what is kali linux
Kali Linux is a Debian-based Linux distribution designed for advanced penetration testing and security auditing; it contains hundreds of tools suitable for various information security tasks such as penetration testing, security research, computer Forensics and reverse engineering, etc.

The operating environment of this tutorial: Kali Linux 2021.2 system, Dell G3 computer.
What is Kali Linux?
Kali Linux is a Debian-based Linux distribution designed for advanced penetration testing and security auditing. Kali contains hundreds of tools suitable for various information security tasks such as penetration testing, security research, computer forensics and reverse engineering. Kali Linux is developed, funded and maintained by Offensive Security, a leading information security training company.

Kali Linux was released on March 13, 2013 as a complete, top-to-bottom rebuild of BackTrack Linux, fully adhering to Debian development standards.
Over 600 Penetration Testing Tools Included: After reviewing every tool included in BackTrack, we eliminated a large number of tools that simply didn’t work or duplicated others that offered the same or similar functional tools. Details on what's included are on the Kali Tools website.
Free (like beer), always will be: Kali Linux, like BackTrack, is completely free, always free. You never pay for Kali Linux.
Open source Git tree: We are committed to the open source development model, and our development tree is available for everyone to view. All source code that goes into Kali Linux is available for anyone who wants to tweak or rebuild the package to suit their specific needs.
FHS Compliant: Kali adheres to file system hierarchy standards, allowing Linux users to easily locate binaries, support files, libraries, and more.
Extensive wireless device support: The wireless interface supports the usual key points of Linux distributions. We've built Kali Linux to support as many wireless devices as possible, allowing it to run well on a variety of hardware, and making it compatible with numerous USB and other wireless devices.
Customized kernel, patched for injections: As penetration testers, development teams often need to conduct over-the-air assessments, so our kernels contain the latest injection patches.
Developed in a secure environment: The Kali Linux team consists of a small group of people who are the only ones trusted to submit packages and interact with the repository, all using a variety of Security protocol completed.
GPG signed packages and repositories: Every package in Kali Linux is signed by every developer who builds and submits it, and the repository then also signs the package Make a signature.
Multi-language support: While penetration tools tend to be written in English, we made sure Kali included true multi-language support, allowing more users to operate in their native language and find where they work required tools.
Fully Customizable: We understand that not everyone will agree with our design decisions, so we’ve made it as easy as possible for our adventurous users to customize Kali Linux to their liking, All the way to the kernel.
ARMEL and ARMHF support: Since ARM-based single-board systems like Raspberry Pi and BeagleBone Black, etc. are becoming more popular and affordable, we know about Kali’s ARM support Needs to be as powerful as we can manage, fully applicable to ARMEL and ARMHF systems. Kali Linux is available for a variety of ARM devices, and the ARM repositories are integrated with the mainline distribution, so ARM's tools will be updated along with other distributions.
What can Kali Linux do?
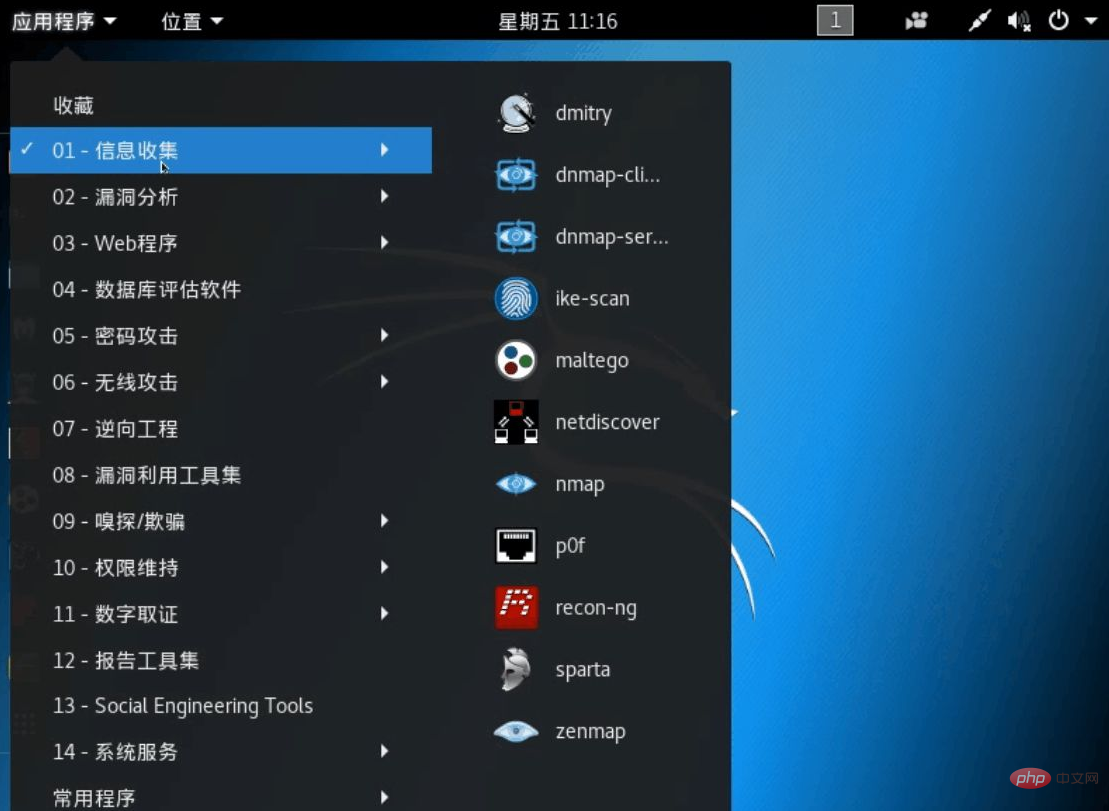
Information forensics (disk recovery, memory analysis, PDF audit, registry audit)
Penetration testing evaluates network system security (white hat hacking tools). Generally, more people learn this, and now it is mainly white hat hackers.
