 Java
Java
 javaTutorial
javaTutorial
 How to use Java simulation to achieve intranet penetration into the black box?
How to use Java simulation to achieve intranet penetration into the black box?
How to use Java simulation to achieve intranet penetration into the black box?
1. Introduction to Intranet Penetration
Understanding from the perspective of a black box: Usually, whether a personal computer is connected to WIFI to access the Internet or uses a network cable to access the Internet, it belongs to the inside of the LAN. The Internet cannot directly access your computer. Intranet penetration can allow computers in your LAN to access the external network. Give an example: If you run a Web service locally and the occupied port is 8080, then your local test is: //localhost:8080. But what if you want to share your services with a good friend? Yes, it is through intranet penetration. In fact, intranet penetration is a very complicated operation. The explanation on Baidu Encyclopedia is:
Intranet penetration, that is, NAT penetration. NAT penetration is performed to enable certain A data packet with a specific source IP address and source port number is not blocked by the NAT device and is correctly routed to the intranet host.
I obviously can’t do it here. All I need is the service to access the intranet from the external network. As for the specific process, I don't care, I just need to achieve this goal.
2. Specific ideas and implementation details
2.1 Specific ideas
No matter which method is used to achieve intranet penetration, a public IP address is required. Here I am An Alibaba Cloud server is used. The following is a schematic diagram of the entire simulation:

Note:
1. The intranet penetration server is deployed on a machine with a public IP.
2. Intranet services and intranet penetration clients are deployed on intranet machines.
Explanation:
My idea is very simple, that is, the user accesses the intranet penetration server, and then the intranet penetration server sends the user's request message Forward to intranet penetration client , and then the intranet penetration client forwards the request message to intranet service , and then receives the of the intranet service The response message is forwarded to the intranet penetration server, and finally the intranet penetration server forwards it to the user. The general process is like this. For external users, it will only think that they have accessed an external network service, because the user is facing a black box system.
2.2 Implementation details
In order to achieve the above goal, the most critical thing is to maintain a long connection between the intranet penetration client and the intranet penetration server, I need to use this long connection to exchange message information from both parties. Therefore, this long connection needs to be established after the system is started. When a user request comes in, the intranet penetration server first receives the request, and then uses the long connection to transfer it to the intranet penetration client. The network penetration client uses this message as a request to access the intranet service, then receives the response from the intranet service, forwards it to the intranet penetration server, and finally forwards it to the user.
3. Code implementation3.1 Directory structure
Or when exporting into a jar package, just select different main classes.
Client code files: Client.java, Connection.java, Msg.java, ProxyConnection.java.Server code files: Server.java, Connection.java, Msg.java, ProxyConnection.java.
package org.dragon;
import java.io.IOException;
import java.net.Socket;
import java.net.UnknownHostException;
/**
* 用于双向通信的客户端
* */
public class Client {
private static final String REMOTE_HOST = "公网IP";
private static final String LOCAL_HOST = "127.0.0.1";
public static void main(String[] args) {
try {
Socket proxy = new Socket(REMOTE_HOST, 10000);
System.out.println("Connect Server Successfully!");
ProxyConnection proxyConnection = new ProxyConnection(proxy); // 维持和内网穿透服务端的长连接
// 可以实现同一个人多次访问
while (true) {
Msg msg = proxyConnection.receiveMsg();
Connection connection = new Connection(new Socket(LOCAL_HOST, 8080));
connection.sendMsg(msg); // 将请求报文发送给内网服务器,即模拟发送请求报文
