 Technology peripherals
Technology peripherals
 AI
AI
 Specialized in treating 'image misuse'! Elsevier, Nature and other top journals use AI to uncover cheating scientists
Specialized in treating 'image misuse'! Elsevier, Nature and other top journals use AI to uncover cheating scientists
Specialized in treating 'image misuse'! Elsevier, Nature and other top journals use AI to uncover cheating scientists
Not long ago, we just recruited a Nobel Prize winner who published many papers through PS method.
Now, as more and more academic publishing organizations begin to use AI software to detect tampered data, scientists who are lucky enough to do so should think twice before committing.

#Is the picture misused?
In today's academic circles, it is quite common to copy, flip, rotate, move, and crop pictures of the same cell group before reusing them.
Using these doctored images, researchers pretend that they have a lot of data and have done a lot of experiments, when this is not the case.
According to Daniel Evanko, director of operations for the American Association for Cancer Research (AACR), image duplication was the primary reason AACR retracted papers between 2016 and 2020. And retraction not only damages the reputation of the author, but also damages the reputation of the publisher.
To avoid embarrassment to both parties, academic publications like AACR have begun using AI software to detect image duplications before publishing papers. The software is called Proofig, an image inspection program developed by an Israeli startup.
Evanko presented the results of the pilot study at the International Peer Review and Scientific Publishing Conference in Chicago in early September and described how Proofig has impacted the AACR.

AACR publishes ten research journals and reviews more than 13,000 submissions annually. From January 2021 to May 2022, officials used Proofig to screen 1,367 papers tentatively accepted for publication, checked 208 papers with duplicate images, and contacted the authors of the papers.
According to foreign media reports: In many cases, the duplication of images in papers is due to "image misuse", and this problem can be solved by submitting new data.
The editor said: Is it that simple?
In other cases, Proofig showed clear signs of fraud. Of these 208 papers, 4 were retracted and 1 was rejected.
Academic fraud has always been common and occurs in institutions with poor reputations. However, now, academic fraud is frequently discovered in top laboratories of famous universities.
Science recently released an investigative report saying that decades of research on new treatments for Alzheimer’s disease have failed and clinical trials have failed, all based on an article. Image duplication in highly cited papers.
One of the evidences of fraud that Proofig found was a series of blurred lines produced using Western blots technology that were copied, edited and pasted into the mouse data. This kind of fraud is difficult to spot to the untrained eye.
Proofig CEO Dror Kolodkin-Gal said finding such subtle changes would be a fairly tedious task for most humans, but it's ideal for computers.
