Harnessing the power of lists: Building with the Twitter API
What is a Twitter list?
Twitter Lists allow you to group individual Twitter users and view their tweets individually from your timeline. For example, you could have a list of only your favorite Twitter friends. It helps isolate the signal from the noise and focus on the person you want to pay closer attention to. But lists have countless other uses. You can also share your list publicly or subscribe to other people's lists.
One of the ways to make better use of lists is through the Twitter List API, which gives you complete control over things where the user interface is still cumbersome.
In this two-part tutorial, we'll review useful and innovative uses of lists within the broader Twitter API family. In the next tutorial, we'll dive into coding using the List API to take fuller advantage of these features.
List: An Overlooked Feature
Twitter first launched lists in 2009, but they never became a high priority for the company. In fact, judging by the way they've managed the user interface over the past few years, you might wonder if they want to ditch that feature. Lists remains Twitter's pathetic stepchild - out of sync with their efforts to simplify the interface and make their social network more accessible to the public. Accessing lists through mobile and desktop user interfaces is often difficult and cumbersome.
The fact is that Twitter lists are very useful and powerful, but this functionality is not easily accessible through the Twitter interface. For example, lists are more accessible in third-party apps like TweetDeck than in Twitter's own app:
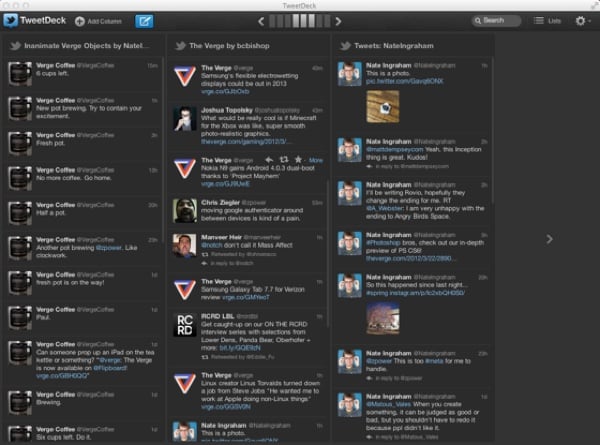
One of my pet peeves is that Twitter makes it very difficult to add people to lists. There is no bulk account import. You must visit each account page and add them individually:
This is one of the biggest drawbacks to planning and using lists.
Methods of using lists
There are many ways to use Twitter lists. I've listed some of my favorites below. Please share your suggestions with other readers in the comments.
- Favorites: Follow favorite accounts or close friends so you can easily see all of their tweets without them getting lost in the endless noise of Twitter.
- Topics Follow a list of experts, colleagues, or authors so you can see all their tweets above the noise, such as technology, productivity, or food.
- Customers: Focusing on your customers and their brand helps you stay in sync with your staff.
- Employees: Build a list of employees for your company, news site, or blog contributors to make it easier for Twitter users to engage more deeply with your team.
- Events & Conferences: Create a list of people participating in events for a specific hashtag, such as #ferguson or #WDS2014 (World Domination Summit 2014).
-
Local: Follow accounts that are local to your geographic area, such as your neighborhood or city.
- Community: Build a list of people who are affiliated with a group, such as your book club or membership organization.
- Functionality:Follow company accounts that post job openings to help you with your career search, or follow accounts for products and apps you own to keep track of updates.
- Government: Follow public officials, such as your city's council slate or elected officials.
- Curation: Build and curate a popular list to grow your followers and increase your visibility as a Twitter moderator. As you build a subscriber base for your curated list, people will seek you out to interact with you, and your account will get more exposure overall.
- Build a Follower: See who has added you to their lists and what topics they consider you an expert on. Follow these curators and interact with them more.
- Build influence: If you browse the Lists of popular peers in your industry > Members page, you can find a popular curated list of founders whose founders you may want to interact with.
- Public Relations: Build a list of Twitter users who have mentioned or interacted with your brand account.
