How to solve the simple dynamic string problem of SDS in Redis
1. The structure of SDS
C language does not have a string type, it is essentially a char[] array; and the size of the C language array must be initialized when it is created. It cannot be changed after the type is specified, and the last character array The element is always the null character '\0' .
The following shows a C string with the value "Redis":
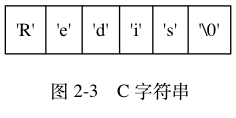
Redis does not directly use the string method of C language, but builds A type of simple dynamic string (SDS). The underlying strings in Redis are stored using the SDS structure. For example, the underlying key-value pairs containing strings are all implemented using the SDS structure.
The SDS structure is defined in sds.h
struct sdshdr{
int len;//SDS保存的字符串长度
int free;//buf数组中未使用字节数量
char buf[];//字符数组,保存字符串
}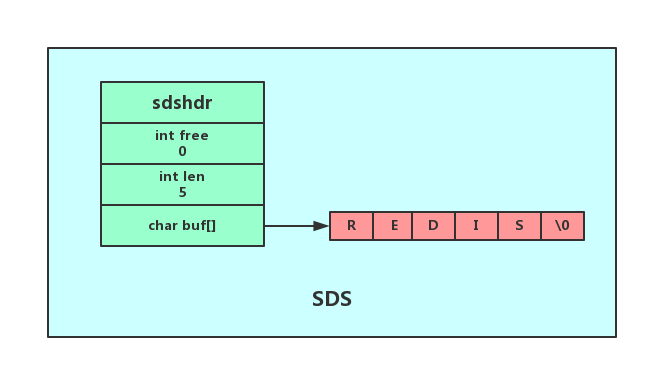
The last byte saves the null character '\0', retaining the specification of the C string , so that the SDS structured string can reuse some functions of the C function library.
2. Why not use C string
Mainly because C string has the following shortcomings:
The time complexity of obtaining the string length is O(N): C To obtain the length of a string, you need to traverse the entire string until you encounter the '\0' null character. A buffer overflow can occur if insufficient memory is allocated during a string append operation. Memory reallocation: Every time a string is grown or truncated, the program must perform a memory reallocation operation on the array that holds the C string. Memory reallocation involves complex algorithms and may require the execution of system calls, so it is usually relatively time-consuming. hour. Null character problem: Spaces cannot be stored in the middle of a C string, otherwise the program will mistakenly think it is the end of the string when traversing. Due to this limitation, C strings can only be used to store text data and are not suitable for saving binary data such as pictures, audio and video, and compressed files.
3. How to solve the C string problem

1. SDS records the SDS length through the len attribute, so the time complexity of obtaining the length is O( 1), that is, the time complexity of the strlen command is O(1).
2. The SDS space allocation strategy avoids buffer overflow: when SDS is modified, it will first check whether the SDS space meets the modification. If not, it will automatically expand to the required size before performing the modification.
3. Fewer memory reallocation times when modifying strings: free in SDS records unused bytes in the buf byte array.
Redis implements two optimization strategies of space pre-allocation and lazy space release through the free attribute.
Space pre-allocation: When performing a growth operation on SDS, the program will not only allocate the space necessary for modification, but also allocate additional unused space for SDS. The number of memory reallocations is reduced when string growth operations are performed continuously, which is achieved through the pre-allocation strategy. Lazy space release: When the SDS is truncated, the program will not immediately reclaim the memory occupied by the extra bytes after shortening. Instead, it will use the free attribute to record the extra bytes for future use. The unused space may come in handy for future SDS growth, where the growth operation does not necessarily require memory reallocation.
The buf byte array in the SDS structure is binary safe and can not only save characters but also binary data.
SDS retains the convention of C strings, setting the end of the data to the null character '\0'. The reason why SDS retains this specification is that it can reuse some functions of the C string function library, such as append String.