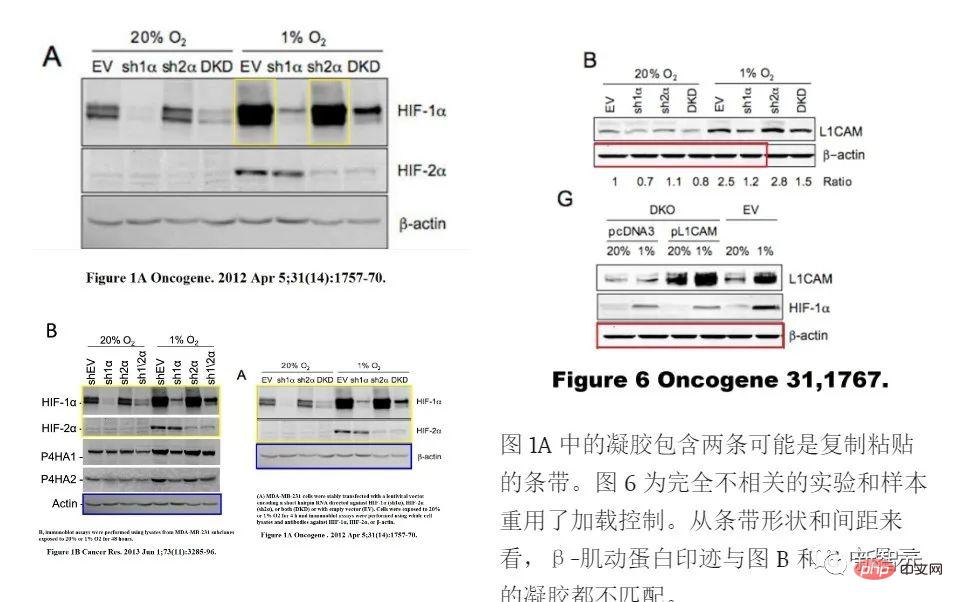
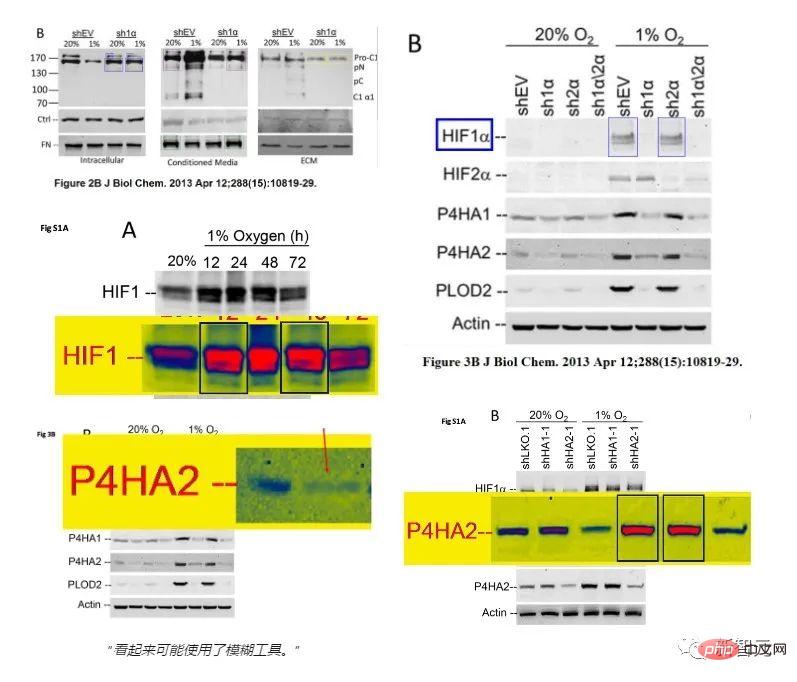
##"Misuse of Pictures" by 2019 Nobel Laureate Gregg L. Semenza
When Proofig works, it first checks whether a specific image matches other sub-images in the paper. The sub-image may be moved, flipped or rotated, cropped or copied, there are quite a few possibilities.
Proofig combines computer vision and artificial intelligence algorithms to extract and classify images. This kind of calculation is very complicated, but fortunately, machine learning is making rapid progress.
"Before the advent of artificial intelligence, just extracting sub-images from papers required ten times the R&D investment, and God knows how to calculate it. Whether it was technological advancements in algorithms or running GPUs in the cloud Ability has brought about huge changes." Kolodkin-Gal said.
Still requires human intervention
Of course, AI software like Proofig cannot find cheaters on its own.
Elisabeth Bik, an image forensics expert and independent scientific consultant, said: "To interpret the results of the software, we still need a person with relevant knowledge and experience." After all, the human eye can outperform a computer in some situations.
"You can't let the software run on its own because it might flag a lot of things that aren't problematic."
Bik at work Another AI software-ImageTwin was used. Sometimes, it doesn't analyze protein blots very clearly. "A Western blot is basically a black stripe on a plain background. I can see some subtleties in the shape with my human eye, but this software somehow just can't see it."
"This is probably because the workings of our eyes and brains are super complex. I think maybe it's because the software only looks for relative distances, so a black stripe just looks like a black stripe. It's also not very good at finding Small edges, or similar shapes to other shapes," Bik said.
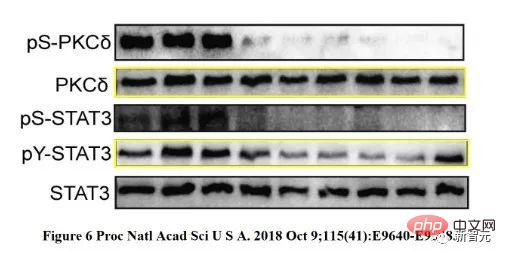
##"Misuse of Pictures" by 2019 Nobel Laureate Gregg L. Semenza
Examining protein prints is very challenging for machines, Kolodkin-Gal agrees. "It took us a lot of investment to finally find a good algorithm to find those bands. This is too challenging for artificial intelligence because the bands are very small."
Academic publications use image inspection tools like Proofig at different stages of the publishing process. AACR will scan all manuscripts that are initially accepted, and Taylor & Francis will only use it to check papers that are questioned by editors or peer reviewers.
"If the software detects potential image duplication or other manipulation, and this determination is supported by our team of experts, we will respond to such incidents in accordance with established procedures and the Publication Ethics Committee An investigation will be carried out in accordance with the established guidelines," a company spokesperson said.
In the publishing process, when to use these tools depends on the cost. Image processing is computationally intensive, so publications must pay cloud computing costs for companies like Proofig.
