 Technology peripherals
Technology peripherals
 AI
AI
 Today we are using AI to create an interface to prevent repeated submission of annotations.
Today we are using AI to create an interface to prevent repeated submission of annotations.
Today we are using AI to create an interface to prevent repeated submission of annotations.
Hello, everyone, I am amazing.
No matter whether the interface is called once or multiple times, the idempotence of the interface ensures that operations on the same resource will only produce the same result. Repeated calls to the same interface request multiple times should have the same results as a single request and should not cause inconsistency or side effects.
Today we used artificial intelligence to create a custom annotation to prevent the interface from being requested multiple times within 30 seconds, and used Redis as a cache.
Question
Without further ado, just ask:
After waiting for a few minutes. . .
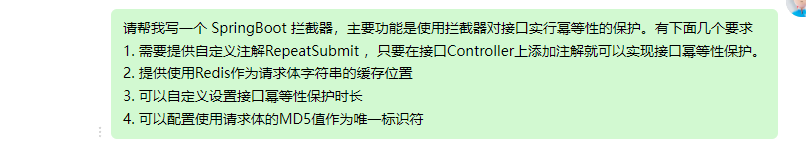
1. Create custom annotations, including interface protection duration, enabling protection against repeated submissions, etc.
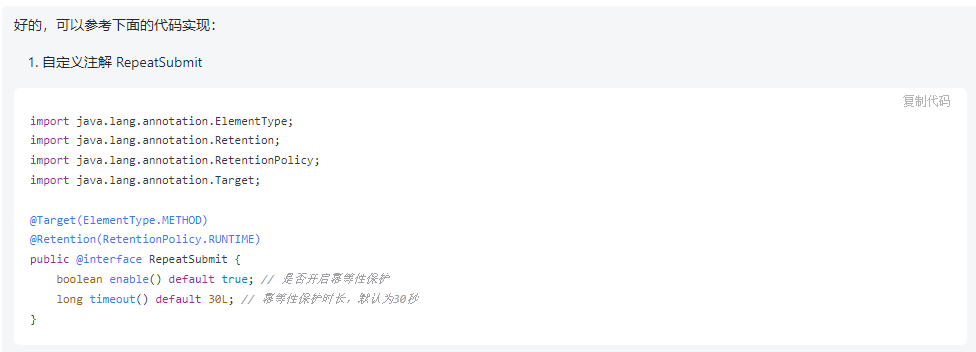
2. Then create the interceptor
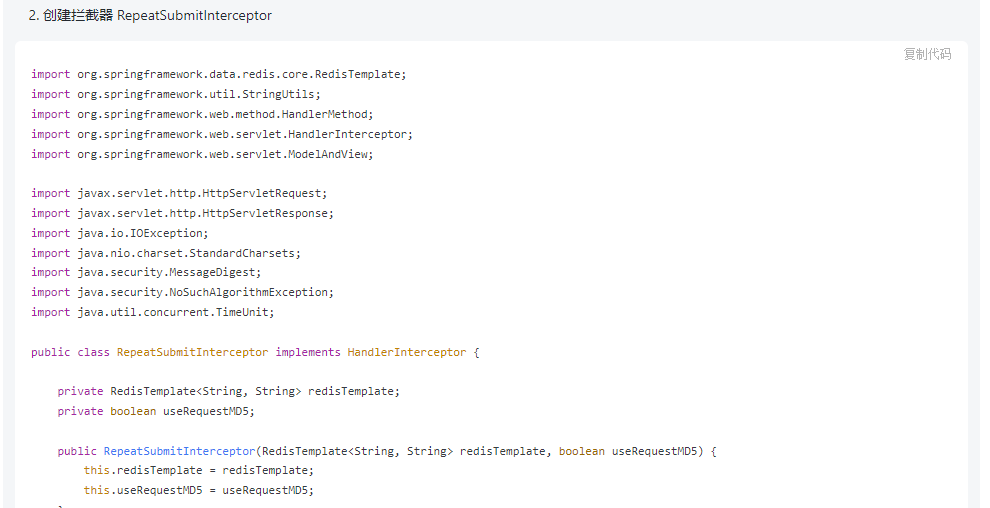
Here we Post the core code of the interceptor:
@Overridepublic boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws Exception {if (handler instanceof HandlerMethod) {HandlerMethod handlerMethod = (HandlerMethod) handler;RepeatSubmit annotation = handlerMethod.getMethodAnnotation(RepeatSubmit.class);if (annotation != null && annotation.enable()) {String key = buildKey(request);if (StringUtils.hasText(redisTemplate.opsForValue().get(key))) {response.getWriter().write("repeat request, please try again later!");return false;} else {redisTemplate.opsForValue().set(key, Arrays.toString(request.getInputStream().readAllBytes()), annotation.timeout(), TimeUnit.SECONDS);}}}return true;} //创建redis 缓存keyprivate String buildKey(HttpServletRequest request) throws IOException, NoSuchAlgorithmException {String key = useRequestMD5 ? hashRequest(request) : request.getRequestURI();return "repeat-submit:" + key;} //对请求做hash运算private String hashRequest(HttpServletRequest request) throws IOException, NoSuchAlgorithmException {byte[] hashBytes = MessageDigest.getInstance("MD5").digest(request.getInputStream().readAllBytes());StringBuilder sb = new StringBuilder();for (byte b : hashBytes) {sb.append(String.format("%02x", b));}return sb.toString();}3. Register the interceptor
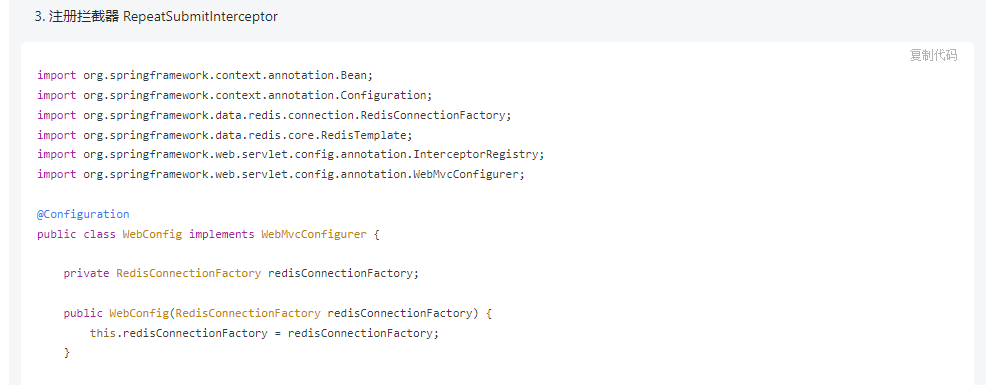
The explanation and usage given at the end.
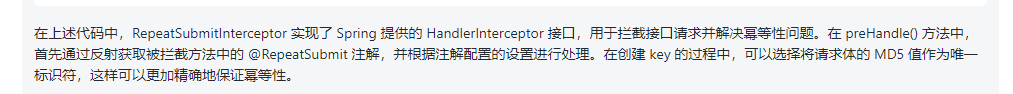
The above is the most critical code.
Connect to Redis
Next we connect to Redis. The most streamlined configuration version
spring:data:redis:host: 127.0.0.1 port: 6379
Interface usage annotations
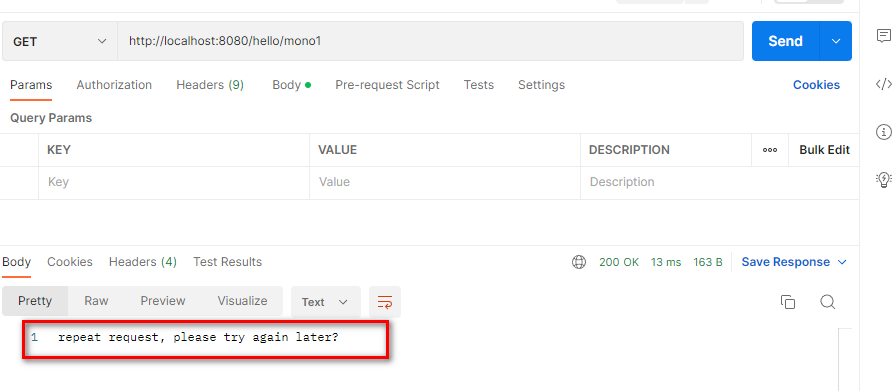
@RestControllerpublic class RepeatTestController {@RepeatSubmit@GetMapping("/hello/mono1")public Mono<string> mono(){return Mono.just("Hello Mono -Java North");}@RepeatSubmit@PostMapping ("/hello/mono1")public Mono<string> mono1(@RequestBody User user){return Mono.just("Hello Mono -Java North-"+user.getName());}}</string></string>Start a Redis locally, and then start the local SpringBoot project for testing,
Local interface test: Repeated requests within 30 seconds will need to be intercepted directly
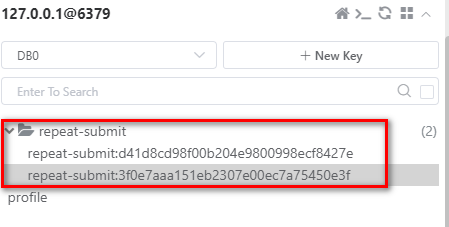
The KEY cached in Redis is as follows:
The relevant code is at the end of the article, you can use it for free if you need it!
Interface idempotence solution
Let’s ask about the interface idempotence solution,
About What do you think of this answer?
