What is the nisec user management tool?
NISEC user management tool refers to the "tax control disk tax digital certificate driver", which is Piovan invoicing software and belongs to the value-added tax invoicing software; it is an auxiliary driver for the tax control disk, and the USB is inserted into the golden tax disk or To log in to the tax control disk and query platform website, you need to use the NISEC user management tool. If you uninstall the software, the computer will not be able to open the tax control invoicing software and will prompt that the USBKEY driver is not installed.

The operating environment of this tutorial: windows7 system, NISEC user management tool 1.0.8.7, Dell G3 computer.
NISEC user management tool is the tax digital certificate driver for the tax control disk. Insert the USB into the golden tax disk or tax control disk. To log in to the query platform website, you need to use the NISEC user management tool!
NISEC user management tool is Piovan invoicing software, which is a VAT invoicing software. It is an auxiliary driver for the tax control disk. If you uninstall this software, the computer will not be able to open the tax control and invoicing software, and it will prompt that the USBKEY driver is not installed.
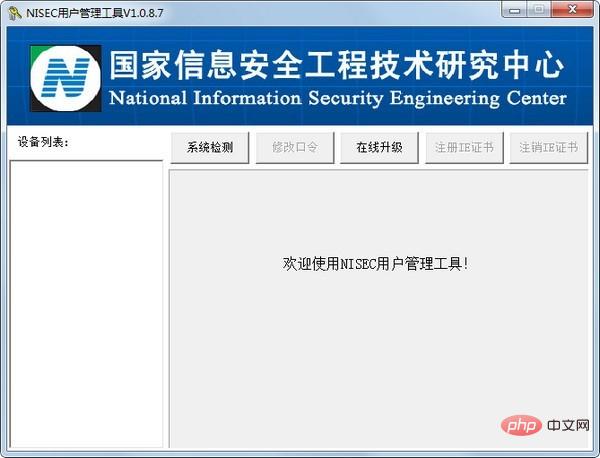
Installation instructions
1. Before installing this driver, please be sure to have installed the value-added tax invoice issuing software. If the invoicing software has been installed, the driver needs to be reinstalled, otherwise it will affect normal use.
2. The Golden Tax Disk can realize all the functions of other KEYs. Therefore, after installing this driver, in order to avoid certificate conflicts, it cannot be mixed with keys or disks from other manufacturers on the same machine.
Notes
Notes on the Golden Tax Disk Tax Digital Certificate Driver:
1. Please do not click "Import Certificate" and "Delete" when using it Certificate", otherwise normal use will be affected.
2. If the "Invoicing Software" has been reinstalled, the driver needs to be reinstalled.
3. You must enter the operating system as an administrator.
4. You must use the IE browser that comes with the system. IE11 is not supported yet.
5. If all operating systems are using IE9 and above, the browser needs to check "Use SSL2.0" in the Internet Options → "*" and uncheck "Use TLS1.2" and "Use TLS1.3".
Expand knowledge:
Value-added tax is a type of circulation that is levied based on the added value generated during the circulation of goods (including taxable services) as the basis for tax calculation. Tax. In terms of tax calculation principles, value-added tax is a turnover tax levied on the added value of multiple links in the production, circulation, and labor services of goods or the added value of goods.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What is the nisec user management tool?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
How to use the chrono library in C?
Apr 28, 2025 pm 10:18 PM
Using the chrono library in C can allow you to control time and time intervals more accurately. Let's explore the charm of this library. C's chrono library is part of the standard library, which provides a modern way to deal with time and time intervals. For programmers who have suffered from time.h and ctime, chrono is undoubtedly a boon. It not only improves the readability and maintainability of the code, but also provides higher accuracy and flexibility. Let's start with the basics. The chrono library mainly includes the following key components: std::chrono::system_clock: represents the system clock, used to obtain the current time. std::chron
 How to optimize code
Apr 28, 2025 pm 10:27 PM
How to optimize code
Apr 28, 2025 pm 10:27 PM
C code optimization can be achieved through the following strategies: 1. Manually manage memory for optimization use; 2. Write code that complies with compiler optimization rules; 3. Select appropriate algorithms and data structures; 4. Use inline functions to reduce call overhead; 5. Apply template metaprogramming to optimize at compile time; 6. Avoid unnecessary copying, use moving semantics and reference parameters; 7. Use const correctly to help compiler optimization; 8. Select appropriate data structures, such as std::vector.
