requires the user to enter biometric information for the first time, and after one hour You must enter information again to access and change certain data, such as changing your Apple ID password or turning off stolen device protection.




