How to prevent SQL injection attacks?
SQL injection is an injection attack that can execute malicious SQL statements. The following article will introduce you to SQL injection and briefly introduce methods to prevent SQL injection attacks. I hope it will be helpful to you.
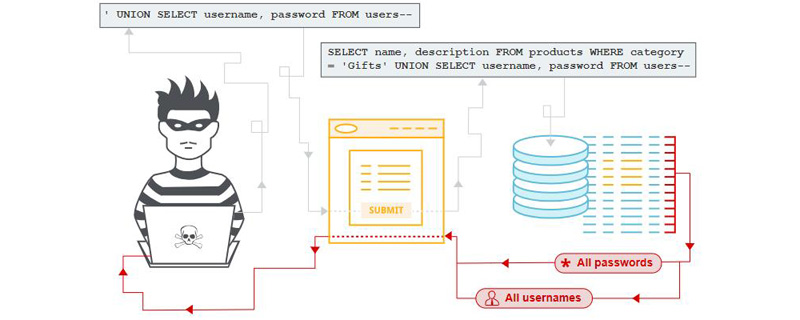
What is SQL injection?
SQL injection (SQLi) is an injection attack that can execute malicious SQL statements. It gives attackers complete control over the database server behind a web application by inserting arbitrary SQL code into database queries. Attackers can use SQL injection vulnerabilities to bypass application security measures; they can bypass authentication and authorization of a web page or web application and retrieve the contents of an entire SQL database; they can also use SQL injection to add, modify, and delete items in the database. Record.
SQL injection vulnerabilities can affect any website or web application that uses a SQL database such as MySQL, Oracle, SQL Server, or others. Criminals may use it to gain unauthorized access to users' sensitive data: customer information, personal data, trade secrets, intellectual property, etc. SQL injection attacks are one of the oldest, most popular, and most dangerous web application vulnerabilities.
Types of SQL Injection Attacks
SQL injection attacks can be performed in a variety of ways. An attacker may observe the behavior of a system before choosing a specific attack method.
In-band injection
This is a typical attack where the attacker can launch the attack through the same communication channel and obtain the results. This is done through two in-band techniques:
● Error-based SQL injection: obtains information about the database from the displayed error message
● Union-based SQL injection: relies on The attacker was able to connect the results of UNION ALL's stolen information with legitimate results.
Both techniques rely on the attacker modifying the SQL sent by the application, as well as the errors displayed in the browser and the information returned. It will succeed if the application developer or database developer fails to properly parameterize the values they use in the query. Both are trial and error methods and errors can be detected.
Blind Injection
Also known as inferential SQL injection, a blind injection attack does not display data directly from the target database; instead, the attacker carefully examines the behavior Indirect clues. Details in the HTTP response, blank web pages for certain user inputs, and how long it takes for the database to respond to certain user inputs can all be clues, depending on the attacker's goals. They can also point to another SQLi attack vector attempted by the attacker.
Out-of-Band Injection
This attack is somewhat sophisticated and may be used by an attacker when he is unable to achieve his goal in a single direct query-response attack attack. Typically, attackers craft SQL statements that, when presented to the database, trigger the database system to create a connection to an external server controlled by the attacker. In this way, an attacker can collect data or possibly control the behavior of the database.
Second-order injection is an out-of-band injection attack. In this case, the attacker will provide a SQL injection that will be stored and executed by a separate act of the database system. When secondary system behavior occurs (it could be something like a time-based job or something triggered by other typical administrators or users using the database) and the attacker's SQL injection is performed, that's when "reaching out" to the system Attacker control occurs.
How to prevent SQL injection attacks?
The following suggestions can help prevent successful SQL injection attacks:
1. Do not use dynamic SQL
Avoid providing the user with The input is put directly into the SQL statement; it is better to use prepared statements and parameterized queries, which is safer.
2. Do not keep sensitive data in plain text
Encrypt private/confidential data stored in the database; this provides another level of protection to Prevent attackers from successfully expelling sensitive data.
3. Limit database permissions and privileges
Set the capabilities of the database user to the minimum required; this will limit what an attacker can do if they manage to gain access. .
4. Avoid displaying database errors directly to the user
An attacker can use these error messages to obtain information about the database.
5. Use a Web Application Firewall (WAF) for web applications that access the database
This provides protection for web-oriented applications and it can help identify SQL injection attempts; depending on the settings, it can also help prevent SQL injection attempts from reaching the application (and therefore the database).
6. Regularly test web applications that interact with databases
Doing so can help catch new bugs or regressions that could allow SQL injection.
7. Update the database to the latest available patches
This prevents attackers from exploiting known weaknesses/bugs present in older versions.