 How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
How to measure thread performance in C?
Apr 28, 2025 pm 10:21 PM
Measuring thread performance in C can use the timing tools, performance analysis tools, and custom timers in the standard library. 1. Use the library to measure execution time. 2. Use gprof for performance analysis. The steps include adding the -pg option during compilation, running the program to generate a gmon.out file, and generating a performance report. 3. Use Valgrind's Callgrind module to perform more detailed analysis. The steps include running the program to generate the callgrind.out file and viewing the results using kcachegrind. 4. Custom timers can flexibly measure the execution time of a specific code segment. These methods help to fully understand thread performance and optimize code.
 How to use string streams in C?
Apr 28, 2025 pm 09:12 PM
How to use string streams in C?
Apr 28, 2025 pm 09:12 PM
The main steps and precautions for using string streams in C are as follows: 1. Create an output string stream and convert data, such as converting integers into strings. 2. Apply to serialization of complex data structures, such as converting vector into strings. 3. Pay attention to performance issues and avoid frequent use of string streams when processing large amounts of data. You can consider using the append method of std::string. 4. Pay attention to memory management and avoid frequent creation and destruction of string stream objects. You can reuse or use std::stringstream.
 What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
What is real-time operating system programming in C?
Apr 28, 2025 pm 10:15 PM
C performs well in real-time operating system (RTOS) programming, providing efficient execution efficiency and precise time management. 1) C Meet the needs of RTOS through direct operation of hardware resources and efficient memory management. 2) Using object-oriented features, C can design a flexible task scheduling system. 3) C supports efficient interrupt processing, but dynamic memory allocation and exception processing must be avoided to ensure real-time. 4) Template programming and inline functions help in performance optimization. 5) In practical applications, C can be used to implement an efficient logging system.
 How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
How to understand DMA operations in C?
Apr 28, 2025 pm 10:09 PM
DMA in C refers to DirectMemoryAccess, a direct memory access technology, allowing hardware devices to directly transmit data to memory without CPU intervention. 1) DMA operation is highly dependent on hardware devices and drivers, and the implementation method varies from system to system. 2) Direct access to memory may bring security risks, and the correctness and security of the code must be ensured. 3) DMA can improve performance, but improper use may lead to degradation of system performance. Through practice and learning, we can master the skills of using DMA and maximize its effectiveness in scenarios such as high-speed data transmission and real-time signal processing.
 What is static analysis in C?
Apr 28, 2025 pm 09:09 PM
What is static analysis in C?
Apr 28, 2025 pm 09:09 PM
The application of static analysis in C mainly includes discovering memory management problems, checking code logic errors, and improving code security. 1) Static analysis can identify problems such as memory leaks, double releases, and uninitialized pointers. 2) It can detect unused variables, dead code and logical contradictions. 3) Static analysis tools such as Coverity can detect buffer overflow, integer overflow and unsafe API calls to improve code security.
 Steps to add and delete fields to MySQL tables
Apr 29, 2025 pm 04:15 PM
Steps to add and delete fields to MySQL tables
Apr 29, 2025 pm 04:15 PM
In MySQL, add fields using ALTERTABLEtable_nameADDCOLUMNnew_columnVARCHAR(255)AFTERexisting_column, delete fields using ALTERTABLEtable_nameDROPCOLUMNcolumn_to_drop. When adding fields, you need to specify a location to optimize query performance and data structure; before deleting fields, you need to confirm that the operation is irreversible; modifying table structure using online DDL, backup data, test environment, and low-load time periods is performance optimization and best practice.





