 Technology peripherals
Technology peripherals
 AI
AI
 New U.S. Department of Commerce rules: Sharing security vulnerabilities to China without approval is prohibited, and Microsoft's objections are invalid
New U.S. Department of Commerce rules: Sharing security vulnerabilities to China without approval is prohibited, and Microsoft's objections are invalid
New U.S. Department of Commerce rules: Sharing security vulnerabilities to China without approval is prohibited, and Microsoft's objections are invalid
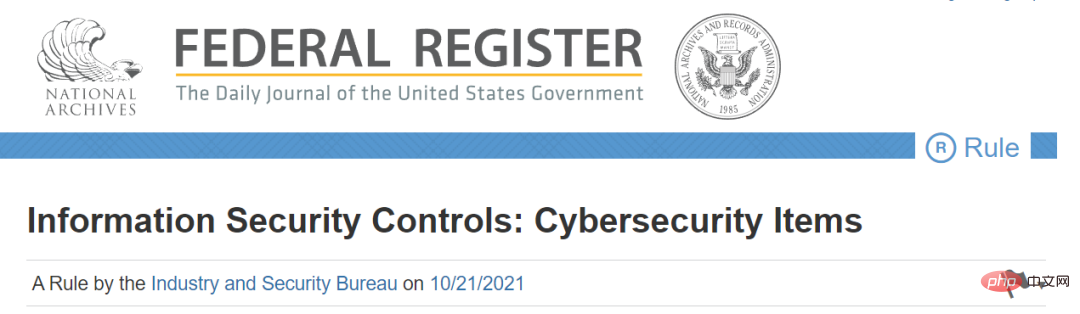
Recently, the U.S. Department of Commerce’s Bureau of Industry and Security (BIS) officially released the latest export control regulations for the field of cybersecurity.
Yes, it is the BIS that publishes the "Entity List" and "Trade Blacklist". In recent years, it can be regarded as an "old friend of Chinese netizens".
What is it this time? It is mainly about the management and control of network security and vulnerability information.
To put it simply, when U.S. entities cooperate with organizations and individuals related to the Chinese government, if security vulnerabilities and information are discovered, they cannot be directly announced and must first be reviewed by the Ministry of Commerce.
The reason is the tried-and-tested "national security" and the "need for counter-terrorism."

In fact, the new regulations announced this time are the final confirmation of the interim regulations (draft for comments) in October 2021. This regulation divides countries around the world into four categories: A, B, D, and E, with restrictive measures and strictness gradually increasing.
China is classified in Category D, which is "restricted countries and regions", and Category E is "comprehensive embargoed countries".
This regulation establishes new control methods for certain network security projects for the purpose of "national security and counter-terrorism considerations."
At the same time, BIS also added a new exception to authorize network security exits. The core content is to authorize the export of these cybersecurity items to most destinations, but not with the exceptions mentioned above.
BIS believes that these controlled projects may be used for surveillance, espionage, or other acts aimed at sabotage.
In addition, the regulations also amend the export control classification numbers in the Commerce Control List.
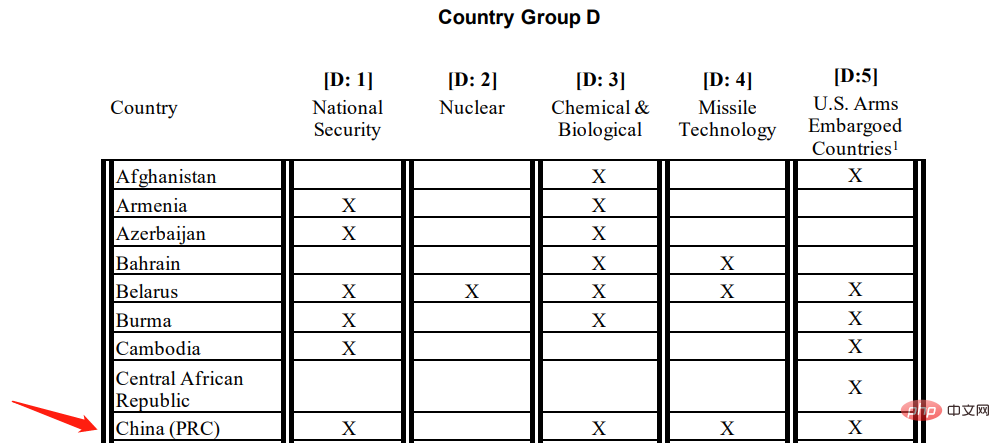
The new BIS regulations divide countries around the world into four categories: A, B, D, and E. Category D is the most concerned and restricted countries and regions.
As shown in the picture above, China is classified in category D.
According to the requirements of the new regulations, when entities cooperate with relevant government departments or individuals in Class D countries and regions, they must apply in advance and obtain permission before they can send potential cross-border Network vulnerability information.
Of course, there are exceptions to the terms. If it is for legitimate cybersecurity purposes, such as public disclosure of vulnerabilities or incident response, no advance application is required.
As you can see, China’s national security, biochemical, missile technology, and U.S. arms embargo are all marked with an X.
The document states that licensing requirements for individuals acting on behalf of governments are necessary to prevent those acting on behalf of governments in Group D countries from obtaining "cyber licenses for engaging in activities contrary to the national security and foreign policy interests of the United States." Safety Project".