msg = connection.receiveMsg(); // 接收内网服务器的响应报文
proxyConnection.sendMsg(msg); // 将内网服务器的响应报文转发给公网服务器(内网穿透服务端)
}
} catch (UnknownHostException e) {
e.printStackTrace();
} catch (IOException e) {
e.printStackTrace();
}
}
}Copy after login
3.3 Connection classpackage org.dragon;
import java.io.IOException;
import java.net.Socket;
import java.net.UnknownHostException;
/**
* 用于双向通信的客户端
* */
public class Client {
private static final String REMOTE_HOST = "公网IP";
private static final String LOCAL_HOST = "127.0.0.1";
public static void main(String[] args) {
try {
Socket proxy = new Socket(REMOTE_HOST, 10000);
System.out.println("Connect Server Successfully!");
ProxyConnection proxyConnection = new ProxyConnection(proxy); // 维持和内网穿透服务端的长连接
// 可以实现同一个人多次访问
while (true) {
Msg msg = proxyConnection.receiveMsg();
Connection connection = new Connection(new Socket(LOCAL_HOST, 8080));
connection.sendMsg(msg); // 将请求报文发送给内网服务器,即模拟发送请求报文
msg = connection.receiveMsg(); // 接收内网服务器的响应报文
proxyConnection.sendMsg(msg); // 将内网服务器的响应报文转发给公网服务器(内网穿透服务端)
}
} catch (UnknownHostException e) {
e.printStackTrace();
} catch (IOException e) {
e.printStackTrace();
}
}
}package org.dragon;
import java.io.BufferedInputStream;
import java.io.BufferedOutputStream;
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
/**
* 维持用户和服务器的连接
* */
public class Connection {
private InputStream input;
private OutputStream output;
public Connection(Socket client) throws IOException {
this.input = new BufferedInputStream(client.getInputStream());
this.output = new BufferedOutputStream(client.getOutputStream());
}
public Msg receiveMsg() throws IOException {
byte[] msg = new byte[2*1024];
int len = input.read(msg);
return new Msg(len, msg);
}
public void sendMsg(Msg msg) throws IOException {
output.write(msg.getMsg(), 0, msg.getLen());
output.flush(); // 每一次写入都要刷新,防止阻塞。
}
}Copy after login
3.4 Msg classpackage org.dragon;
import java.io.BufferedInputStream;
import java.io.BufferedOutputStream;
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.Socket;
/**
* 维持用户和服务器的连接
* */
public class Connection {
private InputStream input;
private OutputStream output;
public Connection(Socket client) throws IOException {
this.input = new BufferedInputStream(client.getInputStream());
this.output = new BufferedOutputStream(client.getOutputStream());
}
public Msg receiveMsg() throws IOException {
byte[] msg = new byte[2*1024];
int len = input.read(msg);
return new Msg(len, msg);
}
public void sendMsg(Msg msg) throws IOException {
output.write(msg.getMsg(), 0, msg.getLen());
output.flush(); // 每一次写入都要刷新,防止阻塞。
}
}package org.dragon;
public class Msg {
private int len;
private byte[] msg;
public Msg(int len, byte[] msg) {
this.len = len;
this.msg = msg;
}
public int getLen() {
return len;
}
public byte[] getMsg() {
return msg;
}
@Override
public String toString() {
return "msg: " + len + " --> " + new String(msg, 0, len);
}
}Copy after login
3.5 ProxyConnection classpackage org.dragon;
public class Msg {
private int len;
private byte[] msg;
public Msg(int len, byte[] msg) {
this.len = len;
this.msg = msg;
}
public int getLen() {
return len;
}
public byte[] getMsg() {
return msg;
}
@Override
public String toString() {
return "msg: " + len + " --> " + new String(msg, 0, len);
}
}package org.dragon;
import java.io.BufferedInputStream;
import java.io.BufferedOutputStream;
import java.io.DataInputStream;
import java.io.DataOutputStream;
import java.io.IOException;
import java.net.Socket;
import java.net.UnknownHostException;
/**
* @author Alfred
*
* 代理服务器和代理客户端是用于维持两者之间通信的一个长连接Socket,
* 主要的目的是因为双方之间的通信方式是全双工的,它们的作用是为了传递报文。
* */
public class ProxyConnection {
private Socket proxySocket;
private DataInputStream input;
private DataOutputStream output;
public ProxyConnection(final Socket socket) throws UnknownHostException, IOException {
proxySocket = socket;
input = new DataInputStream(new BufferedInputStream(proxySocket.getInputStream()));
output = new DataOutputStream(new BufferedOutputStream(proxySocket.getOutputStream()));
}
/**
* 接收报文
* @throws IOException
* */
public Msg receiveMsg() throws IOException {
int len = input.readInt();
if (len <= 0) {
throw new IOException("异常接收数据,长度为:" + len);
}
byte[] msg = new byte[len];
int size = input.read(msg); // 这里到底会不会读取到这么多,我也有点迷惑!