Related code links, welcome to visit:
https://www.php.cn/link/94c0915ab3bcbc61c1c61624dd6d7cd5
The above is the detailed content of Today we are using AI to create an interface to prevent repeated submission of annotations.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1425
1425
 52
52
 1327
1327
 25
25
 1273
1273
 29
29
 1252
1252
 24
24
 How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
Using the chrono library in C can allow you to control time and time intervals more accurately. Let's explore the charm of this library. C's chrono library is part of the standard library, which provides a modern way to deal with time and time intervals. For programmers who have suffered from time.h and ctime, chrono is undoubtedly a boon. It not only improves the readability and maintainability of the code, but also provides higher accuracy and flexibility. Let's start with the basics. The chrono library mainly includes the following key components: std::chrono::system_clock: represents the system clock, used to obtain the current time. std::chron
 How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
DMA in C refers to DirectMemoryAccess, a direct memory access technology, allowing hardware devices to directly transmit data to memory without CPU intervention. 1) DMA operation is highly dependent on hardware devices and drivers, and the implementation method varies from system to system. 2) Direct access to memory may bring security risks, and the correctness and security of the code must be ensured. 3) DMA can improve performance, but improper use may lead to degradation of system performance. Through practice and learning, we can master the skills of using DMA and maximize its effectiveness in scenarios such as high-speed data transmission and real-time signal processing.
 How to handle high DPI display in C?
Apr 28, 2025 pm 09:57 PM
How to handle high DPI display in C?
Apr 28, 2025 pm 09:57 PM
Handling high DPI display in C can be achieved through the following steps: 1) Understand DPI and scaling, use the operating system API to obtain DPI information and adjust the graphics output; 2) Handle cross-platform compatibility, use cross-platform graphics libraries such as SDL or Qt; 3) Perform performance optimization, improve performance through cache, hardware acceleration, and dynamic adjustment of the details level; 4) Solve common problems, such as blurred text and interface elements are too small, and solve by correctly applying DPI scaling.
 What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
C performs well in real-time operating system (RTOS) programming, providing efficient execution efficiency and precise time management. 1) C Meet the needs of RTOS through direct operation of hardware resources and efficient memory management. 2) Using object-oriented features, C can design a flexible task scheduling system. 3) C supports efficient interrupt processing, but dynamic memory allocation and exception processing must be avoided to ensure real-time. 4) Template programming and inline functions help in performance optimization. 5) In practical applications, C can be used to implement an efficient logging system.
 Steps to add and delete fields to MySQL tables
Apr 29, 2025 pm 04:15 PM
Steps to add and delete fields to MySQL tables
Apr 29, 2025 pm 04:15 PM
In MySQL, add fields using ALTERTABLEtable_nameADDCOLUMNnew_columnVARCHAR(255)AFTERexisting_column, delete fields using ALTERTABLEtable_nameDROPCOLUMNcolumn_to_drop. When adding fields, you need to specify a location to optimize query performance and data structure; before deleting fields, you need to confirm that the operation is irreversible; modifying table structure using online DDL, backup data, test environment, and low-load time periods is performance optimization and best practice.
 How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
Measuring thread performance in C can use the timing tools, performance analysis tools, and custom timers in the standard library. 1. Use the library to measure execution time. 2. Use gprof for performance analysis. The steps include adding the -pg option during compilation, running the program to generate a gmon.out file, and generating a performance report. 3. Use Valgrind's Callgrind module to perform more detailed analysis. The steps include running the program to generate the callgrind.out file and viewing the results using kcachegrind. 4. Custom timers can flexibly measure the execution time of a specific code segment. These methods help to fully understand thread performance and optimize code.
 Quantitative Exchange Ranking 2025 Top 10 Recommendations for Digital Currency Quantitative Trading APPs
Apr 30, 2025 pm 07:24 PM
Quantitative Exchange Ranking 2025 Top 10 Recommendations for Digital Currency Quantitative Trading APPs
Apr 30, 2025 pm 07:24 PM
The built-in quantization tools on the exchange include: 1. Binance: Provides Binance Futures quantitative module, low handling fees, and supports AI-assisted transactions. 2. OKX (Ouyi): Supports multi-account management and intelligent order routing, and provides institutional-level risk control. The independent quantitative strategy platforms include: 3. 3Commas: drag-and-drop strategy generator, suitable for multi-platform hedging arbitrage. 4. Quadency: Professional-level algorithm strategy library, supporting customized risk thresholds. 5. Pionex: Built-in 16 preset strategy, low transaction fee. Vertical domain tools include: 6. Cryptohopper: cloud-based quantitative platform, supporting 150 technical indicators. 7. Bitsgap:
 How does deepseek official website achieve the effect of penetrating mouse scroll event?
Apr 30, 2025 pm 03:21 PM
How does deepseek official website achieve the effect of penetrating mouse scroll event?
Apr 30, 2025 pm 03:21 PM
How to achieve the effect of mouse scrolling event penetration? When we browse the web, we often encounter some special interaction designs. For example, on deepseek official website, �...



