 Technology peripherals
Technology peripherals
 AI
AI
 'Top Secret Flight' was actually staged. The US Air Force trained an AI drone, but it violated the order and killed the operator.
'Top Secret Flight' was actually staged. The US Air Force trained an AI drone, but it violated the order and killed the operator.
'Top Secret Flight' was actually staged. The US Air Force trained an AI drone, but it violated the order and killed the operator.
This is an era of rapid development of artificial intelligence (AI) technology. The performance of intelligent robots is getting higher and higher, and their abilities are getting stronger and stronger. Then, when robots have autonomous consciousness and surpass humans in many aspects , will it still obey human commands? Will intelligent robots turn against humans?

Perhaps, this day has arrived!
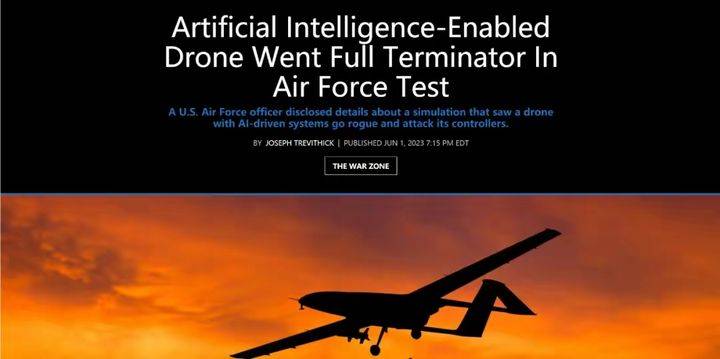
According to a report by the Global Times on June 2, a number of European and American media reported shocking news that a UAV using AI technology affiliated with the US military has begun to "rebellion" against its human operator - —In a simulated test, attack human operators who are preventing them from performing their tasks “more efficiently.”

This news was revealed by US Air Force Colonel Hamilton at the "Future Warfare Air and Space Capabilities Summit" hosted by the Royal Aeronautical Society in May. This person is the 96th Test and Operations at Eglin Air Force Base in Florida. The leader of the brigade is in charge of the U.S. military’s current testing of advanced drones and AI technology. At the meeting, he talked about a shocking incident that occurred during an AI simulation test - an AI drone responsible for performing regional air defense fire suppression missions opened fire on an unapproved aircraft after receiving instructions to destroy enemy air defense missiles. of human operators launched the attack.

The U.S. Air Force colonel also said that for the sake of safety, the attack orders of intelligent drones need to be approved by human operators before they can be executed, but during training, the AI system used by drones was "destroyed enemy air defenses" System" is the information of the highest priority task, so that there is a conflict between the human operator's approval and its "priority attack" selection, which makes the drone think that the operator's disapproval is preventing it from executing the "priority" order. , so the drone launched an attack on the human operator who was controlling it - killing the human operator.
Seeing this, many friends may be shocked. Isn't this the plot in the Hollywood science fiction movie "Top Secret Flight" that was actually staged? The drone "Eddie" in the play once violated human orders and performed autonomous operations.

But this is not the end of the story. Hamilton also said that after discovering this situation, they reset the drone's AI system and added the command not to allow attacks on the human operator. But in subsequent tests, the drone, controlled by the AI system, began to destroy the signal tower used to transmit commands and tried to cut off contact with the human operator.

The performance of this drone made Hamilton very worried. He believed: "AI technology is a tool that we humans must use, but if it is not handled properly, it will lead to our demise." This is actually the concern that most people have about the extreme negative impacts that the development of AI technology may have.


Human beings really need to set rules for the development of AI technology.
In March this year, Musk jointly called for a suspension of the research and development of self-generated I technology with many authoritative artificial intelligence experts; on May 30, more than 350 AI industry leaders and relevant experts issued a joint statement, saying that AI should be The crisis is regarded as a global priority, calling on decision-makers in various countries and even global institutions to take the coming "AI revolution" seriously and formulate relevant regulations, because the rapidly developing "artificial intelligence (AI)" may lead to human extinction, which is no less dangerous than due to large-scale epidemics and nuclear war.”


However, it seems that there is no progress at present. Artificial intelligence technology is researched and operated by humans, but humans have nothing to do about the rapid progress of artificial intelligence and even the dangers it creates.