4. Further optimization of strings
Three encodings of Redis string:
int stores 8-byte long integer (long, 2^63- 1) embstr, embstr format SDS (Simple Dynamic String) raw, raw format SDS, stores long strings greater than 44 bytes
int type refers to numbers, then raw and embstr both represent What are the similarities and differences between strings? Let’s analyze them below.
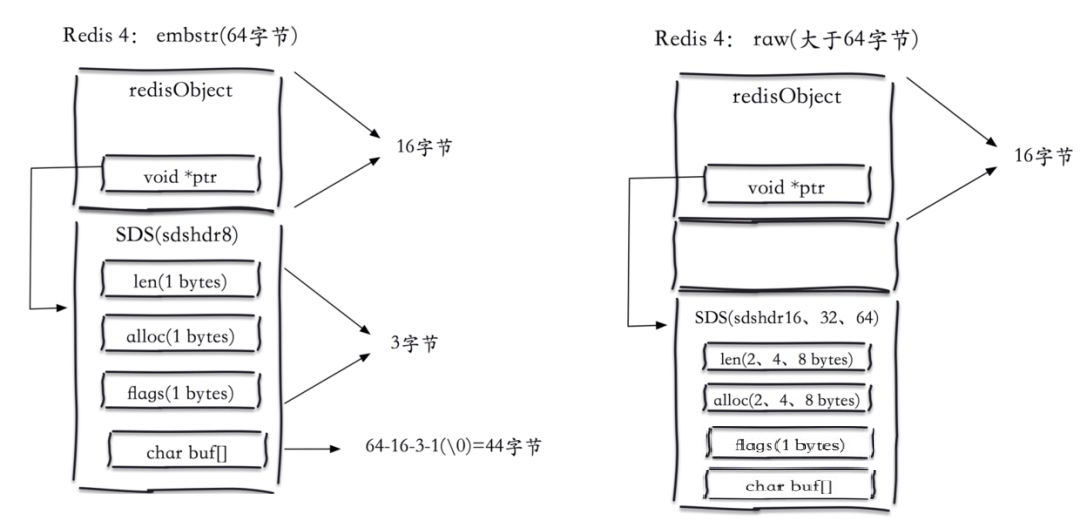
The picture shows the difference between the two. You can see that embstr saves redisObject and SDS in a continuous 64-byte space, so that only one memory allocation is required. For raw, the separation of SDS and redisObject requires two memory allocations and takes up more memory space.
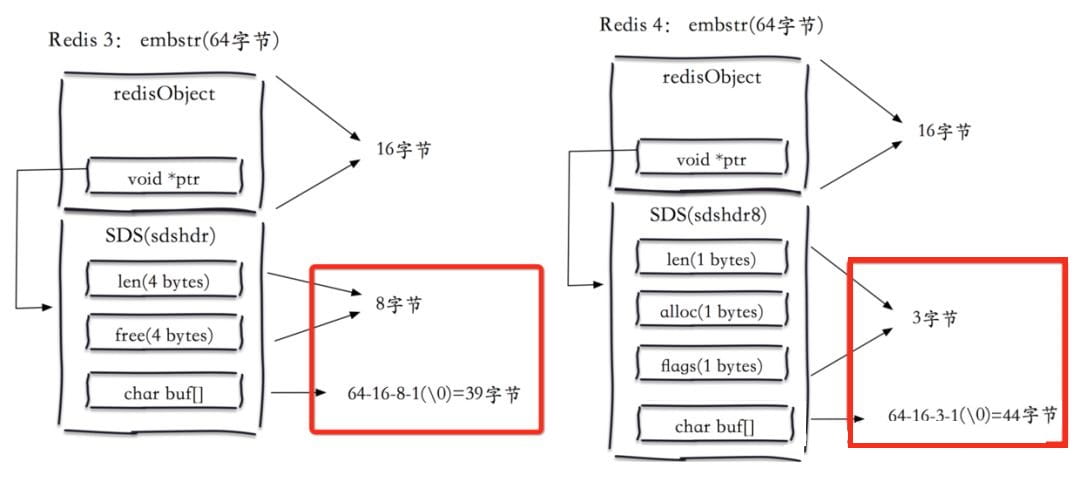
You can see that embstr uses a structure called sdshdr8 in 3.2. Under this structure, metadata only requires 3 bytes, while Redis requires 8 bytes. , so a total of 64 bytes, minus redisObject (16 bytes), and then minus the original information of SDS, the final actual content becomes 44 bytes and 39 bytes.
