How to monitor and optimize services in microservice architecture?
In recent years, with the continuous popularity of microservice architecture, more and more companies have begun to adopt microservice architecture to build their own information systems. The advantages of microservice architecture are obvious, including loose coupling, scalability, fault tolerance, etc.
However, there are also some challenges in the microservice architecture, one of which is how to monitor and optimize services. Because the interactions between services become very complex in this architecture, the failure of one service may have a chain reaction on other services. Therefore, each service must be monitored and optimized to ensure that the entire system can operate stably. This article will discuss how to monitor and optimize services in microservice architecture from two aspects: monitoring and optimization.
1. Monitoring
- Monitoring indicators
In the microservice architecture, each service is independent, so each service needs to be monitored monitor. Generally speaking, the running status of the service can be monitored through the following indicators:
(1) System load: CPU, memory, network traffic, disk space, etc.
(2) Response time: You can monitor the response time of HTTP requests, the response time of RPC requests, the response time of database queries, etc.
(3) Error rate: The error rate of the service can be monitored based on HTTP status codes, RPC error codes, exception stack information, etc.
(4) Transaction processing: If the service provides transaction processing function, you can monitor the transaction submission rate, rollback rate, etc.
(5) Logs: Logs in the service code are very important and can help developers understand the operation of the service, causes of failures, etc.
- Monitoring Tools
In order to monitor the service, you need to use some monitoring tools. Here are some commonly used tools:
(1) Prometheus: It is an open source monitoring system that can help users monitor the running status of various services. A very good feature of Prometheus is that it adopts the Pull method, that is, Prometheus actively sends requests to the service to obtain monitoring indicators.
(2) Grafana: It is a popular data visualization tool that can visually display the data collected by Prometheus. Grafana supports custom charts and panels, and has many predefined Dashboards to help users quickly understand the running status of the service.
(3) Zipkin: It is an open source distributed tracking system that can help users track the call chain between services. If there are frequent interactions between services, using Zipkin can help users understand the dependencies between services and quickly find problems.
2. Optimization
- Optimization goal
Monitoring the service is only the first step. Only if the service can be optimized based on the monitoring data can it truly be used. Advantages of microservice architecture. The goals of optimization usually include the following aspects:
(1) Improving performance: By optimizing the code of the service and using efficient algorithms, the processing speed of the service can be improved.
(2) Reduce costs: By optimizing the underlying architecture of the service and using a better technology stack, the cost of the service can be reduced.
(3) Improve availability: By optimizing the fault tolerance of the service and using load balancing, the availability of the service can be improved.
(4) Improve security: By optimizing the security mechanism of the service and preventing attacks, the security of the service can be improved.
- Optimization methods
There are many ways to optimize services. Here are a few of the more commonly used methods.
(1) Code optimization: By optimizing the service code, the performance of the service can be improved. For example, using concurrent programming, memory pools and other technologies can improve the processing speed of services.
(2) Caching: Caching is an effective means to improve service performance. Hotspot data can be cached and obtained directly from the cache on the next request. However, caching will also bring some problems, such as cache consistency, cache invalidation and other issues.
(3) Load balancing: Load balancing can solve the single point of failure problem and evenly distribute requests to multiple service instances. Load balancing can use hardware load balancers, software load balancers, DNS load balancing and other methods.
(4) Automatic expansion: Automatic expansion can automatically expand or shrink service instances according to the load of the service. If the load on a service increases, instances can be automatically added to share the load, and conversely instances can be scaled down to reduce costs.
(5) Failure degradation: In the case of high concurrency, the service may fail. To ensure the stability of the entire system, fault degradation can be used. For example, if a service fails, it can be temporarily shut down or a backup service used instead.
3. Summary
The advantages of microservice architecture are obvious, but it also requires us to invest more energy in monitoring and optimizing services. By monitoring the service, you can understand the operation of the service, discover and solve problems in a timely manner; by optimizing the service, you can improve the performance, availability, security and reduce costs of the service. Therefore, monitoring and optimization are indispensable links in the implementation of microservice architecture.
The above is the detailed content of How to monitor and optimize services in microservice architecture?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 C++ program optimization: time complexity reduction techniques
Jun 01, 2024 am 11:19 AM
C++ program optimization: time complexity reduction techniques
Jun 01, 2024 am 11:19 AM
Time complexity measures the execution time of an algorithm relative to the size of the input. Tips for reducing the time complexity of C++ programs include: choosing appropriate containers (such as vector, list) to optimize data storage and management. Utilize efficient algorithms such as quick sort to reduce computation time. Eliminate multiple operations to reduce double counting. Use conditional branches to avoid unnecessary calculations. Optimize linear search by using faster algorithms such as binary search.