It’s also helpful to know how some well-known Twitter users use lists. Here's Netscape founder and technology investor Marc Andreesen:
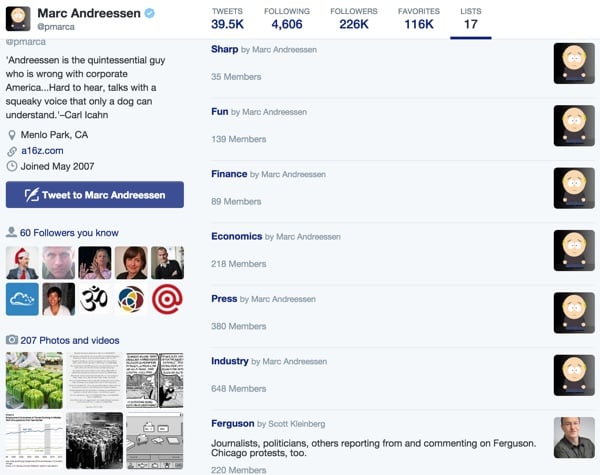
Note how he keeps small lists of sharp and interesting people, as well as topic lists of finance, economics, and news. He also subscribes to other people's lists, such as Scott Kleinberg's Ferguson list.
The following is a list from media guru Brian Stelter:
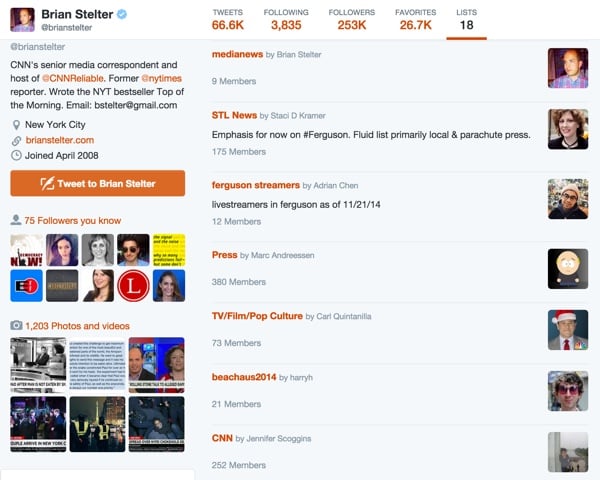
In most cases, he prefers to subscribe to lists curated by others - and who can blame him, given how difficult this curation UI is?
It's useful to see the lists people have added you to. It can help you understand what topics people think you are an expert on and identify curators who might be worthy of following and engaging with more content.
Here is a summary of the lists I have added as members:
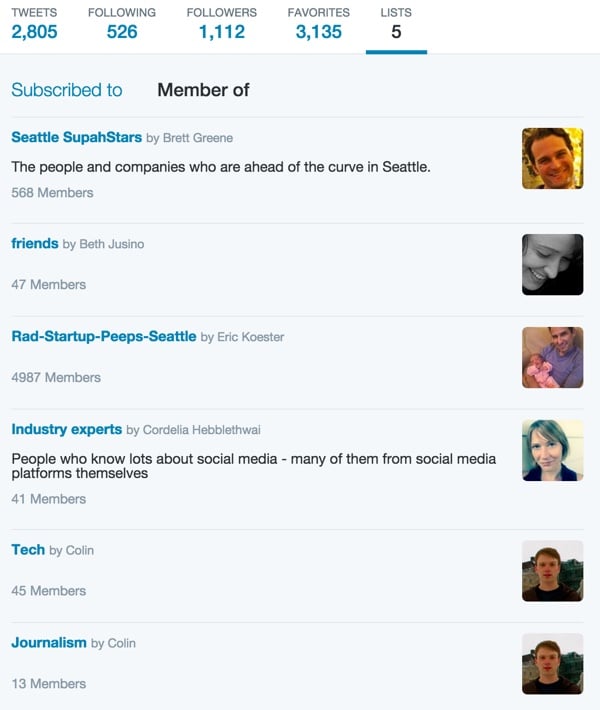
For example, Eric Koester puts a lot of effort into curating his Rad startup list. He probably deserves more attention and engagement.
