How to briefly discuss the security issues of APP
1 Background Analysis
When the Internet era came, people once lamented that everything was being digitized. Today, everything is mobile. In the streets and alleys, people were busy swiping their screens with their heads down. Data from foreign authoritative organizations show that Chinese smartphones have accounted for 96% of total mobile phone sales, and traditional feature phones have basically faded out of the stage of history. According to a recent report by eMarketer, an American market research company, data from Gartner, an authoritative market research organization, shows that in China, smartphones account for 96% of mobile phone sales, while the United States also accounts for 96%. In other words, at the hardware level of mobile Internet, China and the United States are already on the same level.
The popularity of smart phones has promoted the rapid development of mobile apps. Currently, mobile apps can range from communication and chatting, takeout booking, ticket booking, travel booking, shopping, news browsing, etc. to banking investment and financial management. , hospital registration, payment transactions, etc. A person's daily activities can basically be completed by relying on mobile phones. Because of the massive popularity of apps, many software developers have seen the benefits brought by this market. Driven by profits, various apps emerge one after another, and the app market is also a mixed bag. Since the security of instant apps cannot be fully guaranteed, personal information leakage incidents have occurred very frequently through apps in recent years.
Through big data analysis, a statistical table of the commonly used apps on mobile phones is as follows:
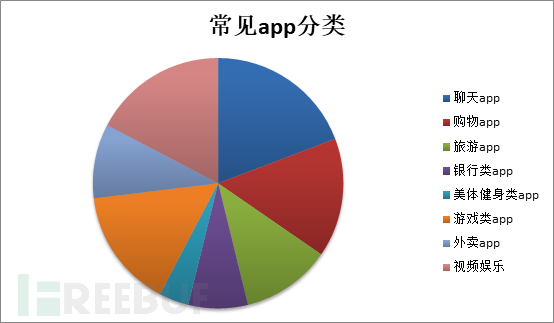
It is not difficult to see from the chart statistics that almost every Mobile phones are equipped with chat, video entertainment, shopping and other related apps. So how do these apps work on mobile phones? What information will be obtained from the mobile phone unknowingly?
2 Common security issues of mobile apps
With the development of technology, the functions of mobile phones are far more than these. The era of big data has arrived, and the era of smart home Internet of Things has also followed. , here we use Android app or apk for analysis. Download any apk and modify its suffix to tar to view some apk related files
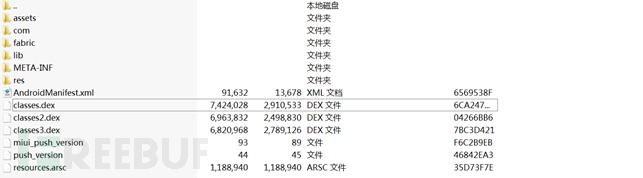
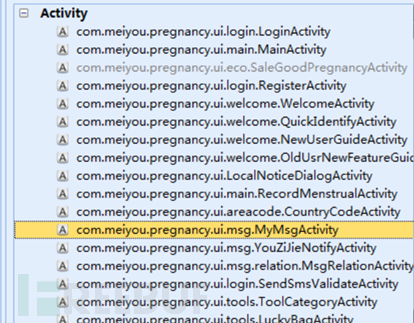
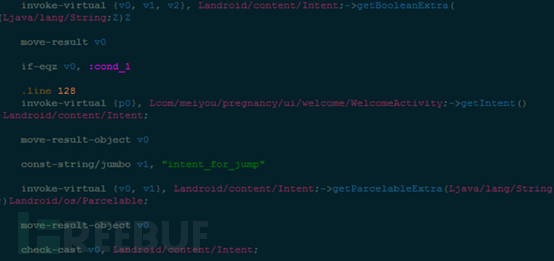
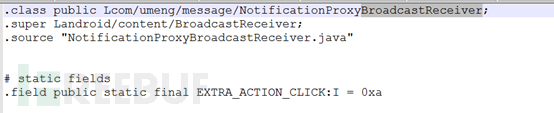
Service service is a background service. When using service service, it needs to be declared in AndroidManifest.xml. The apk for this test is declared as follows in AndroidManifest.xml,
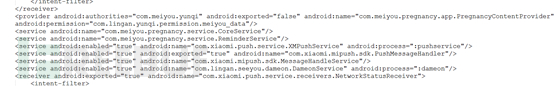
Service is independent of the activity component and performs some operations in the background. For example, when you need to obtain data from the server regularly, you need to use service at this time.