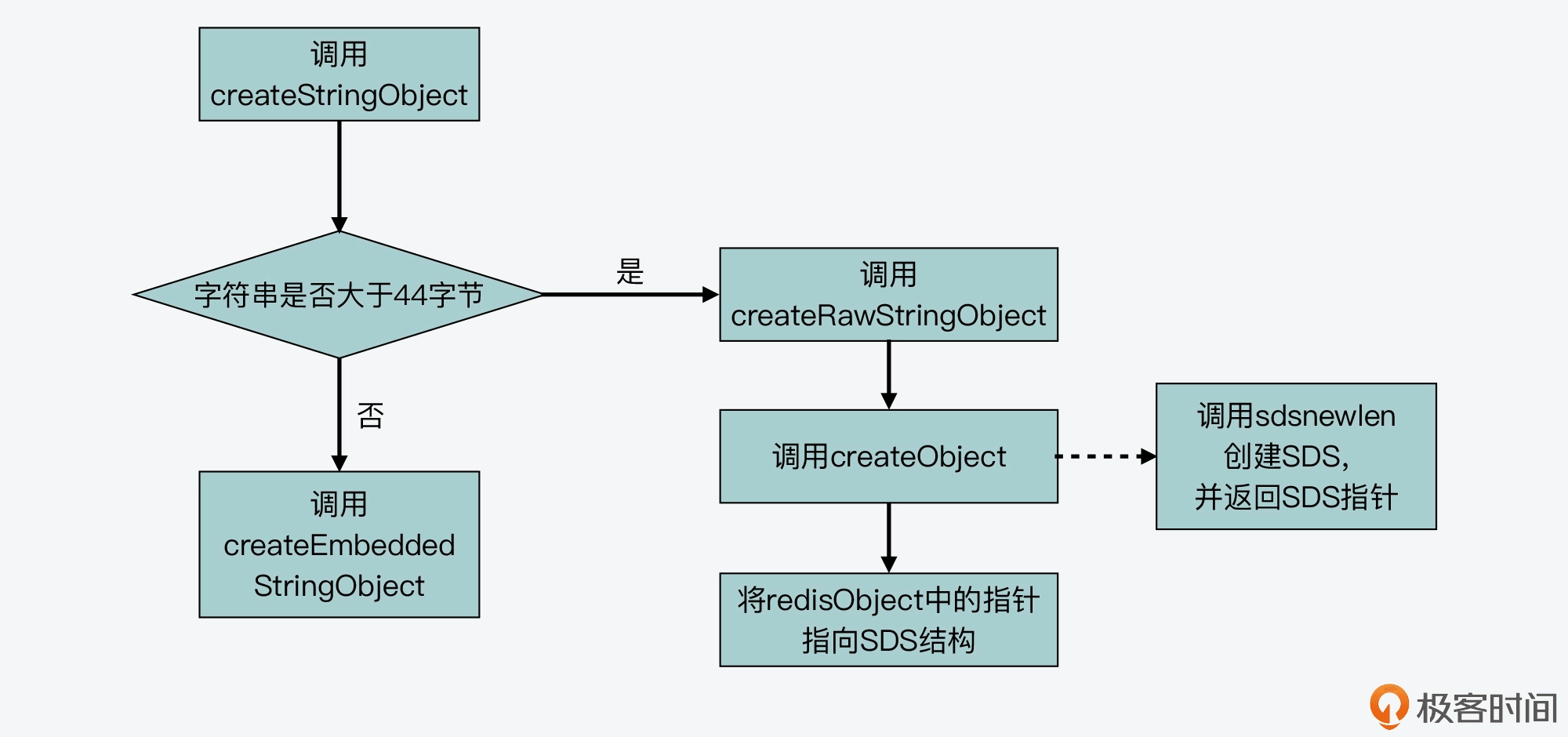
When the string is less than or equal to 44 bytes, Redis uses the embedded string creation method to reduce memory allocation and memory fragmentation.