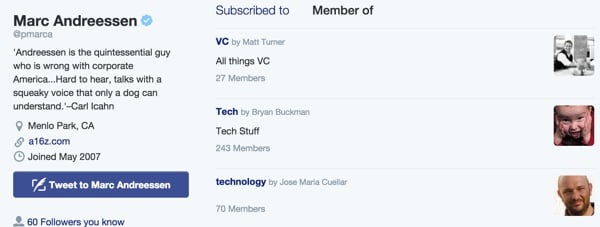
If I wanted to set up my Twitter profile like Marc Andreesen (you can follow me on Twitter now, by the way), I could look at his listings page and look for popular listings that include him as an expert. I can then identify these curators as people I might engage with on Twitter.
Twitter List API Overview
The Twitter list has approximately 19 APIs, divided into three main areas:
- List Management (CRUD)
- List members
- List Subscribers
Lists allow you to programmatically accomplish tasks that would be difficult to accomplish manually or through the Twitter user interface.
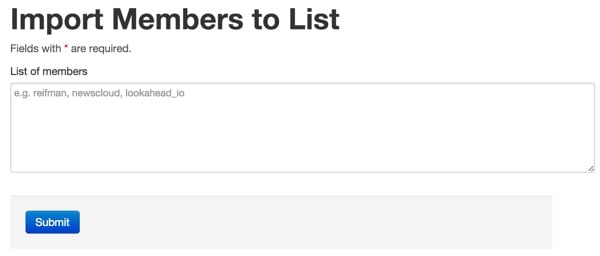
Import members into the list
For example, you can add a comma-separated list of Twitter accounts to a list, which is very time-consuming to do through the Twitter user interface.
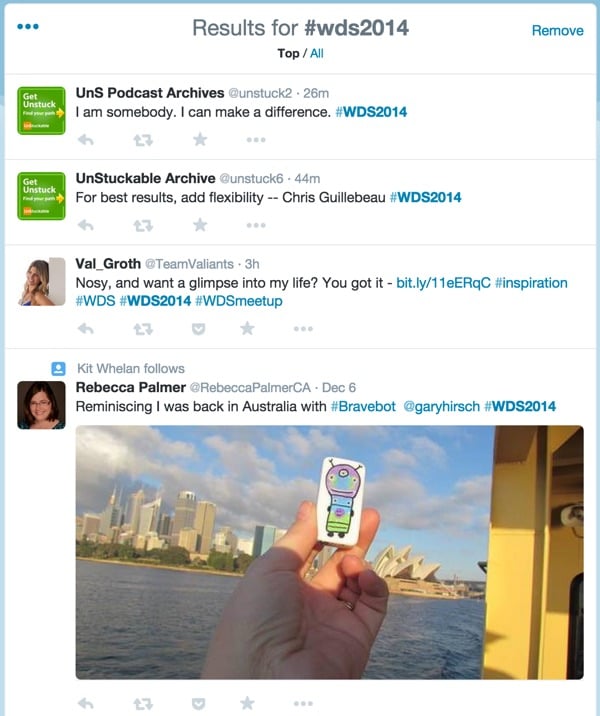
Convert saved searches to Twitter lists
Or you can convert saved searches in Twitter into curated lists. For example, I can programmatically browse tweets from a saved search for a conference such as World Domination Summit 2014 (hashtag: #WDS2014) and select individual Twitter accounts to add to the list for WDS2014.
public relationship
Similarly, you can programmatically build a private list of Twitter accounts that negatively mention your corporate brand account or business.
Create a local Twitter user list
Twitter does not easily expose its local searches through the user interface. However, I can use the API geosearch feature to find tweets close to a GPS location. The result looks like this:
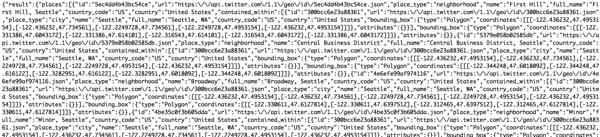
Through the API, we can filter these results to identify Twitter users who are tweeting near my GPS location. If they repeat frequently, we can identify possible nearby residents. We can then programmatically add them to a Twitter list representing Twitter users around my GPS location.
Email summary of list
Since it's not easy to check a Twitter list in the Twitter app, we can send a daily email summary of the list's tweets. Alternatively, we could provide a filtered summary that only contains the most popular tweets or tweets from users with higher Klout rankings.