In addition to the security vulnerabilities in the four major components, various web vulnerabilities will also appear when calling the web interface, such as sql injection vulnerabilities, xss vulnerabilities, override, unauthorized and other related vulnerabilities. The screenshot is from an app http request data packet, and through testing it was found that the post data packet contains a vulnerability of unauthorized access. You can use a certain parameter to view other people's account information without authorization.
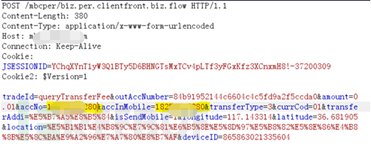
In short, there are many places where app vulnerabilities may appear, and there are many places worthy of our attention, such as whether the data is encrypted during transmission and whether the data is stored locally. Whether it is encrypted, whether it is safe to start the activity component by intent, etc.
3 Security Suggestions
With so many apps, as ordinary users, it is still impossible for users to perform security checks on the apps. So how should we prevent personal information from being leaked due to the apps?
l First of all, it is recommended to download the app through regular channels to prevent the downloaded app from being modified and compiled and not the original application;
l If there are no special requirements, it is not recommended to root the phone;
When installing an application, please pay attention to its required open permissions and turn off unnecessary permissions, such as location information, reading mobile phone contacts, etc.
l can be installed on your phone Appropriate anti-virus software, regularly scan and clean up useless software, program packages, etc.;
l Regularly upgrade relevant apps to fix bugs in old versions.
The above is the detailed content of How to briefly discuss the security issues of APP. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1421
1421
 52
52
 1315
1315
 25
25
 1266
1266
 29
29
 1239
1239
 24
24
 How to perform real-name authentication on Jingdong Mall APP
Mar 19, 2024 pm 02:31 PM
How to perform real-name authentication on Jingdong Mall APP
Mar 19, 2024 pm 02:31 PM
How to get real-name authentication on Jingdong Mall APP? Jingdong Mall is an online shopping platform that many friends often use. Before shopping, it is best for everyone to conduct real-name authentication so that they can enjoy complete services and get a better shopping experience. The following is the real-name authentication method for JD.com, I hope it will be helpful to netizens. 1. Install and open JD.com, and then log in to your personal account; 2. Then click [My] at the bottom of the page to enter the personal center page; 3. Then click the small [Settings] icon in the upper right corner to go to the setting function interface; 4. Select [Account and Security] to go to the account settings page; 5. Finally, click the [Real-name Authentication] option to fill in the real-name information; 6. The installation system requires you to fill in your real personal information and complete the real-name authentication
 How to decrypt app resources in cocos2d-LUA reverse engineering
May 16, 2023 pm 07:11 PM
How to decrypt app resources in cocos2d-LUA reverse engineering
May 16, 2023 pm 07:11 PM
Let's take the Dashen apk as an example. Through the previous analysis of the app decryption Lua script, we can decrypt the Lua script of the Dashen apk. Now let's decrypt its resources (configuration files and pictures, etc.). Let’s take a more important configuration file as an example. Before decryption: the file header also has a signature value: fuckyou!. Seeing this, we first thought about whether it was also encrypted with xxtea. We used the above method to decrypt it with xxtea first, and then decompressed it. We found that it was still garbled, and an error occurred during the operation. Obviously, we have to deny what we just said. conjecture. We continue to decrypt the configuration file step by step. Think about it for a moment, the file header is: fuckyou! If you want to decrypt files, you will inevitably need to process
 Microsoft improves Windows 11's Smart App Control, but you might not be able to use it
Apr 17, 2023 pm 04:40 PM
Microsoft improves Windows 11's Smart App Control, but you might not be able to use it
Apr 17, 2023 pm 04:40 PM
Microsoft launched SmartAppControl, a Windows 11 security feature, earlier this year. At the time, Microsoft described it as a protection tool that "blocks untrusted or potentially dangerous applications." What was unique about the tool at the time was that it determined whether it should run on a Windows 11 device. SmartAppControl initially runs in evaluation mode; it is in this mode that the application decides whether it should be opened. Microsoft did reveal that users can enable Smart App Control in the App and Browser Controls section of the Windows Security app. According only to Microsoft, SmartAppC