Without this requirement, it may result in governments in Class D countries having access to these projects.
The requirement adopted by BIS means exporters must in some cases check the government affiliations of individuals and companies they work with.
However, due to the limited scope and applicability of the licensing requirement, BIS believes that the requirement will protect U.S. national security and foreign policy interests without unduly impacting legitimate cybersecurity activities.
At the same time, BIS also revised clause § 740.22(c)(2)(i), which actually expanded the scope of the exception.

The current terms allow the export of digital products to Group D countries, or the export of any cybersecurity items to Group D countries for police or judicial agencies.
However, BIS actually only intends to allow the export of digital products to police or judicial agencies in Group D countries for the purposes of criminal or civil investigations or prosecutions.
It can be said that these changes reflect the expected opinions.
Microsoft objects, invalid!
Regarding BIS’s new regulations, domestic technology giants in the United States are not monolithic. The software giant Microsoft has clearly expressed its objections.
As early as last year, after this regulation was released for consultation, Microsoft submitted its objections to this document in the form of written comments in the comment section.
Microsoft stated that if individuals and entities involved in cybersecurity activities are restricted due to ties to the government, it will greatly suppress the global cybersecurity market. Capabilities of currently deployed routine cybersecurity activities.
Many times, when companies are unable to determine whether the other party is related to the government, they can only give up cooperation in the face of compliance pressure.

Microsoft’s opposition is not surprising.
The current vulnerability sharing mechanism is very important to Microsoft’s software development ecosystem. Many times, Microsoft needs to analyze vulnerabilities through reverse engineering and other technologies before releasing relevant patches and upgrades. Once the vulnerability sharing mechanism is destroyed, it will directly reduce the speed of Microsoft's discovery and repair of vulnerabilities.
Microsoft proposed that BIS should further clarify the definition of "government end users", or at least clarify which individuals or entities may be covered under this definition.
When BIS released the final draft of the regulation, it mentioned Microsoft's objections but did not name them and stated that "BIS does not agree with this opinion."
BIS mentioned in the document:
"Companies have stated that restrictions on people representing 'government end users' will hinder cross-border cooperation with cybersecurity personnel because of the difficulty in working with these Before communicating with people, check whether they have government connections. The company recommended that this requirement be removed or modified. BIS disagreed with this recommendation."
The final decision, released last week, is consistent with There are no major changes in the content compared to the draft released for comments last October.
However, the regulations adopted some opinions from the research community, further narrowed the scope of security vulnerabilities that need to be verified, and added temporary exceptions.
That is: if it is for legitimate network security purposes, such as disclosing public vulnerabilities or responding to security incidents, no review is required.

#This exception clause is largely to create necessary conditions for the normal operation of the open source community.
While Microsoft thanked BIS for revising the rules, it also stated that it was not sure whether such exceptions could solve the actual problem.
"What is allowed to be directly disclosed and what is not allowed to be disclosed is still in a state of confusion. What activities require a license cannot be determined at this stage. We are worried that for those technologies that cannot be fully classified into specific use categories , the license application will be very cumbersome."
BIS acknowledged Microsoft's concerns, but at the same time insisted that this provision would do more good than harm to U.S. national security.
Similar to the "Wassenaar Agreement"
In fact, as early as October 2021, BIS issued regulations "prohibiting the export of offensive network tools" , preventing U.S. entities from selling offensive cyber tools to China and Russia.

U.S. Commerce Secretary Gina Raimondo said, “Implementing export controls on certain cybersecurity items is an appropriate approach to protect U.S. national security from malicious intent. The infringement of online behavior and to ensure legitimate network security activities."
BIS further stated that the current rules are also within the framework of the "Wassenaar Agreement", that is, the "About Standing Orders" Wassenaar Agreement on Export Controls of Arms and Dual-Use Goods and Technologies.