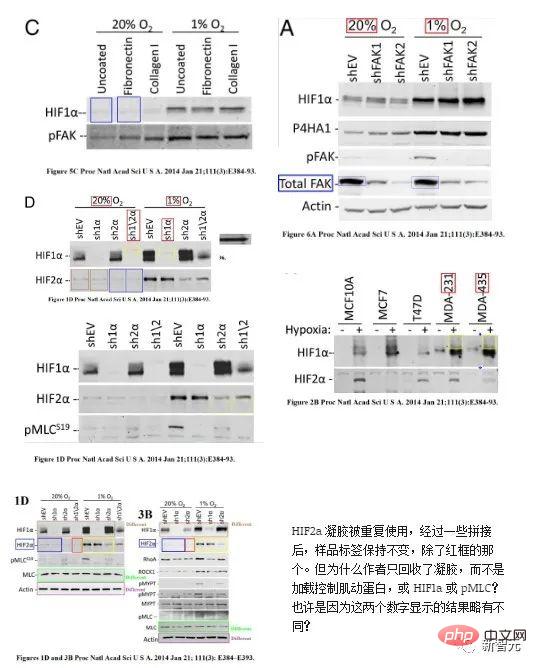
##"Misuse of Pictures" by 2019 Nobel Laureate Gregg L. Semenza
It would be too expensive to screen every paper at the submission stage. For example, using Proofig to analyze 120 sub-images costs $99. To thoroughly check a paper, Proofig needs to handle all possible combinations in a paper, which can be considered a "huge sum of money."Currently, AACR and organizations such as Taylor & Francis are negotiating to provide a packaged service tailored to their business at a cheaper price.
Helen King, director of SAGE, said: “Due to the cost of human supervision and using software, we currently only use Proofig when papers enter more advanced review stages. So far, it has Problems have been flagged in nearly one-third of the papers detected. Next, relevant professional knowledge is needed to explain."
AI cannot detect copied images in different papers
Now, more and more organizations are beginning to use AI software.The American Association for Clinical Research has also adopted Proofig, while publishers such as Frontiers have also developed their own tools.
Wiley is also using some kind of software, while PLOS, Elsevier and Nature are either open to projects or actively testing projects. Although artificial intelligence software is getting better at spotting suspicious data, it cannot catch all forms of cheating by scientists. Proofig can check if an image is duplicated in the same paper, but it won’t catch it if the image has been copied or processed in a different paper. Obviously, in order to deal with this situation, Proofig needs to build an image cache database captured from published papers to conduct a comprehensive comparison. ##"Misuse of Pictures" by 2019 Nobel Laureate Gregg L. Semenza "The biggest challenge we face is big data." Kolodkin-Gal said. "If publications don't band together and build an image database, image plagiarism will still be a big problem. To develop artificial intelligence, you have to have big data." Although we still have Despite all its flaws, the emergence of Proofig software is still a good start in combating cheating and improving academic integrity. “I do think it’s a very good thing for publications to start using software because it provides some quality control over the publishing process and will act as a deterrent. This type of software will Let the authors know: We will review your paper for these types of duplications. In my opinion, it won't prevent fraud, but it will make it a little harder," Bik said. If AI can really act as a sufficient deterrent to academic fraud, it would be a good thing. 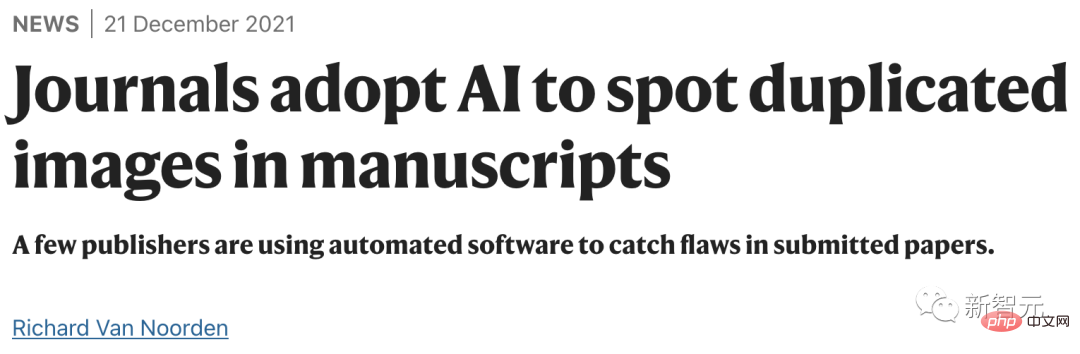
The above is the detailed content of Specialized in treating 'image misuse'! Elsevier, Nature and other top journals use AI to uncover cheating scientists. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1419
1419
 52
52
 1312
1312
 25
25
 1262
1262
 29
29
 1235
1235
 24
24
 How much is Bitcoin worth
Apr 28, 2025 pm 07:42 PM
How much is Bitcoin worth
Apr 28, 2025 pm 07:42 PM
Bitcoin’s price ranges from $20,000 to $30,000. 1. Bitcoin’s price has fluctuated dramatically since 2009, reaching nearly $20,000 in 2017 and nearly $60,000 in 2021. 2. Prices are affected by factors such as market demand, supply, and macroeconomic environment. 3. Get real-time prices through exchanges, mobile apps and websites. 4. Bitcoin price is highly volatile, driven by market sentiment and external factors. 5. It has a certain relationship with traditional financial markets and is affected by global stock markets, the strength of the US dollar, etc. 6. The long-term trend is bullish, but risks need to be assessed with caution.