Attack WPA/WPA2 protected wireless networks (get WiFi passwords, network sniffing)
Crack passwords ( Crack hashed passwords offline and website login passwords online)
-
Reverse engineering (decompile programs written in android, Java, C into code)
Social engineering (the favorite of black hat hackers)
Related recommendations: "Linux Video Tutorial"
The above is the detailed content of what is kali linux. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
VS Code system requirements: Operating system: Windows 10 and above, macOS 10.12 and above, Linux distribution processor: minimum 1.6 GHz, recommended 2.0 GHz and above memory: minimum 512 MB, recommended 4 GB and above storage space: minimum 250 MB, recommended 1 GB and above other requirements: stable network connection, Xorg/Wayland (Linux)
 Linux Architecture: Unveiling the 5 Basic Components
Apr 20, 2025 am 12:04 AM
Linux Architecture: Unveiling the 5 Basic Components
Apr 20, 2025 am 12:04 AM
The five basic components of the Linux system are: 1. Kernel, 2. System library, 3. System utilities, 4. Graphical user interface, 5. Applications. The kernel manages hardware resources, the system library provides precompiled functions, system utilities are used for system management, the GUI provides visual interaction, and applications use these components to implement functions.
 vscode terminal usage tutorial
Apr 15, 2025 pm 10:09 PM
vscode terminal usage tutorial
Apr 15, 2025 pm 10:09 PM
vscode built-in terminal is a development tool that allows running commands and scripts within the editor to simplify the development process. How to use vscode terminal: Open the terminal with the shortcut key (Ctrl/Cmd). Enter a command or run the script. Use hotkeys (such as Ctrl L to clear the terminal). Change the working directory (such as the cd command). Advanced features include debug mode, automatic code snippet completion, and interactive command history.
 Where to write code in vscode
Apr 15, 2025 pm 09:54 PM
Where to write code in vscode
Apr 15, 2025 pm 09:54 PM
Writing code in Visual Studio Code (VSCode) is simple and easy to use. Just install VSCode, create a project, select a language, create a file, write code, save and run it. The advantages of VSCode include cross-platform, free and open source, powerful features, rich extensions, and lightweight and fast.
 How to check the warehouse address of git
Apr 17, 2025 pm 01:54 PM
How to check the warehouse address of git
Apr 17, 2025 pm 01:54 PM
To view the Git repository address, perform the following steps: 1. Open the command line and navigate to the repository directory; 2. Run the "git remote -v" command; 3. View the repository name in the output and its corresponding address.
 How to run java code in notepad
Apr 16, 2025 pm 07:39 PM
How to run java code in notepad
Apr 16, 2025 pm 07:39 PM
Although Notepad cannot run Java code directly, it can be achieved by using other tools: using the command line compiler (javac) to generate a bytecode file (filename.class). Use the Java interpreter (java) to interpret bytecode, execute the code, and output the result.
 What is the main purpose of Linux?
Apr 16, 2025 am 12:19 AM
What is the main purpose of Linux?
Apr 16, 2025 am 12:19 AM
The main uses of Linux include: 1. Server operating system, 2. Embedded system, 3. Desktop operating system, 4. Development and testing environment. Linux excels in these areas, providing stability, security and efficient development tools.
 How to run sublime after writing the code
Apr 16, 2025 am 08:51 AM
How to run sublime after writing the code
Apr 16, 2025 am 08:51 AM
There are six ways to run code in Sublime: through hotkeys, menus, build systems, command lines, set default build systems, and custom build commands, and run individual files/projects by right-clicking on projects/files. The build system availability depends on the installation of Sublime Text.