return new Msg(size, msg); // 为了防止出错,还是使用一个记录实际读取值size
}
/**
* 转发报文
* @throws IOException
* */
public void sendMsg(Msg msg) throws IOException {
output.writeInt(msg.getLen());
output.write(msg.getMsg(), 0, msg.getLen());
output.flush(); // 每一次写入都需要手动刷新,防止阻塞。
}
}Copy after login
3.6 Server classpackage org.dragon;
import java.io.BufferedInputStream;
import java.io.BufferedOutputStream;
import java.io.DataInputStream;
import java.io.DataOutputStream;
import java.io.IOException;
import java.net.Socket;
import java.net.UnknownHostException;
/**
* @author Alfred
*
* 代理服务器和代理客户端是用于维持两者之间通信的一个长连接Socket,
* 主要的目的是因为双方之间的通信方式是全双工的,它们的作用是为了传递报文。
* */
public class ProxyConnection {
private Socket proxySocket;
private DataInputStream input;
private DataOutputStream output;
public ProxyConnection(final Socket socket) throws UnknownHostException, IOException {
proxySocket = socket;
input = new DataInputStream(new BufferedInputStream(proxySocket.getInputStream()));
output = new DataOutputStream(new BufferedOutputStream(proxySocket.getOutputStream()));
}
/**
* 接收报文
* @throws IOException
* */
public Msg receiveMsg() throws IOException {
int len = input.readInt();
if (len <= 0) {
throw new IOException("异常接收数据,长度为:" + len);
}
byte[] msg = new byte[len];
int size = input.read(msg); // 这里到底会不会读取到这么多,我也有点迷惑!
return new Msg(size, msg); // 为了防止出错,还是使用一个记录实际读取值size
}
/**
* 转发报文
* @throws IOException
* */
public void sendMsg(Msg msg) throws IOException {
output.writeInt(msg.getLen());
output.write(msg.getMsg(), 0, msg.getLen());
output.flush(); // 每一次写入都需要手动刷新,防止阻塞。
}
}package org.dragon;
import java.io.IOException;
import java.net.ServerSocket;
import java.net.Socket;
/**
* 用于双向通信的服务器
* */
public class Server {
public static void main(String[] args) {
try (ServerSocket server = new ServerSocket(10000)) {
// 用于交换控制信息的Socket
Socket proxy = server.accept();
ProxyConnection proxySocket = new ProxyConnection(proxy);
// 用于正常通讯的socket
while (true) {
Socket client = server.accept();
Connection connection = new Connection(client);
Msg msg = connection.receiveMsg(); // 接收用户的请求报文
proxySocket.sendMsg(msg); // 转发用户的请求报文给内网服务器
msg = proxySocket.receiveMsg(); // 接收内网服务器的响应报文
connection.sendMsg(msg); // 转发内网服务器的响应报文给用户
}
} catch (IOException e) {
e.printStackTrace();
}
}
}Copy after login
4. Intranet serviceThe intranet service is a web service. Here I am using a simple SpringBoot project, which has only three request methods. package org.dragon;
import java.io.IOException;
import java.net.ServerSocket;
import java.net.Socket;
/**
* 用于双向通信的服务器
* */
public class Server {
public static void main(String[] args) {
try (ServerSocket server = new ServerSocket(10000)) {
// 用于交换控制信息的Socket
Socket proxy = server.accept();
ProxyConnection proxySocket = new ProxyConnection(proxy);
// 用于正常通讯的socket
while (true) {
