 Operation and Maintenance
Operation and Maintenance
 Safety
Safety
 Experiment on simple brute force enumeration method to bypass the 2FA verification mechanism of the target system
Experiment on simple brute force enumeration method to bypass the 2FA verification mechanism of the target system
Experiment on simple brute force enumeration method to bypass the 2FA verification mechanism of the target system

The Writeup shared today is a dynamic password OTP (One Time Password) for the target system that the author is participating in vulnerability testing, and is implemented by using a simple brute force enumeration method. Bypassing or cracking the target system's two-factor authentication mechanism 2FA (Two-Factor Authentication). The target system is the website of India's largest travel service company, which uses dynamic password OTP as a means of implementing two-factor authentication 2FA.
Generally speaking, OTP is a 4-digit combination from 0000 to 9999. If OTP has 10,000 possible combinations, in today's powerful computer era, it only takes a few minutes to process 10,000 combinations. time. So, if the OTP's verification mechanism is improper, anyone can bypass it through simple brute force enumeration.
Why can I bypass 2FA?
The target system does not rate limit unsuccessful request attempts.
The target system has no new dynamic password measures for unsuccessful request attempts.
Prerequisite preparation:
Web browser, BurpSuite.
The recurrence process of bypassing 2FA
The recurrence process of bypassing 2FA
1. Open BurpSuite and log in to the target system website using your mobile phone number , here, deliberately enter the wrong dynamic OTP sent by the system to your mobile phone (here we enter 1234 casually), and then use BurpSuite to capture the traffic;
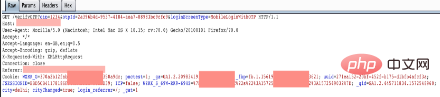
We can see from BurpSuite Relevant information to the OTP API – verifyOTP?otp=:

2. Right-click the OTP sending process and Send to intruder:
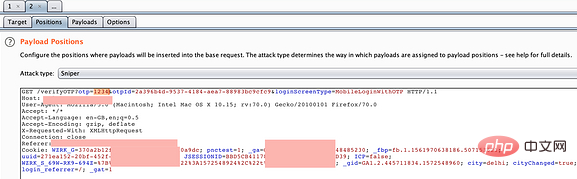
3. Select the otp=1234 placeholder and set it to simple violent enumeration variable mode:

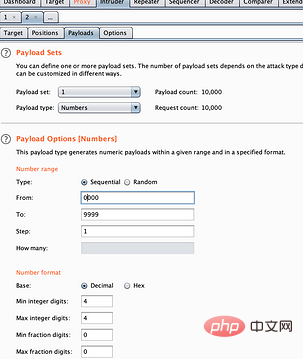
4. Select the Payload tag item, Modify it to any combination, and then click attack:
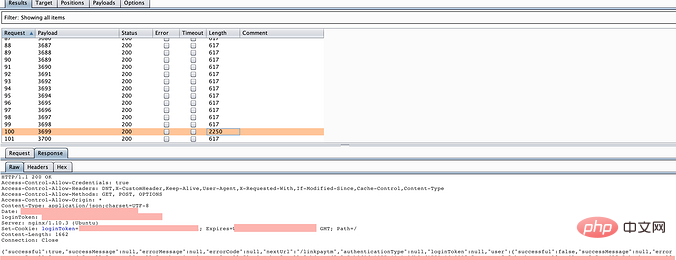
5. The attack begins. From the enumeration response result, we can see an abnormal response with a length of 2250. As expected, this is it:
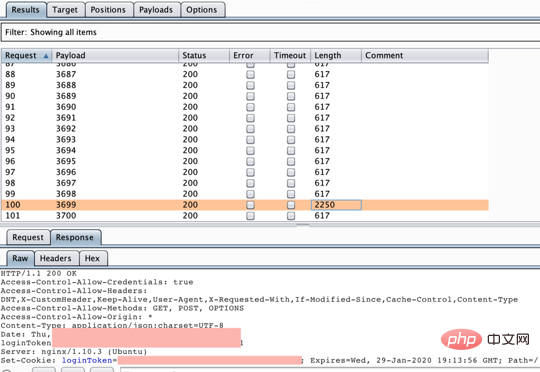
6. Use this OTP to log in, It can be successful and effective!
Related tutorial recommendations: web server security
The above is the detailed content of Experiment on simple brute force enumeration method to bypass the 2FA verification mechanism of the target system. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Will human trials be scrapped? Musk's Neuralink faces federal investigation, experimental animals die frequently
Apr 12, 2023 pm 05:37 PM
Will human trials be scrapped? Musk's Neuralink faces federal investigation, experimental animals die frequently
Apr 12, 2023 pm 05:37 PM
Last week, Musk held Neuralink’s Show & Tell demonstration event to show the world the latest progress in brain-computer interfaces. At the meeting, Musk said that it is very difficult to go from prototype to production and faces many challenges. Neuralink has been working hard to initiate human trials and has submitted all the necessary documentation to the FDA to begin human trials. Musk estimates that the first Neuralink device could be in the human brain within 5-6 months. At the meeting, Musk emphasized that Neuralink respects animal subjects and that brain-computer interface devices have undergone extensive benchmark testing before being implanted in animals. Two monkeys Pager and
 Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
An unpatchable Yubico two-factor authentication key vulnerability has broken the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. The Feitian A22 JavaCard and other devices using Infineon SLB96xx series TPMs are also vulnerable.All
 What are Enumerations (Enums) in PHP 8.1?
Apr 03, 2025 am 12:05 AM
What are Enumerations (Enums) in PHP 8.1?
Apr 03, 2025 am 12:05 AM
The enumeration function in PHP8.1 enhances the clarity and type safety of the code by defining named constants. 1) Enumerations can be integers, strings or objects, improving code readability and type safety. 2) Enumeration is based on class and supports object-oriented features such as traversal and reflection. 3) Enumeration can be used for comparison and assignment to ensure type safety. 4) Enumeration supports adding methods to implement complex logic. 5) Strict type checking and error handling can avoid common errors. 6) Enumeration reduces magic value and improves maintainability, but pay attention to performance optimization.
 Python program to find enum by string value
Sep 21, 2023 pm 09:25 PM
Python program to find enum by string value
Sep 21, 2023 pm 09:25 PM
An enumeration in Python is a user-defined data type that consists of a named set of values. A finite set of values is defined using an enumeration, and these values can be accessed in Python using their names instead of integer values. Enumerations make code more readable and maintainable, and they also enhance type safety. In this article, we will learn how to find an enumeration by its string value in Python. To find an enum by a string value we need to follow these steps: Import the enum module in your code Define the enum with the required set of values Create a function that takes the enum string as input and returns the corresponding enum value . Syntax fromenumimportEnumclassClassName(Enum
 How to use enumerations in C/C++?
Aug 28, 2023 pm 05:09 PM
How to use enumerations in C/C++?
Aug 28, 2023 pm 05:09 PM
Enumeration is a user-defined data type in C language. It is used to give names to integer constants, making programs easier to read and maintain. The keyword "enum" is used to declare an enumeration. The following is the syntax of enumerations in C language: enumenum_name{const1,const2,.....};Theenumkeywordisalsousedtodefinethevariablesofenumtype.Therearetwowaystodefinethevariablesofenumtypeasfollows.enumweek{sunday,monday,tuesday,
 What are the benefits when a C++ function returns an enumeration type?
Apr 20, 2024 pm 12:33 PM
What are the benefits when a C++ function returns an enumeration type?
Apr 20, 2024 pm 12:33 PM
Benefits of using enumeration types as function return values: Improve readability: Use meaningful name constants to enhance code understanding. Type safety: Ensure return values fit within the expected range and avoid unexpected behavior. Save memory: Enumerated types generally take up less storage space. Easy to extend: New values can be easily added to the enumeration.
 C++ syntax error: Enumeration members need to be initialized within parentheses, what should I do?
Aug 22, 2023 pm 03:41 PM
C++ syntax error: Enumeration members need to be initialized within parentheses, what should I do?
Aug 22, 2023 pm 03:41 PM
C++ is a common programming language whose syntax is relatively rigorous and easy to learn and apply. However, during specific programming, it is inevitable to encounter various errors. One of the common errors is "enumeration members need to be initialized within parentheses". In C++, the enumeration type is a very convenient data type that can define a set of constants with discrete values, such as: enumColor{RED,YELLOW,GREEN}; In this example, we define an enumeration Type Color, which contains three enumerations
 Java program accesses all constants defined in an enumeration
Aug 19, 2023 pm 04:29 PM
Java program accesses all constants defined in an enumeration
Aug 19, 2023 pm 04:29 PM
After JDK version 5, Java introduced enumerations. It is a set of constants defined using the keyword 'enum'. In Java, final variables are somewhat similar to enumerations. In this article, we will create a Java program in which we define an enumeration class and try to access all the constants defined in the enumeration using valueOf() and values() methods. The Chinese translation of Enum is: Enumeration. When we need to define a fixed set of constants, we use the enumeration class. For example, if we want to use the days of the week, the names of the planets, the names of the five vowels, etc. Note that the names of all constants are declared in uppercase letters. Although in Java, enumeration is a class type, we cannot instantiate it. exist