The following picture shows the process of createEmbeddedStringObject creating an embedded string:
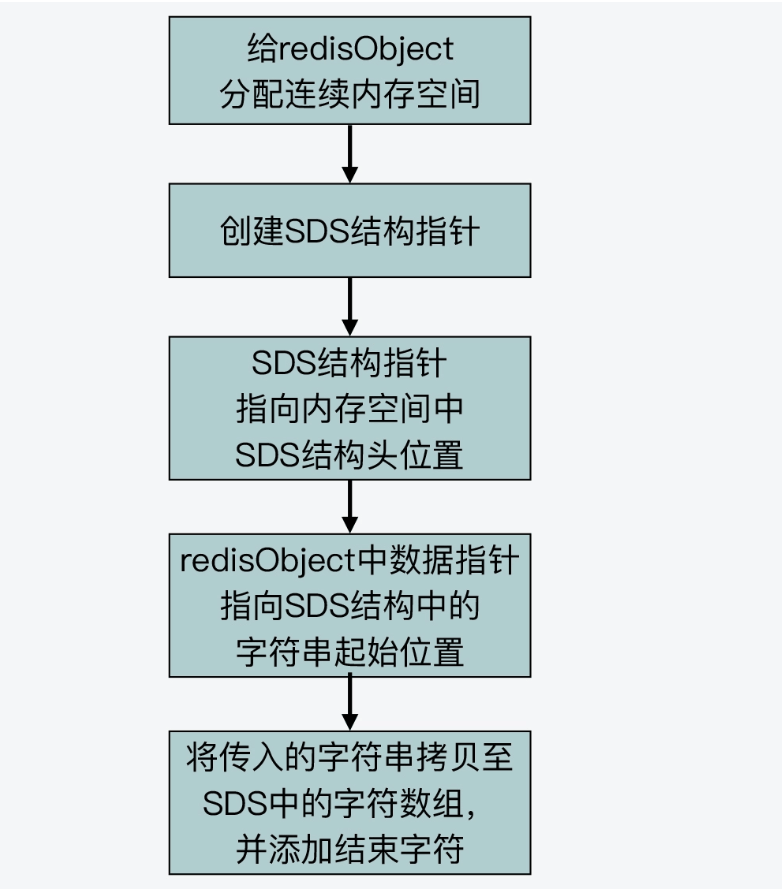
In short, just remember that Redis will realize a continuous piece of string by design. Memory space, compactly place the redisObject structure and SDS structure together.
In this way, for strings no longer than 44 bytes, memory fragmentation and the overhead of two memory allocations can be avoided.
SDS is an efficient string implementation in Redis. It has the advantages of automatic expansion, binary safety, O(1) length acquisition and modification, etc. In actual applications, SDS can help us achieve efficient string operations and also avoid some common string operation problems, such as buffer overflow. By in-depth understanding of the internal structure and implementation principles of SDS, we can better understand the underlying mechanism of Redis and further improve our Redis application capabilities.
The above is the detailed content of How to solve the simple dynamic string problem of SDS in Redis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1425
1425
 52
52
 1327
1327
 25
25
 1273
1273
 29
29
 1252
1252
 24
24
 How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
Redis cluster mode deploys Redis instances to multiple servers through sharding, improving scalability and availability. The construction steps are as follows: Create odd Redis instances with different ports; Create 3 sentinel instances, monitor Redis instances and failover; configure sentinel configuration files, add monitoring Redis instance information and failover settings; configure Redis instance configuration files, enable cluster mode and specify the cluster information file path; create nodes.conf file, containing information of each Redis instance; start the cluster, execute the create command to create a cluster and specify the number of replicas; log in to the cluster to execute the CLUSTER INFO command to verify the cluster status; make
 How to clear redis data
Apr 10, 2025 pm 10:06 PM
How to clear redis data
Apr 10, 2025 pm 10:06 PM
How to clear Redis data: Use the FLUSHALL command to clear all key values. Use the FLUSHDB command to clear the key value of the currently selected database. Use SELECT to switch databases, and then use FLUSHDB to clear multiple databases. Use the DEL command to delete a specific key. Use the redis-cli tool to clear the data.