Socket client = server.accept();
Connection connection = new Connection(client);
Msg msg = connection.receiveMsg(); // 接收用户的请求报文
proxySocket.sendMsg(msg); // 转发用户的请求报文给内网服务器
msg = proxySocket.receiveMsg(); // 接收内网服务器的响应报文
connection.sendMsg(msg); // 转发内网服务器的响应报文给用户
}
} catch (IOException e) {
e.printStackTrace();
}
}
}package org.dragon.controller;
import java.util.HashMap;
import java.util.LinkedHashMap;
import java.util.Map;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
@RestController
public class Controller {
@GetMapping("/loveEN")
public String testEN() {
return "I love you yesterday and today!";
}
@GetMapping("/loveZH")
public String loveZH() {
return "有一美人兮,见之不忘。一日不见兮,思之如狂。凤飞翱翔兮,四海求凰。无奈佳人兮,不在东墙。";
}
@GetMapping("/loveJson")
public Map<String, String> loveJson() {
HashMap<String, String> map = new LinkedHashMap<>();
map.put("english", "I love you yesterday and today!");
map.put("chinese", "有一美人兮,见之不忘。一日不见兮,思之如狂。"
+ "凤飞翱翔兮,四海求凰。无奈佳人兮,不在东墙。");
return map;
}
}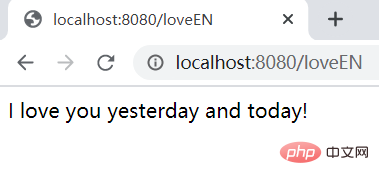


5.2 External network test
Start the intranet penetration server and the intranet penetration client successively, and then access the three URLs in the browser. Note: 1. If you test it yourself, you can switch to the IP address of the intranet penetration server you are running or use a domain name. 2. The external network machine and the internal network machine here use different ports (use them casually, as long as it does not conflict with the service port on your own machine). In fact, you can use port 80 on the external network, which is more friendly to ordinary users. . 3. The third test actually failed. You can see that the loading animation above keeps loading. It stands to reason that this should stop soon, but it seems impossible to stop. This is a system bug, but due to the limited knowledge I have, I won’t solve it.

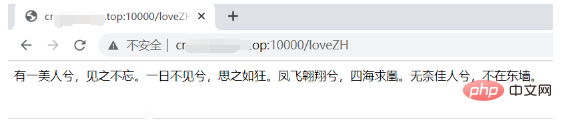

6. Notes
The code here is A simulation, it can only simulate this function, but basically has no actual effect, haha. Because I only have one long connection here, I can only support serial communication. It is best to simply call it by one person. It seems that the calling speed cannot be too fast. I thought of a way to maintain a connection pool between the client and the server, so that multi-threaded access can be achieved. There is no handling of TCP packet sticking and sub-packaging here (I understand this concept, but I am not very good at handling it), so I default to request and response messages being within 2KB in size. Exceeding this length will cause problems. Although this parameter can be increased, if most packets are very small, it will also lead to low efficiency. This intranet penetration can support various protocols above TCP, not necessarily HTTP, at least in theory it is possible.