The "Wassenaar Agreement" stipulates that member states shall decide on their own to issue export licenses for dual-use items of sensitive products and technologies, and on a voluntary basis Notify relevant information to other member states of the Agreement on a basic basis.
In fact, the agreement is actually controlled by the United States to a large extent and affects the export control regulations of other member countries, becoming an important tool for the West to implement high-tech monopoly on China.
The agreement controls the export policy of "military and dual-use technologies". There are 42 agreement countries, including major developed countries such as the United States, Britain, France, Germany, and Japan. Although Russia is also a party to the agreement, it is still one of the embargo targets.
The above is the detailed content of New U.S. Department of Commerce rules: Sharing security vulnerabilities to China without approval is prohibited, and Microsoft's objections are invalid. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
Using the chrono library in C can allow you to control time and time intervals more accurately. Let's explore the charm of this library. C's chrono library is part of the standard library, which provides a modern way to deal with time and time intervals. For programmers who have suffered from time.h and ctime, chrono is undoubtedly a boon. It not only improves the readability and maintainability of the code, but also provides higher accuracy and flexibility. Let's start with the basics. The chrono library mainly includes the following key components: std::chrono::system_clock: represents the system clock, used to obtain the current time. std::chron
 How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
Measuring thread performance in C can use the timing tools, performance analysis tools, and custom timers in the standard library. 1. Use the library to measure execution time. 2. Use gprof for performance analysis. The steps include adding the -pg option during compilation, running the program to generate a gmon.out file, and generating a performance report. 3. Use Valgrind's Callgrind module to perform more detailed analysis. The steps include running the program to generate the callgrind.out file and viewing the results using kcachegrind. 4. Custom timers can flexibly measure the execution time of a specific code segment. These methods help to fully understand thread performance and optimize code.
 How to optimize code
Apr 28, 2025 pm 10:27 PM
How to optimize code
Apr 28, 2025 pm 10:27 PM
C code optimization can be achieved through the following strategies: 1. Manually manage memory for optimization use; 2. Write code that complies with compiler optimization rules; 3. Select appropriate algorithms and data structures; 4. Use inline functions to reduce call overhead; 5. Apply template metaprogramming to optimize at compile time; 6. Avoid unnecessary copying, use moving semantics and reference parameters; 7. Use const correctly to help compiler optimization; 8. Select appropriate data structures, such as std::vector.
 What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
C performs well in real-time operating system (RTOS) programming, providing efficient execution efficiency and precise time management. 1) C Meet the needs of RTOS through direct operation of hardware resources and efficient memory management. 2) Using object-oriented features, C can design a flexible task scheduling system. 3) C supports efficient interrupt processing, but dynamic memory allocation and exception processing must be avoided to ensure real-time. 4) Template programming and inline functions help in performance optimization. 5) In practical applications, C can be used to implement an efficient logging system.
 How to use string streams in C?
Apr 28, 2025 pm 09:12 PM
How to use string streams in C?
Apr 28, 2025 pm 09:12 PM
The main steps and precautions for using string streams in C are as follows: 1. Create an output string stream and convert data, such as converting integers into strings. 2. Apply to serialization of complex data structures, such as converting vector into strings. 3. Pay attention to performance issues and avoid frequent use of string streams when processing large amounts of data. You can consider using the append method of std::string. 4. Pay attention to memory management and avoid frequent creation and destruction of string stream objects. You can reuse or use std::stringstream.
 How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
DMA in C refers to DirectMemoryAccess, a direct memory access technology, allowing hardware devices to directly transmit data to memory without CPU intervention. 1) DMA operation is highly dependent on hardware devices and drivers, and the implementation method varies from system to system. 2) Direct access to memory may bring security risks, and the correctness and security of the code must be ensured. 3) DMA can improve performance, but improper use may lead to degradation of system performance. Through practice and learning, we can master the skills of using DMA and maximize its effectiveness in scenarios such as high-speed data transmission and real-time signal processing.
 What is static analysis in C?
Apr 28, 2025 pm 09:09 PM
What is static analysis in C?
Apr 28, 2025 pm 09:09 PM
The application of static analysis in C mainly includes discovering memory management problems, checking code logic errors, and improving code security. 1) Static analysis can identify problems such as memory leaks, double releases, and uninitialized pointers. 2) It can detect unused variables, dead code and logical contradictions. 3) Static analysis tools such as Coverity can detect buffer overflow, integer overflow and unsafe API calls to improve code security.
 How to implement loosely coupled design in C?
Apr 28, 2025 pm 09:42 PM
How to implement loosely coupled design in C?
Apr 28, 2025 pm 09:42 PM
To implement loose coupling design in C, you can use the following methods: 1. Use interfaces, such as defining the Logger interface and implementing FileLogger and ConsoleLogger; 2. Dependency injection, such as the DataAccess class receives Database pointers through the constructor; 3. Observer mode, such as the Subject class notifies ConcreteObserver and AnotherObserver. Through these technologies, dependencies between modules can be reduced and code maintainability and flexibility can be improved.