 How to read redis queue
Apr 10, 2025 pm 10:12 PM
How to read redis queue
Apr 10, 2025 pm 10:12 PM
To read a queue from Redis, you need to get the queue name, read the elements using the LPOP command, and process the empty queue. The specific steps are as follows: Get the queue name: name it with the prefix of "queue:" such as "queue:my-queue". Use the LPOP command: Eject the element from the head of the queue and return its value, such as LPOP queue:my-queue. Processing empty queues: If the queue is empty, LPOP returns nil, and you can check whether the queue exists before reading the element.
 How to configure Lua script execution time in centos redis
Apr 14, 2025 pm 02:12 PM
How to configure Lua script execution time in centos redis
Apr 14, 2025 pm 02:12 PM
On CentOS systems, you can limit the execution time of Lua scripts by modifying Redis configuration files or using Redis commands to prevent malicious scripts from consuming too much resources. Method 1: Modify the Redis configuration file and locate the Redis configuration file: The Redis configuration file is usually located in /etc/redis/redis.conf. Edit configuration file: Open the configuration file using a text editor (such as vi or nano): sudovi/etc/redis/redis.conf Set the Lua script execution time limit: Add or modify the following lines in the configuration file to set the maximum execution time of the Lua script (unit: milliseconds)
 How to use the redis command line
Apr 10, 2025 pm 10:18 PM
How to use the redis command line
Apr 10, 2025 pm 10:18 PM
Use the Redis command line tool (redis-cli) to manage and operate Redis through the following steps: Connect to the server, specify the address and port. Send commands to the server using the command name and parameters. Use the HELP command to view help information for a specific command. Use the QUIT command to exit the command line tool.
 How to implement redis counter
Apr 10, 2025 pm 10:21 PM
How to implement redis counter
Apr 10, 2025 pm 10:21 PM
Redis counter is a mechanism that uses Redis key-value pair storage to implement counting operations, including the following steps: creating counter keys, increasing counts, decreasing counts, resetting counts, and obtaining counts. The advantages of Redis counters include fast speed, high concurrency, durability and simplicity and ease of use. It can be used in scenarios such as user access counting, real-time metric tracking, game scores and rankings, and order processing counting.
 How to set the redis expiration policy
Apr 10, 2025 pm 10:03 PM
How to set the redis expiration policy
Apr 10, 2025 pm 10:03 PM
There are two types of Redis data expiration strategies: periodic deletion: periodic scan to delete the expired key, which can be set through expired-time-cap-remove-count and expired-time-cap-remove-delay parameters. Lazy Deletion: Check for deletion expired keys only when keys are read or written. They can be set through lazyfree-lazy-eviction, lazyfree-lazy-expire, lazyfree-lazy-user-del parameters.
 How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
How to optimize the performance of debian readdir
Apr 13, 2025 am 08:48 AM
In Debian systems, readdir system calls are used to read directory contents. If its performance is not good, try the following optimization strategy: Simplify the number of directory files: Split large directories into multiple small directories as much as possible, reducing the number of items processed per readdir call. Enable directory content caching: build a cache mechanism, update the cache regularly or when directory content changes, and reduce frequent calls to readdir. Memory caches (such as Memcached or Redis) or local caches (such as files or databases) can be considered. Adopt efficient data structure: If you implement directory traversal by yourself, select more efficient data structures (such as hash tables instead of linear search) to store and access directory information