These are some ideas we will explore through code in the next tutorial. Again, please post your suggestions and favorite API scenarios in the comments. I'd love to hear their voices.
What’s next?
Now you know a little bit about how people use Twitter lists and some of their user interface limitations. You also learned some ideas for getting the most out of the Twitter List API. In the next tutorial, we'll walk through building list functionality into the Twitter API.
If you have any questions or suggestions, please ask them in the comments. If you'd like to continue following my future Tuts tutorials and other series, please visit my instructor page or follow @reifman.
Related Links
- Twitter API for lists
- 10 Ways to Use Twitter Mashables
The above is the detailed content of Harnessing the power of lists: Building with the Twitter API. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP...
 Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
JWT is an open standard based on JSON, used to securely transmit information between parties, mainly for identity authentication and information exchange. 1. JWT consists of three parts: Header, Payload and Signature. 2. The working principle of JWT includes three steps: generating JWT, verifying JWT and parsing Payload. 3. When using JWT for authentication in PHP, JWT can be generated and verified, and user role and permission information can be included in advanced usage. 4. Common errors include signature verification failure, token expiration, and payload oversized. Debugging skills include using debugging tools and logging. 5. Performance optimization and best practices include using appropriate signature algorithms, setting validity periods reasonably,
 How does session hijacking work and how can you mitigate it in PHP?
Apr 06, 2025 am 12:02 AM
How does session hijacking work and how can you mitigate it in PHP?
Apr 06, 2025 am 12:02 AM
Session hijacking can be achieved through the following steps: 1. Obtain the session ID, 2. Use the session ID, 3. Keep the session active. The methods to prevent session hijacking in PHP include: 1. Use the session_regenerate_id() function to regenerate the session ID, 2. Store session data through the database, 3. Ensure that all session data is transmitted through HTTPS.
 Describe the SOLID principles and how they apply to PHP development.
Apr 03, 2025 am 12:04 AM
Describe the SOLID principles and how they apply to PHP development.
Apr 03, 2025 am 12:04 AM
The application of SOLID principle in PHP development includes: 1. Single responsibility principle (SRP): Each class is responsible for only one function. 2. Open and close principle (OCP): Changes are achieved through extension rather than modification. 3. Lisch's Substitution Principle (LSP): Subclasses can replace base classes without affecting program accuracy. 4. Interface isolation principle (ISP): Use fine-grained interfaces to avoid dependencies and unused methods. 5. Dependency inversion principle (DIP): High and low-level modules rely on abstraction and are implemented through dependency injection.
 What are Enumerations (Enums) in PHP 8.1?
Apr 03, 2025 am 12:05 AM
What are Enumerations (Enums) in PHP 8.1?
Apr 03, 2025 am 12:05 AM
The enumeration function in PHP8.1 enhances the clarity and type safety of the code by defining named constants. 1) Enumerations can be integers, strings or objects, improving code readability and type safety. 2) Enumeration is based on class and supports object-oriented features such as traversal and reflection. 3) Enumeration can be used for comparison and assignment to ensure type safety. 4) Enumeration supports adding methods to implement complex logic. 5) Strict type checking and error handling can avoid common errors. 6) Enumeration reduces magic value and improves maintainability, but pay attention to performance optimization.
 How to debug CLI mode in PHPStorm?
Apr 01, 2025 pm 02:57 PM
How to debug CLI mode in PHPStorm?
Apr 01, 2025 pm 02:57 PM
How to debug CLI mode in PHPStorm? When developing with PHPStorm, sometimes we need to debug PHP in command line interface (CLI) mode...
 How to automatically set permissions of unixsocket after system restart?
Mar 31, 2025 pm 11:54 PM
How to automatically set permissions of unixsocket after system restart?
Mar 31, 2025 pm 11:54 PM
How to automatically set the permissions of unixsocket after the system restarts. Every time the system restarts, we need to execute the following command to modify the permissions of unixsocket: sudo...
 Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Static binding (static::) implements late static binding (LSB) in PHP, allowing calling classes to be referenced in static contexts rather than defining classes. 1) The parsing process is performed at runtime, 2) Look up the call class in the inheritance relationship, 3) It may bring performance overhead.