The above is the detailed content of How to use Java simulation to achieve intranet penetration into the black box?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1663
1663
 14
14
 1419
1419
 52
52
 1313
1313
 25
25
 1264
1264
 29
29
 1237
1237
 24
24
 Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Java 8 introduces the Stream API, providing a powerful and expressive way to process data collections. However, a common question when using Stream is: How to break or return from a forEach operation? Traditional loops allow for early interruption or return, but Stream's forEach method does not directly support this method. This article will explain the reasons and explore alternative methods for implementing premature termination in Stream processing systems. Further reading: Java Stream API improvements Understand Stream forEach The forEach method is a terminal operation that performs one operation on each element in the Stream. Its design intention is
 PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP is a scripting language widely used on the server side, especially suitable for web development. 1.PHP can embed HTML, process HTTP requests and responses, and supports a variety of databases. 2.PHP is used to generate dynamic web content, process form data, access databases, etc., with strong community support and open source resources. 3. PHP is an interpreted language, and the execution process includes lexical analysis, grammatical analysis, compilation and execution. 4.PHP can be combined with MySQL for advanced applications such as user registration systems. 5. When debugging PHP, you can use functions such as error_reporting() and var_dump(). 6. Optimize PHP code to use caching mechanisms, optimize database queries and use built-in functions. 7
 PHP vs. Python: Understanding the Differences
Apr 11, 2025 am 12:15 AM
PHP vs. Python: Understanding the Differences
Apr 11, 2025 am 12:15 AM
PHP and Python each have their own advantages, and the choice should be based on project requirements. 1.PHP is suitable for web development, with simple syntax and high execution efficiency. 2. Python is suitable for data science and machine learning, with concise syntax and rich libraries.
 PHP vs. Other Languages: A Comparison
Apr 13, 2025 am 12:19 AM
PHP vs. Other Languages: A Comparison
Apr 13, 2025 am 12:19 AM
PHP is suitable for web development, especially in rapid development and processing dynamic content, but is not good at data science and enterprise-level applications. Compared with Python, PHP has more advantages in web development, but is not as good as Python in the field of data science; compared with Java, PHP performs worse in enterprise-level applications, but is more flexible in web development; compared with JavaScript, PHP is more concise in back-end development, but is not as good as JavaScript in front-end development.
 PHP vs. Python: Core Features and Functionality
Apr 13, 2025 am 12:16 AM
PHP vs. Python: Core Features and Functionality
Apr 13, 2025 am 12:16 AM
PHP and Python each have their own advantages and are suitable for different scenarios. 1.PHP is suitable for web development and provides built-in web servers and rich function libraries. 2. Python is suitable for data science and machine learning, with concise syntax and a powerful standard library. When choosing, it should be decided based on project requirements.
 Java Program to Find the Volume of Capsule
Feb 07, 2025 am 11:37 AM
Java Program to Find the Volume of Capsule
Feb 07, 2025 am 11:37 AM
Capsules are three-dimensional geometric figures, composed of a cylinder and a hemisphere at both ends. The volume of the capsule can be calculated by adding the volume of the cylinder and the volume of the hemisphere at both ends. This tutorial will discuss how to calculate the volume of a given capsule in Java using different methods. Capsule volume formula The formula for capsule volume is as follows: Capsule volume = Cylindrical volume Volume Two hemisphere volume in, r: The radius of the hemisphere. h: The height of the cylinder (excluding the hemisphere). Example 1 enter Radius = 5 units Height = 10 units Output Volume = 1570.8 cubic units explain Calculate volume using formula: Volume = π × r2 × h (4
 PHP's Impact: Web Development and Beyond
Apr 18, 2025 am 12:10 AM
PHP's Impact: Web Development and Beyond
Apr 18, 2025 am 12:10 AM
PHPhassignificantlyimpactedwebdevelopmentandextendsbeyondit.1)ItpowersmajorplatformslikeWordPressandexcelsindatabaseinteractions.2)PHP'sadaptabilityallowsittoscaleforlargeapplicationsusingframeworkslikeLaravel.3)Beyondweb,PHPisusedincommand-linescrip
 PHP: The Foundation of Many Websites
Apr 13, 2025 am 12:07 AM
PHP: The Foundation of Many Websites
Apr 13, 2025 am 12:07 AM
The reasons why PHP is the preferred technology stack for many websites include its ease of use, strong community support, and widespread use. 1) Easy to learn and use, suitable for beginners. 2) Have a huge developer community and rich resources. 3) Widely used in WordPress, Drupal and other platforms. 4) Integrate tightly with web servers to simplify development deployment.