Summary: SQL injection is a popular attack method, but by taking appropriate precautions, such as ensuring data is encrypted, your web application is secured and tested, and that you are up to date with patches, You can take meaningful steps to keep your data secure.
Recommended video tutorials: "MySQL Tutorial"
The above is the entire content of this article, I hope it will be helpful to everyone's learning. For more exciting content, you can pay attention to the relevant tutorial columns of the PHP Chinese website! ! !
The above is the detailed content of How to prevent SQL injection attacks?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1655
1655
 14
14
 1413
1413
 52
52
 1306
1306
 25
25
 1252
1252
 29
29
 1226
1226
 24
24
 How do you prevent SQL Injection in PHP? (Prepared statements, PDO)
Apr 15, 2025 am 12:15 AM
How do you prevent SQL Injection in PHP? (Prepared statements, PDO)
Apr 15, 2025 am 12:15 AM
Using preprocessing statements and PDO in PHP can effectively prevent SQL injection attacks. 1) Use PDO to connect to the database and set the error mode. 2) Create preprocessing statements through the prepare method and pass data using placeholders and execute methods. 3) Process query results and ensure the security and performance of the code.
 MySQL's Role: Databases in Web Applications
Apr 17, 2025 am 12:23 AM
MySQL's Role: Databases in Web Applications
Apr 17, 2025 am 12:23 AM
The main role of MySQL in web applications is to store and manage data. 1.MySQL efficiently processes user information, product catalogs, transaction records and other data. 2. Through SQL query, developers can extract information from the database to generate dynamic content. 3.MySQL works based on the client-server model to ensure acceptable query speed.
 How to start mysql by docker
Apr 15, 2025 pm 12:09 PM
How to start mysql by docker
Apr 15, 2025 pm 12:09 PM
The process of starting MySQL in Docker consists of the following steps: Pull the MySQL image to create and start the container, set the root user password, and map the port verification connection Create the database and the user grants all permissions to the database
 Laravel Introduction Example
Apr 18, 2025 pm 12:45 PM
Laravel Introduction Example
Apr 18, 2025 pm 12:45 PM
Laravel is a PHP framework for easy building of web applications. It provides a range of powerful features including: Installation: Install the Laravel CLI globally with Composer and create applications in the project directory. Routing: Define the relationship between the URL and the handler in routes/web.php. View: Create a view in resources/views to render the application's interface. Database Integration: Provides out-of-the-box integration with databases such as MySQL and uses migration to create and modify tables. Model and Controller: The model represents the database entity and the controller processes HTTP requests.
 Solve database connection problem: a practical case of using minii/db library
Apr 18, 2025 am 07:09 AM
Solve database connection problem: a practical case of using minii/db library
Apr 18, 2025 am 07:09 AM
I encountered a tricky problem when developing a small application: the need to quickly integrate a lightweight database operation library. After trying multiple libraries, I found that they either have too much functionality or are not very compatible. Eventually, I found minii/db, a simplified version based on Yii2 that solved my problem perfectly.
 Laravel framework installation method
Apr 18, 2025 pm 12:54 PM
Laravel framework installation method
Apr 18, 2025 pm 12:54 PM
Article summary: This article provides detailed step-by-step instructions to guide readers on how to easily install the Laravel framework. Laravel is a powerful PHP framework that speeds up the development process of web applications. This tutorial covers the installation process from system requirements to configuring databases and setting up routing. By following these steps, readers can quickly and efficiently lay a solid foundation for their Laravel project.
 MySQL and phpMyAdmin: Core Features and Functions
Apr 22, 2025 am 12:12 AM
MySQL and phpMyAdmin: Core Features and Functions
Apr 22, 2025 am 12:12 AM
MySQL and phpMyAdmin are powerful database management tools. 1) MySQL is used to create databases and tables, and to execute DML and SQL queries. 2) phpMyAdmin provides an intuitive interface for database management, table structure management, data operations and user permission management.
 MySQL vs. Other Databases: Comparing the Options
Apr 15, 2025 am 12:08 AM
MySQL vs. Other Databases: Comparing the Options
Apr 15, 2025 am 12:08 AM
MySQL is suitable for web applications and content management systems and is popular for its open source, high performance and ease of use. 1) Compared with PostgreSQL, MySQL performs better in simple queries and high concurrent read operations. 2) Compared with Oracle, MySQL is more popular among small and medium-sized enterprises because of its open source and low cost. 3) Compared with Microsoft SQL Server, MySQL is more suitable for cross-platform applications. 4) Unlike MongoDB, MySQL is more suitable for structured data and transaction processing.




