How to perform code authorization and encryption protection?
In the current information age, there are a large number of software, programs and code files on the Internet. Many of them need to be protected to avoid piracy or malicious use. At the same time, some codes need to be authorized to obtain Economy Profit. So, the question arises: How to perform code authorization and encryption protection?
1. Code Authorization
Code authorization refers to granting the right to use, modify, or publish software or program source code under certain conditions. At this time, the program developer, as the copyright holder, needs to clarify under what circumstances others are allowed to use the code, in what manner, and what restrictions the other party has. The following common code licensing methods are:
- Public domain licensing: that is, the program developer gives up all rights to the copyright of the program, allowing anyone to freely use, modify and distribute the program. The biggest advantage of this licensing method is that it is easy to obtain and use. The most famous public domain licensing agreement is the BSD agreement.
- MIT license: The MIT license is a very loose open source software license that allows others to use, distribute and modify the source code freely and without restriction. But there is a condition of the MIT license, which is to include a copyright statement and a license statement in the source code and documentation.
- GPL/RPL protocol authorization: GPL/RPL protocol is also a frequently used authorization method. It requires anyone to use, modify, and distribute source code or derivative works to open source code, and the code used must also follow the same authorization method, thus ensuring the freedom and openness of software code.
- Commercial license: Commercial license requires payment, but also allows the licensor to restrict the use, modification, and distribution of software users. This authorization method can guarantee the economic rights and interests of program developers.
2. Code encryption protection
In fact, authorization is only the first step in source code protection, and code encryption protection is the real means to prevent source code leakage and theft. Code encryption methods can generally be divided into the following categories:
- Algorithmic encryption: Algorithmic encryption uses mathematical calculations to encrypt codes, and is generally used to encrypt information or protect important algorithms. For ordinary software programs, algorithmic encryption is not commonly used because the threshold for decryption is very low. Once it is cracked, program security will be completely out of control.
- Difference analysis: Differential analysis compares the original file with the encrypted file, and cracks the original code by counting the differences between the two files. The reliability of this method is not high and it is suitable for projects with low security requirements.
- Multi-layer encryption: Multi-layer encryption can encrypt the code multiple times. Generally, it is combined with other encryption methods to make decryption very difficult. This is an optimization of several previous encryption methods.
- Conditional compilation: Conditional compilation is a technology that compiles different versions of source code according to different conditions, and achieves code confusion in the process of generating different versions. The encryption of this method is relatively high, but the disadvantage is that it greatly increases the difficulty of maintenance.
It should be noted that the purpose of encryption is to ensure the security of the source code. In order to achieve this purpose, the encryption method cannot be absolutely safe. Once the encryption is cracked, all code security will be lost. Loss of guarantee, so we should standardize the design of the code structure while considering encryption, and adopt a high-cohesion, low-coupling design pattern to make the code highly robust and robust.
In general, code authorization and encryption protection are very important parts of the program development process. Authorization allows developers to better manage software copyrights, while encryption protection can protect the software to a certain extent. Security and Copyright. It is necessary to fully consider the design of the code structure during the development process, establish a robust and robust code structure, and adopt reasonable authorization methods and encryption methods to achieve the best code protection effect.
The above is the detailed content of How to perform code authorization and encryption protection?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
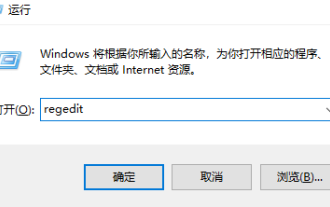 How to upgrade win10 enterprise version 2016 long-term service version to professional version
Jan 03, 2024 pm 11:26 PM
How to upgrade win10 enterprise version 2016 long-term service version to professional version
Jan 03, 2024 pm 11:26 PM
When we no longer want to continue using the current Win10 Enterprise Edition 2016 Long-Term Service Edition, we can choose to switch to the Professional Edition. The method is also very simple. We only need to change some contents and install the system image. How to change win10 enterprise version 2016 long-term service version to professional version 1. Press win+R, and then enter "regedit" 2. Paste the following path directly in the address bar above: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion3 , then find the EditionID and replace the content with "professional" to confirm
 Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Bitlocker is the default encryption technology for Windows operating systems. It is widely used on Windows, but some users prefer third-party solutions such as VeraCrypt. What many users of Bitlocker don't know is that it defaults to 128-bit encryption, even though 256-bit is available. Without going into too much detail about the differences; the core difference between AES 128-bit and 256-bit encryption is the length of the security key. Longer keys make brute force attacks more difficult. While the default is 128-bit, even Microsoft recommends 256-bit for better security. The problem is, most users probably don't know about the weaker defaults or how to change them. First, you might want to know W
 Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Microsoft previously provided dns encryption services for win11, but many users do not know how to use win11 encrypted dns. In fact, we only need to open the dns settings under network settings. Detailed tutorial on win11 encrypted dns: 1. First enter the disk and find the folder you want to encrypt. 2. Then open "Ethernet" on the right 3. Then find the DNS server allocation below and click "Edit" 4. After changing "Auto (DHCP)" to "Manual", open "IPv4" below 5. After turning it on, enter "8.8.8.8" in the preferred DNS 6. Then change the preferred DNS encryption to "Encryption only (DNS over HTTPS)" 7. After the changes are completed, click "Save" and you will find
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
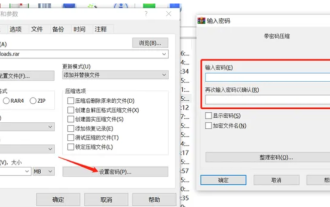 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
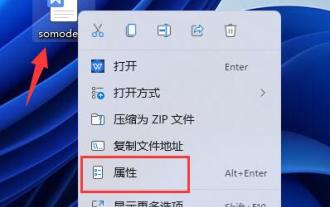 Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Some friends want to protect their files, but don’t know how to encrypt win11 documents. In fact, we can directly use folder encryption or use third-party software to encrypt files. Detailed tutorial on win11 document encryption: 1. First find the file you want to encrypt, right-click to select it, and open "Properties" 2. Then click "Advanced" in the properties column 3. Select "Encrypt content to protect data" in Advanced and click " OK" 4. Then click "OK" to save. 5. Finally, select the desired encryption mode and "OK" to save the document to encrypt the document.






