What is an application layer denial of service attack?
Application layer denial of service attack refers to application layer DDOS. DDOS is also called distributed denial of service. It is different from network layer DDOS. Since it occurs at the application layer, the TCP three-way handshake has been completed, the connection has been established, and initiated The attacking IP addresses are all real.

Application Layer Denial of Service Attack
DDOS Introduction
DDOS is also called distributed denial of service, and its full name is Distributed Denial of Service. DDOS originally uses reasonable requests to cause resource overload, resulting in service unavailability
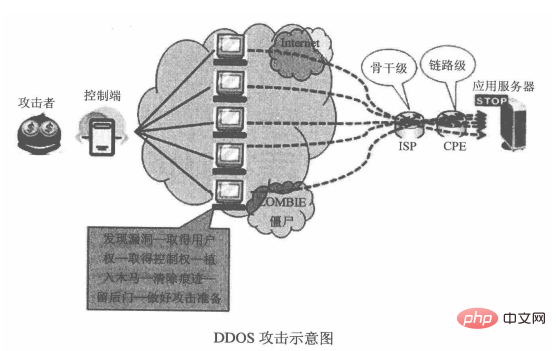
Network layer DDOS: forge a large number of source IP addresses and send a large number of SYN packets to the server, because the source address It is fake, will not respond, and consumes a lot of server resources (CPU and memory)
Application layer DDOS
Application layer DDOS is different from network layer DDOS. Due to the occurrence At the application layer, the TCP three-way handshake has been completed, the connection has been established, and the IP addresses that launched the attack are all real
CC attacks: continuously launched against some application interfaces that consume large resources Normal requests to consume server-side resources
Limit request frequency: Make a request frequency limit for each client in the application
For more related technical articles, please visit PHP中文网!
The above is the detailed content of What is an application layer denial of service attack?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1318
1318
 25
25
 1268
1268
 29
29
 1248
1248
 24
24
 What are the protocols belonging to the application layer in the tcp ip reference model?
Jul 04, 2022 am 10:09 AM
What are the protocols belonging to the application layer in the tcp ip reference model?
Jul 04, 2022 am 10:09 AM
Application layer protocols include: 1. Telnet, which allows users on one machine to log in to a remote machine and perform work; 2. FTP, which provides a method to move files from one machine to another; 3. SMTP is a protocol that provides email transmission; 4. SNMP is a standard protocol used to manage network nodes in IP networks; 5. DNS is mainly used to "translate" familiar web addresses into An IP address that a computer can understand; 6. HTTP is a request-response protocol used to obtain the home page on the WWW.
 Nginx security practice: preventing DDoS attacks
Jun 11, 2023 am 08:13 AM
Nginx security practice: preventing DDoS attacks
Jun 11, 2023 am 08:13 AM
With the development of the Internet, network attack methods have become more and more diverse, including DDoS attacks. This attack method uses multiple attack sources to initiate a large number of requests to the target server at the same time, causing the server to be overwhelmed and unable to work properly. . Therefore, protecting the server is very important for some important websites. As a high-performance, cross-platform web server and reverse proxy server, Nginx can help us resist DDoS attacks. The following will summarize the security practices of Nginx to prevent D
 How to use Nginx and Nginx Plus to resist DDOS attacks
May 14, 2023 pm 08:34 PM
How to use Nginx and Nginx Plus to resist DDOS attacks
May 14, 2023 pm 08:34 PM
1. Characteristics of application layer DDoS attacks. Application layer (seventh layer/http layer) DDoS attacks are usually initiated by Trojan horse programs, which can be designed to better exploit the vulnerabilities of the target system. For example, for a system that cannot handle a large number of concurrent requests, just by establishing a large number of connections and periodically sending out a small number of data packets to maintain the session, the system's resources can be exhausted, making it unable to accept new connection requests to achieve the purpose of DDoS. Other attacks include sending a large number of connection requests to send large data packets. Because the attack is initiated by a Trojan horse program, the attacker can quickly establish a large number of connections and issue a large number of requests in a short period of time. The following are some DDoS characteristics. We can use these characteristics to resist DDoS (including
 Microsoft sets defense record in response to 3.47 Tbps DDoS attack
Apr 22, 2023 am 08:52 AM
Microsoft sets defense record in response to 3.47 Tbps DDoS attack
Apr 22, 2023 am 08:52 AM