 How to view and delete App Store purchase history on iPhone
Apr 13, 2023 pm 06:31 PM
How to view and delete App Store purchase history on iPhone
Apr 13, 2023 pm 06:31 PM
The AppStore is a marketplace for iOS-related applications. Here you can also find free apps and paid apps. Apps can be gaming apps, productivity apps, utility apps, social media apps, and many more categories of apps. You may have downloaded or purchased many apps for iPhone from the AppStore. Now you may be wondering how to view the purchase history of apps purchased in the App Store. Sometimes, you may want to hide certain purchases from your purchase history for privacy reasons. In this article, we will guide you to find your purchase history and how to delete/hide purchases from your purchase history if necessary. Part 1
 Steps and precautions for registering a Hong Kong Apple ID (enjoy the unique advantages of the Hong Kong Apple Store)
Sep 02, 2024 pm 03:47 PM
Steps and precautions for registering a Hong Kong Apple ID (enjoy the unique advantages of the Hong Kong Apple Store)
Sep 02, 2024 pm 03:47 PM
Apple's products and services have always been loved by users around the world. Registering a Hong Kong Apple ID will bring more convenience and privileges to users. Let’s take a look at the steps to register a Hong Kong Apple ID and what you need to pay attention to. How to register a Hong Kong Apple ID When using Apple devices, many applications and functions require using Apple ID to log in. If you want to download applications from Hong Kong or enjoy the preferential content of the Hong Kong AppStore, it is very necessary to register a Hong Kong Apple ID. This article will detail the steps on how to register a Hong Kong Apple ID and what you need to pay attention to. Steps: Select language and region: Find the "Settings" option on your Apple device and enter
 How to cancel the data package on China Unicom app How to cancel the data package on China Unicom
Mar 18, 2024 pm 10:10 PM
How to cancel the data package on China Unicom app How to cancel the data package on China Unicom
Mar 18, 2024 pm 10:10 PM
The China Unicom app can easily meet everyone's needs. It has various functions to solve your needs. If you want to handle various services, you can easily do it here. If you don't need it, you can unsubscribe in time here. It is effective. To avoid subsequent losses, many people sometimes feel that the data is not enough when using mobile phones, so they buy additional data packages. However, they don’t want it next month and want to unsubscribe immediately. Here, the editor explains We provide a method to unsubscribe, so that friends who need it can come and use it! In the China Unicom app, find the "My" option in the lower right corner and click on it. In the My interface, slide the My Services column and click the "I have ordered" option
 What is the full name of the app?
Aug 21, 2023 am 10:29 AM
What is the full name of the app?
Aug 21, 2023 am 10:29 AM
The full name of app is "Application", which is the abbreviation of application program. It refers to a software application developed for mobile devices. The emergence of apps provides users with a wider variety of mobile application choices, meeting various user needs in different scenarios. The app development process involves many aspects such as software design, programming, and testing. It also needs to consider issues such as device compatibility, performance optimization, and security.
 How to use deep linking to backdoor Facebook APP
May 19, 2023 pm 02:49 PM
How to use deep linking to backdoor Facebook APP
May 19, 2023 pm 02:49 PM
Recently, the author discovered a deep link vulnerability in the Facebook Android APP. Using this vulnerability, the Facebook Android APP installed on the user's mobile phone can be converted into a backdoor program (Backdoor) to achieve backdooring. In addition, this vulnerability can also be used to repackage the Facebook APP and send it to specific target victims for installation and use. Let’s take a look at the author’s discovery process of this vulnerability, and how to construct it through Payload and finally transform it into a security risk in the actual production environment of Facebook APP. When I usually do public testing when discovering vulnerabilities, I will first carefully understand the application mechanism of the target system. In my last blog, I have shared how to parse Face