 Which of the top ten currency trading platforms in the world are among the top ten currency trading platforms in 2025
Apr 28, 2025 pm 08:12 PM
Which of the top ten currency trading platforms in the world are among the top ten currency trading platforms in 2025
Apr 28, 2025 pm 08:12 PM
The top ten cryptocurrency exchanges in the world in 2025 include Binance, OKX, Gate.io, Coinbase, Kraken, Huobi, Bitfinex, KuCoin, Bittrex and Poloniex, all of which are known for their high trading volume and security.
 Which of the top ten currency trading platforms in the world are the latest version of the top ten currency trading platforms
Apr 28, 2025 pm 08:09 PM
Which of the top ten currency trading platforms in the world are the latest version of the top ten currency trading platforms
Apr 28, 2025 pm 08:09 PM
The top ten cryptocurrency trading platforms in the world include Binance, OKX, Gate.io, Coinbase, Kraken, Huobi Global, Bitfinex, Bittrex, KuCoin and Poloniex, all of which provide a variety of trading methods and powerful security measures.
 Decryption Gate.io Strategy Upgrade: How to Redefine Crypto Asset Management in MeMebox 2.0?
Apr 28, 2025 pm 03:33 PM
Decryption Gate.io Strategy Upgrade: How to Redefine Crypto Asset Management in MeMebox 2.0?
Apr 28, 2025 pm 03:33 PM
MeMebox 2.0 redefines crypto asset management through innovative architecture and performance breakthroughs. 1) It solves three major pain points: asset silos, income decay and paradox of security and convenience. 2) Through intelligent asset hubs, dynamic risk management and return enhancement engines, cross-chain transfer speed, average yield rate and security incident response speed are improved. 3) Provide users with asset visualization, policy automation and governance integration, realizing user value reconstruction. 4) Through ecological collaboration and compliance innovation, the overall effectiveness of the platform has been enhanced. 5) In the future, smart contract insurance pools, forecast market integration and AI-driven asset allocation will be launched to continue to lead the development of the industry.
 What are the top ten virtual currency trading apps? The latest digital currency exchange rankings
Apr 28, 2025 pm 08:03 PM
What are the top ten virtual currency trading apps? The latest digital currency exchange rankings
Apr 28, 2025 pm 08:03 PM
The top ten digital currency exchanges such as Binance, OKX, gate.io have improved their systems, efficient diversified transactions and strict security measures.
 What are the top currency trading platforms? The top 10 latest virtual currency exchanges
Apr 28, 2025 pm 08:06 PM
What are the top currency trading platforms? The top 10 latest virtual currency exchanges
Apr 28, 2025 pm 08:06 PM
Currently ranked among the top ten virtual currency exchanges: 1. Binance, 2. OKX, 3. Gate.io, 4. Coin library, 5. Siren, 6. Huobi Global Station, 7. Bybit, 8. Kucoin, 9. Bitcoin, 10. bit stamp.
 Recommended reliable digital currency trading platforms. Top 10 digital currency exchanges in the world. 2025
Apr 28, 2025 pm 04:30 PM
Recommended reliable digital currency trading platforms. Top 10 digital currency exchanges in the world. 2025
Apr 28, 2025 pm 04:30 PM
Recommended reliable digital currency trading platforms: 1. OKX, 2. Binance, 3. Coinbase, 4. Kraken, 5. Huobi, 6. KuCoin, 7. Bitfinex, 8. Gemini, 9. Bitstamp, 10. Poloniex, these platforms are known for their security, user experience and diverse functions, suitable for users at different levels of digital currency transactions
 How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
DMA in C refers to DirectMemoryAccess, a direct memory access technology, allowing hardware devices to directly transmit data to memory without CPU intervention. 1) DMA operation is highly dependent on hardware devices and drivers, and the implementation method varies from system to system. 2) Direct access to memory may bring security risks, and the correctness and security of the code must be ensured. 3) DMA can improve performance, but improper use may lead to degradation of system performance. Through practice and learning, we can master the skills of using DMA and maximize its effectiveness in scenarios such as high-speed data transmission and real-time signal processing.