Microsoft inadvertently set a new record last November when it mitigated a 3.47Tbps DDoS (distributed denial of service) attack. In a blog post, the Redmond giant shared Azure DDoS protection data for the third quarter of 2021. The company noted that the number of DDoS attacks increased in the second half of 2021. DDoS is a popular attack method that anyone can use due to the low price of attack services. In the second half of 2021, Microsoft mitigated an average of 1,955 attacks per day, an increase of 40% from the first half of the year. However, this pales in comparison to the 4,296 attacks mitigated on August 10, 2021. Overall,
 Dialogue with Chang Chai, the founder of Unbounded AI: The entrepreneurial opportunities of AI are at the application layer丨Innovator
Aug 04, 2023 pm 11:21 PM
Dialogue with Chang Chai, the founder of Unbounded AI: The entrepreneurial opportunities of AI are at the application layer丨Innovator
Aug 04, 2023 pm 11:21 PM
Author | Editor Yu Huiru | Liu Yu The lowering of technical barriers has spawned a large number of AI painting startups, which also means fierce competition. Unbounded AI, who is among them, has personal experience of this. Currently, the number of Unbounded AI users is less than 3 million, which is still far from the annual goal of 10 million. Chang Chai, the founder of Wujie AI, said bluntly that user growth has entered a climbing period and will continue to work hard in the second half of the year. The sluggish growth of unbounded AI is a microcosm of the industry. As an emerging field, the AI painting industry is changing rapidly. At the World Artificial Intelligence Conference a week ago, Alibaba Cloud added a new member to its Tongyi series of large models - Tongyi Wanxiang, which is positioned as a large model for AI painting creation. In addition to Alibaba, large models launched by Baidu, iFlytek, SenseTime and other companies all have Wensheng diagrams and many other features.
 What are the attack methods of Ddos?
May 19, 2023 pm 04:10 PM
What are the attack methods of Ddos?
May 19, 2023 pm 04:10 PM
The three attack methods of DDoS are: 1. SYN/ACKFlood attack; mainly by sending a large number of SYN or ACK packets with forged source IPs and source ports to the victim host, causing the host's cache resources to be exhausted or busy sending response packets to cause rejection. Serve. 2. TCP full connection attack; it is designed to bypass conventional firewall inspections. 3. Script attack; characterized by establishing a normal TCP connection with the server and constantly submitting queries, lists and other calls that consume a large number of database resources to the script program. The biggest headache for websites is being attacked. Common server attack methods mainly include the following: port penetration, port penetration, password cracking, and DDOS attacks. Among them, DDOS is currently the most powerful and the most
 Seven myths and misconceptions about robot attacks
Apr 12, 2023 pm 06:49 PM
Seven myths and misconceptions about robot attacks
Apr 12, 2023 pm 06:49 PM
Although bot attacks are more common than ever, there are some unsubstantiated myths surrounding them. By understanding these myths, you'll be better able to protect your website from potential damage and keep your customers happy. Here are seven of the most common robot myths and their truths. 1. Firewalls will stop sophisticated bot attacks 73% of enterprises believe legacy WAFs will protect them from bot attacks. A WAF is one of the first lines of defense for protecting web applications. It covers the most critical risks, including but not limited to the OWASP Top 10. WAF can be used to block malicious bots by creating WAF rules. Its basic mitigations include applying rate limiting to manage suspicious IPs
 What are the three attack methods of DDoS?
Jan 29, 2023 pm 05:25 PM
What are the three attack methods of DDoS?
Jan 29, 2023 pm 05:25 PM
The three attack methods of DDoS are: 1. SYN/ACK Flood attack; mainly caused by sending a large number of SYN or ACK packets with forged source IPs and source ports to the victim host, causing the host's cache resources to be exhausted or busy sending response packets. Denial of service. 2. TCP full connection attack; it is designed to bypass conventional firewall inspections. 3. Script attack; characterized by establishing a normal TCP connection with the server and constantly submitting queries, lists and other calls that consume a large number of database resources to the script program.