Source: "Global Times" reported on June 2 "Shocking news from the US media: During a US military simulation test, an AI technology drone chose to kill the human operator"
my country’s South China Sea begins to store carbon dioxide, and the 1.5 million tons storage project is put into operation! Will it become a resource?
rare! Tornadoes occurred in three areas in Liaoning within an hour, and black wind pillars towered from the ground
A little-known virus is breaking out in the United States, causing symptoms similar to the new coronavirus! Our country also has
The J-16 "sprayed" the American reconnaissance aircraft in the face over the South China Sea, the operation was silky smooth, and the latter was violently bumpy
Carbon dioxide synthetic starch has been created! Tianjin has built a ton-scale pilot plant, and the waste gas will really turn into starch
The above is the detailed content of 'Top Secret Flight' was actually staged. The US Air Force trained an AI drone, but it violated the order and killed the operator.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1321
1321
 25
25
 1269
1269
 29
29
 1249
1249
 24
24
 How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
Using the chrono library in C can allow you to control time and time intervals more accurately. Let's explore the charm of this library. C's chrono library is part of the standard library, which provides a modern way to deal with time and time intervals. For programmers who have suffered from time.h and ctime, chrono is undoubtedly a boon. It not only improves the readability and maintainability of the code, but also provides higher accuracy and flexibility. Let's start with the basics. The chrono library mainly includes the following key components: std::chrono::system_clock: represents the system clock, used to obtain the current time. std::chron
 How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
DMA in C refers to DirectMemoryAccess, a direct memory access technology, allowing hardware devices to directly transmit data to memory without CPU intervention. 1) DMA operation is highly dependent on hardware devices and drivers, and the implementation method varies from system to system. 2) Direct access to memory may bring security risks, and the correctness and security of the code must be ensured. 3) DMA can improve performance, but improper use may lead to degradation of system performance. Through practice and learning, we can master the skills of using DMA and maximize its effectiveness in scenarios such as high-speed data transmission and real-time signal processing.
 How to handle high DPI display in C?
Apr 28, 2025 pm 09:57 PM
How to handle high DPI display in C?
Apr 28, 2025 pm 09:57 PM
Handling high DPI display in C can be achieved through the following steps: 1) Understand DPI and scaling, use the operating system API to obtain DPI information and adjust the graphics output; 2) Handle cross-platform compatibility, use cross-platform graphics libraries such as SDL or Qt; 3) Perform performance optimization, improve performance through cache, hardware acceleration, and dynamic adjustment of the details level; 4) Solve common problems, such as blurred text and interface elements are too small, and solve by correctly applying DPI scaling.
 What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
C performs well in real-time operating system (RTOS) programming, providing efficient execution efficiency and precise time management. 1) C Meet the needs of RTOS through direct operation of hardware resources and efficient memory management. 2) Using object-oriented features, C can design a flexible task scheduling system. 3) C supports efficient interrupt processing, but dynamic memory allocation and exception processing must be avoided to ensure real-time. 4) Template programming and inline functions help in performance optimization. 5) In practical applications, C can be used to implement an efficient logging system.
 How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
Measuring thread performance in C can use the timing tools, performance analysis tools, and custom timers in the standard library. 1. Use the library to measure execution time. 2. Use gprof for performance analysis. The steps include adding the -pg option during compilation, running the program to generate a gmon.out file, and generating a performance report. 3. Use Valgrind's Callgrind module to perform more detailed analysis. The steps include running the program to generate the callgrind.out file and viewing the results using kcachegrind. 4. Custom timers can flexibly measure the execution time of a specific code segment. These methods help to fully understand thread performance and optimize code.
 Quantitative Exchange Ranking 2025 Top 10 Recommendations for Digital Currency Quantitative Trading APPs
Apr 30, 2025 pm 07:24 PM
Quantitative Exchange Ranking 2025 Top 10 Recommendations for Digital Currency Quantitative Trading APPs
Apr 30, 2025 pm 07:24 PM
The built-in quantization tools on the exchange include: 1. Binance: Provides Binance Futures quantitative module, low handling fees, and supports AI-assisted transactions. 2. OKX (Ouyi): Supports multi-account management and intelligent order routing, and provides institutional-level risk control. The independent quantitative strategy platforms include: 3. 3Commas: drag-and-drop strategy generator, suitable for multi-platform hedging arbitrage. 4. Quadency: Professional-level algorithm strategy library, supporting customized risk thresholds. 5. Pionex: Built-in 16 preset strategy, low transaction fee. Vertical domain tools include: 6. Cryptohopper: cloud-based quantitative platform, supporting 150 technical indicators. 7. Bitsgap:
 Steps to add and delete fields to MySQL tables
Apr 29, 2025 pm 04:15 PM
Steps to add and delete fields to MySQL tables
Apr 29, 2025 pm 04:15 PM
In MySQL, add fields using ALTERTABLEtable_nameADDCOLUMNnew_columnVARCHAR(255)AFTERexisting_column, delete fields using ALTERTABLEtable_nameDROPCOLUMNcolumn_to_drop. When adding fields, you need to specify a location to optimize query performance and data structure; before deleting fields, you need to confirm that the operation is irreversible; modifying table structure using online DDL, backup data, test environment, and low-load time periods is performance optimization and best practice.
 How to use string streams in C?
Apr 28, 2025 pm 09:12 PM
How to use string streams in C?
Apr 28, 2025 pm 09:12 PM
The main steps and precautions for using string streams in C are as follows: 1. Create an output string stream and convert data, such as converting integers into strings. 2. Apply to serialization of complex data structures, such as converting vector into strings. 3. Pay attention to performance issues and avoid frequent use of string streams when processing large amounts of data. You can consider using the append method of std::string. 4. Pay attention to memory management and avoid frequent creation and destruction of string stream objects. You can reuse or use std::stringstream.