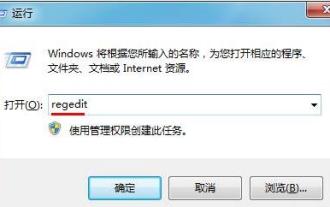 How to optimize the startup items of WIN7 system
Mar 26, 2024 pm 06:20 PM
How to optimize the startup items of WIN7 system
Mar 26, 2024 pm 06:20 PM
1. Press the key combination (win key + R) on the desktop to open the run window, then enter [regedit] and press Enter to confirm. 2. After opening the Registry Editor, we click to expand [HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorer], and then see if there is a Serialize item in the directory. If not, we can right-click Explorer, create a new item, and name it Serialize. 3. Then click Serialize, then right-click the blank space in the right pane, create a new DWORD (32) bit value, and name it Star
 Will Sunflower Remote Control be monitored? Will Sunflower Remote Control reveal privacy?
Mar 15, 2024 pm 05:28 PM
Will Sunflower Remote Control be monitored? Will Sunflower Remote Control reveal privacy?
Mar 15, 2024 pm 05:28 PM
Will Sunflower remote control be monitored? Sunflower remote control software can help users quickly retrieve information from another computer, etc. However, there are also many users who are worried about the security of their own computers. Let the editor answer these questions for users. Question. Will Sunflower Remote Control be monitored? Answer: No. Although Sunflower Remote Control has the ability to do this, large software companies like Sunflower Remote Control that have been established for many years will not do such a thing. For office workers, perhaps a piece of software that must be installed on the computer is remote control. For many people, whether they are working from home or because they are unable to leave, operating the current computer from a distance through another computer can save a lot of time.
 The best PHP framework for microservice architecture: performance and efficiency
Jun 03, 2024 pm 08:27 PM
The best PHP framework for microservice architecture: performance and efficiency
Jun 03, 2024 pm 08:27 PM
Best PHP Microservices Framework: Symfony: Flexibility, performance and scalability, providing a suite of components for building microservices. Laravel: focuses on efficiency and testability, provides a clean API interface, and supports stateless services. Slim: minimalist, fast, provides a simple routing system and optional midbody builder, suitable for building high-performance APIs.
 What are some ways to resolve inefficiencies in PHP functions?
May 02, 2024 pm 01:48 PM
What are some ways to resolve inefficiencies in PHP functions?
May 02, 2024 pm 01:48 PM
Five ways to optimize PHP function efficiency: avoid unnecessary copying of variables. Use references to avoid variable copying. Avoid repeated function calls. Inline simple functions. Optimizing loops using arrays.
 Vivox100s parameter configuration revealed: How to optimize processor performance?
Mar 24, 2024 am 10:27 AM
Vivox100s parameter configuration revealed: How to optimize processor performance?
Mar 24, 2024 am 10:27 AM
Vivox100s parameter configuration revealed: How to optimize processor performance? In today's era of rapid technological development, smartphones have become an indispensable part of our daily lives. As an important part of a smartphone, the performance optimization of the processor is directly related to the user experience of the mobile phone. As a high-profile smartphone, Vivox100s's parameter configuration has attracted much attention, especially the optimization of processor performance has attracted much attention from users. As the "brain" of the mobile phone, the processor directly affects the running speed of the mobile phone.
 Hash table-based data structure optimizes PHP array intersection and union calculations
May 02, 2024 pm 12:06 PM
Hash table-based data structure optimizes PHP array intersection and union calculations
May 02, 2024 pm 12:06 PM
The hash table can be used to optimize PHP array intersection and union calculations, reducing the time complexity from O(n*m) to O(n+m). The specific steps are as follows: Use a hash table to map the elements of the first array to a Boolean value to quickly find whether the element in the second array exists and improve the efficiency of intersection calculation. Use a hash table to mark the elements of the first array as existing, and then add the elements of the second array one by one, ignoring existing elements to improve the efficiency of union calculations.
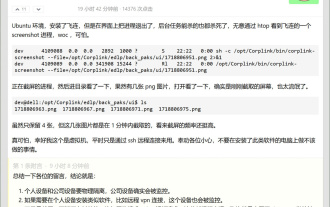 Byte Feilian accused of monitoring screenshots? Relevant person: It is the enterprise that has turned on the data leakage prevention function
Jun 21, 2024 pm 09:47 PM
Byte Feilian accused of monitoring screenshots? Relevant person: It is the enterprise that has turned on the data leakage prevention function
Jun 21, 2024 pm 09:47 PM
According to news on the afternoon of June 21, recently, some netizens said that after installing FeiLian (FeiLian is an office platform used internally by ByteDance and open to the public), they accidentally discovered that FeiLian was executing a screenshot process in the background. The user It reminds everyone not to do things you shouldn't do on computers with such software installed. Sina Technology asked ByteDance about this, and relevant sources said that Feilian provides data security protection functions for corporate customers. Enterprises can set the functional configuration of automated audit policies based on their own business needs and data sensitivity. The situation described in the forum post is that the enterprise administrator has enabled the DLP (data leakage prevention) function on the device that stores sensitive data. Felian will cycle through sensitive devices with DLP enabled at certain intervals.






